NB-IoT technology, with its advantages of full coverage, low power consumption, and low cost, overcomes the shortcomings of traditional IoT technologies, such as high power consumption, high costs, poor coverage, fragmentation, and difficulty in large-scale applications. It has been applied in various IoT application scenarios, including remote meter reading, asset tracking, smart healthcare, and smart agriculture. However, the security vulnerabilities associated with NB-IoT technology pose new challenges to its application in various fields.
In response to the security threats faced, we first analyze the security requirements of IoT based on NB-IoT technology. We also propose a security domain partitioning based on NB-IoT technology and depict a security reference model for IoT based on NB-IoT technology according to the security domain division. Finally, we combine the security reference model to propose a security functional architecture for IoT based on NB-IoT technology. The above research is of reference significance for the design of security protection based on NB-IoT technology.
NB-IoT (Narrow Band Internet of Things) is an emerging technology in the IoT field based on cellular communication, belonging to the Low Power Wide Area Network (LPWAN) technologies. It has advantages such as low power consumption, low cost, long distance, and wide connectivity, making it suitable for various application fields like remote meter reading, asset tracking, smart healthcare, and smart agriculture.
However, the application environment of NB-IoT is somewhat open, making wireless channels susceptible to eavesdropping and interference. At the same time, IoT devices face security threats such as access authentication, privacy protection, and unauthorized access. Additionally, the vast number of IoT terminals, their variety, limited computational capabilities, and constrained battery resources mean that traditional security protection measures cannot be deployed. Currently, many NB-IoT application providers in China have adopted “soft protection” to launch some solutions, but these solutions, given the generally weak computational capabilities of terminals, only address data encryption, which has limited effectiveness in securing IoT systems.
Therefore, further research is needed on security protection technologies for IoT based on NB-IoT technology to ensure system security and normal operation.
1 Analysis of Security Requirements for IoT Based on NB-IoT Technology
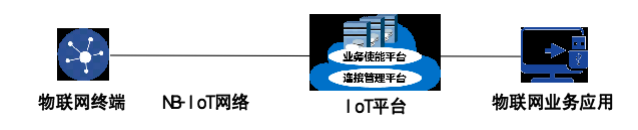
According to the methodology, the requirements of a system should be composed of the requirements of each component needed during the system’s operation. A typical NB-IoT application system information entity mainly consists of four information entities: IoT terminals, the operator’s NB-IoT network, the IoT platform, and IoT business applications.
The IoT terminals are mainly sensing devices based on NB-IoT, such as NB-IoT IoT terminals and NB-IoT smart locks. The operator’s NB-IoT narrowband IoT achieves communication connections from terminals to the IoT platform, while the IoT platform manages terminal connections and distributes and processes uplink and downlink data. The IoT business applications mainly consist of backend systems that aggregate, process, and display IoT business data, as shown in Figure 1.
Figure 1 Composition of Typical NB-IoT Application System Information Entities
Below, we propose the following analysis and thoughts on the security requirements of each information system entity.
IoT terminals are in a user application environment and have limited computing and storage capabilities, open wireless channels with narrow bandwidth, limited energy, and sporadic business. Therefore, they are susceptible to malicious destruction and information attacks. The main security threats include: key information acquisition, unauthorized access, impersonation of terminal nodes, malicious energy consumption, and malicious code/vulnerability attacks.
Key information acquisition mainly occurs through brute force dismantling, obtaining sensitive information stored in the IoT terminal’s memory devices, such as the terminal’s unique serial number ID, sensitive data, or communication keys, threatening the security of the entire perception layer network and user data security.
Unauthorized access mainly refers to unauthorized users sending control commands to IoT terminals, causing them to report data or force them to execute illegal operations, leading to sensitive data leakage and control chaos.
Impersonation of terminal nodes mainly occurs by capturing IoT terminals to inject fake code or copying the unique serial number of IoT terminals to disguise as normal IoT terminals, eavesdropping on and interfering with the normal communication of other IoT terminals, causing data leakage and system business disruption.
Malicious energy consumption mainly occurs by continuously sending wake-up commands to IoT terminals within the coverage area, forcing them to work continuously, leading to energy depletion and inability to operate normally.
Malicious code/vulnerability attacks mainly occur by scanning for software vulnerabilities in IoT terminals and injecting malicious code, Trojans, worm viruses, etc., leading to key information leakage and even turning into zombie nodes, thereby launching DoS attacks on the network.
The NB-IoT network provides wide area network connections for IoT terminals and the IoT platform or backend applications. The NB-IoT network is a public network provided by the operator, with business applications sharing wireless air channels and C-SGN core network resources with other industries or personal businesses. Therefore, data exchanged on the NB-IoT network faces security threats such as data interception, malicious tampering, privacy information leakage, and security policy conflicts.
Data interception mainly occurs through eavesdropping on the wireless air interface to capture and analyze transmitted data, obtaining a large amount of sensitive information; intercepting and analyzing data transmitted over mobile communication wide area networks, leading to data leakage for IoT operating enterprises.
Malicious tampering of data mainly occurs through man-in-the-middle attacks, altering the data exchanged between IoT terminals and RAN; intercepting and tampering with data transmitted over wired connections.
Privacy information leakage mainly occurs when internal personnel of the operator exploit vulnerabilities in operational management to obtain sensitive data from IoT operating enterprises and users, including user identity information, leading to sensitive information leakage.
Security policy conflicts mainly arise due to the integration of heterogeneous networks, which may lead to conflicts in security policy settings, mainly reflected in conflicts between the security policy settings of the operator’s network and the user’s network.
The IoT platform provides connection management functions for terminals and application support functions for backend applications. In most cases, the IoT platform operates on public clouds, sharing cloud infrastructure with other cloud tenants. Additionally, the IoT platform is often directly connected to the internet, which may expose it to security threats from the internet. Therefore, the main security threats include DDoS attacks, unauthorized access, malicious code/vulnerability attacks, and privacy information leakage.
DDoS attacks mainly occur when a large number of IoT terminals are exploited by attackers, sending a large number of request messages (such as ICMP, TCP SYN, etc.) to the IoT platform, causing congestion or service unavailability in the IoT platform network.
Unauthorized access mainly refers to unauthorized users accessing the IoT platform through application systems, using various services provided by the IoT platform, and performing operations that exceed permission levels, including unauthorized remote read/write of user sensitive data and remote execution of critical operations.
Virus/vulnerability attacks mainly occur because the IoT platform consists of a large number of software systems and is connected to external networks. Malicious code, Trojans, worm viruses, etc., can easily spread through the network to the IoT platform, causing abnormal service or even paralysis of the IoT platform.
Privacy information leakage mainly occurs when internal personnel exploit management vulnerabilities of the IoT platform to obtain sensitive data from IoT operating enterprises and users, including user identity information, leading to sensitive information leakage.
Data loss may occur unexpectedly due to failures or attacks on the IoT platform, potentially leading to unexpected loss or destruction of operational data for IoT operating enterprises, causing significant losses.
( 4 ) IoT Business Applications
IoT business applications are located within the application environment of the IoT application system, connecting to the IoT platform or operator network via wired networks, thus enabling data exchange with IoT terminals. The main security threats come from connections to external networks, including unauthorized access, malicious code/vulnerability attacks, and privacy information leakage.
Unauthorized access mainly refers to unauthorized users accessing the IoT application system and performing operations that exceed permission levels, including obtaining sensitive information, querying and analyzing business operational data, and remotely executing illegal operations, leading to economic losses for IoT operating enterprises.
Virus/vulnerability attacks mainly occur because IoT applications consist of a series of software systems connected to the IoT platform via external networks, making them susceptible to attacks from external networks and various malicious codes, Trojans, worm viruses, etc., causing abnormal operation or even paralysis of the IoT application system.
Privacy information leakage mainly occurs when internal personnel exploit management vulnerabilities in the IoT application system to obtain sensitive data from operating enterprises and users.
2 Research on IoT Security Technology Based on NB-IoT
2.1 Security Domain Partitioning
According to the “top-down” design principle in the methodology, after understanding the security requirements, the first step is to partition the security domains, which is a prerequisite for network structure design. Different domains should implement different security protection strategies. Based on the composition of the IoT application system, the system can be roughly divided into four security domains: terminal security domain, network security domain, platform security domain, and application security domain.
( 1 ) Terminal Security Domain
This domain refers to the terminal system security domain where smart IoT terminals are located, including IoT terminals, smart controllers, communication modules, software systems, and terminal data, etc. The protection of the terminal security domain is mainly the responsibility of the IoT operating enterprises.
( 2 ) Network Security Domain
This domain refers to the network system security domain where the public communication network connecting IoT and the IoT platform is located, specifically referring to the operator’s NB-IoT cellular IoT, including NB-IoT’s RAN, C-SGN, etc. The composition entities and operating environment of the network security domain are provided by the network operator, and the security protection of this domain is mainly the responsibility of the NB-IoT operator.
( 3 ) Platform Security Domain
This domain refers to the service system security domain where cloud service systems providing terminal connection management and business support functions are located, including cloud infrastructure, connection management platforms, business enabling platforms, etc. The composition entities and operating environment of the platform security domain are provided by IoT platform manufacturers, and the security protection of this domain is mainly the responsibility of IoT manufacturers.
( 4 ) Application Security Domain
This domain refers to the application system security domain where the backend applications of the IoT application system are located, including computing infrastructure, network infrastructure, application software systems, application data, etc. The application security domain is in the application environment of the IoT operating enterprise, and the security protection of this domain is mainly the responsibility of the IoT operating enterprise.
Among the above four security domains, except for the network security domain and platform security domain, the other two security domains require IoT operating enterprises to provide security protection measures to ensure security for terminals and applications.
2.2 Security Reference Model
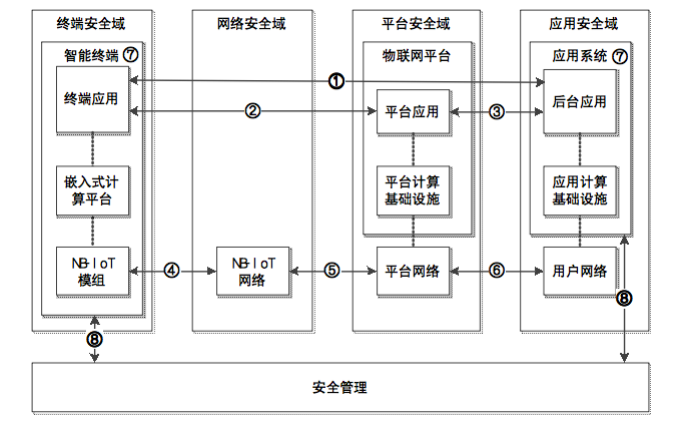
Based on the security domain partitioning above, the functions in the system are partitioned into four security domains according to their locations, while adding security management functional entities to implement security management and control for the IoT system based on NB-IoT technology, depicting the security reference model for the NB-IoT application system, as shown in Figure 2.
Figure 2 Security Reference Model for IoT Terminal Application System
As shown in Figure 2, the model defines eight security functional groups, each corresponding to a set of security functions between functional entities, addressing the security issues of information exchange between entities. These eight functional groups are:
( 1 ) Terminal and Backend Application Security Interaction Function
Provides end-to-end business security interaction functions for the IoT terminal application system, addressing trust issues between terminals and backend systems at the application layer, as well as ensuring the confidentiality and integrity of business data exchange between terminals and backend systems.
( 2 ) Terminal and Platform Application Security Interaction Function
Establishes a secure connection between terminals and the IoT platform, providing secure data transmission functions from terminals to the IoT platform, addressing the security of terminal access to the IoT platform and the security of data transmission.
( 3 ) Platform and Backend Application Security Interaction Function
Establishes a secure connection between backend applications and the IoT platform, providing secure data transmission functions from backend applications to the IoT platform, addressing the security of backend applications accessing the IoT platform and the security of data transmission.
( 4 ) Terminal Wireless Access Security Function
Establishes a secure connection from terminals to the operator’s network, providing confidentiality and integrity protection functions for air interface data, addressing the security of terminal access to the operator’s network and the security of air interface data transmission.
( 5 ) Operator Network and IoT Platform Network Security Interaction Function
Establishes a secure connection from the operator’s network to the IoT platform network, providing confidentiality and integrity protection functions and network boundary protection functions, addressing the security of information exchange between the operator’s network and the IoT platform network, as well as access control issues for the operator’s and platform networks.
( 6 ) Platform Network and User Network Security Interaction Function
Establishes a secure connection from the user network to the platform network, providing confidentiality and integrity protection functions and network boundary protection functions, addressing the security of information exchange between the user network and the platform network, as well as access control issues for the user and platform networks.
( 7 ) Terminal/Application System Device Security Function
Provides security protection functions for IoT terminals and application system devices, addressing the security and trustworthiness of the operating environment for terminals and application system devices.
( 8 ) Security Management Function
Provides security management functions for IoT terminals and backend applications, including monitoring of security components within terminals and application systems, key management, and identity management.
Among the eight functional groups above, (1) to (3) are application security protection functions, (4) to (6) are network security protection functions, (7) is device security protection functions, and (8) is management security functions.
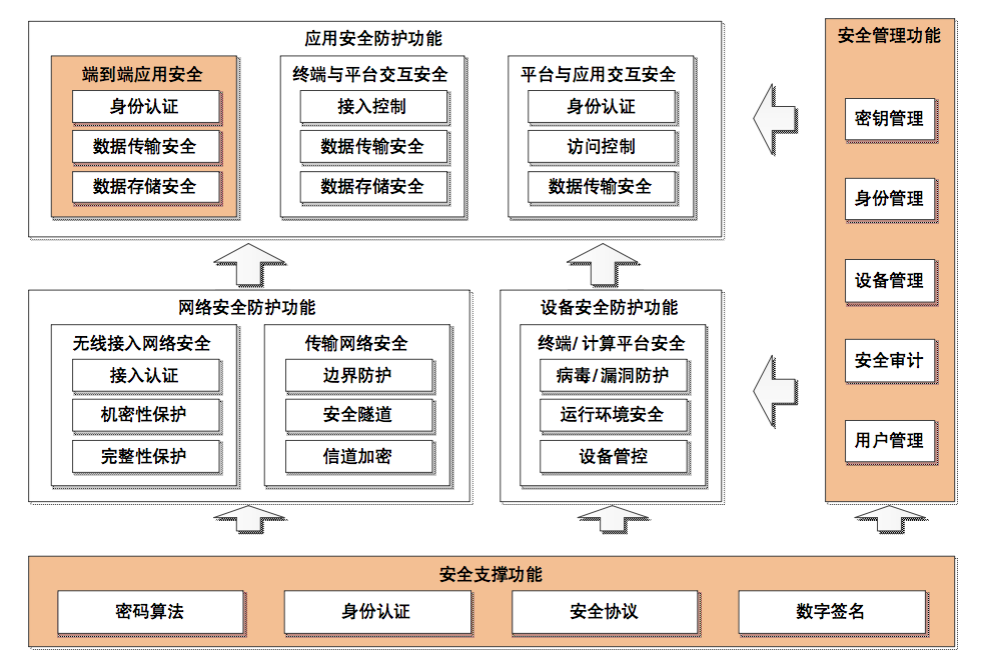
2.3 Security Functional Architecture
Based on the eight functional groups defined in the system security reference model, these functional groups can be divided into five categories: application security protection functions, network security protection functions, device security protection functions, and security management functions, while providing security technical support for the above four categories with security support functions. The specific security protection functions for each category are shown in Figure 3.
Figure 3 Security Functional Architecture for IoT Terminal Application System
As shown in Figure 3, it lists the complete security functional architecture of the IoT terminal application system.
( 1 ) Application Security Protection Functions
The application security protection functions mainly ensure end-to-end application security, security of interactions between terminals and platforms, and security of interactions between platforms and applications. Among them, the security of interactions between terminals and platforms and between platforms and applications is mainly provided by NB-IoT operators and IoT platform providers, which are relatively mature in terms of security protection technology. The key focus is to ensure end-to-end application security between IoT terminals and IoT business applications.
The security protection of IoT terminals can be achieved through a mutual authentication mechanism between the terminal and backend applications, ensuring mutual identification and completing session key negotiation, while utilizing the session key to ensure the confidentiality and integrity of the data exchange process.
In end-to-end application security, identity authentication is used to achieve mutual identification and establish secure sessions between IoT terminals and IoT business applications. This prevents impersonation of terminals or backend applications from accessing real backend applications and terminals, ensuring the trustworthiness of the subjects and objects in business data exchanges. Moreover, the severe limitations of IoT resources make traditional security protocol technologies, which have high computational, storage, and communication overheads, unsuitable for application. Therefore, lightweight identity authentication protocols need to be adopted.
Data security transmission mainly utilizes cryptographic technology to ensure the confidentiality and integrity of the business data transmission process.
Data security storage is mainly used for the secure storage of sensitive data in IoT terminals and IoT application systems.
( 2 ) Network Security Protection Functions
Network security protection mainly ensures the security of wireless access networks and transmission networks.
Wireless access network security mainly relies on NB-IoT operators to complete mutual access authentication between the NB-IoT base stations and IoT terminals.
Transmission network security mainly refers to the secure transmission channels between the IoT platform and IoT business applications, which can be realized through traditional IPSEC, SSL, AKA, etc.
( 3 ) Device Security Protection Functions
Device security protection mainly ensures the security of terminals/computing platforms, primarily achieved through OS hardening, firmware security, trusted computing, etc., to ensure the security of the local operating environment of IoT terminals. Additionally, for specific industry applications with high security protection requirements, low-power security chips or security protection modules may be used to provide corresponding security functions.
( 4 ) Security Management Functions
Security management functions mainly include key management, identity management, device management, security auditing, and user management.
Key management mainly implements the full lifecycle management functions of keys used in cryptographic algorithms, including key generation, distribution, and destruction.
Identity management mainly manages the identities of IoT terminals based on the IoT identification system.
Device management mainly refers to the management of parameter configurations and status collection of various security management function information entities.
Security auditing mainly records security behaviors and events in the system for retrospective security behavior tracing.
User management mainly involves account management and access control functions for security system operation and maintenance personnel, categorizing user accounts, controlling access permissions for accounts, and managing the number of online users.
( 5 ) Security Support Functions
Security support includes cryptographic algorithms, lightweight identity authentication protocols, and digital signatures, mainly providing technical support for the above security functions.
This article conducts an in-depth analysis of the security requirements of various information system entities based on NB-IoT technology, while partitioning the system into terminal security domain, network security domain, platform security domain, and application security domain, and proposing a security reference model and security functional architecture.
Considering the overall security of IoT based on NB-IoT technology, the network security domain and platform security domain are respectively managed by NB-IoT operators and IoT platform providers, both of which have relatively mature security protection technology and comprehensive security measures.
Therefore, the weak point in the overall security protection of the system lies with the IoT security operating enterprises, making the research content of this article of certain reference significance for IoT operating enterprises in their security protection design.
Original source: Information Security and Communication Confidentiality Journal