1. Overview
2. Dissemination and Download Trends of IoT Firmware Files
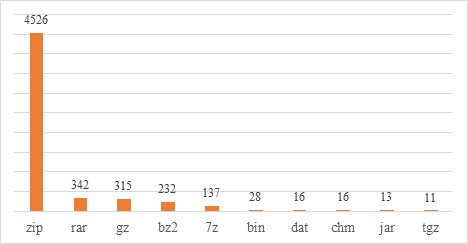
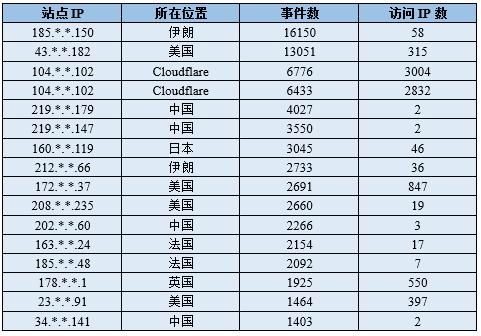
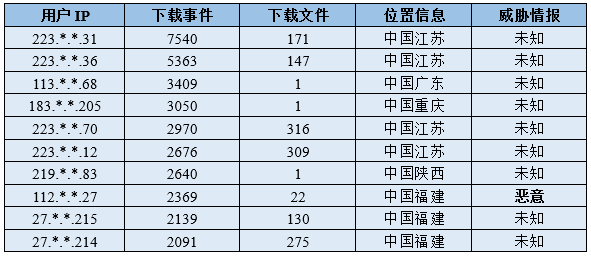
2.2 Monitoring and Analysis of Router Device Firmware Dissemination
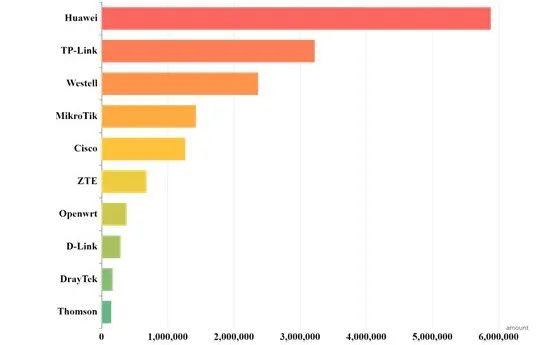


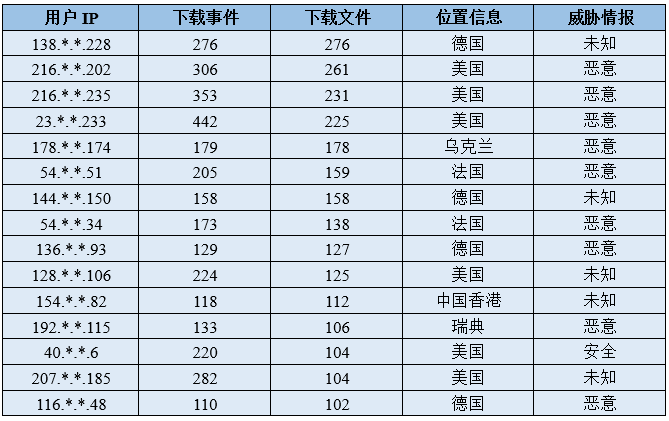
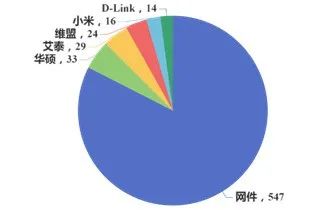
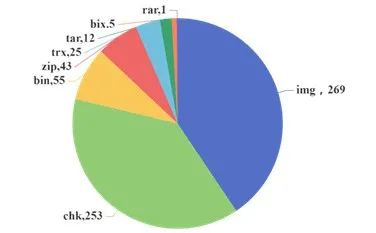




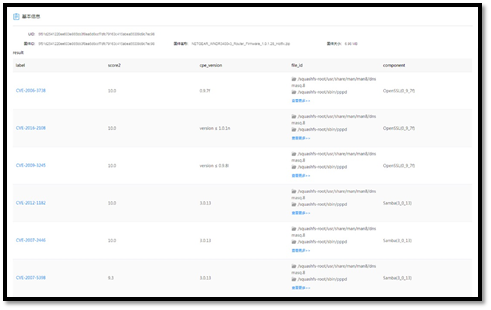
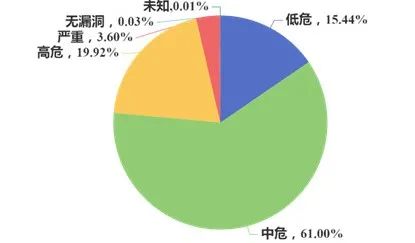
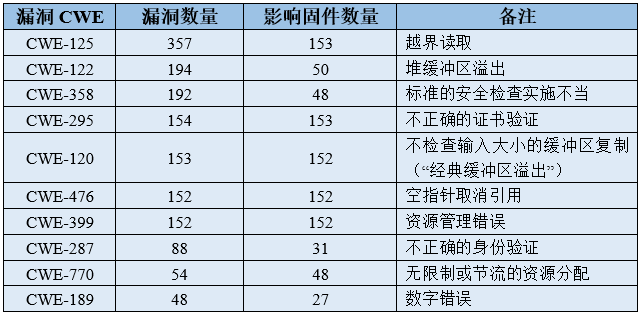
3. Batch Security Analysis of Router Firmware
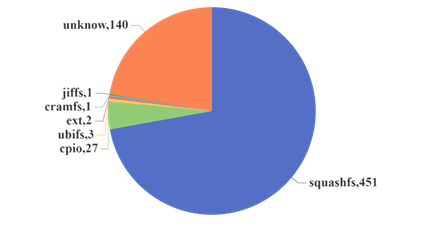


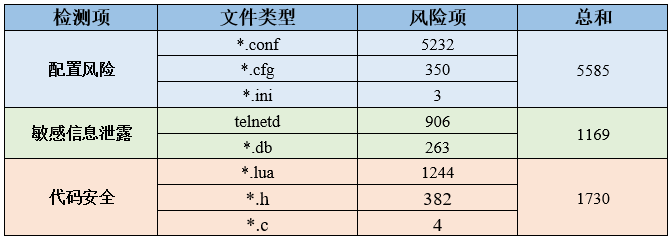
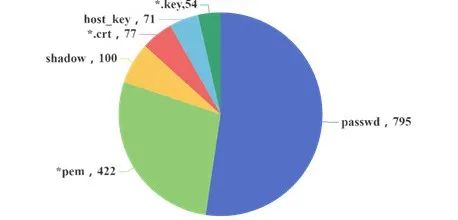



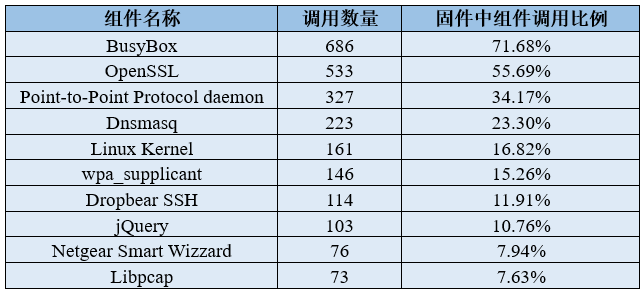
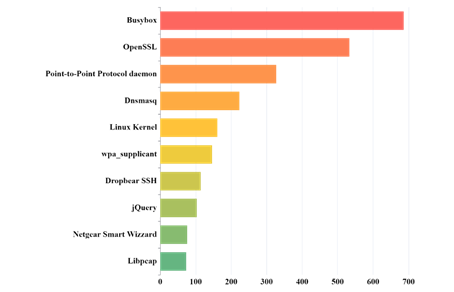

5. Conclusion

1. Overview
2. Dissemination and Download Trends of IoT Firmware Files













3. Batch Security Analysis of Router Firmware














5. Conclusion
