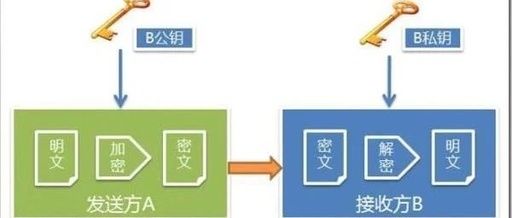
Explaining the Mathematical Principles of Encryption Algorithms
Recently, Jason invited Mei from the Mathematics Department of Fudan University to give five hardcore math classes for friends interested in Web3. Starting from natural numbers, he explained the details of RSA asymmetric encryption. Let me review and try to explain this rather complex topic. (Math warning ahead, but I promise to limit it to … Read more