Author: Gentle But Ruthless Character
Original Link: http://blog.csdn.net/qq_25827845/article/details/66975129
Please indicate the source when reprinting
TCP/IP Protocol
TCP/IP is not a single protocol, but a general term for a protocol suite. It includes the IP protocol, ICMP protocol, and TCP protocol.
Here are some key points to note:
-
Internet Address: This is the IP address, generally consisting of the network number + subnet number + host number
-
Domain Name System: Simply put, it is a database that can convert host names into IP addresses
-
RFC: The standard documents for TCP/IP protocols
-
Port Number: A logical number that marks the IP packet
-
Socket: Application programming interface
Working characteristics of the Data Link Layer:
-
Sending and receiving IP datagrams for the IP module
-
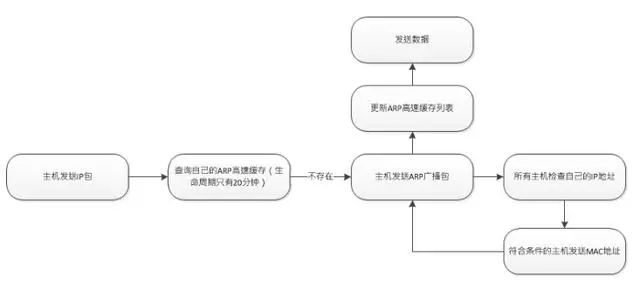
Sending ARP requests and receiving ARP replies for the ARP module (ARP: Address Resolution Protocol, which converts IP addresses into MAC addresses)
-
Sending RARP requests and receiving RARP replies
Next, let’s understand the working process of TCP/IP:
The Data Link Layer obtains data transmission information from ARP, and then obtains specific data information from IP
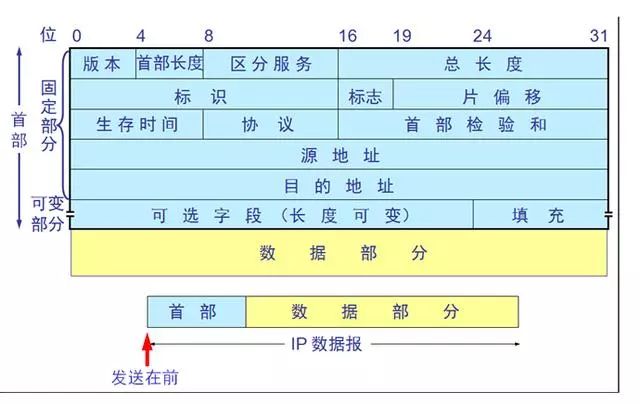
IP Protocol
More C/C++ learning materials, please message me “code” to obtain
The most important field in the IP protocol header is the TTL (Time To Live) field (8 bits), which specifies the maximum number of network segments that the packet can traverse before being discarded.
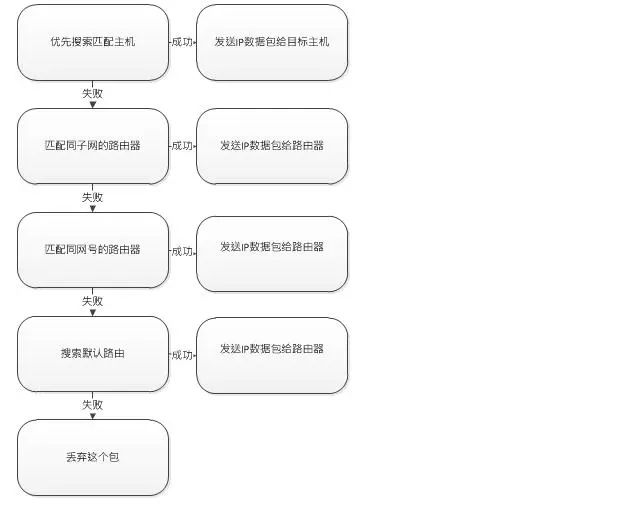
IP Routing
More C/C++ learning materials, please message me “code” to obtain
Working Principle of ARP Protocol
More C/C++ learning materials, please message me “code” to obtain
ICMP Protocol (Internet Control Message Protocol)
Transmits error messages when IP packets cannot be delivered to the host
Query Messages
-
Ping query: Check if the host is reachable by calculating the interval time and the number of packets sent
-
Subnet Mask
-
Timestamp: Obtain the current time
Error Messages
Conditions where no error messages are generated:
-
ICMP error messages do not generate error messages
-
Source address is zero address, loopback address, broadcast address, multicast address
IP Router Selection Protocol
Static Routing

More C/C++ learning materials, please message me “code” to obtain
Static Routing Selection
-
Configure interfaces to generate routing table entries by default, or manually add entries using route add
-
ICMP messages (ICMP redirect messages) update entries
-
Dynamic routing selection (only used between routers)
RIP (Routing Information Protocol)
A distributed distance vector-based routing selection protocol (records the distance from the router to each destination network)
Responsibilities of the router:
-
Send RIP request messages to each known router, requesting the complete routing table
-
If it accepts the request, it will provide its routing table to the requester; if not, it will process the IP request table entry (its own part + hops / missing part + 16)
-
Accept the response and update the routing table
-
Regularly update the routing table (generally every 30 seconds, which is considered too frequent~)
OSPF (Open Shortest Path First Protocol)
A distributed link-state protocol (network with interfaces on both routers)
-
When the link state changes, use a reliable flooding method to send information to all routers (link states of all neighboring routers)
-
Ultimately, a complete network topology diagram will be established
TCP/IP’s Three-Way Handshake and Four-Way Teardown
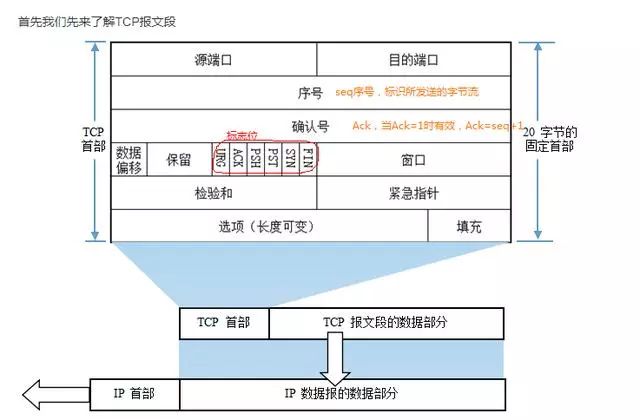
First, let’s understand the TCP segment
More C/C++ learning materials, please message me “code” to obtain
Important flags are also marked in the diagram, focus on understanding the flag bits
ACK: Acknowledges that the sequence number is valid
RST: Resets the connection
SYN: Initiates a new connection
FIN: Releases a connection
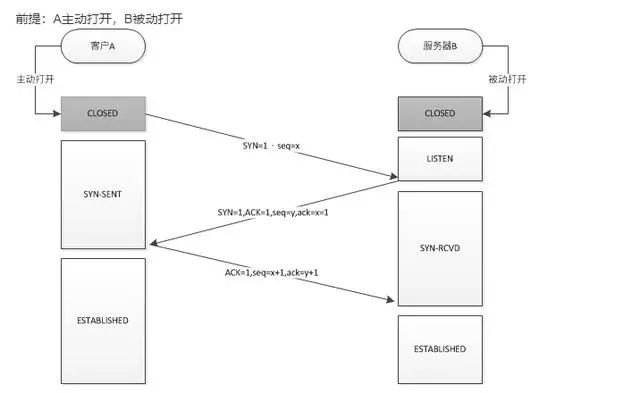
Process of the Three-Way Handshake (Client A, Server B)
Precondition: A actively opens, B passively opens
More C/C++ learning materials, please message me “code” to obtain
-
Before establishing a connection, B first creates TCB (Transmission Control Block) and prepares to accept connection requests from the client process, in LISTEN (Listening) state
-
A first creates TCB, then sends a connection request to B, setting SYN to 1, while selecting the initial sequence number seq=x, and enters SYN-SEND (Synchronized Sent) state
-
B receives the connection request and sends an acknowledgment to A, setting SYN to 1, ACK to 1, while generating an acknowledgment number ack=x+1. It also randomly selects the initial sequence number seq=y, entering SYN-RCVD (Synchronized Received) state
-
A receives the acknowledgment of the connection request, sets ACK to 1, acknowledgment number ack=y+1, seq=x+1, and enters the ESTABLISHED (Connection Established) state. It sends an acknowledgment of the connection to B, and finally B also enters the ESTABLISHED state.
In simple terms:
-
When establishing a connection, the client sends a SYN packet (SYN=i) to the server and enters SYN-SEND state, waiting for server acknowledgment
-
The server must acknowledge the client’s SYN (ack=i+1) and also send a SYN packet (SYN=k), that is, a SYN+ACK packet, at this point the server enters SYN-RECV state
-
The client receives the server’s SYN+ACK packet and sends an acknowledgment ACK (ack=k+1) back to the server, after this packet is sent, both client and server enter the ESTABLISHED state, completing the three-way handshake
Here we insert a knowledge point about SYN attacks. So what is a SYN attack? What are the conditions for its occurrence? How to prevent it?
In the three-way handshake process, the TCP connection that the server sends SYN-ACK to before receiving the client’s ACK is called a half-open connection. At this point, the server is in SYN_RCVD state. When it receives the ACK, the server transitions to ESTABLISHED state. A SYN attack occurs when the client forges a large number of nonexistent IP addresses in a short period and continuously sends SYN packets to the server. The server replies with acknowledgment packets and waits for the client’s confirmation. Since the source addresses are nonexistent, the server needs to continuously retransmit until it times out. These forged SYN packets will occupy the unconnected queue, causing normal SYN requests to be dropped due to a full queue, leading to network congestion or even system failure. SYN attacks are a typical DDOS attack. The method of detecting SYN attacks is very simple: if there are many half-open connections on the server and the source IP addresses are random, it can be concluded that a SYN attack has occurred. The following command can be used to make it evident:
#netstat -nap | grep SYN_RECV
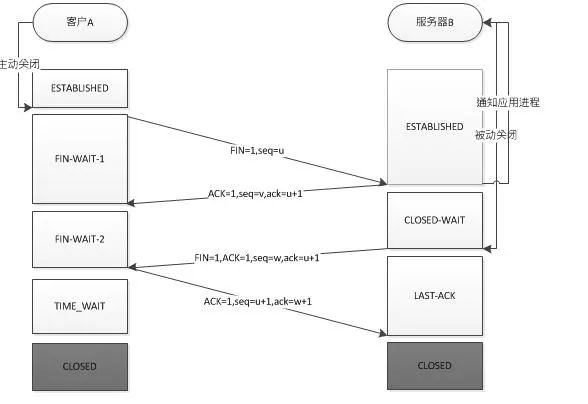
Process of the Four-Way Teardown (Client A, Server B)
Since TCP connections are full-duplex, each direction must be closed separately. This principle means that when one party completes its data sending task, it sends a FIN to terminate the link in that direction. Receiving a FIN only means that there is no data flow in that direction; it does not mean that no data can be sent on this TCP connection until that direction also sends a FIN. The first party to close will execute an active close, while the other party will execute a passive close.
Precondition: A actively closes, B passively closes
More C/C++ learning materials, please message me “code” to obtain
Some may wonder why there are three-way handshakes when connecting, but four-way teardowns when disconnecting?
This is because when the server is in LISTEN state and receives a SYN packet for a connection request, it sends an ACK and SYN in one packet to the client. However, when closing the connection, receiving the other party’s FIN packet only indicates that the other party will not send data anymore, but it can still receive data. The local side may not have sent all data to the other party, so it can either close immediately or send some data to the other party before sending a FIN packet to indicate agreement to close the connection. Therefore, the local side’s ACK and FIN are generally sent separately.
-
A sends a FIN to close the data transmission from A to B, and enters FIN_WAIT_1 state.
-
B receives the FIN and sends an ACK to A, with the acknowledgment number being the received number +1 (similar to SYN, one FIN occupies one sequence number), and B enters CLOSE_WAIT state.
-
B sends a FIN to close the data transmission from B to A, and B enters LAST_ACK state.
-
A receives the FIN, enters TIME_WAIT state, and then sends an ACK to B, with the acknowledgment number set to the received number +1, and B enters CLOSED state, completing the four-way teardown.
In simple terms:
-
Client A sends a FIN to close the data transmission from client A to server B (Segment 4).
-
Server B receives this FIN and sends back an ACK, with the acknowledgment number being the received number +1 (Segment 5). Like SYN, one FIN occupies one sequence number.
-
Server B closes the connection with client A and sends a FIN to client A (Segment 6).
-
Client A sends back an ACK message of acknowledgment, setting the acknowledgment number to the received number +1 (Segment 7).
A does not immediately release TCP after entering the TIME-WAIT state. It must wait for the time set by the waiting timer of 2MSL (Maximum Segment Lifetime) before entering the CLOSED state. Why?
-
To ensure that the last ACK packet sent by A can reach B
-
To prevent “expired connection request segments” from appearing in this connection
OK~ Doesn’t it feel very difficult? Let’s put it in a more “humanized” way:
Three-Way Handshake Process
-
The client sends a request “Open the door, I want to come in” to the server
-
The server replies “Come in, I will open the door for you” to the client
-
The client politely replies “Thank you, I am coming in” to the server
Four-Way Teardown Process
-
The client sends “It’s getting late, I am leaving” to the server, waiting for the server to see him off
-
The server hears this and replies “I understand, I will see you off” to the client, waiting for the client to leave
-
After the server closes the door, it sends “I have closed the door” to the client, then waits for the client to leave (Oh my~ so pretentious)
-
The client replies “I understand, I am leaving now,” and then leaves by himself
OK, let’s stop here.
1. Shenzhen StationRT-Thread Salon: In addition to the exciting theme, this workshop’s content is BLE: How Bluetooth Real-Time Switches Transmission Speed (Based on RT-Thread and NRF52840), with the board type being Nordic’s official NRF52840
Please long press the following QR code to register

2. Reply with [Wildfire RT-Thread], to download the electronic version of “RT-Thread Kernel Implementation and Application Development Practical Guide – Based on STM32” for free
You can add WeChat 13924608367 as a friend, indicating: Company + Name, to be added to the RT-Thread official WeChat group

RT-Thread
Making the development of IoT terminals simple and fast, maximizing the value of chips. GPLv2+ protocol, can be used for free in commercial products.
Long press the QR code to follow us
👇 Click to enter the developer community