
Requirements for Industrial Control Level Protection 2.0
On May 13, 2019, the Cybersecurity Level Protection System 2.0 standard (Level Protection 2.0) was released, which refined, classified, and strengthened the existing standards, incorporating industrial control systems, cloud computing, mobile internet, IoT, and big data security into the management scope.
Level Protection 2.0 officially came into effect on December 1, 2019. How to meet the compliance requirements of Level Protection 2.0 and establish an effective industrial control security system is a pressing issue for every industrial enterprise.
Industrial Control Level Protection Security Technology Design Framework
The security technology design architecture for industrial control systems adopts a “vertical layering and horizontal partitioning” defense-in-depth strategy, constructing a security management center and designing a triple protection system of secure computing environment, security area boundaries, and secure communication networks to achieve a trusted, controllable, and manageable system security interconnection, regional boundary security protection, and computing environment security.
The security technology design framework for industrial control level protection is shown in the figure:
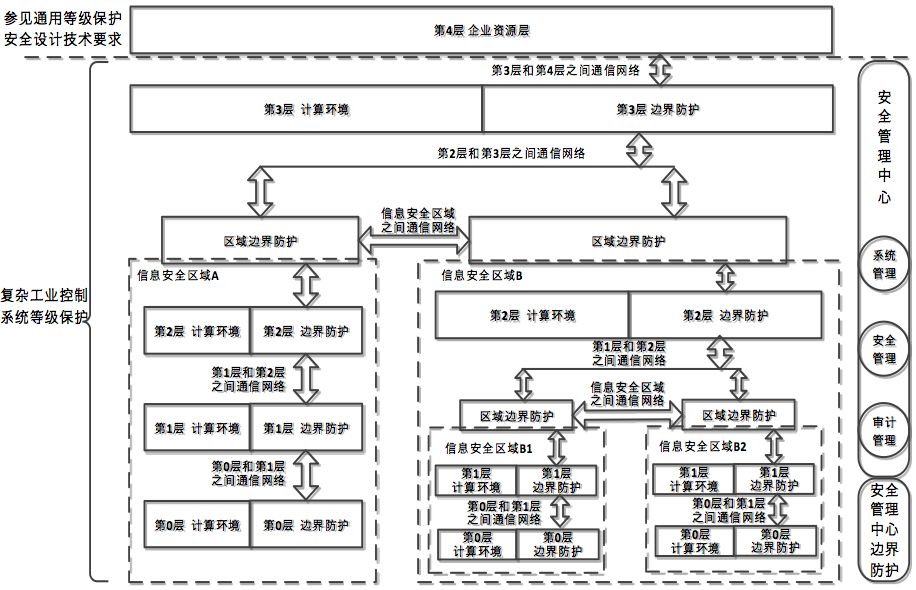
Industrial Control Level Protection Defense Solutions
01
Secure Communication Network
Based on “vertical layering and horizontal partitioning,” technical means are used for isolation; the wide area network can implement encryption techniques to ensure secure communication transmission based on existing business situations.
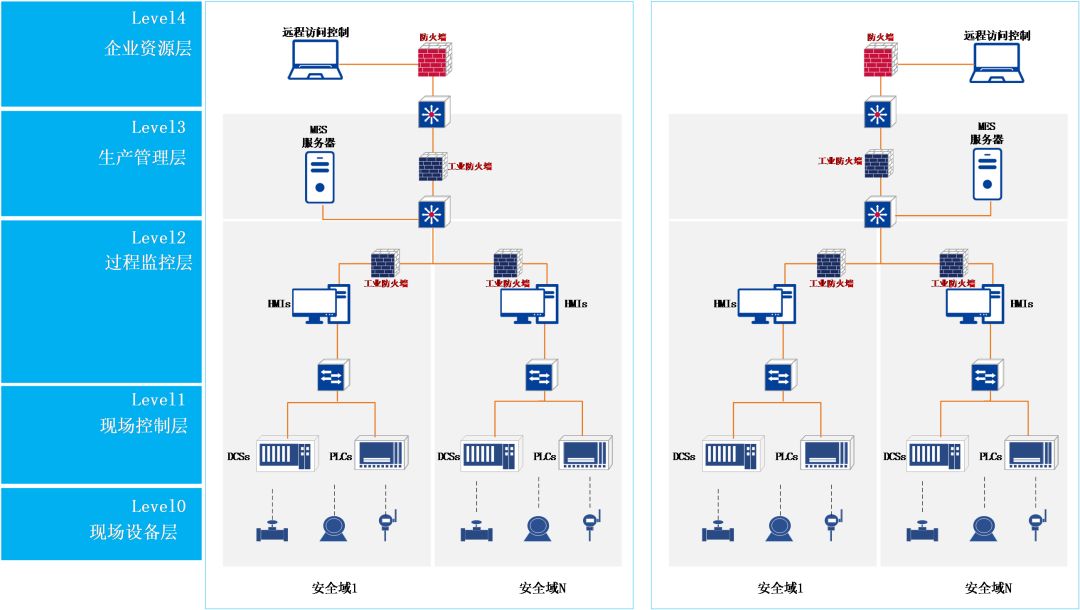
1
Industrial Network Isolation
Deploy industrial firewalls between the production management layer and the enterprise resource layer, configure unidirectional transmission policies, prohibit illegal access from the office network to the production network, and implement a whitelist strategy between different security domains to prevent unauthorized access and stop malicious code from spreading between security domains.
2
Internet and Office Network Isolation
Deploy next-generation firewalls at the boundary between the internet and the office network to prohibit illegal access from the internet to the office network, ensuring network architecture security.
02
Secure Area Boundaries
Prohibit non-industrial network service requests such as E-Mail, Web, Telnet, Rlogin, FTP from crossing the boundary; additional dial-up and wireless control requirements should be added for specific industrial scenarios.
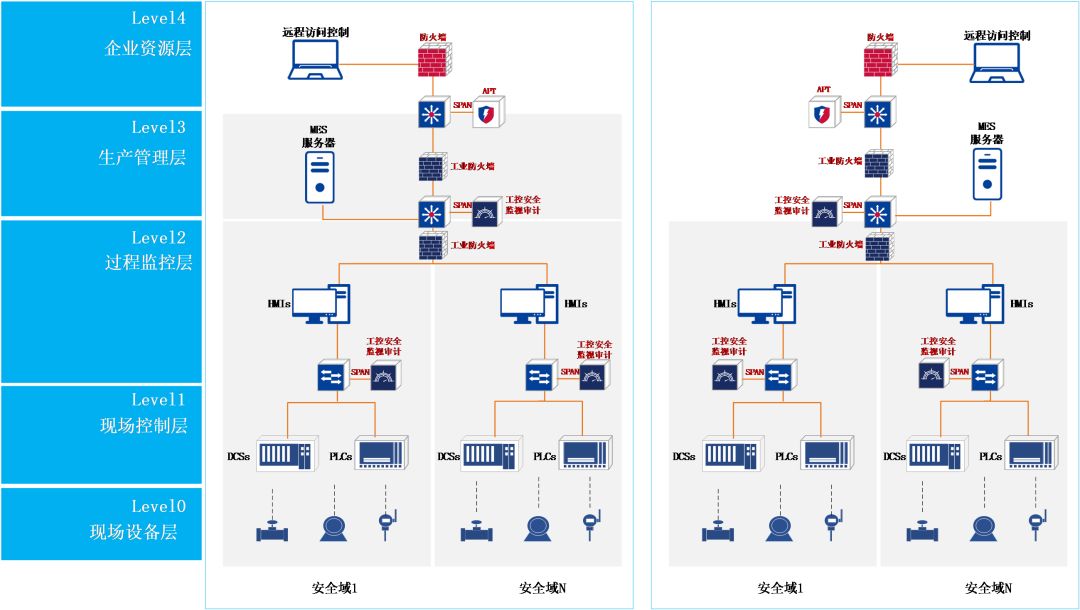
1
Monitoring and Auditing Production Network Traffic
Deploy an industrial control security monitoring and auditing platform beside each core switch to timely detect network intrusion behaviors and alarm for abnormal behaviors exceeding the baseline.
2
Monitoring Design for Production Management Layer Traffic
Deploy an APT attack (cyber warfare) early warning platform on the core switch of the office network to analyze, record, and alarm for new types of network attack behaviors.
03
Secure Computing Environment
Control devices should meet general requirements such as identity verification, access control, and security auditing under conditional circumstances; ensure stability/availability, and use dedicated methods to update control devices; unnecessary drivers, USB ports, network ports, etc., should be strictly controlled.
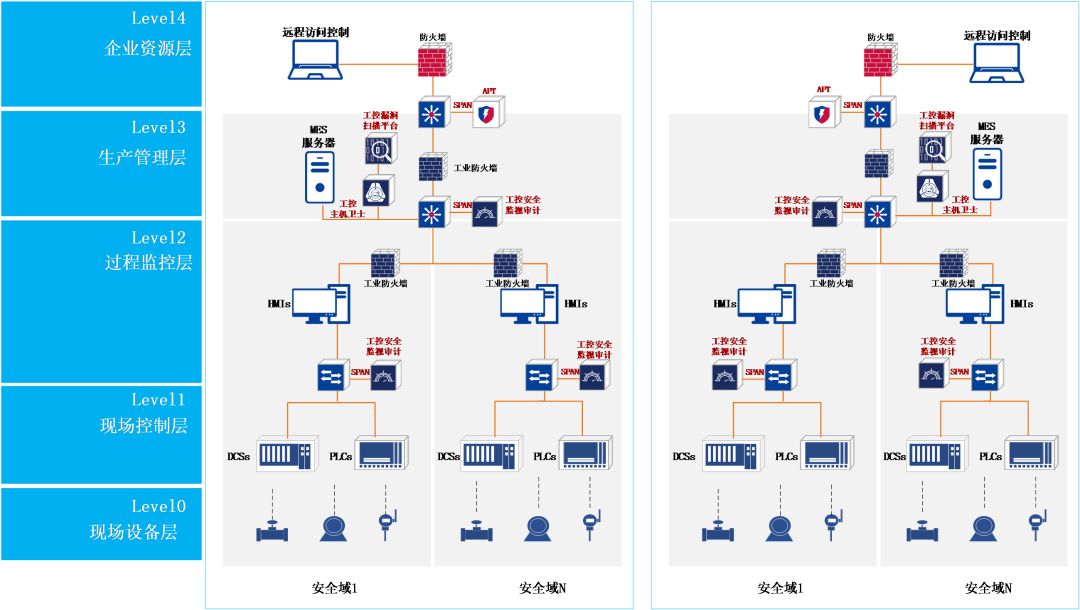
1
Security Reinforcement of Industrial Environment Hosts
Deploy industrial host guardians on key hosts and servers to block the installation and execution of any software or programs not in the whitelist database. Strictly control access permissions to host baselines, host resources, and user identity verification, and monitor and manage peripherals (such as USB drives) strictly.
2
Discovery of Vulnerabilities in Industrial Control Systems
Deploy an industrial control vulnerability scanning platform in reachable areas of the industrial control system network to detect and assess vulnerabilities in control devices, guiding timely patch updates and firmware updates for control devices.
04
Security Management Center
A specific management area should be defined to achieve minimal privilege system management, audit operations with traceability, and centralized control of security requirements and analysis.
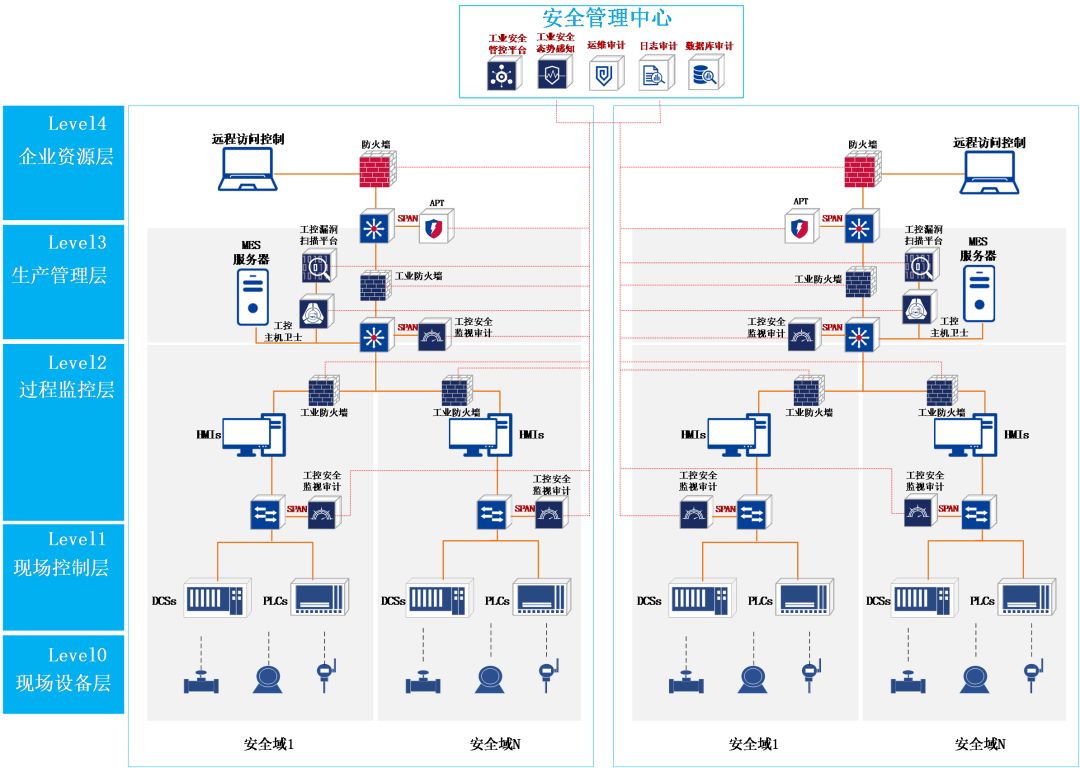
1
Security Operation and Maintenance Audit
The operation and maintenance audit and risk control system conduct comprehensive audits and identity verification for system operation and maintenance, auditing, recording, storing, and querying operational behaviors.
The comprehensive log auditing platform collects and centralizes data dispersed across various devices for analysis.
Database auditing and risk control systems audit, record, and store operation behaviors of databases.
2
Centralized Control of Security Devices
Deploy the Anheng Industrial Security Control Platform to achieve unified centralized management of security policies, malicious code, patch upgrades, etc., for security devices or components.
3
Situational Awareness of Industrial Security
The Anheng Industrial Security Situational Awareness Platform centrally monitors security devices, network devices, network links, hosts, and servers, identifying, alarming, and analyzing various security events, and tracking and tracing attack behaviors.

Anheng Information Partner Center
Long press to identify the QR code to follow us