Skip to content
 Click on the above “China Information Security” to subscribe
■ China Information Security Evaluation Center / Gao Yang, Zheng Dongji
Due to the globally interconnected nature of cyberspace, various cybercrimes targeting individuals and enterprises have surged in recent years, and critical national industrial infrastructure is also facing real threats from hacker organizations, terrorist forces, and state adversaries. The Stuxnet virus that attacked Iran’s nuclear power plant in 2010, the Havex virus that stole industrial data in 2014, and the large-scale power outage in Ukraine due to a cyber attack in 2015 all reveal the vulnerability of national infrastructure in the face of cyber attacks. Therefore, it is crucial to analyze the security threats faced by industrial control systems.
By analyzing the research on relevant domestic and international industrial control standards and the characteristics of industrial control systems, this study defines the threat entities and types within industrial control systems and provides corresponding security strategies as a reference. This is also a way to study security threats within industrial control systems.
Main Forms of Information Security Threats in Industrial Control Systems
In the field of information security, threats are widely understood as dangers posed by threat entities that exploit vulnerabilities. Among them, the threat entity is also known as the threat subject, which refers to entities that can impose adverse actions on assets. In simple terms, the threat subject is the source of the threat. In the information security standard IEC 62443 formulated for industrial control systems, the definition of threats has been extended, specifically stated as:
There exists a situation, capability, behavior, or event that has the potential to damage information security or cause harm. A comparison reveals that in the field of industrial control, the definition of threat causes is more explicit, which can be a situation, capability, behavior, or event; whereas the consequences resulting from threats are not only the destruction of information security assets but may also include production accidents and other harms. Overall, the definition of threats in industrial control systems is an extension and expansion based on traditional information security.
In terms of threat classification, the German BSI’s “IT Baseline Protection Manual” classifies nearly a hundred defined threats into the following five categories:
In the “Information Security Risk Assessment – Exploration and Practice”, there are also corresponding descriptions and analyses of threat classification. Based on the OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) method of threat expression, threats are classified into the following categories:
· Actors who access information systems via the network: This threat is classified as a network-based threat to the organization’s critical assets, which can be intentional or unintentional actions by the actor.
· Actors who approach information systems physically: This threat is classified as a physical threat to the organization’s critical assets, which can also be intentional or unintentional actions by the actor.
· System Issues: This threat is classified as problems within the organization’s information technology systems, including hardware defects, software defects, unavailability of related systems, and failure of critical infrastructure (such as telecommunications and power), like power outages or burst pipes (staff shortages and lack of IT expertise can significantly impact this part).
· Virus and Malware Issues: This has become a significant factor affecting the secure operation of systems.
· Natural Disasters: This threat belongs to issues and situations outside the organization’s scope. This threat category includes natural disasters (such as floods, earthquakes, or storms).
Drawing on the aforementioned threat classifications and combining them with the characteristics of industrial control systems, the security threats in industrial control may manifest in the following forms:
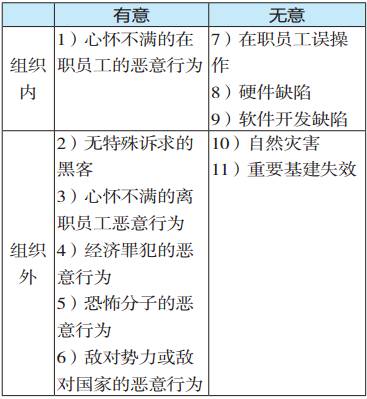
1) Malicious actions by disgruntled employees: They are familiar with the processes and can access various equipment, but their computer skills are average. They wish to conceal their destructive actions.
2) Hackers with no specific demands: They have strong computer skills but find it challenging to directly access various equipment and may not be well-informed about the factory’s situation, and they do not necessarily wish to conceal their destructive actions.
3) Malicious actions by disgruntled former employees: They understand the processes and may not be able to access various equipment but might exploit loopholes to retain network access or direct access to equipment after leaving. Their computer skills are average, and they wish to conceal their destructive actions.
4) Malicious actions by economic criminals: They have clear goals and wish to hijack control systems for economic gain.
5) Malicious actions by terrorists: They have clear goals and wish to hijack control systems to create significant social impact.
6) Malicious actions by hostile forces or countries: They have clear goals, abundant resources, and can execute various attacks.
7) Accidental errors by employees: There may be mistakes in equipment wiring, power switching, and functional operations.
8) Hardware defects: The hardware itself may have weak information security capabilities or may have been pre-installed with backdoors by hostile forces.
9) Software development defects: Problems caused by lax software development practices.
10) Natural disasters: The information system may suffer wiring changes due to lightning strikes, electric shocks, vibrations, etc. Such disasters are highly random, have unclear targets, and unpredictable consequences.
11) Failure of critical infrastructure: Failure of public service supplies such as energy.
For ease of expression and research, these 11 sources of threats (or threat subjects) can be represented in a table based on intentional/unintentional or within/outside the organization:
The Significance of Studying Information Security Threats in Industrial Control Systems
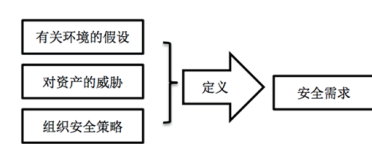
The significance of researching information security threats in industrial control systems mainly lies in: by identifying security threats within industrial control systems, it can help define the security requirements for industrial control. Moreover, whether for setting information security goals for industrial control systems or extracting security requirements, it is necessary to clarify the threats to assets, which serves as one of the key elements in defining information security requirements for industrial control. Clear requirements have already been made in the guidelines for generating protection profiles and security goals (GB/Z 20283).
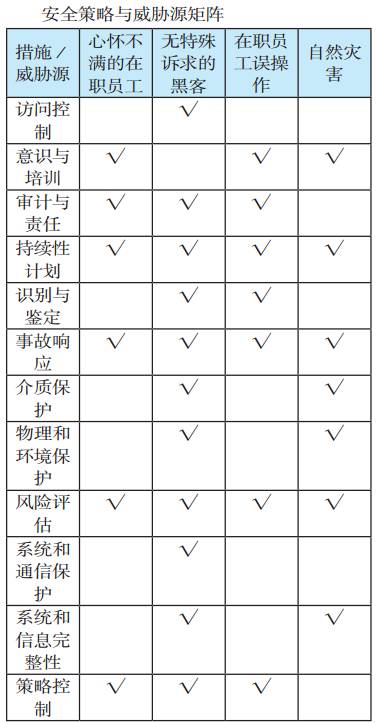
Through the aforementioned series of discussions and studies, the ultimate goal is to strengthen information security in industrial control systems. Based on the 11 threats summarized earlier and in conjunction with NIST-related documents, strategies can be summarized from management, operational, and technical aspects to directly counter the various sources of threats, providing some references and suggestions.
For example, access control can provide mechanisms that allow only authorized users to operate, enhancing the security capabilities of the system, especially at access points and entry points of programs, channels, etc., which can, to some extent, prevent threats from ordinary hackers.
In the context of “Made in China 2025” and “Industry 4.0”, information and network technologies play an increasingly important role in industrial control. Currently, China’s industrial infrastructure will remain in a vulnerable state for a long time, and with the development of “Internet Plus”, the security risks it faces will further increase. Therefore, researching security threats to industrial control systems is not only important but also very meaningful. (This article was published in the 4th issue of “China Information Security” in 2016)
China Information Security
Public Account: chinainfosec
Long press to follow “China Information Security”
Click on the above “China Information Security” to subscribe
■ China Information Security Evaluation Center / Gao Yang, Zheng Dongji
Due to the globally interconnected nature of cyberspace, various cybercrimes targeting individuals and enterprises have surged in recent years, and critical national industrial infrastructure is also facing real threats from hacker organizations, terrorist forces, and state adversaries. The Stuxnet virus that attacked Iran’s nuclear power plant in 2010, the Havex virus that stole industrial data in 2014, and the large-scale power outage in Ukraine due to a cyber attack in 2015 all reveal the vulnerability of national infrastructure in the face of cyber attacks. Therefore, it is crucial to analyze the security threats faced by industrial control systems.
By analyzing the research on relevant domestic and international industrial control standards and the characteristics of industrial control systems, this study defines the threat entities and types within industrial control systems and provides corresponding security strategies as a reference. This is also a way to study security threats within industrial control systems.
Main Forms of Information Security Threats in Industrial Control Systems
In the field of information security, threats are widely understood as dangers posed by threat entities that exploit vulnerabilities. Among them, the threat entity is also known as the threat subject, which refers to entities that can impose adverse actions on assets. In simple terms, the threat subject is the source of the threat. In the information security standard IEC 62443 formulated for industrial control systems, the definition of threats has been extended, specifically stated as:
There exists a situation, capability, behavior, or event that has the potential to damage information security or cause harm. A comparison reveals that in the field of industrial control, the definition of threat causes is more explicit, which can be a situation, capability, behavior, or event; whereas the consequences resulting from threats are not only the destruction of information security assets but may also include production accidents and other harms. Overall, the definition of threats in industrial control systems is an extension and expansion based on traditional information security.
In terms of threat classification, the German BSI’s “IT Baseline Protection Manual” classifies nearly a hundred defined threats into the following five categories:
In the “Information Security Risk Assessment – Exploration and Practice”, there are also corresponding descriptions and analyses of threat classification. Based on the OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) method of threat expression, threats are classified into the following categories:
· Actors who access information systems via the network: This threat is classified as a network-based threat to the organization’s critical assets, which can be intentional or unintentional actions by the actor.
· Actors who approach information systems physically: This threat is classified as a physical threat to the organization’s critical assets, which can also be intentional or unintentional actions by the actor.
· System Issues: This threat is classified as problems within the organization’s information technology systems, including hardware defects, software defects, unavailability of related systems, and failure of critical infrastructure (such as telecommunications and power), like power outages or burst pipes (staff shortages and lack of IT expertise can significantly impact this part).
· Virus and Malware Issues: This has become a significant factor affecting the secure operation of systems.
· Natural Disasters: This threat belongs to issues and situations outside the organization’s scope. This threat category includes natural disasters (such as floods, earthquakes, or storms).
Drawing on the aforementioned threat classifications and combining them with the characteristics of industrial control systems, the security threats in industrial control may manifest in the following forms:
1) Malicious actions by disgruntled employees: They are familiar with the processes and can access various equipment, but their computer skills are average. They wish to conceal their destructive actions.
2) Hackers with no specific demands: They have strong computer skills but find it challenging to directly access various equipment and may not be well-informed about the factory’s situation, and they do not necessarily wish to conceal their destructive actions.
3) Malicious actions by disgruntled former employees: They understand the processes and may not be able to access various equipment but might exploit loopholes to retain network access or direct access to equipment after leaving. Their computer skills are average, and they wish to conceal their destructive actions.
4) Malicious actions by economic criminals: They have clear goals and wish to hijack control systems for economic gain.
5) Malicious actions by terrorists: They have clear goals and wish to hijack control systems to create significant social impact.
6) Malicious actions by hostile forces or countries: They have clear goals, abundant resources, and can execute various attacks.
7) Accidental errors by employees: There may be mistakes in equipment wiring, power switching, and functional operations.
8) Hardware defects: The hardware itself may have weak information security capabilities or may have been pre-installed with backdoors by hostile forces.
9) Software development defects: Problems caused by lax software development practices.
10) Natural disasters: The information system may suffer wiring changes due to lightning strikes, electric shocks, vibrations, etc. Such disasters are highly random, have unclear targets, and unpredictable consequences.
11) Failure of critical infrastructure: Failure of public service supplies such as energy.
For ease of expression and research, these 11 sources of threats (or threat subjects) can be represented in a table based on intentional/unintentional or within/outside the organization:
The Significance of Studying Information Security Threats in Industrial Control Systems
The significance of researching information security threats in industrial control systems mainly lies in: by identifying security threats within industrial control systems, it can help define the security requirements for industrial control. Moreover, whether for setting information security goals for industrial control systems or extracting security requirements, it is necessary to clarify the threats to assets, which serves as one of the key elements in defining information security requirements for industrial control. Clear requirements have already been made in the guidelines for generating protection profiles and security goals (GB/Z 20283).
Through the aforementioned series of discussions and studies, the ultimate goal is to strengthen information security in industrial control systems. Based on the 11 threats summarized earlier and in conjunction with NIST-related documents, strategies can be summarized from management, operational, and technical aspects to directly counter the various sources of threats, providing some references and suggestions.
For example, access control can provide mechanisms that allow only authorized users to operate, enhancing the security capabilities of the system, especially at access points and entry points of programs, channels, etc., which can, to some extent, prevent threats from ordinary hackers.
In the context of “Made in China 2025” and “Industry 4.0”, information and network technologies play an increasingly important role in industrial control. Currently, China’s industrial infrastructure will remain in a vulnerable state for a long time, and with the development of “Internet Plus”, the security risks it faces will further increase. Therefore, researching security threats to industrial control systems is not only important but also very meaningful. (This article was published in the 4th issue of “China Information Security” in 2016)
China Information Security
Public Account: chinainfosec
Long press to follow “China Information Security”