The control gate of the underground water well pump at my hometown can be remotely controlled from a distance using a remote control. This way, when watering, one does not have to run over to push the gate, which is very convenient. Last time I went home, my mother said the accompanying remote control was lost, and she needed to buy a new one. The person selling it said it could be used but needed to be paired, though the seller did not explain how to pair it. However, no one in the village knew how to pair it, so while I was back, I was asked if I could help. At that time, I was busy helping with the autumn harvest and did not assist her, but later I researched related remote control products.
Researching Remote Control Types
Common remote control principles can be divided into 433MHz, LoRa, 2.4GHz, GPRS, NB-IOT, etc. However, for rural areas like ours, only 433MHz remote controls are applicable. This type of remote control scheme is relatively mature, simple, and has no ongoing costs. If using NB-IOT, one would also need to obtain an IoT card. There is also a LoRa scheme, which has a longer transmission distance and lower power consumption, and can form a network, but the cost is relatively higher.
The modulation methods for wireless signals include OOK, ASK, FSK, and GFSK. The demodulation principles include super-regeneration and superheterodyne. For those who want to delve deeper, please refer to university textbooks on communication principles. To briefly explain OOK (On-Off Keying), it is a modulation principle used to control one amplitude to be 0 and the other amplitude to be non-zero, which is OOK. Also known as binary amplitude shift keying (2ASK), it controls the on and off of a sine carrier wave using a unipolar non-return-to-zero code sequence. A long high-level code + a short low-level code represents logic 1, while a short high-level code + a long low-level code represents logic 0. The modulated signal is then transmitted through the antenna.
To achieve wireless communication, data signals must be modulated and demodulated according to the principles mentioned above. Debugging is necessary to send data via radio waves, while demodulation is to parse the transmitted data from the modulated radio waves. Therefore, the chip on the remote control side is the signal modulation chip, while the chip on the controlled side is the signal demodulation chip and data processing logic control chip.
Physical Analysis
I disassembled two remote control products that I had on hand. The images are as follows:

Remote Control Image 1

Remote Control Image 2

Receiver Module Image 1
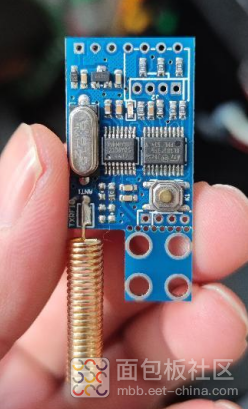
Receiver Module Image 2
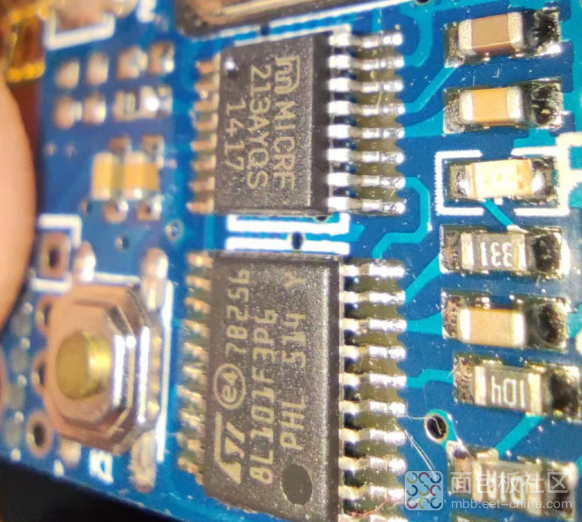
Receiver Module Image 3
Remote Control Product 2:

Remote Control Image 1

Remote Control Image 2

Receiver Module Image 1
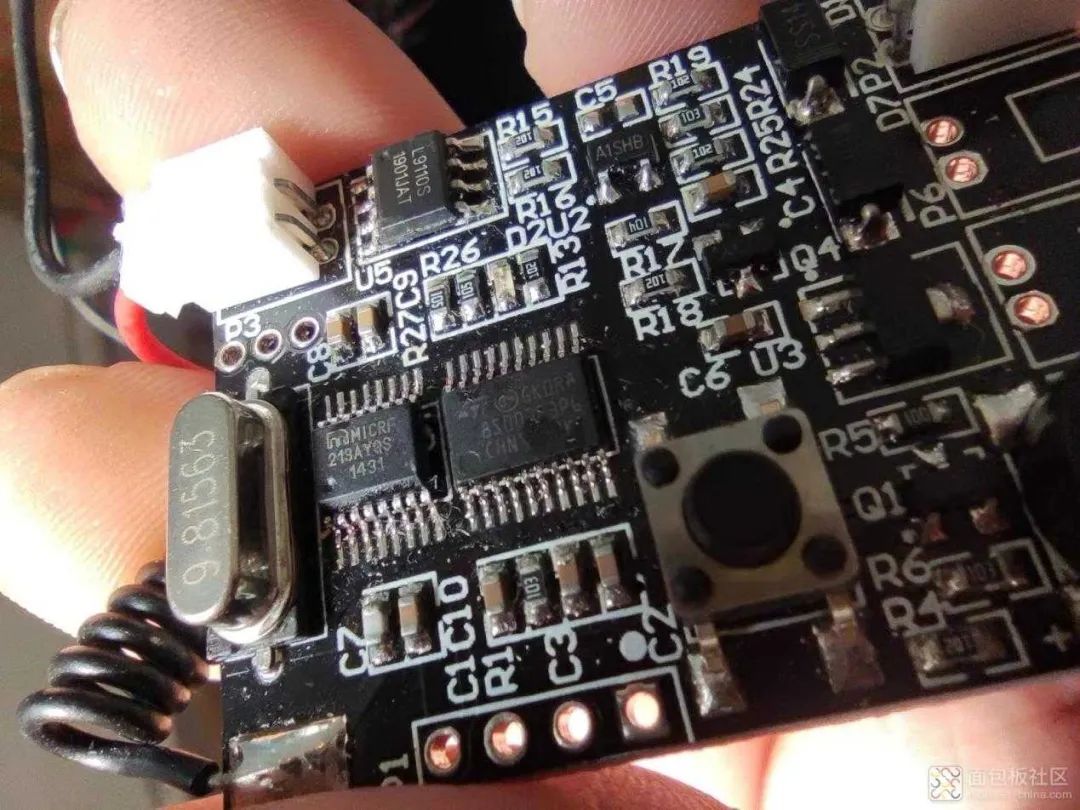
Receiver Module Image 2
Research Materials

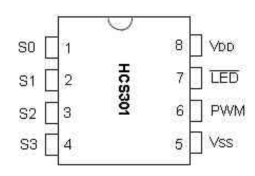

Data Transmission Process
Data Reception Process
This concludes the physical disassembly and material inquiry. Upon seeing the data for this chip, those who are new to remote control products may feel confused. Don’t worry; I will guide everyone through a deeper analysis and answer questions. Interested friends, please continue reading.
Summary
Based on the chip information we reviewed in the third part, we know that the two remote controls I have belong to the “rolling code” type of remote control. The so-called rolling code is a form of data encryption.
First, let me address the first question: why can one remote control operate one device, while others cannot? Or if the remote control is lost, how can a new one be paired? The answer to this question is as follows: currently, there are three types of 433 remote controls.
Fixed Code: Its address code is fixed and unchanging. Some may ask, if it is fixed, why can the living room remote control not operate the light in the room? Although the address code is fixed, it is composed of 8 different address code combinations, allowing pairing through different combinations to avoid the aforementioned situation! Fixed code remote controls are relatively simpler than rolling codes and are generally composed of systems like PT2262/2272, which are hardware-coded, fixed code remote control systems.
Learning Code: It consists of millions of different codes, and the receiver can only recognize the remote control through code learning. This greatly enhances product security. Typically, the encoding IC for learning codes is 1527 and 2240, with decoding done by a microcontroller.
Rolling Code: The encoder detects key input, wakes the system from power-saving mode, synchronously increments the counter by 1, and forms encrypted ciphertext data with the sequence number and key value, which is then sent out. Since the synchronized counter value is different each time it is sent, even if the same key is pressed multiple times, the output will differ. The synchronized counter automatically rolls forward, and the transmitted code will not repeat. Hence, it is called a rolling code. The synchronized counter and encoder sequence number are encrypted together with DES, with the DES key being unique to the manufacturer and must be kept confidential. The encrypted ciphertext is then transmitted via the RF system. Upon receiving the ciphertext, the receiver uses the manufacturer’s DES key to decrypt it, obtaining the synchronized counter and encoder sequence number. First, it checks if the encoder sequence number corresponds to that of the receiver. If it matches, it checks if the synchronized counter is within the synchronization window, meaning it is greater than the stored synchronized counter but not excessively so. If it is too large, the device will resynchronize. If within the synchronization window, it notifies the actuator to execute the user command, such as unlocking or locking the door.
Fixed code remote controls are configured through hardware to match the address of the remote control and the controlled device. The chip has address pins, and the address is determined by the pull-up, pull-down, or floating of these pins. Only devices with the same address can match. The drawbacks of this type of device include: first, low security, as the total number of addresses is limited, making it easy to have duplicate codes. This means that unsafe operations can occur, where devices with the same address can control each other, increasing the likelihood that someone else’s remote can control your device. Second, if a user wants to add a remote control, it can be quite troublesome. The main controller has only one fixed address code, and all detectors and remote controls must be set to the same address code as the main unit to function. Therefore, adding components requires knowing the main unit’s address code and having a certain level of electronic technical knowledge to manually configure it through jumpers or soldering for proper communication. Third, if the remote control is lost, it becomes a more serious issue, as the main unit cannot delete its code. If someone finds the remote, they can control the main unit at will; changing the main unit’s address code is even more troublesome, as it requires changing the address of all components to match the main unit’s address code.
Learning code remote controls can be said to be devices with internal memory that require pre-programmed firmware addresses to be burned into the sending and receiving chips. Only devices with the same address can match. Compared to fixed codes, these devices have relatively higher security, as the number of address bits can be very high, reducing the probability of “duplicate codes”. Second, adding components becomes much simpler, as the main unit does not have a fixed address code; all detectors and remote controls use different codes, and the main unit can learn the codes of each component to work. Therefore, adding components only requires learning and inputting on the main unit. Even if the remote control is lost, there is no need to worry; just delete its code on the main unit, usually by pressing a button to clear existing codes and short-pressing to add a new remote.
Next, we have our rolling code remote controls, which are the two products I disassembled. The above two types of remote controls communicate in plaintext. Of course, fixed code remote controls can also implement encryption measures. The term plaintext means that our data is transmitted without processing, directly added to the carrier wave and transmitted through the antenna. At this point, anyone can receive the data you send through the antenna and parse it, thus knowing what data you sent to control the device, allowing them to replicate an identical remote control. This sounds quite scary, as I have seen online experts say that using an audio line can reveal what data this type of remote control sends.

Audio Line
By plugging this line into a computer and opening a recording software, when your remote control sends data, the audio line can act as a receiving antenna, capturing the radio waves you send. The computer can then collect the carrier wave information you send, allowing for parsing of the data. For security reasons, rolling codes were developed, which encrypt the data before sending it out. The encryption method is rolling code encryption. The advantages of this type of product are security; while not absolutely secure, it is very secure. The downside is that replacing the remote control is not easy.
With the knowledge above, we understand why more and more products are using rolling codes, gradually phasing out fixed code and learning code products. Next, let’s focus on a deeper analysis of rolling code remote control products.

First, let’s look at the components of our remote control.
Chip: I disassembled several, and they are all HCS301, a product from MicroChip. It is likely that they hold the patent for encoding, which is why most rolling code schemes are from their company. Let’s delve into their product specifications to see how they achieve security.
Let’s look at the two images from the previous chapter regarding the product description.

Product Description
After reading this, I was completely confused and had no idea what they were talking about—what is rolling code, what is a sequence number, what is KeeLoQ, and how is it secure? If you are as puzzled as I was, let’s look at the sending process.
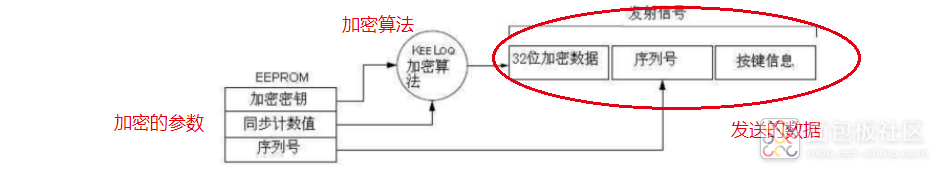
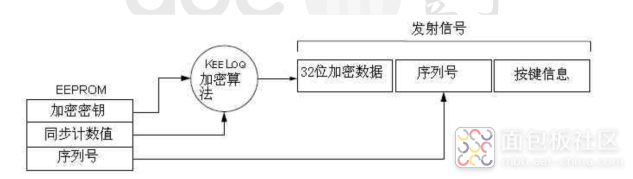
Sending Process
This is much clearer.
KeeLoQ is an encryption algorithm. To briefly mention encryption algorithms, if you were to design one, it might not be very realistic; we just use what works. The so-called encryption involves inputting a string of plaintext and a key, and through some mathematical operations, obtaining a new string of numbers, which is the ciphertext. The plaintext is the unencrypted numbers we want to send. The ciphertext can also be decrypted back to plaintext using the key through mathematical calculations. This process is called encryption and decryption. Therefore, the encryption key + synchronized counter value, processed through the KeeLoQ algorithm, generates the ciphertext. The term “rolling” comes from the continuously updating synchronized counter value, while the encryption key is generated from the sequence number and manufacturer code combined, with the generated information stored in the chip’s memory area.

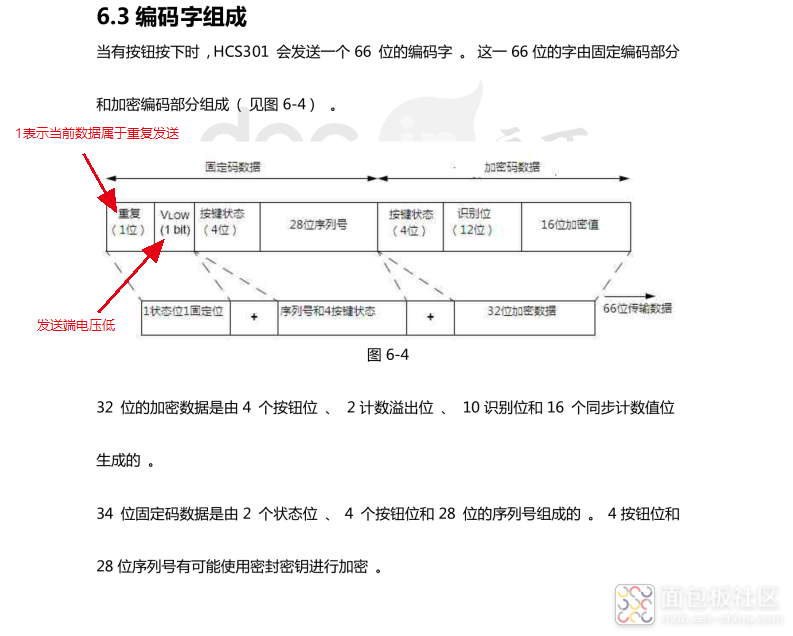
First, let’s look at the internal storage structure of the sending chip.
Content stored in the memory

Actual data format sent

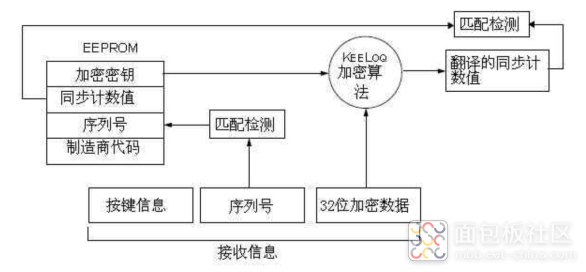
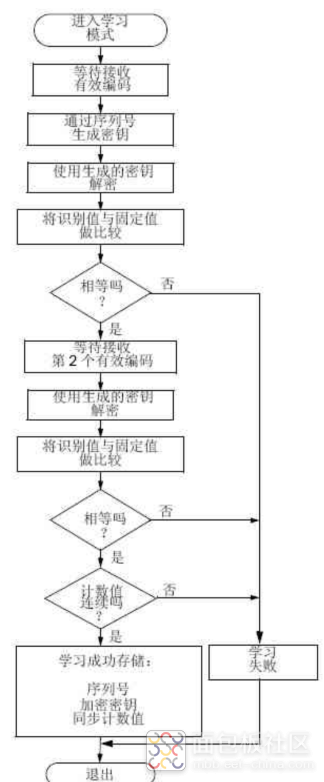
Learning Process
The learning process: the controlled end generally has a setting button. When the button is long-pressed, it clears the already paired remote controls, and a short press adds a remote control. The process of adding a remote control is called the learning process. When the controlled end enters the learning process, the remote control sends its data, which includes “32 bytes of ciphertext + 2 bits of status + 4 button states + 28 bits of sequence number”. The ciphertext is generated from 4 button states + identification bit + synchronized counter value + overflow bit. Both the ciphertext and plaintext contain sequence number information. The received plaintext sequence number is used to generate a key using the same encryption algorithm and manufacturer number as the remote control. The ciphertext is then decrypted, and the decrypted data is compared to see if the sequence number matches. If it matches, the sequence number is stored in the key.
Therefore, the controlled end and the key must first have the same encryption algorithm and manufacturer number. In summary, if a rolling code key is lost, one can only buy a key from the same manufacturer; otherwise, both must be replaced. This is because it is very secure.
Finally, looking back at the product features mentioned at the beginning of the MicroChip specifications, it becomes clearer.

 Breadboard Community [Original Disassembly] Collection
Breadboard Community [Original Disassembly] Collection
Disassembling a bear egg beater, what is the secret of the internal motor?
Disassembling a TV remote control, let’s see how small appliances control costs.
Disassembled a USB charger that costs 3 yuan with free shipping: learned two points from a simple circuit!
Disassembling an electric mosquito swatter, the board is all through-hole components! (With circuit schematic analysis)
Disassembling a Midea electric oven, do you know how it achieves temperature control?
Disassembled a scrap CNC power supply, drawing a schematic for everyone’s reference.
[Disassembly] A remote control for an underwater drone costing thousands only costs 30 yuan; let’s see what’s inside.
Disassembling a “tens of thousands of yuan” Phicomm K2T router.
👇 For more DIY circuit disassemblies, please follow the Breadboard Community WeChat account.