Author | Green Alliance Technology Ge Wu Laboratory Chen Jie
Introduction: In firmware analysis, it is often necessary to locate the firmware’s loading address, especially the memory address where Vxworks or Linux kernel is loaded into memory, which facilitates reverse engineering tools like IDA PRO for correct disassembly and string references. In the following sections, several examples will be combined to introduce how to find the correct firmware loading address.
Data Sheet
In the data sheet of processor chips, the memory layout of the processor is generally described, including various interrupt table addresses, and there are also memory addresses for loading flash data, which is the firmware loading address to be found, as shown below, starting from 0x8000000 where flash data is stored, this address can be set during analysis.
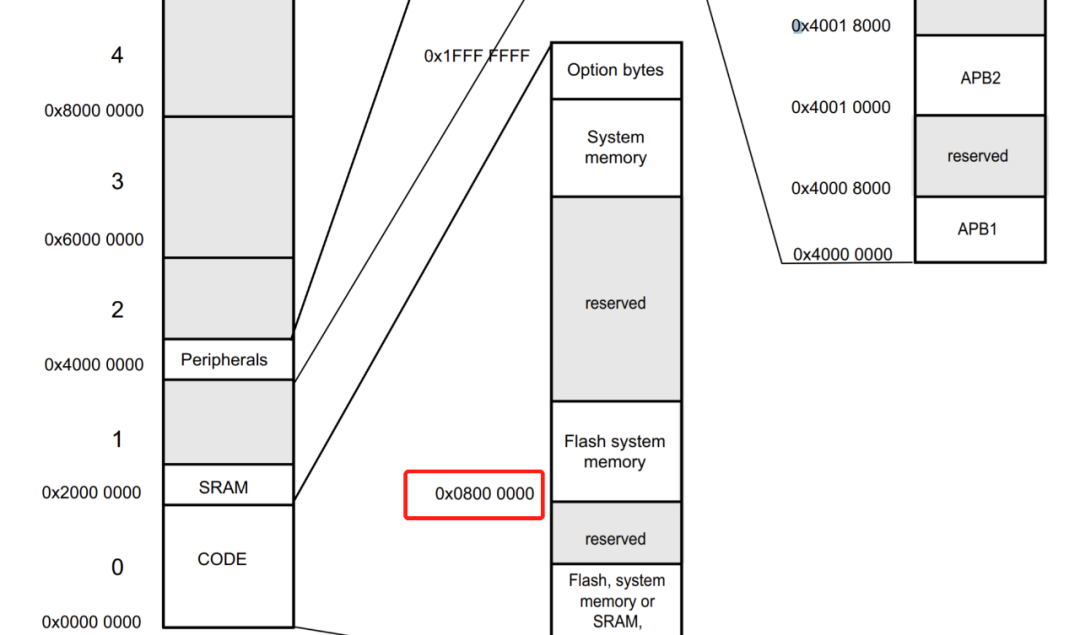
However, the actual situation is often much more complicated; some firmware is not continuous. For example, Linux and U-Boot will load the Linux kernel into memory for execution. Since the Linux kernel is compressed, there is a segment of decompression code at the beginning. Where is the decompressed kernel code placed? These are all things we need to analyze.
Serial Port Information
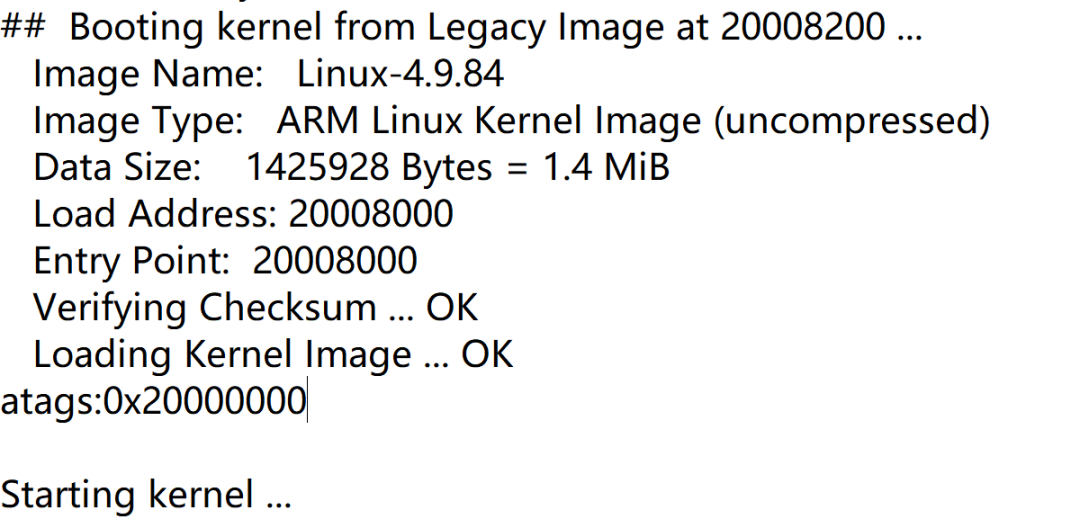
Through UART, sensitive information about firmware startup can generally be obtained, which may include the loading address, as shown below. However, this address, although it is the kernel firmware’s loading address, the kernel is compressed, and it will be decompressed to another memory address. This means that we still need to find the actual firmware loading address.
Firmware Constants
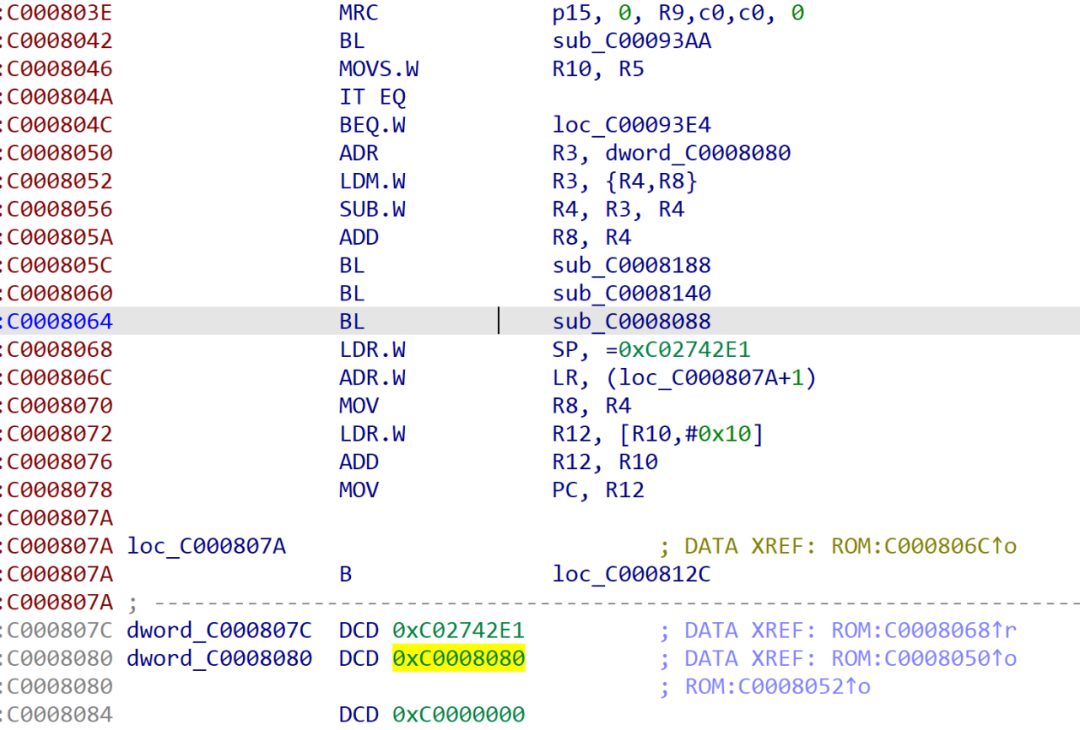
To obtain the decompressed data of the Linux Kernel, you can use binwalk -e kernel.bin to extract the original kernel image. Load it into IDA for analysis. Note that the highlighted area has been marked, 0xC0008080, and it is easy to guess that the actual kernel firmware loading address is 0xC0008000.
Switch Positioning Method
This method has already been shared by many people online, mainly using the switch jump table to determine the firmware loading address. This method is often used in analyzing ARM architecture Vxworks.
1. Search for “switch”:
2. Find a suitable jump table:
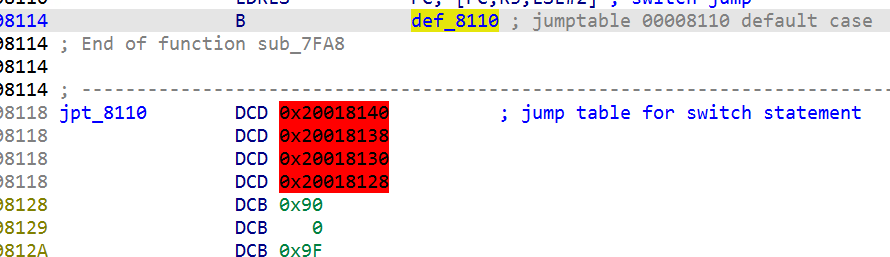
The loading address is: (0x20018140-0x8110) & 0xfffff000 = 0x20010000 (the loading address is generally aligned to 0x1000).
Magic Number Positioning Method
The magic number, i.e., magic number, mainly uses some characteristic numbers to locate related functions, and then finds strings from related functions. By adjusting the address of the string reference, the firmware loading address can be determined. Essentially, it still requires the use of the string reference address.
As shown below, this time the target is a U-Boot, and we need to find the loading address of U-Boot:
Finding Characteristics
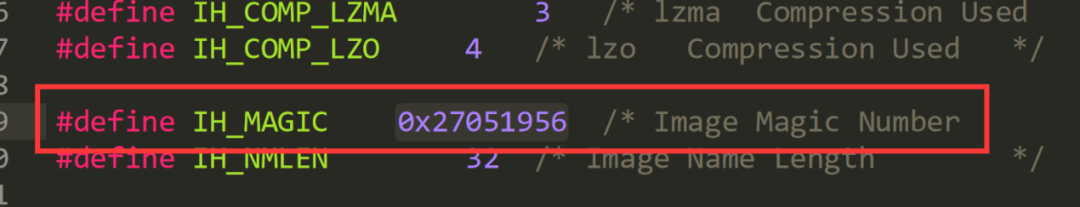
By analyzing the source code, it can be seen that the IH_MAGIC constant value is referenced in many places:
Select a function that references this constant:
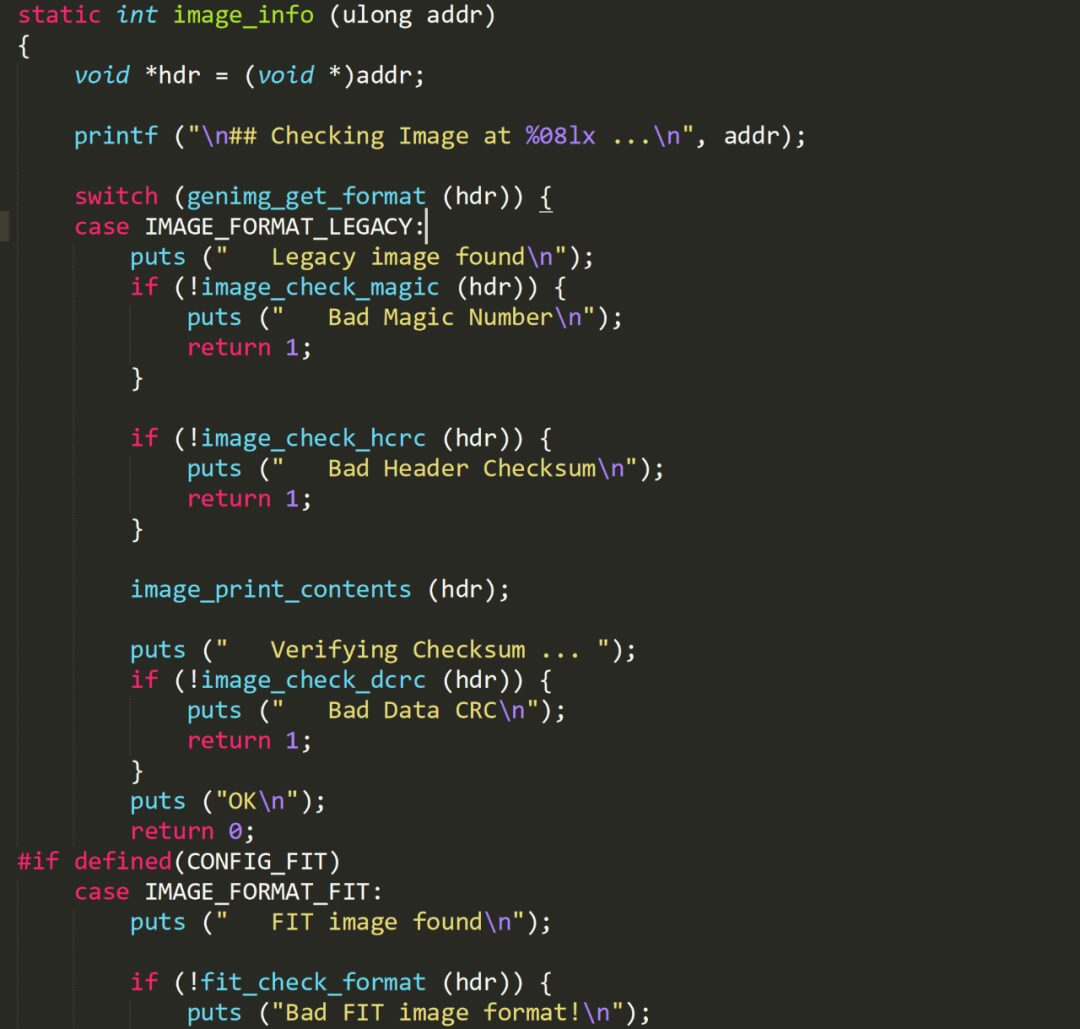
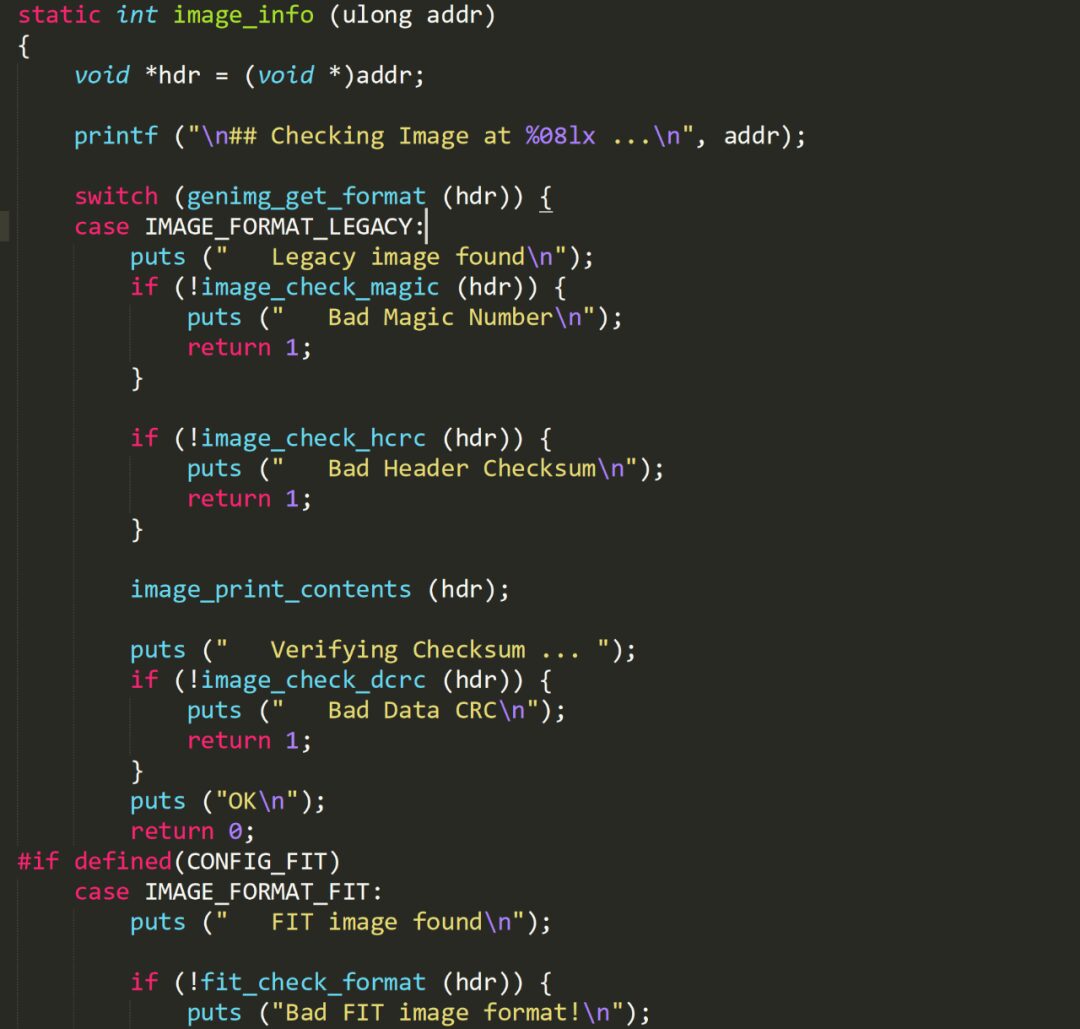
The core idea is to calculate the difference through the string reference address to determine the loading address, using the constant value 0x27051956 to find the above function in the firmware:
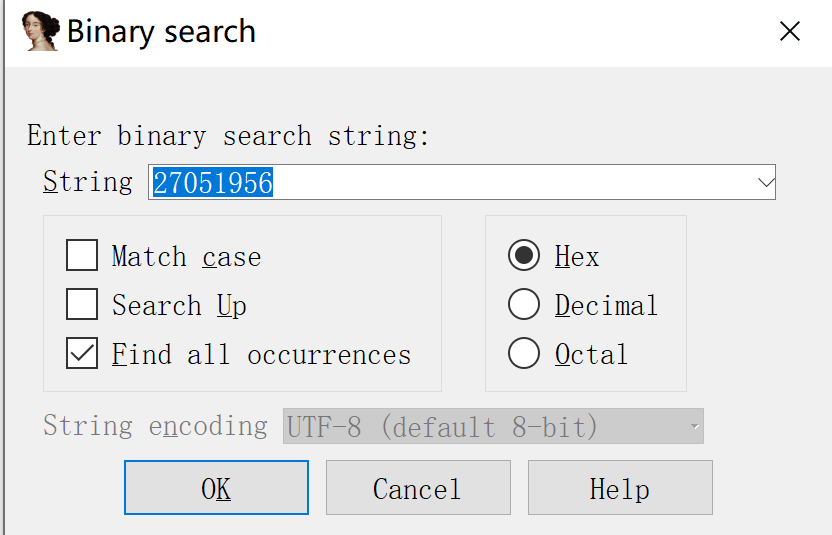
Several reference points were found, not many, so go through them one by one to see which one looks like the function. If there are places that IDA cannot recognize, it should be converted to assembly code using “C”.
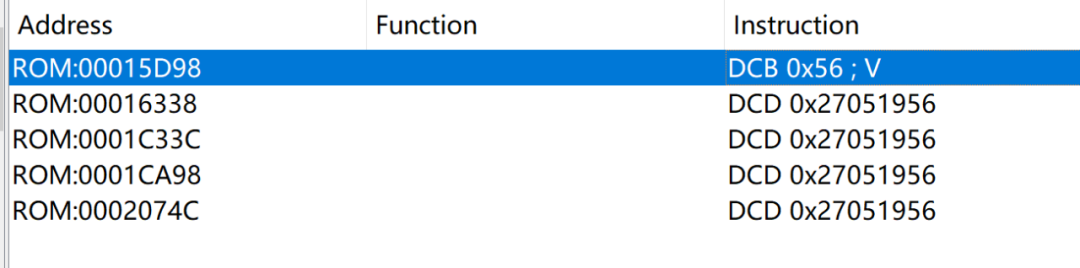
Finally, find this function. From the source code, it can be seen that 0xA082012C is the string reference value for ” Bad Magic Number\n”.
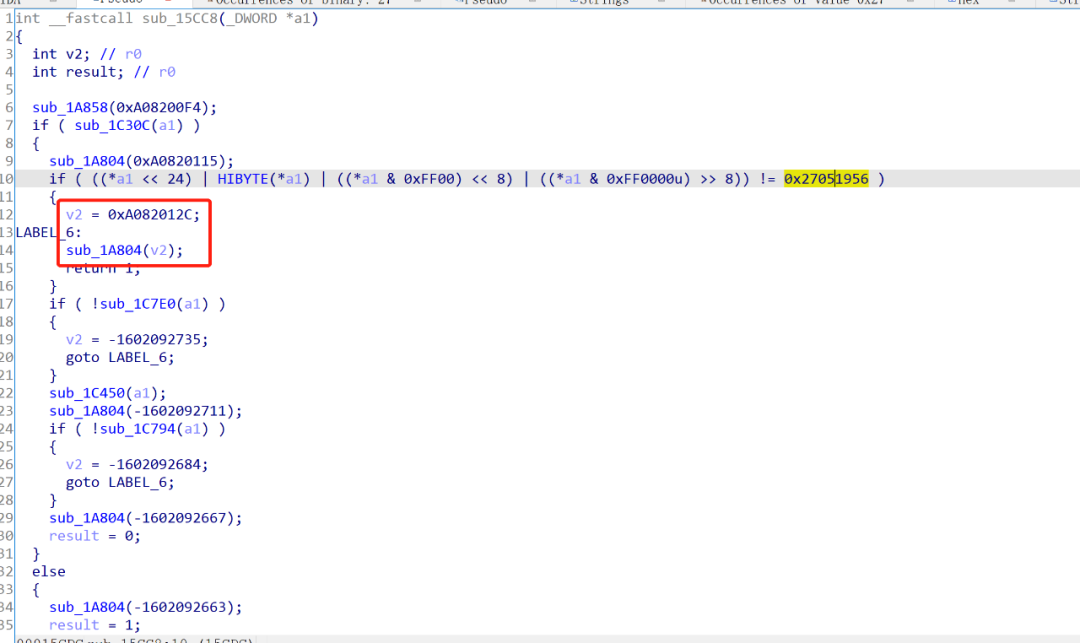
Search for the string ” Bad Magic Number” in the string window, obtaining the file offset address 0x2F12C.
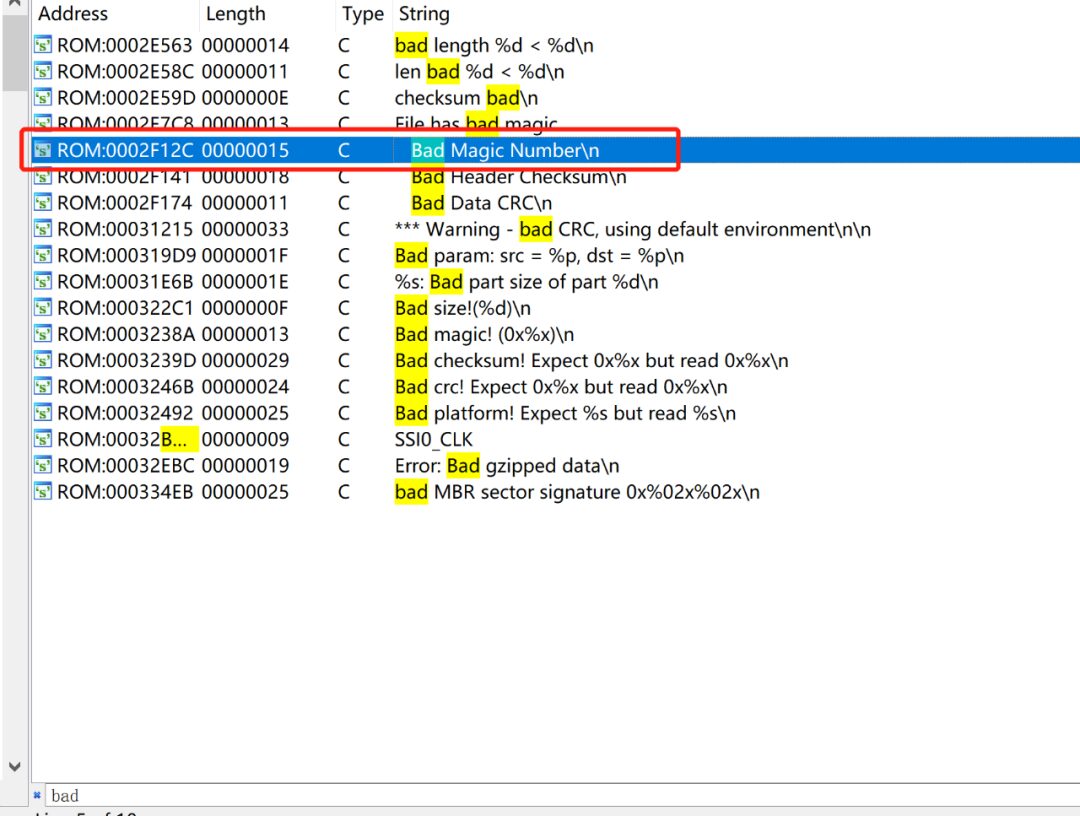
The firmware loading address is: 0xA082012C-0x2F12C=0xA07F1000.
Instruction Positioning Method
The instruction positioning method ultimately still utilizes strings, but instead of using a magic number to find the corresponding string, it uses instructions. As is well known, r0 is the first parameter for ARM passing, and in functions like printf, the first string is often a constant string from the constant area. Therefore, we use this feature to locate the corresponding string and its address by first searching for the instructions that meet the conditions:
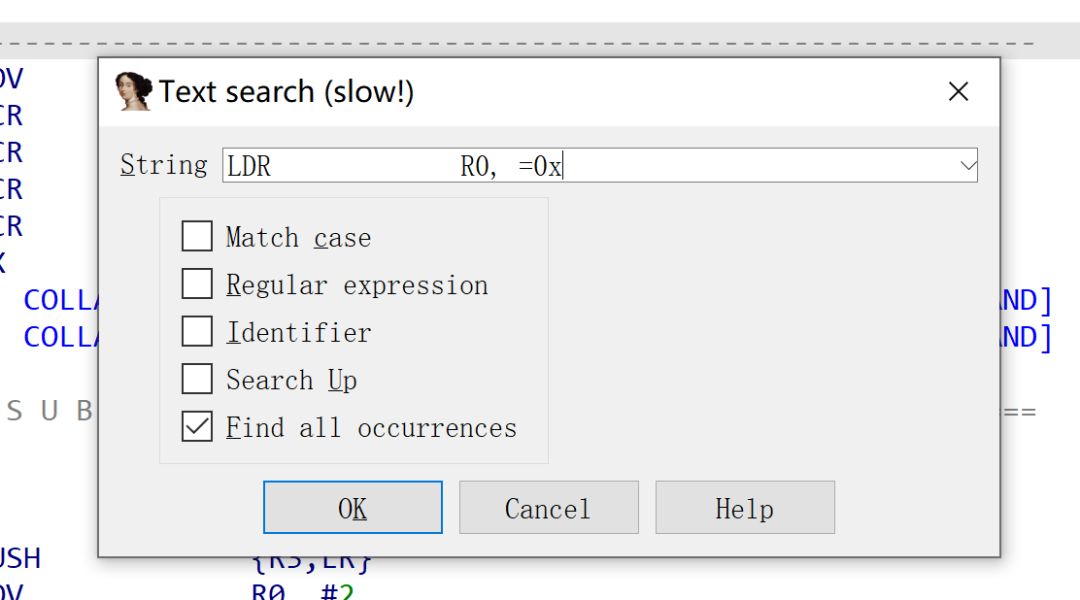
The search results are as follows. Let’s casually find one ” LDR R0, =0x23E1B571″, and we tentatively assume 0x23E1B571 holds a string.
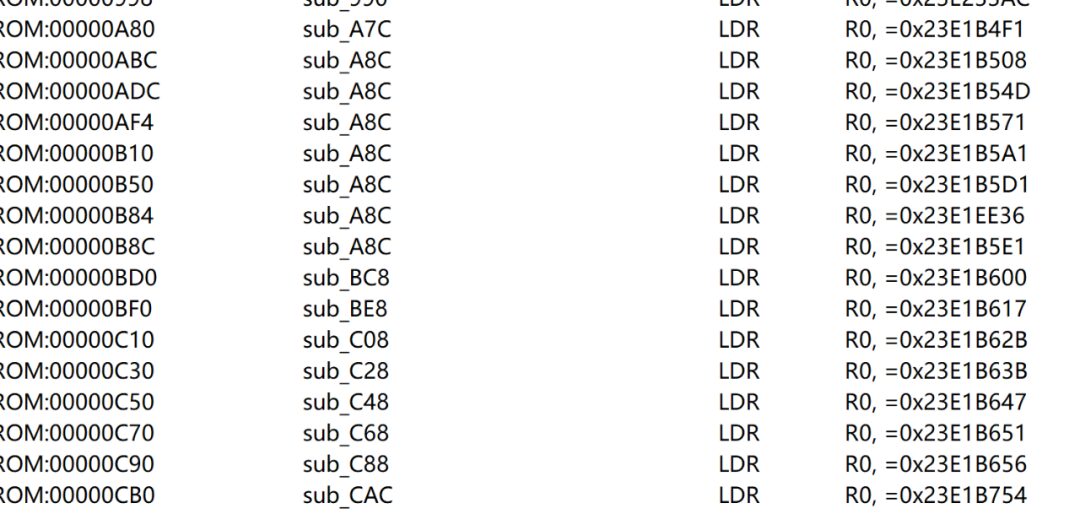
Directly search the last three digits of the address in IDA: 517
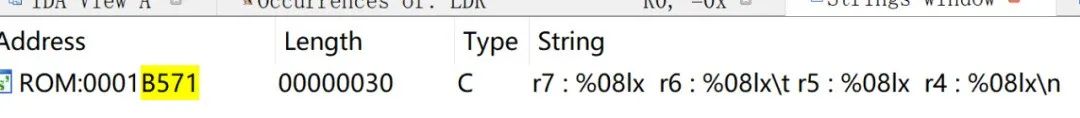 The loading address is very obvious: 0x23E1B571-0x1B571=0x23E00000. In summary, this method is relatively fast, yielding results in about 1 minute, and can be used for ARM, MIPS, PPC to find firmware loading addresses.
The loading address is very obvious: 0x23E1B571-0x1B571=0x23E00000. In summary, this method is relatively fast, yielding results in about 1 minute, and can be used for ARM, MIPS, PPC to find firmware loading addresses.
rbasefind is a very efficient firmware loading address brute-forcing tool developed with Rust, and it is very easy to use. Source code address: https://github.com/sgayou/rbasefind.
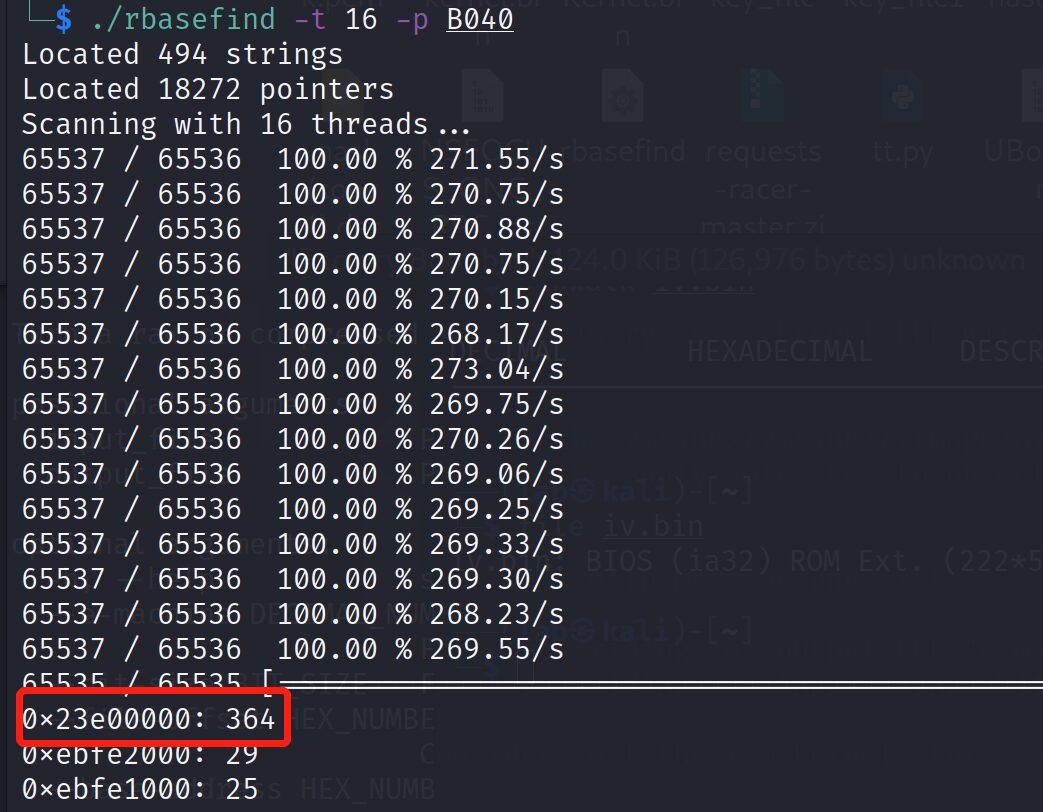
This article briefly introduces various methods and techniques for obtaining firmware loading addresses, including some very quick and efficient manual methods, and tools for automated brute force cracking, hoping to provide some technical inspiration.
Reprint must indicate the source: National Engineering Laboratory for Emergency Technology in Cybersecurity
