Editor’s Note
The Cybersecurity Level Protection System 2.0 standard has been officially released, Qi An Xin has specially launched the “Interpreting Level Protection 2.0” series to systematically analyze and interpret various aspects of Level Protection 2.0 through the publication of related articles. We invite you to discuss and welcome your comments.
Abstract
In the three articles published last week, we introduced and analyzed the core connotations and core changes of Level Protection 2.0, as well as design solutions based on the new standard. Starting this week, we will provide professional and systematic interpretations for different security application areas.
With the gradual implementation of China’s “Internet +” strategy, the industrial Internet will become one of the most important infrastructures for the country in the future. New technologies such as cloud computing, big data, artificial intelligence, and the Internet of Things are widely used in critical information infrastructure, leading to rapid changes in cybersecurity situations and demands. As a result, Level Protection 1.0, namely the 2008 released “GB/T22239-2008 Information Security Technology Basic Requirements for Information System Security Level Protection” and its supporting policy documents and standards, no longer meet the cybersecurity protection requirements under new technologies and business scenarios.
Level Protection 2.0 expands the scope of cybersecurity protection, enhances the requirements for level protection of critical information infrastructure, and adopts a combination of general security requirements and extended security requirements to better meet the common and personalized requirements for security protection, improving the universality and operability of level protection, and providing strong technical support for the implementation and enforcement of the “Cybersecurity Law”.
1. Security Extension Requirements of Level Protection 2.0 for Industrial Control Systems
In addition to general security requirements, Level Protection 2.0 proposes security extension requirements for industrial control systems to suit the unique technologies and application characteristics of industrial control, as shown in the figure below.
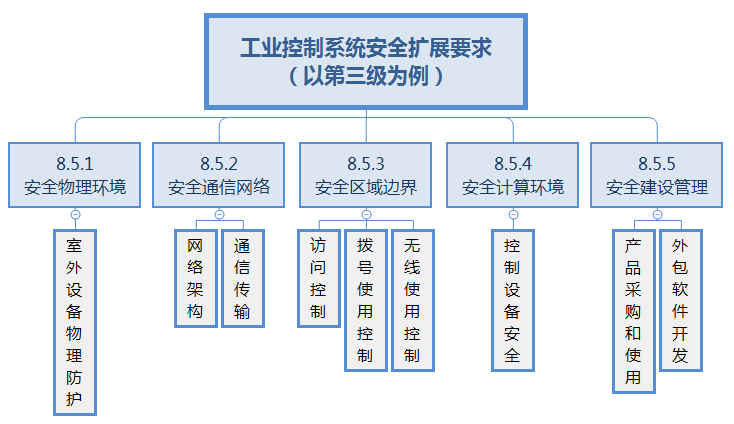
The special requirements for security extension include:
Physical and Environmental Security: Increased security protection requirements for outdoor control devices, such as enclosures or devices housing the control equipment and the environment surrounding the control devices;
Network and Communication Security: Increased requirements for network architecture security protection, communication transmission requirements, and access control requirements adapted to the industrial control system network environment, as well as requirements for dial-up control and wireless control;
Device and Computing Security: Increased security requirements for control devices, which are mainly real-time controllers used in industrial control systems to execute control logic and data acquisition functions, such as PLCs, DCS controllers, etc.;
Security Construction Management: Increased requirements for product procurement and usage and software outsourcing, mainly targeting the requirements for industrial control devices and dedicated information security products for industrial control, as well as confidentiality and professionalism requirements when outsourcing industrial control system software;
Security Operation and Maintenance Management: Adjusted demands for vulnerability and risk management, malicious code prevention management, and security incident handling, more adaptable to industrial scene applications and industrial control systems.
2. Key Requirements Interpretation for Industrial Control System Security
Based on the general and extended requirements of Level Protection 2.0 for industrial control system security, it can be seen that the focus of industrial security protection lies in industrial host security, boundary security, and industrial security management.
1. Industrial Host Security Requirements
-
8.1.4.5 Malicious Code Prevention
Technical measures or proactive immune verification mechanisms should be adopted to identify intrusion and virus behavior in a timely manner and effectively block them.
-
8.5.4.1 Control Device Security
b) After sufficient testing and evaluation, patch updates, firmware updates, and other tasks should be performed on control devices without affecting the stable operation of the system;
c) The floppy disk drive, CD-ROM drive, USB ports, serial ports, or redundant network ports of control devices should be closed or removed; if they must be retained, strict monitoring and management through relevant technical measures must be implemented;
Interpretation: Continuity is the basic requirement of industrial production. Therefore, both production equipment and the control systems of these devices need to operate continuously for long periods, making it difficult to update patches in a timely manner. In practice, such systems usually adopt a “whitelist” approach for security protection, meaning that only software on the whitelist is allowed to run, while other processes are blocked to prevent attacks from viruses, Trojans, and malicious software. Furthermore, with technological advancements, USB drives have become the most convenient medium for information exchange. However, the risk of spreading viruses and malicious software through USB drives is extremely high, necessitating strict management of USB port usage. Therefore, installing industrial host protection systems on the upper-level machines of control systems is the most common and effective measure. Excellent industrial host protection products in the industry typically possess USB security management capabilities, managing the use of USB drives throughout the entire process through typical security measures such as “registration-authorization-audit,” effectively preventing unauthorized USB drives from introducing viruses. Industrial host security protection systems are the first choice for addressing the pain points of industrial host security.
2. Industrial Boundary Security Requirements
-
8.1.3.1 Boundary Protection
a) Access and data flow crossing boundaries should be communicated through controlled interfaces provided by boundary devices;
b) The behavior of unauthorized devices connecting to the internal network should be able to be checked or restricted;
c) The behavior of internal users connecting unauthorized to external networks should be able to be checked or restricted;
d) The use of wireless networks should be restricted, ensuring that wireless networks access the internal network through controlled boundary devices;
-
8.5.2.1 Network Architecture
a) The industrial control system and other enterprise systems should be divided into two areas, with one-way technical isolation methods used between areas;
b) The internal industrial control system should be divided into different security domains based on business characteristics, with technical isolation methods employed between security domains;
-
8.5.3.1 Access Control
a) Access control devices should be deployed between the industrial control system and other enterprise systems, with access control policies configured to prohibit any common network services such as E-Mail, Web, Telnet, Rlogin, FTP from crossing regional boundaries.
Interpretation: Industrial control networks are usually physically isolated from enterprise resource networks (office networks). However, with the deep integration of industrialization and information technology, more and more devices will be interconnected. The trend of informationization, digitization, and intelligence in industrial production environments is continuously developing. To protect the core production systems of industry from external network attacks while transmitting production data to management systems in real time, it is necessary to deploy network isolation and information exchange devices between the industrial control network and the resource network. Typical devices that meet such requirements include industrial gateways. Additionally, the industrial control network needs to implement security domain partitioning, employing isolation methods between security domains to ensure safety. Moreover, industrial control networks typically use proprietary industrial protocols and applications, while common applications and protocols such as E-Mail, Telnet, Rlogin are common carriers for network attacks and should be denied access to the industrial control network. Industrial firewalls are usually deployed at the boundary of the industrial network to achieve protective functions. Therefore, to address the pain points of industrial boundary security, the focus should be on adopting industrial gateways and industrial firewall devices.
3. Industrial Security Management Requirements
-
8.1.5.4 Centralized Control
a) A specific management area should be delineated to control security devices or security components distributed across the network;
b) A secure information transmission path should be established to manage security devices or security components in the network;
c) The operational status of network links, security devices, network devices, and servers should be monitored centrally;
d) Audit data scattered across various devices should be collected, summarized, and analyzed centrally, ensuring that the retention time of audit records complies with legal and regulatory requirements;
e) Security-related matters such as security policies, malicious code, and patch upgrades should be managed centrally;
f) Various security incidents occurring in the network should be able to be identified, alerted, and analyzed.
Interpretation: The construction of industrial network security started late, is weak, and lacks effective management leverage. By addressing the pain points of boundary and host security, security issues are only resolved at isolated points. A greater requirement is to perceive the security state of the entire industrial network, collect and analyze data, and conduct security monitoring of the industrial network, promptly identifying abnormal operations and alerting illegal behaviors. Through a visual centralized management interface, various security issues within the industrial network are clearly displayed, accurately pinpointing and managing potential failures caused by network security issues. Therefore, “seeing clearly, seeing through, and seeing the entire threat in industrial production is the foundation and prerequisite for ensuring industrial network security.” Based on this, industrial security monitoring systems and control centers can be utilized as a technical platform for unified management of industrial network security, serving as the industrial network security management center to meet the three-tier requirements of Level Protection 2.0 for industrial control systems.
3. Solutions for Industrial Security Pain Points
The three key requirements of Level Protection 2.0 regarding industrial control system security also represent the three pain points of security construction in industrial enterprises. Qi An Xin, after years of research in industrial security technology and customer service practice, has proposed an integrated solution, as shown in the figure below.
The solution comprehensively covers the protection, monitoring, and centralized management of industrial control networks, including four products: industrial host security protection system, industrial control security gateway (industrial firewall), industrial security monitoring system (including control platform), and industrial security isolation and information exchange system (industrial gateway).
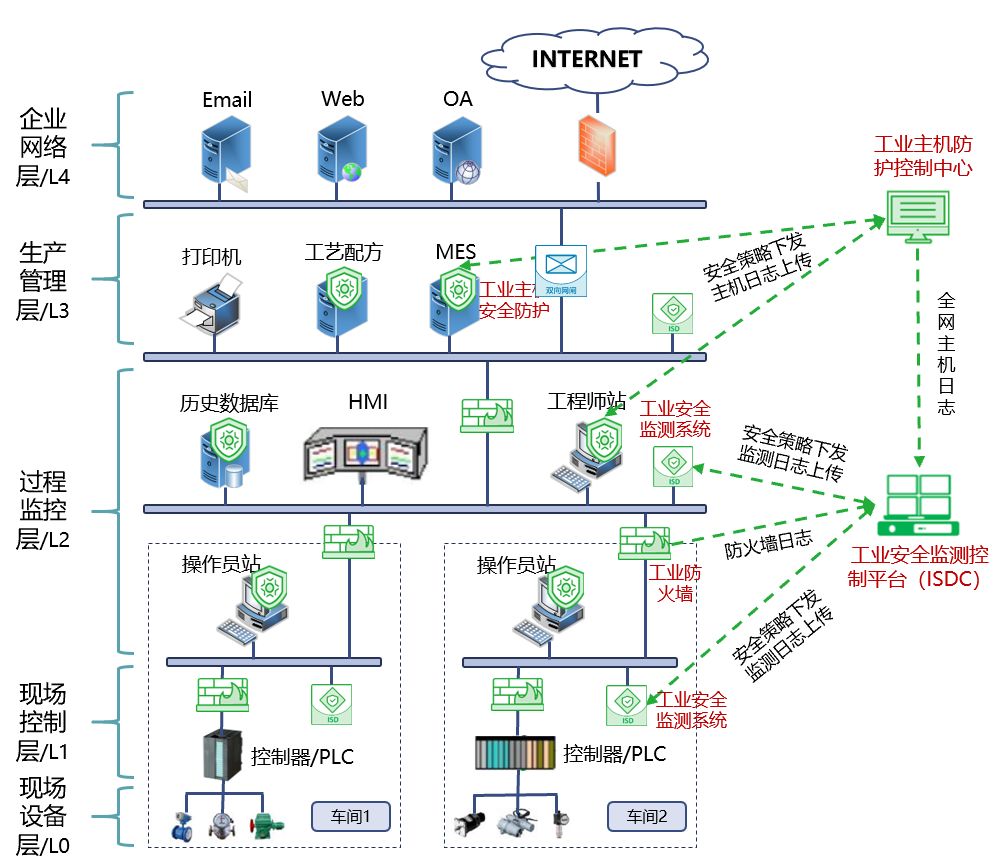
Industrial Host Security Protection System is a software product installed on industrial control upper machines and industrial servers. It utilizes whitelist intelligent matching technology and a three-tier interception technique of “entry-operation-diffusion” to prevent virus and malicious program invasions, controlling illegal access of USB mobile devices, providing a secure and clean operating environment for industrial software.
Industrial Control Security Gateway System (Industrial Firewall) is a boundary security protection product specifically designed for industrial environments, providing secure isolation for the connection between the industrial control network and the enterprise network, as well as for connections within various areas of the industrial control network. The product adopts a four-tier whitelist security strategy to filter illegal access, ensuring that only trusted devices can connect to the industrial control network and that trusted traffic is transmitted within the network.
Industrial Security Monitoring System (ISD) passively and non-invasively collects operational data from industrial control systems, automatically discovers industrial assets, monitors unauthorized access devices, detects network intrusion behaviors in real-time, and monitors abnormal operations of industrial control devices. It promptly uploads various attack and abnormal information to the industrial security monitoring control platform (ISDC). ISDC aggregates logs from all security monitoring devices, as well as logs from the industrial host security protection system, industrial firewall, and industrial gateway, centralizing storage and unified analysis, helping security operation personnel understand the overall security status and threat dynamics of the industrial network in a timely manner.
Industrial Security Isolation and Information Exchange System (Industrial Gateway) is used for secure data exchange between networks of different security levels in the industrial control network. It implements information ferrying through link blocking and protocol conversion, capable of deeply analyzing various industrial protocols (OPC, ModBus, S7, DNP3, IEC104, etc.), integrating multiple functions such as security isolation, real-time information exchange, protocol analysis, content detection, access control, and security protection, providing high-speed and secure data exchange capabilities and reliable information exchange services while ensuring network security isolation.
Appendix: Overview of Industrial Control Systems
1. Overview of Industrial Control Systems
Industrial control systems (ICS) are a collective term for various types of control systems, including data acquisition and supervisory control systems (SCADA), distributed control systems (DCS), and other control systems, such as programmable logic controllers (PLC) commonly used in industrial sectors and critical infrastructure. Industrial control systems are typically used in industries such as power, water and wastewater treatment, oil and gas, chemicals, transportation, pharmaceuticals, pulp and paper, food and beverage, as well as discrete manufacturing (such as automotive, aerospace, and durable goods). Industrial control systems mainly consist of process levels, operational levels, and communication networks between various levels and internally. For large-scale control systems, they also include management levels. The process level includes controlled objects, field control devices, and measuring instruments; the operational level includes engineer and operator stations, human-machine interfaces, configuration software, and control servers; the management level includes production management systems and enterprise resource systems; and the communication network includes commercial Ethernet, industrial Ethernet, field buses, etc.
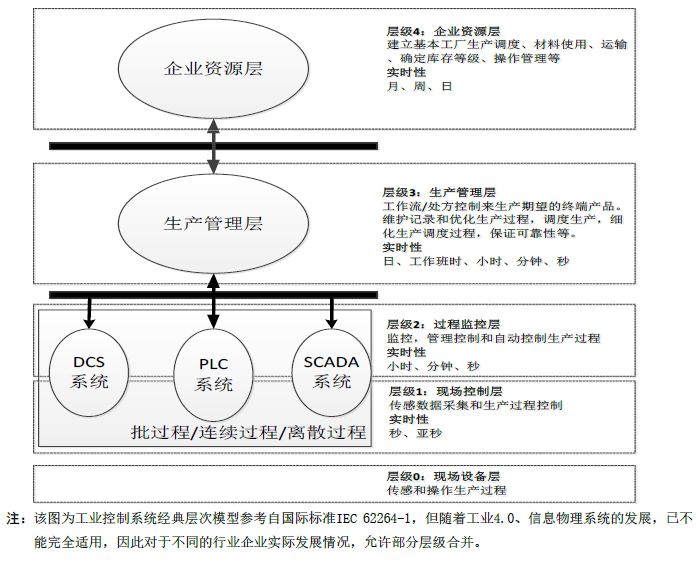
2. Hierarchical Model of Industrial Control Systems
The hierarchical model of industrial control networks is divided into five levels from top to bottom: enterprise resource layer, production management layer, process monitoring layer, field control layer, and field device layer, with different real-time requirements at each level. The enterprise resource layer mainly includes ERP system functional units, providing decision-making operational means for enterprise decision-makers; the production management layer mainly includes MES system functional units, managing the production process, such as manufacturing data management and production scheduling management; the process monitoring layer mainly includes monitoring servers and HMI system functional units, used for data acquisition and monitoring of production processes, and implementing human-computer interaction through HMI systems; the field control layer mainly includes various controller units, such as PLCs, DCS control units, etc., used for controlling various execution devices; the field device layer mainly includes various process sensing devices and execution device units, used for sensing and operating the production process.
Previous Recommendations
Interpreting Level Protection 2.0: New Ideas for Cybersecurity Construction Based on New Level Protection Requirements
Interpreting Level Protection 2.0: Core Changes
Interpreting Level Protection 2.0: Core Connotations