0 1 2 40 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Type | Code | Checksum |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| |Message Body +| |RDNSS Option0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Type | Length | Reserved |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Lifetime |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| |: Addresses of IPv6 Recursive DNS Servers :| |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+typedef struct _NET_BUFFER {.....0x18 ULONG DataLength;0x28 ULONG DataOffset.....} NET_BUFFER, *PNET_BUFFER;PVOID NdisGetDataBuffer(PNET_BUFFER NetBuffer,ULONG BytesNeeded,PVOID Storage,UINT AlignMultiple,UINT AlignOffset);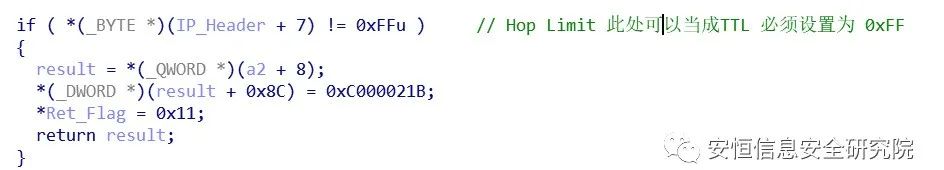
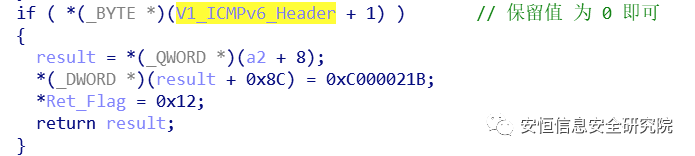
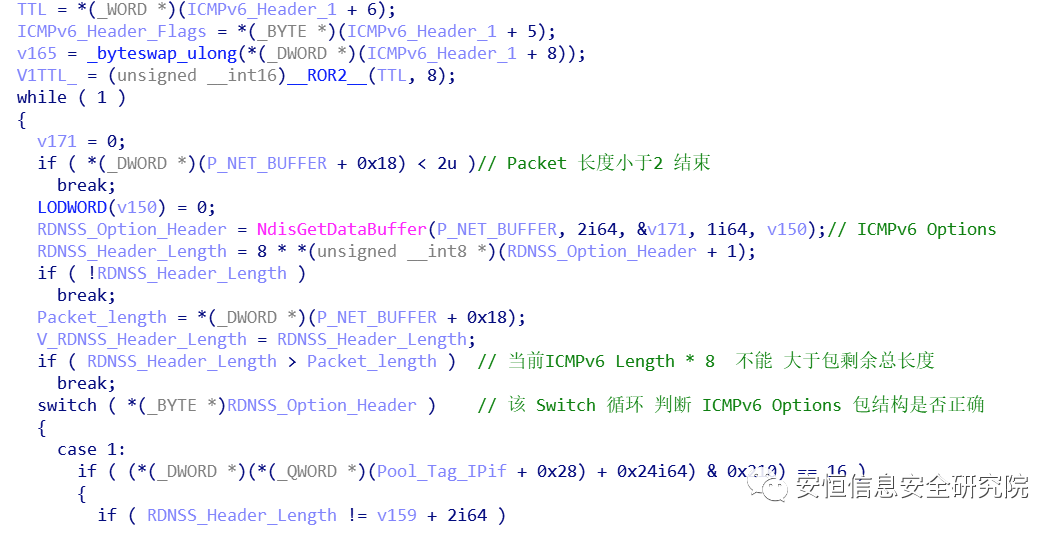
case 0x19: if ( *(_BYTE *)(v12 + 0x194) < 0 && (RDNSS_Header_Length < 0x18u) *v8 = 0x19; break;We only need to set the packet so that Length * 8 > 0x18.
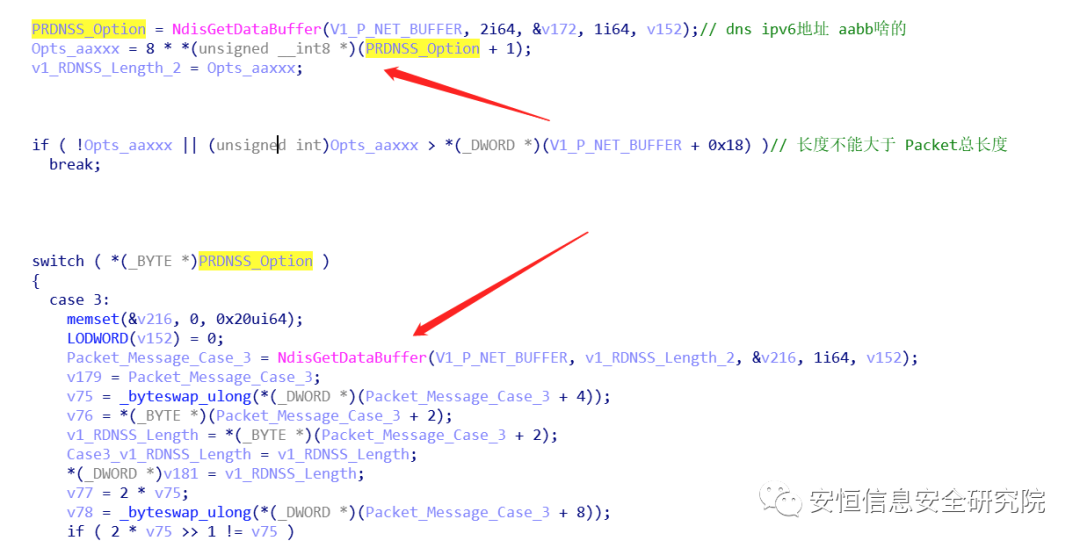
RDNSS Optionscase 0x19:if ( (_BYTE )(v12 + 0x194) < 0 && (RDNSS_Header_Length < 0x18u || ((_BYTE)RDNSS_Header_Length - 8) & 0xF) )*v8 = 0x19;break;