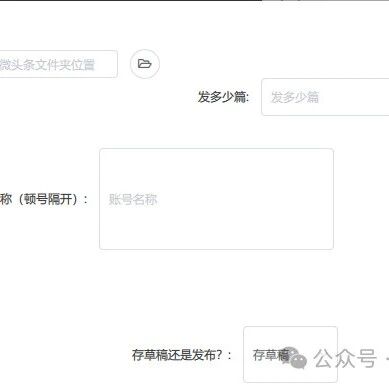
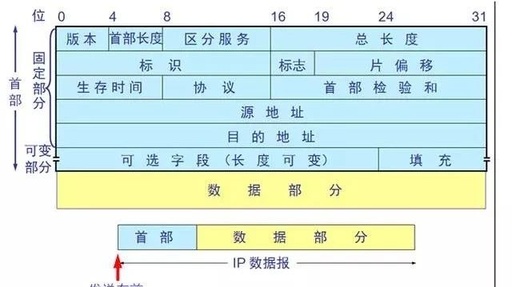
Enterprise Automation Solutions – RPA
View the historical selected articles below Major Release – Basic Guide to Automation Framework PDFv1.1Big Data Testing Processes, Strategies, and Challenges The principles of testing frameworks, the cornerstone of successful construction 10 tips you should know before starting automated testing In automated testing, the tools are not the most important What is RPA? RPA stands … Read more