▲ Click Above to Follow STM32

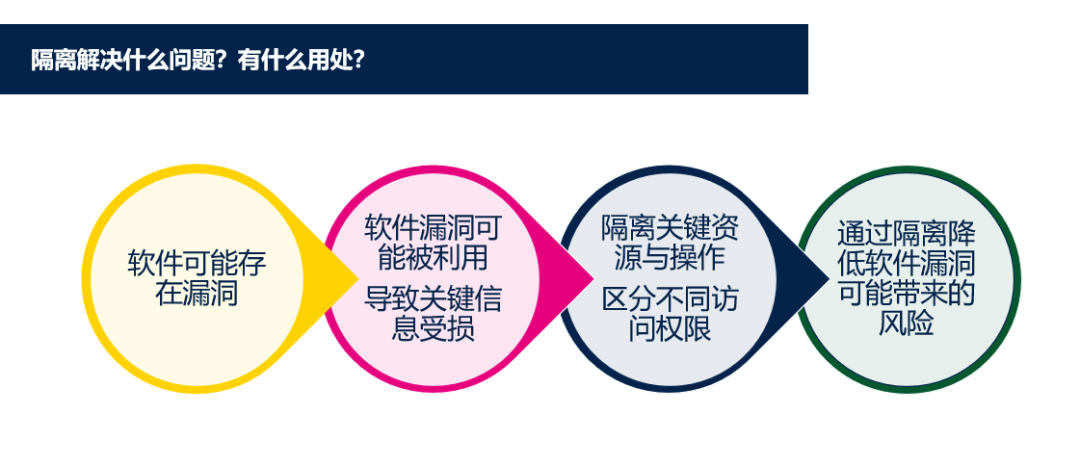
In the past, developers often overlooked the security issues of embedded devices when discussing them, assuming that embedded devices are not easily susceptible to network attacks and are not targets for hackers, or that simply implementing encryption and authentication suffices for adequate security.
However, in today’s world of the Internet of Things, the number of connected devices is increasing exponentially, and the scale and complexity of attacks on embedded devices are also on the rise. It is a consensus among developers that embedded systems require more security measures.
This article organizes the embedded software vulnerabilities and security isolation measures based on STM32.
Typical Security Threats and Countermeasures for Embedded Devices

Security Isolation
Demonstration of Attacks Using Software Vulnerabilities to Steal MCU Code and STM32 Hardware Security Protections Against Such Attacks
Below video source is from STM32
Isolation Mechanism of STM32 MCU
Utilizing the Isolation Function of the MPU Built into the Arm Cortex Core
-
Most STM32 MCUs (except for those with the M0 core) have a built-in MPU unit
-
The MPU unit can partition the 4G address space into several regions, each with different attributes, achieving a certain level of isolation protection
➤ For example, in the previously mentioned scenario, if the MPU is used, a region corresponding to the on-chip SRAM address can be defined and set with the XN (execute never) attribute to prevent the execution of malicious code injected into the on-chip SRAM
-
With the user and privilege modes of the kernel, the MPU can also achieve access control to the required critical resources. For more on this, refer to:
➤ STM32 WeChat Article:Using STM32’s MPU (Memory Protection Unit) for Code Isolation and Access Control
-
➤ STM32 Chinese Official Website LAT:Using STM32’s MPU for Code Isolation and Access Control
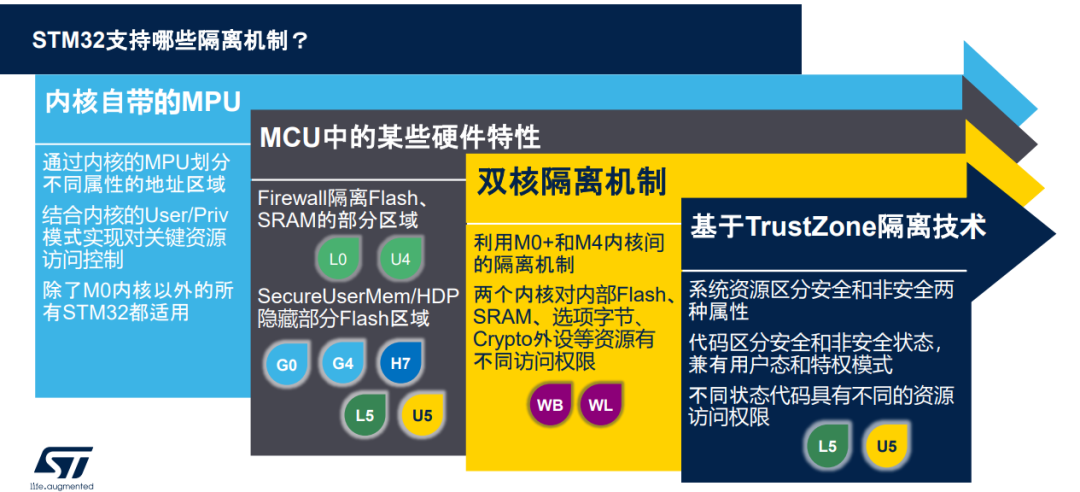
Isolation Features of Different STM32 MCU Series
-
In addition to the MPU, certain STM32 series also have special hardware units that can also provide isolation, such as Firewalls and Flash secure storage areas
-
Firewalls for L0 and L4 ➤ STM32s with Firewall hardware can protect on-chip Flash and RAM via the Firewall ➤ Regions protected by the Firewall are isolated from those outside the region, making them inaccessible to the CPU and DMA directly; access is only possible through a unique entry function address via function calls to utilize the services provided by the code inside the Firewall ➤ The use of the Firewall mechanism can reduce the risks associated with software vulnerabilities. For example, in the previously mentioned scenario, if the Firewall is used, even if malicious code is injected and successfully executed, that code cannot directly read any content within the Firewall-protected area ➤ Examples of using the Firewall for data protection can be referenced STM32 WeChat Article:Information Security Topic | Step-by-Step Guide to Implementing Key Data and Code Protection on STM32L0 STM32 Chinese Official Website LAT:Protection of Key Data and Code on L0 Based on Firewall and PCROP:https://stmcu.com.cn/Designresource/detail/localization_resource/666718
-
Flash secure storage areas on G0, G4, H7, L5, and the latest U5➤ Flash secure storage area (Secure Area), also known as (HiDeProtect) hidden protection Flash area, can be configured in size via Option Bytes➤ Once the protection for this area is enabled via register settings, it cannot be accessed again before reset, including read, write, and erase➤ The secure storage area can also isolate the Flash within and outside the secure area, thus protecting the data within the area. For the previously mentioned scenario, if the secure storage area is used and its protection is enabled, even if the injected malicious code runs, it will not be able to access any data within the secure storage area.
-
Examples of using the secure storage area can be referenced ➤ STM32 Chinese Official Website LAT: Using STM32H7 Secure User Storage Area:https://stmcu.com.cn/Designresource/detail/localization_resource/666714 Using New Features of STM32H7 for Secure Storage and Use of Sensitive Data:https://stmcu.com.cn/Designresource/detail/localization_resource/666716 ➤ STM32 WeChat Article: Information Security Topic | Code Protection (1) Using New Features of STM32H7 to Protect the Confidentiality of On-Chip Code Information Security Topic | Secure Storage (1) Key Storage of STM32H7
Inter-Core Isolation of STM32 MCUs
-
Certain STM32s with dual-core architecture also provide inter-core isolation mechanisms ➤ Series supporting dual-core isolation include WB and WL ➤ Inter-core isolation utilizes the different access permissions of M0+ and M4 to achieve secure isolation of code, data, and other hardware resources 1. The M0+ core can access all on-chip resources 2. The M4 core (the core running the application) cannot access the resources allocated to M0+, including Flash, SRAM, related option bytes, Crypto, and other peripherals
-
A typical application utilizing dual-core isolation on WB and WL is the key storage service (Customer Key Storage) ➤ Relevant content can be referenced STM32 Chinese Official Website LAT:Key Security Storage and Use of STM32WB: STM32 WeChat Article:Information Security Topic | Secure Storage (2) User Key Storage (CKS) of STM32WB
System-Level Isolation of STM32 Based on TrustZone Architecture
-
The latest STM32L5 and STM32U5 series with CM33 cores adopt TrustZone-based isolation technology
-
From the core to memory to peripherals, the entire system’s resources can be configured with secure and non-secure attributes. The CPU can run code in both secure and non-secure states, and secure and non-secure codes have different access permissions to resources with different security attributes
-
The TrustZone-based system and isolation mechanism of STM32 offer significant flexibility, allowing not only simple key storage and crypto operations but also running more complex software logic in the secure area, such as running a fingerprint matching algorithm, etc.
-
Utilizing the TrustZone-based isolation mechanism can effectively address software vulnerabilities and reduce system risks ➤ For the previously mentioned scenario, if TrustZone is enabled, the code is divided into secure and non-secure zones. Even if the communication code in the non-secure zone has vulnerabilities, the code and data in the secure zone will remain unaffected.
-
For more information on the TrustZone architecture’s isolation mechanism, refer to -
➤ STM32 Chinese Official Website: L5 Series Course:STM32L5 Introduction Course (1) Understanding TrustZone from Cortex-M33:https://www.stmcu.com.cn/ecosystem/chip/chipfamily-STM32L5 Video:STM32L5 Trust Example:https://www.stmcu.com.cn/video/1582 ➤ AI Electric Hall L5 Related Courses 
▲STM32L5 Series Course
Summary: Security Isolation Features of STM32 MCUs
© THE END