1. Introduction to TCP/IP
The IP protocol is the network layer, the TCP protocol is the transport layer, the HTTP protocol is the application layer, and socket is the code encapsulation and application of the TCP/IP protocol.
TCP/IP mainly addresses how data is transmitted over the network, while HTTP mainly deals with how to package data.
The TCP/IP protocol is used for data transmission, and application layer protocols make the transmitted data meaningful. There are many application layer protocols, such as HTTP, FTP, TELNET, etc., and you can also define your own application layer protocols.
For example, web pages use the HTTP protocol to encapsulate HTTP text information, and then use TCP/IP as the transport layer protocol to send it to the browser.
2. Introduction to Socket
Socket is not a protocol, but rather an interface (API) that can be called. It is through Socket that we can use the TCP/IP protocol.
Socket is not necessarily linked to the TCP/IP protocol. When designing the Socket programming interface, it was hoped that it could also adapt to other network protocols. Therefore, the emergence of Socket simply makes it more convenient for programmers to use the TCP/IP protocol stack, abstracting the TCP/IP protocol, forming some of the basic function interfaces we know, such as create, listen, connect, accept, send, read, and write, etc.
The TCP/IP protocol is just a protocol; it must be specifically implemented and provide external operation interfaces, which is the Socket programming interface. Socket itself is not considered a protocol; as mentioned above, it simply provides an interface for programming with TCP or UDP.
3. Introduction to TCP Three-Way Handshake
First handshake: The client sends a packet to the server and waits for the server to confirm;
Second handshake: The server receives and confirms the client’s data packet, and also sends a data packet back to the client;
Third handshake: The client receives the server’s data packet and sends a confirmation packet to the server. Once this packet is sent, the three-way handshake is complete.
Here’s a vivid metaphor: I (the client) sent you (the server) an email (this is the first handshake), but I don’t know if you received it, so you sent me a reply saying “I have received it” (this is the second handshake). I received your email, but you don’t know whether I actually received your email, so you are unsure if I know that “you have received it.” Therefore, I have to send another email to let you know that I received the email (this is the third handshake).
Thus, it can be confirmed that communication between the two parties is normal.
The packets transmitted during the handshake do not contain data, and only after the three-way handshake is completed do the client and server officially start transmitting data.
In an ideal state, once a TCP connection is established, it will be maintained until either party actively closes the connection.
When disconnecting, both the server and the client can actively initiate the request to disconnect the TCP connection, and the disconnection process requires “four-way handshake.”
4. Steps to Establish Socket Network Connection
Establishing a Socket connection requires at least a pair of sockets, one running on the client side, called ClientSocket, and the other running on the server side, called ServerSocket.
The connection process between sockets is divided into three steps: server listening, client requesting, and connection confirmation.
1. Server Listening: The server side monitors the network status in real-time, waiting for connection requests from clients.
2. Client Request: The client’s socket initiates a connection request, targeting the server’s socket. The client socket must specify the address and port number of the server socket, and then it sends a connection request to the server socket.
3. Connection Confirmation: When the server socket detects a request from the client socket, it establishes a new thread and sends the description of the server socket to the client. Once the client confirms this description, the connection is officially established, while the server socket continues to listen for other clients’ connection requests.
5. Differences Between TCP and UDP
TCP is connection-oriented. Although the insecure and unstable characteristics of the network determine that no number of handshakes can guarantee the reliability of the connection, the three-way handshake at a minimum greatly ensures connection reliability;
On the other hand, UDP does not establish a connection before transmitting data, nor does it send confirmation signals for received data. The sender does not know whether the data will be received correctly, nor does it need to retransmit. UDP is a connectionless and unreliable data transmission protocol.
Therefore, UDP has less overhead, a higher data transmission rate, and better real-time performance.
Thus, file transfers using the TCP transmission protocol are slower than those using UDP, but this does not mean that QQ communication is insecure, as programmers can manually verify the receipt of UDP data packets, such as numbering each data packet sent and having the receiver verify it.
6. Deep Dive into TCP/IP
1. TCP/IP Data Format
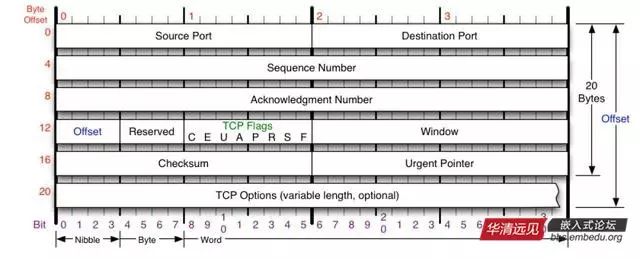
For everyone’s viewing, here is the image translated into Chinese:
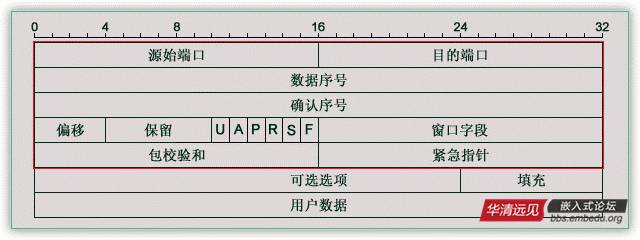
Meaning of each field:
Source Port (源端口) and Destination Port (目的端口): occupy 16 bits each, used to distinguish different processes in the host, while the IP address is used to distinguish different hosts. The source port number and destination port number, combined with the source IP address and destination IP address in the IP header, can uniquely determine a TCP connection.
Sequence Number (数据序号): used to identify the byte stream sent from TCP sender to TCP receiver, indicating the sequence number of the first data byte in this segment; mainly used to solve the problem of network out-of-order delivery.
Acknowledgment Number (确认序号): 32 bits, which contains the next expected sequence number that the sending side wants to receive. Therefore, the acknowledgment number should be the last successfully received data byte’s sequence number plus 1. However, this acknowledgment sequence number field is only valid when the ACK flag in the flag field (described below) is set to 1. It is mainly used to solve the problem of not losing packets;
Offset (偏移): gives the number of 32-bit words in the header. This value is needed because the length of optional fields is variable. This field occupies 4 bits (can represent up to 15 32-bit words, i.e., 4*15=60 bytes of header length), so TCP can have a maximum of 60 bytes of header. However, without optional fields, the normal length is 20 bytes;
TCP Flags: There are 6 flag bits in the TCP header, of which multiple can be set to 1 simultaneously, mainly used to control the TCP state machine, namely URG, ACK, PSH, RST, SYN, FIN. The meaning of each flag is as follows:
URG: This flag indicates that the urgent pointer field of the TCP packet (which will be discussed shortly) is valid, used to ensure that the TCP connection is not interrupted and urges intermediate devices to process this data as soon as possible;
ACK: This flag indicates that the acknowledgment field is valid, meaning that the previously mentioned TCP acknowledgment number will be included in the TCP packet; it has two values: 0 and 1, where 1 indicates the acknowledgment field is valid, and 0 indicates otherwise;
PSH: This flag indicates a Push operation. It means that once the data packet arrives at the receiving end, it is immediately delivered to the application program instead of queuing in the buffer;
RST: This flag indicates a connection reset request. It is used to reset erroneous connections and is also used to refuse erroneous and illegal packets;
SYN: Indicates synchronization sequence numbers, used to establish connections. The SYN flag and ACK flag are used in conjunction; when a connection request is made, SYN=1, ACK=0; when the connection is responded to, SYN=1, ACK=1; this flag’s packet is often used for port scanning. The scanner sends a packet with only SYN, and if the other host responds with a packet, it indicates that this host has this port; however, since this scanning method only performs the first handshake of the TCP three-way handshake, the success of this scanning indicates that the scanned machine is not very secure. A secure host will enforce a strict connection to perform the TCP three-way handshake;
FIN: Indicates that the sender has reached the end of the data, meaning that the data transmission between both parties is complete. After sending the FIN flag TCP packet, the connection will be closed. This flag’s packet is also often used for port scanning.
Window: Window size, also known as sliding window, used for flow control; this is a complex issue.
2. TCP/IP Three-Way Handshake
The TCP protocol can provide a reliable connection because of the three-way handshake. The purpose of the three-way handshake is to synchronize the sequence numbers and acknowledgment numbers of both parties and exchange TCP window size information.
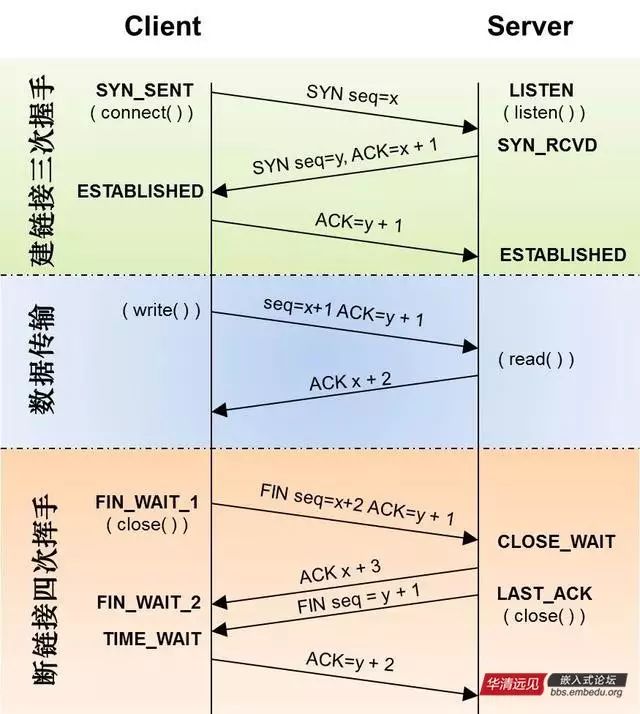
Let’s briefly explain the seq in the above image: Sequence Number (数据序号). SYN: indicates synchronization sequence number. ACK: is not a flag in TCP Flags, but refers to Acknowledgment Number (确认序号).
First handshake: The client sends a connection request segment, setting SYN to 1 and Sequence Number (数据序号) to x; then, the client enters SYN_SEND state, waiting for the server’s confirmation;
Second handshake: The server receives the client’s SYN segment, confirms this SYN segment, sets the Acknowledgment Number (确认序号) to x+1 (Sequence Number+1); at the same time, it sends its own SYN request, setting SYN to 1 and Sequence Number to y; the server puts all this information into a segment (i.e., SYN+ACK segment) and sends it to the client. At this point, the server enters SYN_RECV state;
Third handshake: The client receives the server’s SYN+ACK segment. It then sets the Acknowledgment Number to y+1 and sends an ACK segment to the server. Once this segment is sent, both the client and server enter ESTABLISHED state, completing the TCP three-way handshake.
Now, if the three-way handshake were changed to a two-way handshake, what problems would arise: an invalid connection request segment suddenly arrives at the server, causing errors. Detailed explanation:
The first connection request segment sent by the client was not lost but was delayed at some network node for a long time, causing it to arrive at the server after the connection was released. Originally, this was an already invalid segment. However, the server mistakenly believes it to be a new connection request from the client when it receives this invalid connection request segment. The server then sends a confirmation segment to the client, agreeing to establish the connection. Assuming that the “three-way handshake” is not used, as long as the server sends a confirmation, a new connection will be established.
Since the client has not sent a connection establishment request, it will not acknowledge the server’s confirmation and will not send data to the server. However, the server thinks that a new transport connection has been established and is waiting for the client to send data. In this way, many resources on the server are wasted. Using the “three-way handshake” prevents the above phenomenon from occurring. For example, in the situation described earlier, the client would not confirm the server’s acknowledgment. The server, not receiving confirmation, knows that the client has not requested to establish a connection.
4. After the three-way handshake, data can be transmitted.Once data transmission is complete, the TCP connection must be disconnected, which is the fourth breakup of TCP.
First breakup: Host 1 (which can be either the client or the server) sets the Sequence Number and Acknowledgment Number, sending a FIN segment to host 2; at this point, host 1 enters FIN_WAIT_1 state; this indicates that host 1 has no data to send to host 2;
Second breakup: Host 2 receives the FIN segment sent by host 1 and replies with an ACK segment, with Acknowledgment Number equal to Sequence Number plus 1; host 1 enters FIN_WAIT_2 state; host 2 tells host 1 that it “agrees” to the close request;
Third breakup: Host 2 sends a FIN segment to host 1, requesting to close the connection, while host 2 enters LAST_ACK state;
Fourth breakup: Host 1 receives the FIN segment sent by host 2 and sends an ACK segment to host 2, after which host 1 enters TIME_WAIT state; once host 2 receives the ACK segment from host 1, it closes the connection; at this point, host 1 waits for 2MSL, and if it still does not receive a reply, it proves that the server has closed normally, and host 1 can also close the connection.
5. Why is the breakup process so complicated?
The TCP protocol is a connection-oriented, reliable, byte-stream-based transport layer communication protocol.
TCP operates in full-duplex mode, meaning that when host 1 sends a FIN segment, it only indicates that host 1 has no data left to send; host 1 informs host 2 that it has completed sending all its data. However, at this point, host 1 can still receive data from host 2; when host 2 returns an ACK segment, it indicates that it knows host 1 has no data to send, but host 2 can still send data to host 1; then, when host 2 also sends a FIN segment, it indicates that host 2 also has no data to send, informing host 1 that it has no data to send, and after that, they both terminate this TCP connection.
6. State changes during the four-way handshake process.
FIN_WAIT_1: In fact, both FIN_WAIT_1 and FIN_WAIT_2 states indicate waiting for the other party’s FIN segment. The difference between these two states is that FIN_WAIT_1 state actually occurs when the socket is in ESTABLISHED state and wants to actively close the connection, sending a FIN segment to the other party, at which point the socket enters FIN_WAIT_1 state. When the other party responds with an ACK segment, it enters FIN_WAIT_2 state. In normal circumstances, regardless of the other party’s situation, it should immediately respond with an ACK segment, so the FIN_WAIT_1 state is generally rare, while the FIN_WAIT_2 state can often be seen using netstat. (Active party)
FIN_WAIT_2: As explained above, this state indicates that the socket is half-connected, meaning one party has requested to close the connection but also informs the other party that it still has some data to send (ACK information), and will close the connection later. (Active party)
CLOSE_WAIT: Indicates waiting for closure. When the other party closes a socket and sends a FIN segment to you, your system will undoubtedly respond with an ACK segment to the other party, at which point it enters CLOSE_WAIT state. Next, you need to consider whether you have any data to send to the other party; if not, you can close this socket and send a FIN segment to the other party, thereby closing the connection. Therefore, while in CLOSE_WAIT state, you need to complete the task of waiting to close the connection. (Passive party)
LAST_ACK: It is the passive closing party waiting for the other party’s ACK segment after sending the FIN segment. Once the ACK segment is received, it can enter the CLOSED state. (Passive party)
TIME_WAIT: Indicates that the FIN segment from the other party has been received and the ACK segment has been sent, and after waiting for 2MSL, it can return to the CLOSED state. If in FIN_WAIT_1 state, it receives a packet with both FIN and ACK flags from the other party, it can directly enter the TIME_WAIT state without going through the FIN_WAIT_2 state. (Active party)
CLOSED: Indicates that the connection has been interrupted.
Click to read the original text: Sign up now to receive a 5 million red envelope, come to Huqing to help youachieveyour high salary dream!
【Weekly Hot ArticlesRecommended】
1.Top ten majors that are easy for science students to find jobs, computer science ranks first!
2.Should computer graduates choose a company or an industry?
3.Four tips for novice programmers
4.Things to consider for fresh graduates’ interviews
5.Interview insights: skills that a programmer with 3 years of experience should have
6.Interviewing an embedded driver engineer: there are techniques to interviews
Follow Huqing Maker Online WeChat public account,
to get more information on smart hardware development.

Long press the QR code to follow me