Disclaimer
Any direct or indirect consequences and losses caused by the dissemination and use of the information provided in this article shall be borne by the user. Thunder God Testing and the author of the article shall not bear any responsibility for this. Thunder God Testing reserves the right to modify and explain this article. If you wish to reproduce or disseminate this article, you must ensure its integrity, including copyright statements and all content. Without permission from Thunder God Testing, the content of this article must not be arbitrarily modified or reduced, nor used for commercial purposes in any way.
Content
By default, PDO supports multiple statement execution. It sends a Set Option request to the MySQL server to enable multi-statements. PDO defaults to supporting multi-statement queries. Test code:
<?php
header(‘content-type: text/html; charset=utf-8’);
$dbms=’mysql’;
$host=’127.0.0.1‘;
$dbName=’test’;
$user=’root’;
$pass=’root’;
$dsn=”$dbms:host=$host;
dbname=$dbName”;
try {
$pdo = new PDO($dsn, $user, $pass);
} catch (PDOException $e) {
echo $e;
}
$id = $_GET[‘id’];$sql = “SELECT * from test where id =”.$id;
$stmt = $pdo->query($sql); while($row=$stmt->fetch(PDO::FETCH_ASSOC)){
echo “User ID: “.$row[‘id’].”<br >”;
echo “Username: “.$row[‘name’].”<br >”;
}
Using a semicolon to separate and then execute other statements allows for multiple statement execution.
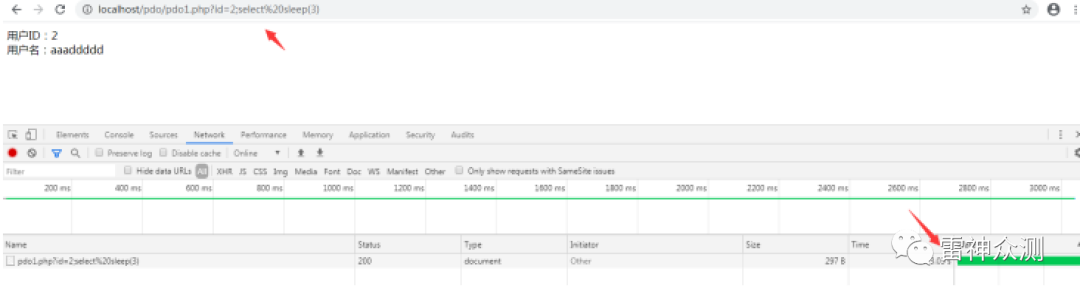
MySQL databases support prepared statements, which are used for efficiently executing repeated statements.
The MySQL official refers to prepare, execute, and deallocate collectively as PREPARE STATEMENT.
The most commonly used are prepare and execute.
Test code:
<?php
header(‘content-type: text/html; charset=utf-8’);
$dbms=’mysql’;
$host=’127.0.0.1‘;
$dbName=’test’;
$user=’root’;
$pass=’root’;$dsn=”$dbms:host=$host;
dbname=$dbName”;
try {
$pdo = new PDO($dsn, $user, $pass, array( PDO::MYSQL_ATTR_MULTI_STATEMENTS => false));
} catch (PDOException $e) {
echo $e;
}
$id = $_GET[‘id’];$sql = “SELECT * from test where id =”.$id;$stmt = $pdo->prepare($sql);
//$stmt->bindParam(1,$id);$stmt->execute();while($row=$stmt->fetch(PDO::FETCH_ASSOC)){
echo “User ID: “.$row[‘id’].”<br >”;
echo “Username: “.$row[‘name’].”<br >”;
}
Multiple statement execution fails because it has been set to
array( PDO::MYSQL_ATTR_MULTI_STATEMENTS => false)
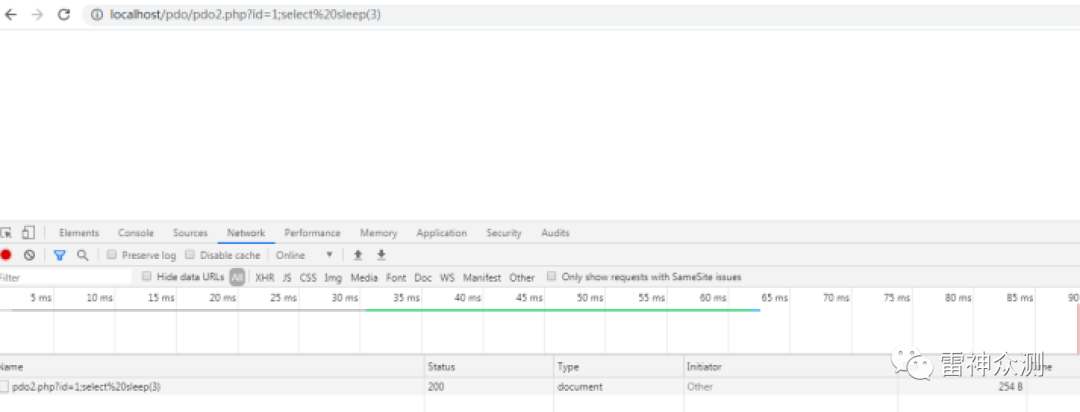
Therefore, under PDO, as long as array( PDO::MYSQL_ATTR_MULTI_STATEMENTS => false) is not set, it is possible to execute multiple statements. Repair plan: Use ?, eliminate string concatenation of SQL statements: Test code:
<?php
header(‘content-type: text/html; charset=utf-8’);
$dbms=’mysql’;
$host=’127.0.0.1‘;
$dbName=’test’;
$user=’root’;
$pass=’root’;$dsn=”$dbms:host=$host;
dbname=$dbName”;
try {
$pdo = new PDO($dsn, $user, $pass, array( PDO::MYSQL_ATTR_MULTI_STATEMENTS => false));
} catch (PDOException $e) {
echo $e;
}
$id = $_GET[‘id’];$sql = “SELECT * from test where id =?”;
$stmt = $pdo->prepare($sql);$stmt->bindParam(1,$id);
$stmt->execute();
while($row=$stmt->fetch(PDO::FETCH_ASSOC))
{
echo “User ID: “.$row[‘id’].”<br >”;
echo “Username: “.$row[‘name’].”<br >”;
var_dump($row);
}
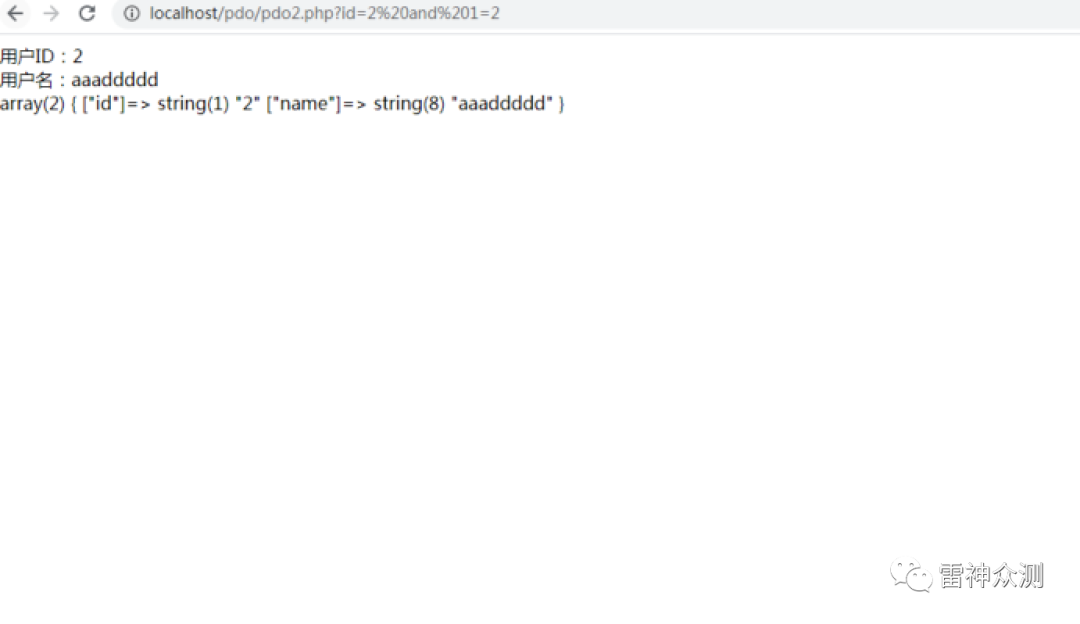
It has been found that injection is no longer possible.
Recruitment
Thunder God Testing SRC Operations (Intern)————————【Job Description】1. Responsible for the operation of SRC’s Weibo, WeChat public account and other online media, maintaining user activity and increasing site traffic; 2. Responsible for reviewing vulnerabilities submitted by white hats, Rank rating, vulnerability repair processing, and related communication work, promoting friendly cooperation and communication between reviewers and white hats; 3. Participate in planning, organizing, and implementing offline activities for white hats, such as salons, press conferences, technical exchange forums, etc.; 4. Actively participate in the brand promotion work of Thunder God Testing, assisting technical personnel in producing high-quality technical articles; 5. Actively participate in communication work with relevant media and other market resources in the company.【Job Requirements】 1. Strong sense of responsibility, lively personality, and good interpersonal skills; 2. Interested in network security and have a basic understanding of the industry; 3. Good copywriting ability and event organization coordination ability.
4. Have artistic skills, understand design beautification, etc.
Send your resume to [email protected]
Designer (Intern)
————————
【Job Description】Responsible for designing the company’s daily promotional images, soft articles, and other design-related work, responsible for product brand design.【Job Requirements】1. More than 1 year of experience in graphic design-related work, familiar with printing processes; have keen observation and aesthetic ability, and excellent creative design ability; have expertise in VI design, advertising design, album design, etc.; 2. Good artistic skills, aesthetic ability and creativity, strong sense of color; proficient in Photoshop/Illustrator/CorelDRAW and other design production software; 3. Experience in brand communication, product design, or new media visual work;【Other Information about the Position】Company Name: Hangzhou Anheng Information Technology Co., Ltd. Office Location: 19th Floor, Anheng Building, Binjiang District, Hangzhou Education Requirements: Bachelor’s degree or above Work Experience: 1 year or more, conditions can be relaxed for outstanding candidates.
Send your resume to [email protected]
Position: Red Team Weaponization Golang Development Engineer Salary: 13-30K Work Experience: 2+ years Work Location: Hangzhou (Headquarters)【Job Responsibilities】1. Responsible for weaponization implementation and research in red-blue confrontation; 2. Platform construction; 3. Implementation of security research.【Job Requirements】1. Master at least one language among C/C++/Java/Go/Python/JavaScript as the main development language; 2. Proficient in using common web development frameworks such as Gin, Beego, Echo, familiar with the design of mainstream database structures such as MySQL, Redis, MongoDB, and have independent deployment and tuning experience; 3. Understand Docker and can perform simple project deployment; 3. Familiar with common web vulnerability principles and can write corresponding exploitation tools; 4. Familiar with the basic operation principles of TCP/IP protocol; 5. Have a strong interest and enthusiasm for security technology and development technology, possess subjective research and learning motivation, have a positive value orientation, good teamwork ability, and strong problem-solving ability, be good at communication and willing to share.【Bonus Points】1. Those with experience in high concurrency TCP services, distributed systems, message queues, etc. are preferred; 2. Open source security products on GitHub are preferred; 3. Have security development experience, independently analyzed related open-source security tools, and participated in the development of related post-exploitation frameworks are preferred; 4. Shared relevant technical articles on security platforms such as Freebuf, Security Guest, and Prophet are preferred; 5. Good English document reading ability.
Send your resume to [email protected]
Security Recruitment————————Company: Anheng Information Position: Web Security Researcher Department: Strategic Support Department Salary: 13-30K Work Experience: 1+ years Work Location: Hangzhou (Headquarters), Guangzhou, Chengdu, Shanghai, Beijing
Work Environment: A building, fitness facilities, doctors, handsome men, beautiful women, high-end cafeteria…【Job Responsibilities】1. Regular technical sharing for the department and the entire company; 2. Research on cutting-edge attack and defense technologies, tracking domestic and foreign security dynamics, vulnerability disclosures, and landing and sedimentation; 3. Responsible for departmental penetration testing and red-blue confrontation business; 4. Responsible for the construction of automation platforms; 5. Responsible for testing and implementing bypass solutions for common WAF product rules【Job Requirements】1. At least 1 year of work experience in the security field; 2. Familiar with HTTP protocol-related technologies; 3. Have case studies of vulnerability discovery in large products, CMS, and vendors; 4. Proficient in code auditing basics for PHP, Java, ASP.NET (one or more); 5. Proficient in Web Fuzz fuzz testing vulnerability discovery techniques; 6. Proficient in OWASP TOP 10 security vulnerability principles and familiar with vulnerability exploitation methods; 7. Have independent vulnerability analysis experience and be familiar with various web debugging techniques; 8. Familiar with at least one common programming language (ASP.NET, Python, PHP, Java)【Bonus Points】1. Good English document reading ability; 2. Have participated as a guest in technical sharing at technical salons; 3. Hold security-related qualifications such as CISSP, CISA, CSSLP, ISO27001, ITIL, PMP, COBIT, Security+, CISP, OSCP; 4. Have experience in submitting vulnerabilities for large SRC, receiving annual awards, and ranking in large CTFs; 5. Developed security-related open-source projects; 6. Good interpersonal communication, coordination ability, analysis, and problem-solving ability are preferred; 7. Personal technical blog; 8. Submitted articles to quality communities;
Position: Security Red Team Weapon Automation Engineer Salary: 13-30K Work Experience: 2+ years Work Location: Hangzhou (Headquarters)【Job Responsibilities】1. Responsible for weaponization implementation and research in red-blue confrontation; 2. Platform construction; 3. Implementation of security research.【Job Requirements】1. Proficient in using Python, Java, C/C++, etc. as the main development language; 2. Proficient in using Django, Flask, and other common web development frameworks, as well as proficient in MySQL, MongoDB, Redis, and other data storage solutions; 3: Familiar with domain security and internal lateral penetration, common web vulnerabilities; 4. Have a strong interest and enthusiasm for security technology and development technology, possess subjective research and learning motivation; 5. Have a positive value orientation, good teamwork ability, and strong problem-solving ability, be good at communication and willing to share.【Bonus Points】1. Those with experience in high concurrency TCP services, distributed systems, etc. are preferred; 2. Open source security products on GitHub are preferred; 3: Have security development experience, independently analyzed related open-source security tools, and participated in the development of related post-exploitation frameworks are preferred; 4. Shared relevant technical articles on security platforms such as Freebuf, Security Guest, and Prophet are preferred; 5. Good English document reading ability.
Send your resume to [email protected]

Focus on penetration testing technology
Latest global network attack techniques
END