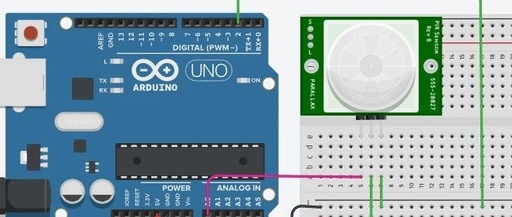
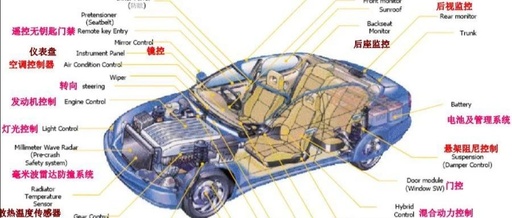
Embedded System Software Vulnerabilities and Security Isolation
▲ Click Above to Follow STM32 In the past, developers often overlooked the security issues of embedded devices when discussing them, assuming that embedded devices are not easily susceptible to network attacks and are not targets for hackers, or that simply implementing encryption and authentication suffices for adequate security. However, in today’s world of the … Read more