
OriginalVulnerability

1. Coding Standards and Software Vulnerabilities
Software vulnerabilities are often closely related to the lack of coding standards. If input validation, dependency management, and security design principles are ignored during development, even if the functionality is normal, security risks may be hidden. Taking the Java deserialization vulnerability as an example, the essence is that developers did not follow the following standards:
Missing validation of untrusted data: Directly calling ObjectInputStream.readObject() on user-input serialized data without verifying the legitimacy of the data source (e.g., not filtering Base64 encoded data starting with rO0AB).
Abuse of dangerous functions: Using third-party libraries (such as Apache Commons Collections’ InvokerTransformer) that pose reflection call risks, allowing attackers to execute arbitrary commands by constructing TransformedMap chain calls.
Outdated dependencies not updated: To maintain backward compatibility, old versions of libraries containing vulnerabilities (such as Log4j 2.x not removing JNDI lookup functionality) are retained for a long time, leading to significant vulnerabilities like CVE-2021-44228.
The security of industrial control systems is based on their isolation from external networks. However, with the deep integration of information technology and industrialization, the isolation of industrial control systems from external network environments is becoming blurred. This exposes numerous vulnerabilities within the system to external networks, providing opportunities for attackers.
In our research on the upper computer software of industrial control systems, we found security vulnerabilities caused by the improper use of .NET functional modules.
2. Deserialization in .NET
2.1 Concept of Deserialization
Serialization is the process of converting the state of an object into a form that can be persisted or transmitted. The complement of serialization is deserialization, which converts a stream back into an object. Together, these two processes ensure that data can be stored and transmitted.
.NET has the following serialization technologies:
Binary serialization maintains type fidelity, which is very useful for preserving object state during multiple calls to an application. For example, by serializing an object to the clipboard, it can be shared between different applications. You can serialize objects to streams, disks, memory, and networks. Remote processing uses serialization to pass objects “by value” between computers or application domains.
XML and SOAP serialization only serialize public properties and fields and do not maintain type fidelity. This is useful when you want to provide or use data without restricting the applications that can use that data. Since XML is an open standard, it is an ideal choice for sharing data over the web. SOAP is also an open standard, making it an ideal choice as well.
JSON serialization only serializes public properties and does not maintain type fidelity. JSON is an open standard and is ideal for sharing data over the web.
The main purpose of serialization is to save the state of an application in a disk file or database and restore that state when the application runs next. Objects can also be sent by value from one application domain to another, and if an object is serialized into a byte stream in memory, some other techniques can be used to process the data, such as encryption and compression.
2.2 .NET Remoting
.NET Remoting is a framework for communication across application domains or networks, allowing client applications to access and call objects in server-side applications. .NET Remoting is implemented based on the classes and interfaces provided by the System.Runtime.Remoting namespace and its sub-namespaces in the .NET Framework. The framework supports various communication protocols such as TCP and HTTP and can implement security, logging, and other functions through configuration.
All local objects that use .NET Remoting across application domains must be passed by value and should be marked with the [Serializable] custom attribute; otherwise, they must implement the ISerializable interface. When an object is passed as a parameter, the framework serializes the object and transmits it to the target application domain, where the object will be reconstructed. Local objects that cannot be serialized cannot be passed to other application domains and thus cannot be remotely processed.
However, Microsoft has explicitly stated in its official documentation that there are security vulnerabilities in deserialization within .NET Remoting, and it has deprecated .NET Remoting in favor of WCF. To mitigate deserialization vulnerabilities in .NET Remoting, Microsoft has also divided the deserialization levels of the .NET Framework Remoting into Low and High, limiting the types that users can deserialize to reduce the risks posed by deserialization vulnerabilities. Nevertheless, in our research, we found that the default Low permission configuration can be bypassed through certain technical means, allowing for a High permission deserialization process, ultimately achieving remote code execution.
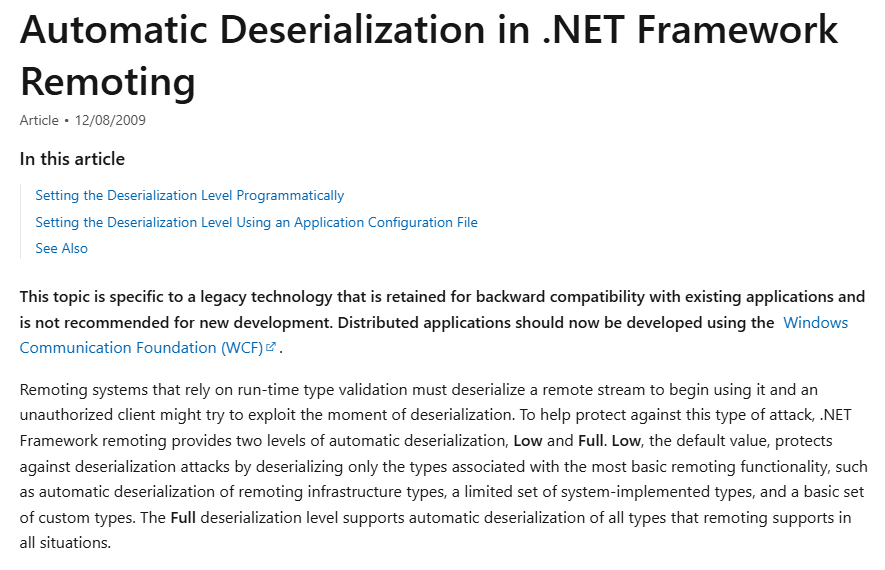
Figure 1 Microsoft Official Documentation
2.3 Deserialization Vulnerabilities
Despite Microsoft marking .NET Remoting as unsafe and warning developers to fully consider its security risks and implement corresponding security measures, we still found many software applications in industrial control systems improperly using this communication framework, leading to security vulnerabilities.
Table 1 Deserialization Vulnerabilities Caused by BinaryFormatter in .NET Remoting
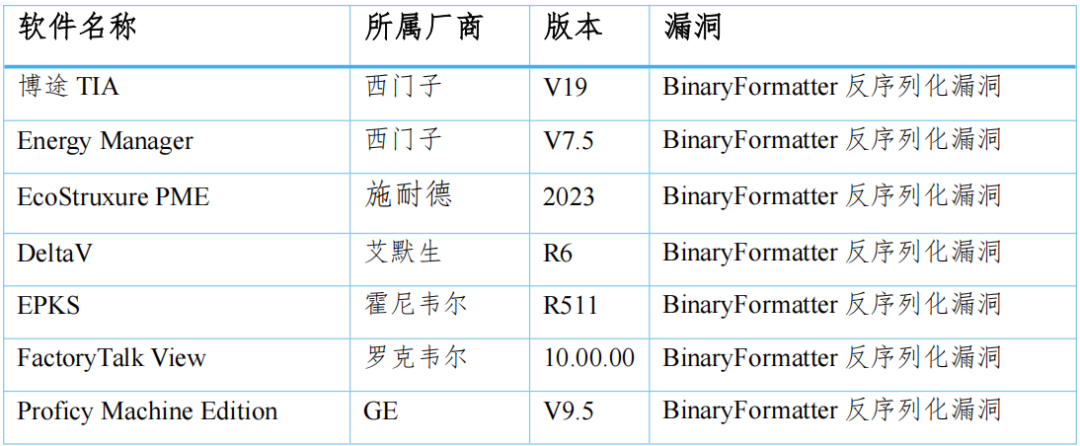
These vulnerabilities are caused by using BinaryFormatter for deserialization in .NET Remoting. The BinaryFormatter class was implemented before deserialization vulnerabilities became well-known security models in the industry, and therefore did not follow best security practices. This led to the BinaryFormatter.Deserialize method having deserialization vulnerabilities, allowing attackers to construct malicious objects, serialize them, and send them to the target system, triggering the vulnerability when deserialized using this method, enabling remote code execution.
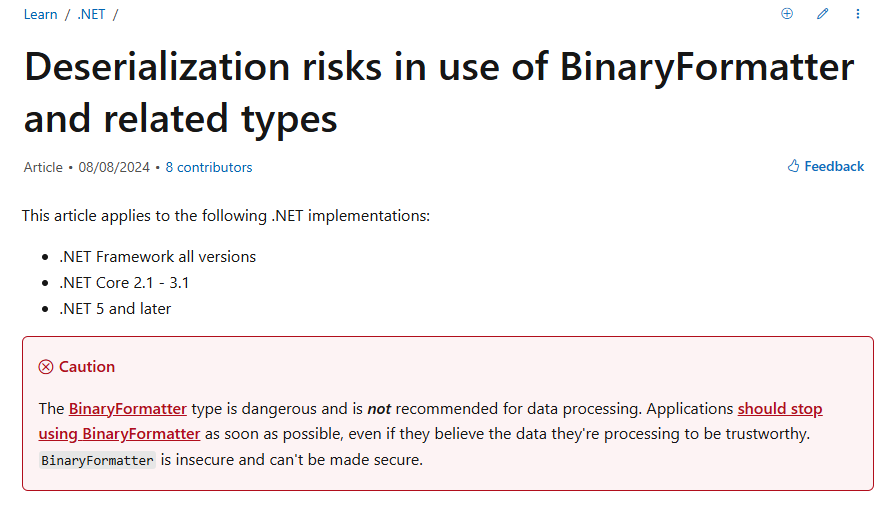
Figure 2 Security Vulnerabilities in BinaryFormatter Deserialization
Despite the deserialization vulnerabilities in BinaryFormatter, the Microsoft .NET team attributes this to a design choice rather than a vulnerability, and thus refuses to provide security updates for this issue. Instead, they leave the assessment of security risks when using BinaryFormatter to developers, allowing them to fully evaluate the scenarios in which they use BinaryFormatter in development and provide corresponding measures to filter and sanitize deserialization data. At the same time, developers must also assess the potential security risks when using this class. In this case, improper coding by developers is likely to introduce security vulnerabilities.
3. Mitigation Measures
The security vulnerabilities in industrial control systems are critical to the production safety of industrial enterprises. To address these vulnerabilities and minimize the attack surface faced by enterprises, companies should strengthen protective measures for hosts. Focused detection of shellcode used by attackers can be conducted from both static and dynamic detection perspectives.
Static detection methods typically use signature matching techniques, comparing known shellcode signatures (such as \xE8\xFF jump instructions) using YARA rules to detect some known shellcode.
Dynamic detection methods include sandbox behavior monitoring, entropy analysis, and control flow anomaly detection. Sandbox behavior monitoring simulates the entire system, providing a runtime environment for programs and comprehensively monitoring their execution processes to determine whether they are shellcode constructed by attackers; entropy analysis detects high-entropy code segments in memory (encrypted/compressed shellcode typically has an entropy value > 7.5) to determine whether it is shellcode; control flow anomaly detection verifies the legitimacy of return addresses to block ROP chain exploitation, achieving detection and prevention of shellcode.
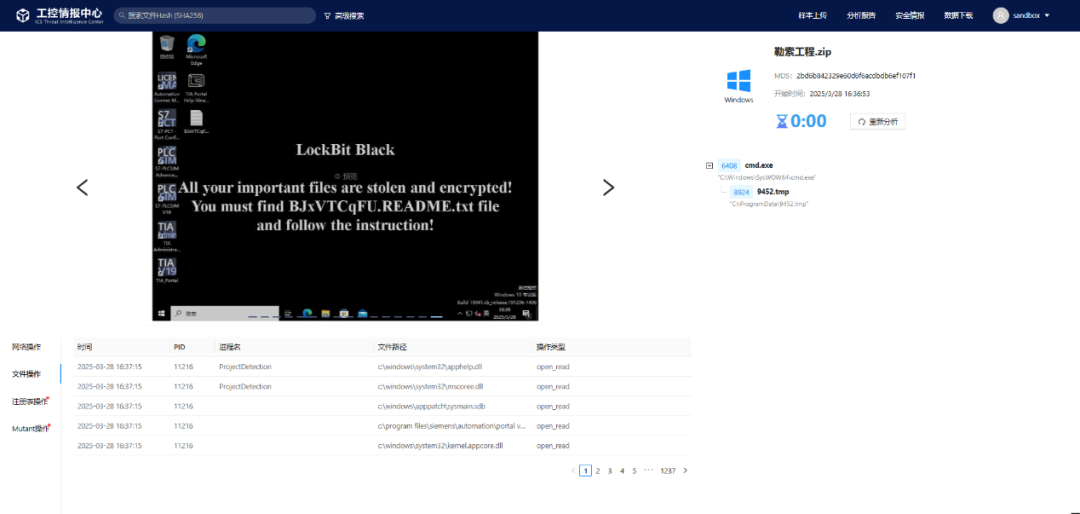
Figure 3 Sandbox Simulation Environment for Industrial Control Systems
The Polaris Industrial Control Security Joint Laboratory established by Shanghai Jiao Tong University and Zhejiang Guoli Network Security Technology Co., Ltd. has launched core functions of the industrial control intelligence center, including simulating typical industrial control microenvironments, pioneering industrial control file detection environments, and optimizing analysis processes for industrial control environments, supporting typical industrial control system sandbox simulation environments for in-depth analysis of malicious code or configuration files exploiting such vulnerabilities.
At the same time, enterprises should always pay attention to security announcements released by vendors and relevant security organizations regarding the industrial control system software they use, and promptly update to the latest versions.
4. References
[1]https://siebene.github.io/2023/03/27/Learning-Exploit-of-NET-Remoting/
[2]https://learn.microsoft.com/en-us/previousversions/dotnet/netframework-4.0/5dxse167(v=vs.100)
[3]https://malware.news/t/bypassing-low-type-filter-in-net-remoting/34189
[4]https://github.com/Y4er/dotnet-deserialization/blob/c8dac42dfc267d32492e18fe13a3ba5ef717b58c/NET%20Remoting.md
[5]https://github.com/tyranid/ExploitRemotingService

Company Profile
Company Profile
Zhejiang Guoli Network Security Technology Co., Ltd. adheres to the mission of “making control safer and users more assured”. With 30 years of accumulated industrial control technology and over a decade of industrial control security research, it has formed a unique and advantageous core technology, security products and service system, and complete industry solutions, with numerous clients in water conservancy, petroleum refining, oil and gas pipelines, urban gas, power energy, rail transit, intelligent manufacturing, etc., and is committed to becoming a world-class provider of comprehensive security solutions for critical infrastructure.