This report is jointly released by the National Internet Emergency Center (CNCERT) and Qihoo 360 Technology Co., Ltd. (Qihoo 360).
1
Overview
Recently, CNCERT and Qihoo 360 have jointly monitored the emergence of a new DDoS botnet that is rapidly spreading on the internet. Tracking and monitoring have revealed that the number of domestic compromised hosts (measured by IP count) has exceeded 20,000 daily, and it targets multiple attack objectives each day, posing a significant threat to cyberspace. This botnet is a variant of Mirai, including samples targeting CPU architectures such as mips, arm, and x86. Over the past two months, we have captured at least four iterations of this Mirai variant, with communication protocols largely consistent with Mirai. The primary propagation method is currently Telnet password brute-forcing, although it has historically exploited N-day vulnerabilities for propagation.
2
Botnet Analysis
(1) Sample Analysis
This article selects the latest V4 sample for the X86 CPU architecture as the main analysis object, with the basic information of the sample as follows.
| File Name | gx86 |
| MD5 | 02d163134e3b4eabe62497b81659c2db |
| File Format | ELF 32-bit LSB executable, Intel 80386 |
| C2 | 103.136.42.158:16100 |
1. The sample must run with the filename: GSec; otherwise, it will terminate the process and print a misleading statement.
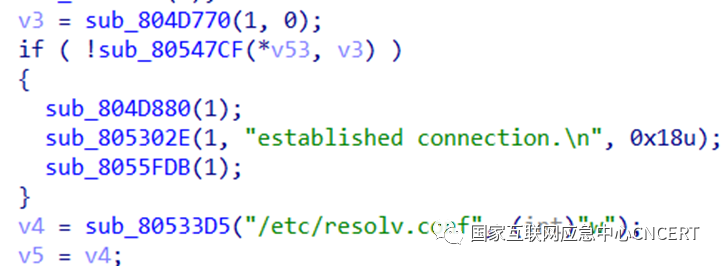
Figure 1 Sample Running Information
2. This sample reuses some code from the Gafgyt family, modifying the process name based on whether the target machine has Python installed.
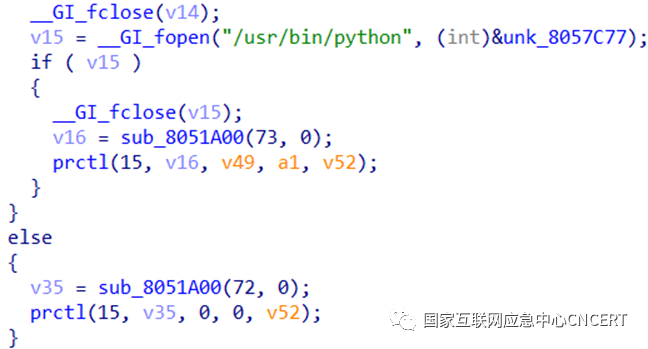
Figure 2 Process Name Modification
3. The bot’s online mechanism is consistent with Mirai. The first packet is a fixed four bytes \x00\x00\x00\x01, the second packet is the sample running parameter length + running parameters, defaulting to \x00, generally specified in shell scripts, followed by sending a fixed two-byte heartbeat packet \x00\x00 every 60 seconds.
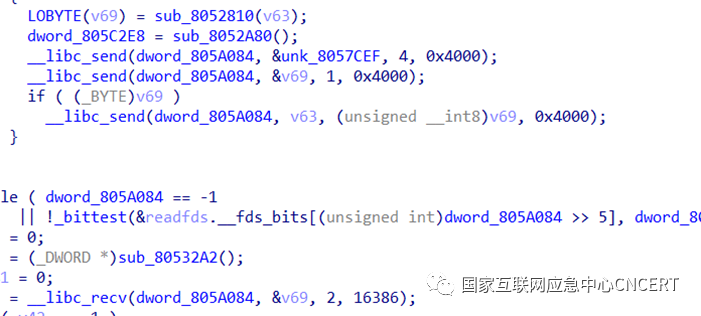
Figure 3 Online Mechanism
4. DDoS Attack MethodsInclude attacks targeting Layer 4 and Layer 7, including typical Mirai DDoS attack methods.Table 1 Attack Method Description
| Attack Method Name | Meaning | Characteristics |
| gudp | Modified UDP FLOOD, Layer 4 | High BPS |
| ovh_bypass | UDP-based Layer 7 attack | Targets OVH-protected servers |
| greeth | Based on GRE protocol, effective attack payload at Layer 2 | High BPS |
| plaintcp | Modified TCP FLOOD, Layer 4 | High BPS |
| greip | Modified greeth FLOOD | High BPS, PPS |
| std | Modified UDP FLOOD | High BPS |
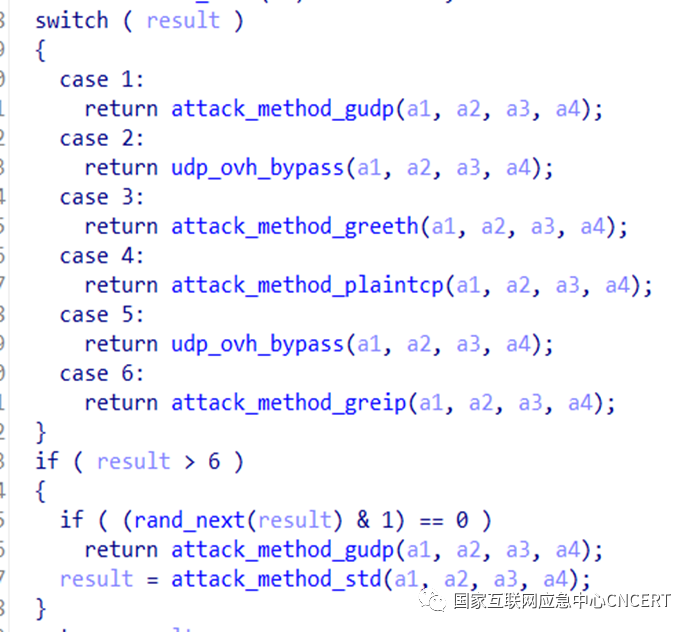
Figure 4 Attack Methods
(2) Propagation Method Analysis
In the changes from version V1 to V4 of this Mirai variant botnet, the propagation model has completely removed the vulnerability propagation module, and there are multiple versions of the weak password list. It can be inferred that the botnet controllers believe that password brute-forcing is more effective, thus favoring this propagation method.
The content of the password decryption for each version is shown in Figure 5.
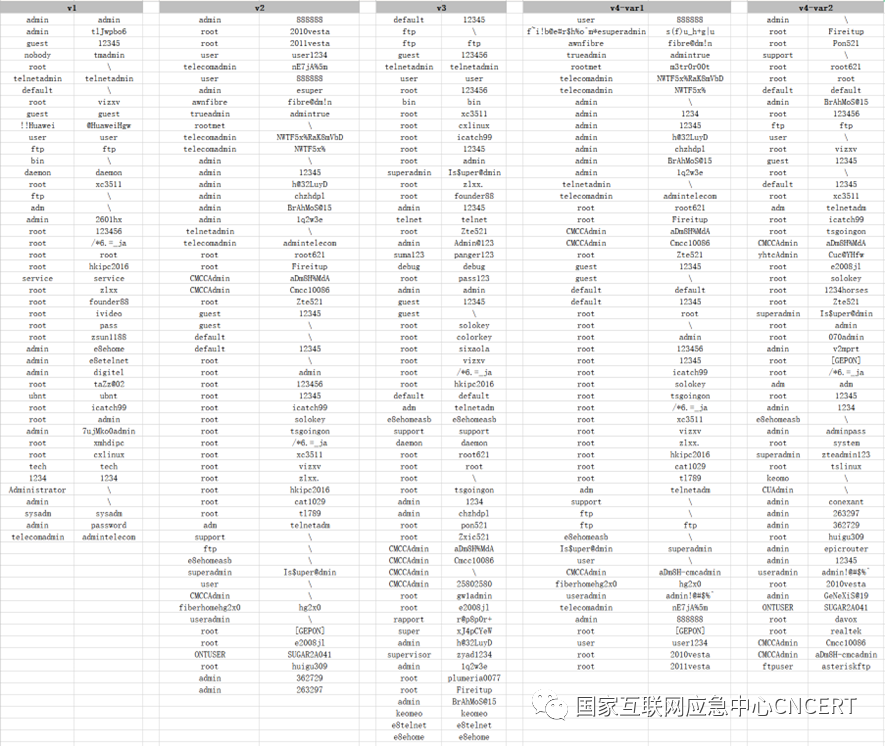
Figure 5 Passwords for Each Version
3
Botnet Infection Scale
Through monitoring and analysis, it was found that from April 1 to May 23, 2022, the number of daily online compromised hosts for this Mirai variant botnet reached a maximum of 21,000, with a cumulative infection count of 112,000. The daily situation of online compromised hosts is as follows.
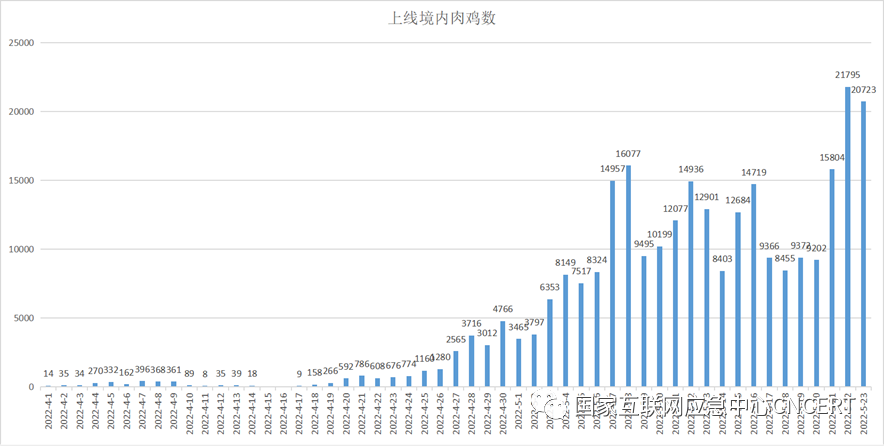
Figure 6 Daily Online Compromised Hosts
This Mirai variant botnet is distributed among compromised hosts by province, with the top three being Zhejiang Province (45.1%), Yunnan Province (16.1%), and Guangdong Province (10.7%); by operator, Telecom accounts for 93.2%, Unicom 6.1%, and Mobile 0.4%.

Figure 7 Distribution of Compromised Hosts by Province and Operator
4
Botnet Attack Dynamics
Through tracking and monitoring, it was found that this Mirai variant botnet has been launching DDoS attacks since April 1, 2022, and the attack behavior has been very active. The most intense attacks occurred on May 16, 2022, with a total of 47 DDoS attacks, and on May 8, 2022, it mobilized 16,000 hosts to attack a specific target. The trend of attack events is as follows:
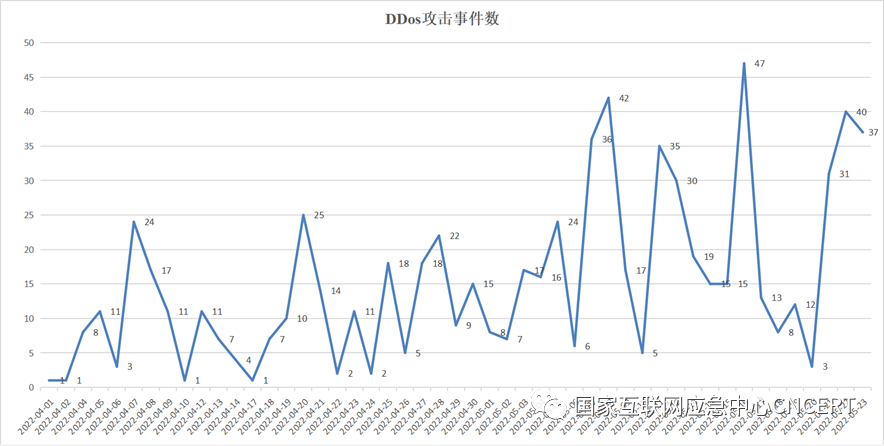
Figure 8 Attack Trend of Mirai Variant Botnet
5
Prevention Recommendations
We urge the public to strengthen risk awareness and enhance security measures to avoid unnecessary economic losses. The main recommendations include: 1. Timely patching of relevant system vulnerabilities. 2. Avoid using weak or default passwords, and change passwords regularly.
Upon discovering that a host is infected with a botnet program, immediately verify the control status of the host and the intrusion path, and clean the affected host.
6
Related IOC
Sample MD5:
79b5152e07ac9f67f337553afd8fdf49
73963353779b44bce2891d11e66d0e91
4cb48ee8d5e948cfe90eb1a9a3b5111f
17659ffa9ba80830b2ec6a7e1601fd38
0c05bcb28832937369e39ee113a6be81
c6ad4c67d5b8c4b2730a187161008da3
70efbb538061fbc2c399f2437a6e0e06
ba8ccfb46737d33e3eceec65d5ea17dd
5704172e740810bd7a808d17a62a2b63
1b469287783dc5f83222c515576653f5
4c160ae988d2489b9f1c27914c1657bf
9ee59e00d14bf71c0e2f1e09c9469dd6
d9e9923f705b6a3bce4bf4ddbb9ab2ec
a9f1e01e6793af26162bfe13f134a285
41dc20f7d94d11d8fceb524ff6b2391f
Download Links:
http[:]//5.255.101.44/garm
http[:]//5.255.101.44/garm5
http[:]//5.255.101.44/garm6
http[:]//5.255.101.44/garm7
http[:]//5.255.101.44/gmpsl
http[:]//5.255.101.44/gm68k
http[:]//5.255.101.44/gsh4
http[:]//5.255.101.44/gppc
http[:]//5.255.101.44/gx86
http[:]//5.255.101.44/gmips
http[:]//103.136.41.159/garm
http[:]//103.136.41.159/garm5
http[:]//103.136.41.159/garm6
http[:]//103.136.41.159/garm7
http[:]//103.136.41.159/gmpsl
http[:]//103.136.41.159/gm68k
http[:]//103.136.41.159/gsh4
http[:]//103.136.41.159/gppc
http[:]//103.136.41.159/gx86
http[:]//103.136.41.159/gmips
http[:]//194.31.98.230/garm
http[:]//194.31.98.230/garm5
http[:]//194.31.98.230/garm6
http[:]//194.31.98.230/garm7
http[:]//194.31.98.230/gmpsl
http[:]//194.31.98.230/gm68k
http[:]//194.31.98.230/gsh4
http[:]//194.31.98.230/gppc
http[:]//194.31.98.230/gx86
http[:]//194.31.98.230/gmips
http[:]//194.31.98.186/garm
http[:]//194.31.98.186/garm5
http[:]//194.31.98.186/garm6
http[:]//194.31.98.186/garm7
http[:]//194.31.98.186/gmpsl
http[:]//194.31.98.186/gm68k
http[:]//194.31.98.186/gsh4
http[:]//194.31.98.186/gppc
http[:]//194.31.98.186/gx86
http[:]//194.31.98.186/gmips
http[:]//107.174.137.24/garm
http[:]//107.174.137.24/garm5
http[:]//107.174.137.24/garm6
http[:]//107.174.137.24/garm7
http[:]//107.174.137.24/gmpsl
http[:]//107.174.137.24/gm68k
http[:]//107.174.137.24/gsh4
http[:]//107.174.137.24/gppc
http[:]//107.174.137.24/gx86
http[:]//107.174.137.24/gmips
Control IP:
46.175.146.159
103.136.42.158

Click “Read Original” below to enter the official website for the complete report download.