Practical Implementation and Development Thoughts of Chaos Engineering at Ping An Bank
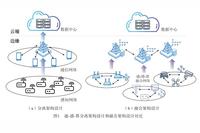
In recent years, with the popularization of new technologies such as distributed system architecture, microservices concepts, and PaaS service components in the financial industry, traditional monolithic business system architectures based on mainframes and storage are rapidly evolving towards distributed system architectures based on cloud foundations (referred to as new system architecture). The new system architecture … Read more