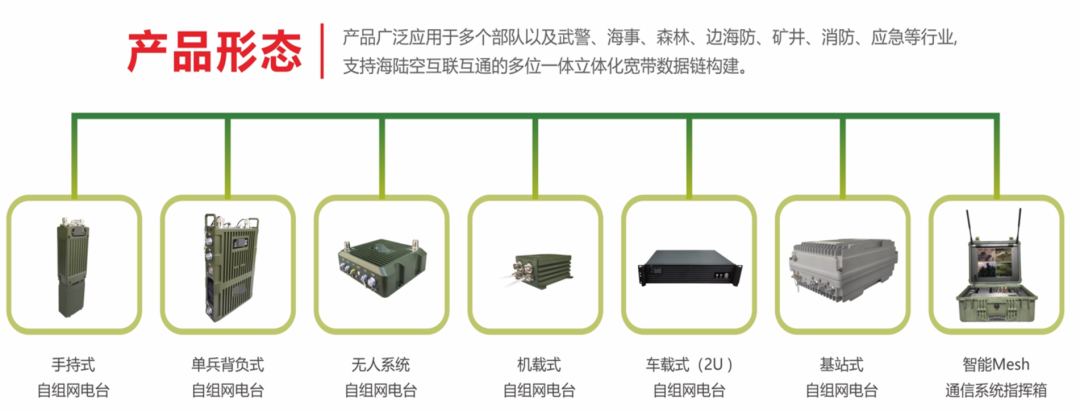
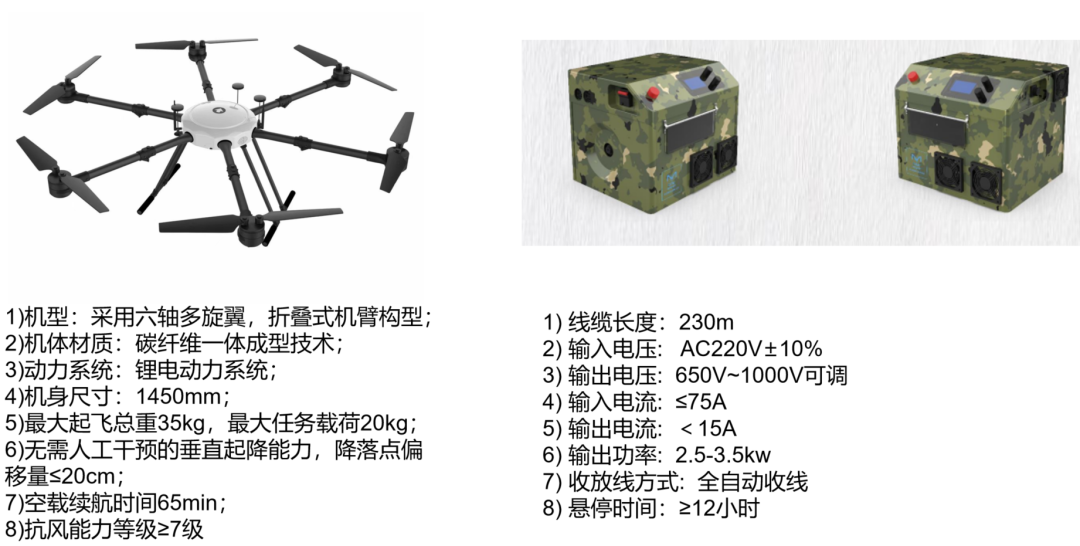
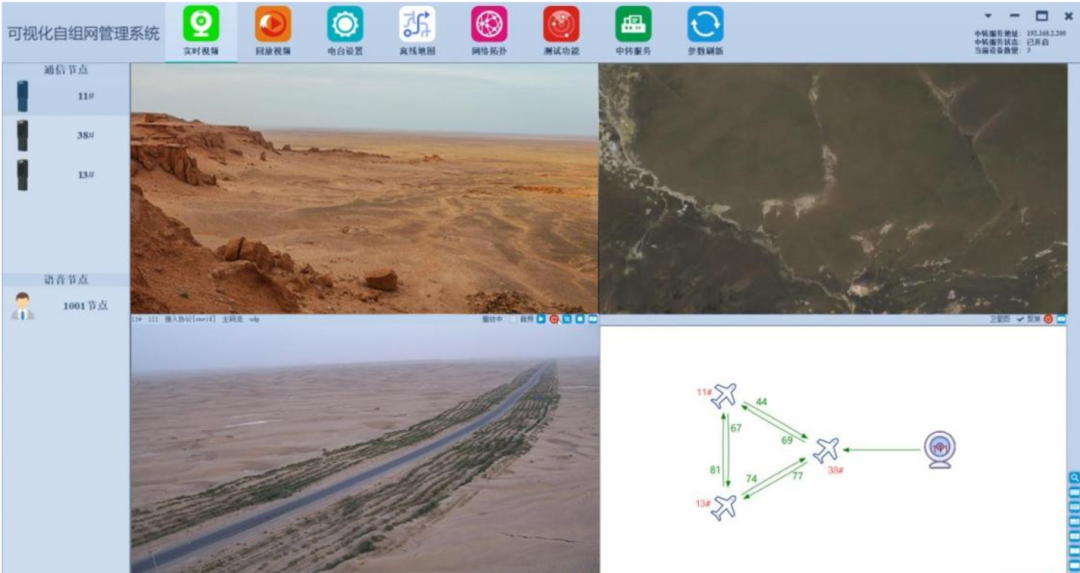
Introduction
- Definition and Core Characteristics of Ad Hoc Networks
- Key Technologies of Ad Hoc Networks (Routing Protocols, Topology Management, Security Mechanisms, etc.)
- Typical Application Scenarios of Ad Hoc Networks (Military, Emergency, IoT, V2X, etc.)
- Recommended Solutions
Question 1: How to communicate on a battlefield without base stations?
On the battlefield in Syria, a special forces unit infiltrated behind enemy lines, all satellite signals were jammed, and traditional communication equipment failed. However, the micro-devices on soldiers’ helmets automatically formed a mesh network, sharing locations and transmitting commands in real-time; aerial drone swarms autonomously adjusted their formations, relaying high-definition images back to command—these scenarios are made possible entirely byad hoc network technology. This “decentralized” black technology is rewriting the rules of modern warfare.
Question 2: How does ad hoc networking address the three major pain points of battlefield communication?
Pain Point1: Rapid Deployment
Traditional Solution: During the Gulf War, the U.S. military needed 3 days to set up a communication network in the combat zone.
Networking Solution: Soldier devices connect to the network upon startup (<1 second), drone swarms autonomously form networks (<30 seconds). Example: The Russian military’s “Warrior” soldier system allows a 20-person squad to establish a 10km² tactical network in 2 minutes.
Pain Point2: Anti-jamming
Records from the Ukrainian battlefield show that ad hoc network systems have an error rate of only0.001%
Pain Point3: Covert Communication
The U.S. military’s “Tactical Ground Reporting System” (WIN-T) enablessilent communication.
Question 3:How to solve communication for drone swarm operations—long-distance reconnaissance and strike?
1. Reconnaissance aircraft detect targets → 2. Electronic warfare drones jam signals → 3. Attack aircraft deploy munitions → 4. Assessment aircraft relay results
Question 4:Intelligent Soldier Systems—How to turn soldiers into information nodes?
First, helmet sensors (wearable smart equipment for data transmission): monitor vital signs and positioning;
Second, handheld terminals: display battlefield GIS3D maps, situational awareness, real-time transmission of on-site information to command, receiving directives from command;
Third, weapon IoT: real-time reporting of ammunition stock, allowing all levels to monitor ammunition and equipment damage ratios, providing logistics with sufficient information for supply decisions;
Fourth, data capabilities—automatically filter key information for transmission, allowing each command level to extract data from respective units to support operational simulations.
Question 5: Armored Cluster Coordination—How to make heavy weapon visuals and vehicle systems into battlefield information extractors?
Tanks communicate directly, bypassing the command chain (response speed increases10 times), inter-vehicle data link transmission rates must exceed 50M, enabling broadband transmission, sharing fire control radar data, and achieving integrated deployment of target shooting. The German “Leopard 2A7+” tank group uses ad hoc networking to achieve “1 detection = all aiming.
Question 6: Battlefield IoT—How to achieve one-stop interconnection for combat, logistics, medical, and support during training and combat?
Devices can connect as much as possible (encryption must be effective); smart mines: automatically report location after triggering; if ammunition box stock falls below20%, automatically request resupply (similar to JD’s automatic refrigerator restocking); when a medical kit is opened, it immediately calls for rescue (in the event of an accident involving a new energy vehicle, it automatically connects to the manufacturer for help).
Question 7: Emergency Communication Network—How to assess the resilience of commonly used communication links? What is Plan B?
Extreme case: In the 2011 operation that killed Osama bin Laden, Navy SEALs maintained communication inside a cave using ad hoc networks. If common links can still transmit critical commands with 50% damage, if not, an emergency communication network must be established, deployed in a timely manner, as opportunities are fleeting.
Question 8:AI command decision-making is essential; how to explore machine takeover of tactics?
1. Frontline sensors collect data → 2. Edge computing nodes analyze → 3. Automatically generate multiple operational plans → 4. Commander revises → execute with one click.
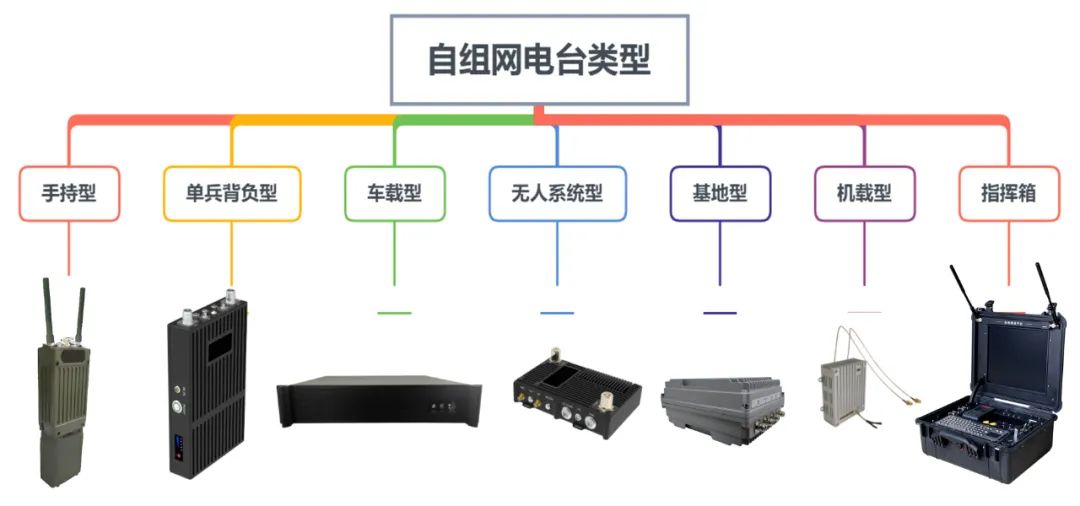
BodyDefinition and Core Characteristics of Ad Hoc NetworksAd Hoc Networks are wireless communication networks that are dynamically formed by mobile nodes without fixed infrastructure, achieving intelligent interconnection between devices through multi-hop relaying. They possess core characteristics of “decentralization, self-organization, and strong resilience,” often referred to as “breathing neural networks”. The essential difference between ad hoc networks and traditional networks (such as cellular networks and fiber optic networks) lies in their decentralized architecture and dynamic adaptability. Dynamic routing protocols, such as AODV (Ad hoc On-Demand Distance Vector) and DSR (Dynamic Source Routing), calculate optimal paths in real-time. Distributed channel access employs CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) or TDMA (Time Division Multiple Access) to avoid signal conflicts. Security mechanisms use encryption algorithms (such as AES), key management, and intrusion detection to resist attacks..
| Field | Application Case |
|---|---|
| Military Communication | Cooperative operations of battlefield drone swarms, soldier communication systems |
| Emergency Rescue | Rapid establishment of temporary communication networks after earthquakes, supporting voice and video transmission back to command centers |
| Smart Transportation | Real-time exchange of traffic information between vehicles in V2V/V2I, reducing traffic accidents |
| Industrial IoT | Sensor networks in oil fields and mines for equipment status monitoring |
| Drone Swarms | Swarm drones synchronize flight paths and task instructions through ad hoc networks |
|
Scenario |
Ad Hoc Network Solution |
Traditional Communication Solution |
|
Frontline Assault |
Soldier radio ad hoc network |
Requires pre-established base stations |
|
Drone Swarm |
200 drones autonomously forming a network |
Relies on ground control centers |
|
Communication Resilience |
30% node loss still operational |
Base station damage leads to paralysis |
Ad hoc networks differ fundamentally from traditional networks (such as cellular networks and fiber optic networks) in their decentralized architecture and dynamic adaptability, specifically manifested as: First, a decentralized architecture. All nodes are equal, without central control devices such as base stations or routers. Each node functions as a terminal, router, and relay, dynamically selecting transmission paths through distributed algorithms. Second, a dynamic topology. The network topology changes in real-time as nodes move, join, or leave. For example, in a drone swarm executing a mission, if some nodes fail and drop out, the remaining nodes can automatically reconfigure communication links. Third, multi-hop relay communication. Nodes achieve long-distance communication through multi-hop forwarding. For instance, in forest fire rescue, if node A cannot directly contact the command center, it can relay data through nodes B and C. Fourth, self-organization and self-healing capabilities. The network automatically completes node discovery, route establishment, and fault recovery. For example, in military battlefields, even if 30% of nodes are destroyed, the remaining nodes can still reconstruct communication links. Fifth, resilience and flexibility. It adapts to extreme environments (such as earthquakes and battlefields), requiring no pre-set infrastructure and can be rapidly deployed within minutes.Key Technologies of Ad Hoc NetworksRouting protocols, topology management, security mechanisms, etc.
|
Protocol Type |
Representative Protocol |
Applicable Scenarios |
Advantages |
Challenges |
|
Proactive |
DSDV |
Low mobility networks |
Low latency |
High control overhead |
|
On-demand |
AODV |
High dynamic networks |
Strong flexibility |
Routing discovery delay |
|
Hybrid |
ZRP |
Large-scale networks |
Performance balance |
High complexity in partition management |
|
Geographic |
GPSR |
Dense nodes |
Energy-efficient |
Dependent on location information |
|
Intelligent |
QGeo |
Dynamic complex environments |
Adaptive optimization |
High computational resource demand |
Typical Application Scenarios of Ad Hoc Networks include military, emergency, IoT, V2X, etc.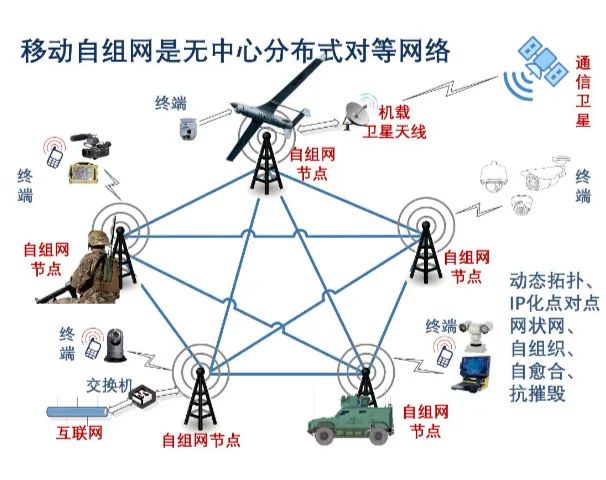
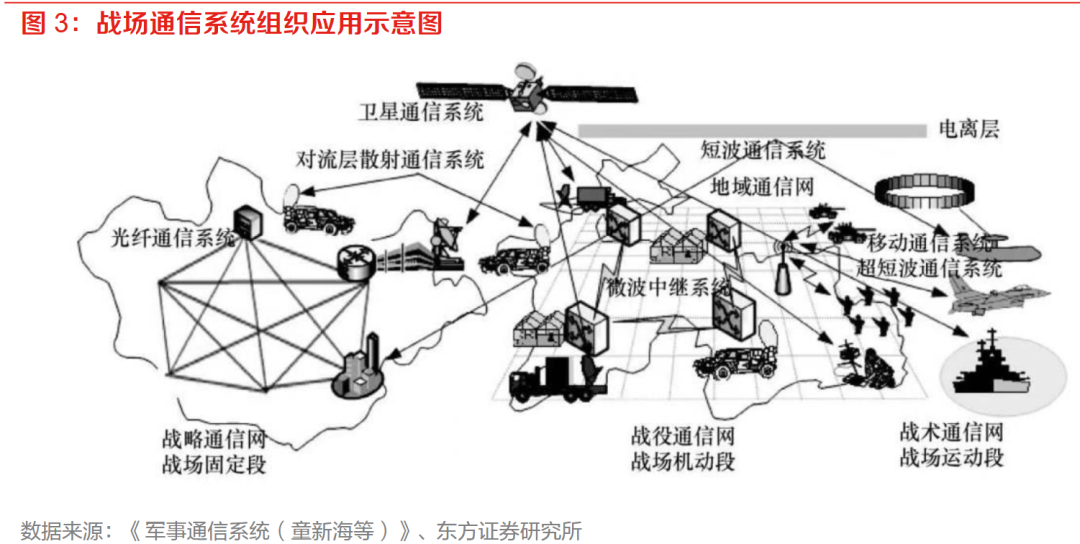
The U.S. military is focusing on developing broadband ad hoc network technology to meet the communication networking needs of mosaic warfare. Compared to traditional tactical communication, the communication networking model in mosaic warfare has higher technical requirements: First, in terms of network hierarchy, the communication networking in mosaic warfare completely abandons hierarchical network structures, replacing them with a super flat network, i.e., a large-scale self-organizing network. Second, in terms of ad hoc networking mode, compared to traditional pre-planned, relatively static ad hoc networking modes, the ad hoc networking in mosaic warfare must evolve from static networking to dynamic self-organizing networks. In traditional ad hoc networks, the data plane and control plane cannot be separated, failing to address the two challenges faced by mosaic warfare communication networking. After adopting broadband self-organizing network technology, the data plane and control plane are separated, allowing a series of new key technologies to be applied to the design of mosaic warfare communication networking. The U.S. military’s most advanced waverelay technology network fully supports the Army’s MANET network (wireless ad hoc networks) with ad-hoc self-forming networks.
 Data source: Battle Armor Military Supplies Data Network.
Data source: Battle Armor Military Supplies Data Network.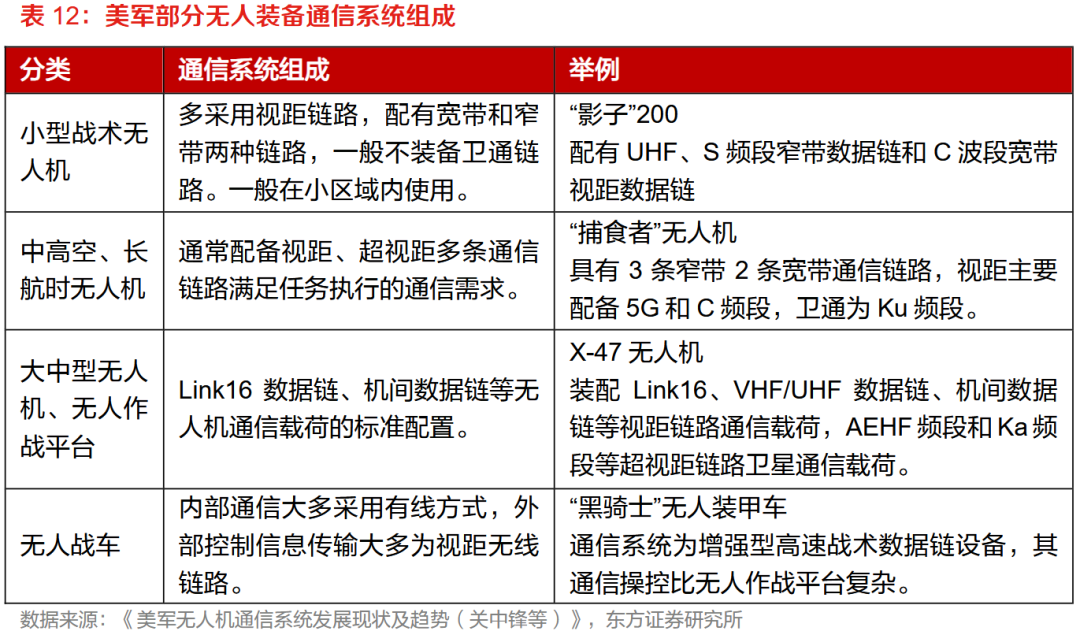
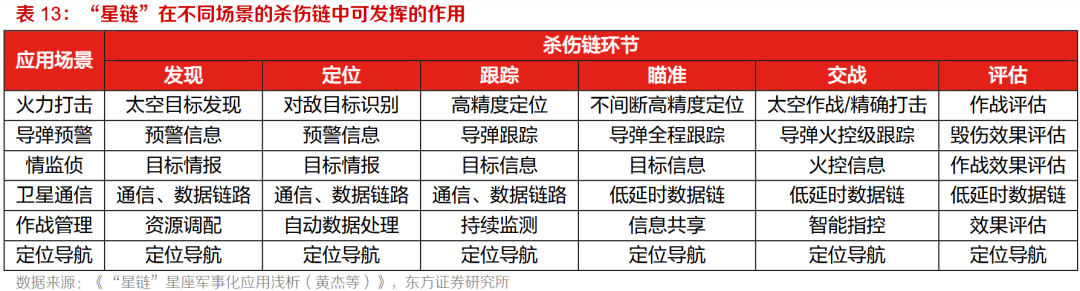
Link-16 data link plays a crucial role in the U.S. military’s tactical system, enabling the U.S. and its allies to share near real-time tactical information, enhancing battlefield situational awareness among various units in the theater, including location information, text messages, images, voice, and data. Link-16 aggregates tactical information obtained from various detection systems such as satellites, reconnaissance aircraft, and early warning aircraft, distributing it to U.S. military units in the theater, allowing commanders at all levels to synchronize near real-time battlefield awareness, creating necessary conditions for rapid command decision-making, tactical maneuvering, and tactical control in large-scale joint operations. Link-16 has been widely equipped to U.S. military vessels (such as Navy aircraft carriers, cruisers, destroyers, and amphibious assault ships), early warning aircraft (such as the Air Force’s E-3A “Sentry” and the Navy’s E-2C “Hawkeye”), fighter jets (such as the Air Force’s F-15, F-16, and the Navy’s F/A-18A and F-14 carrier-based fighters), bombers (B-1, B-2, and B-52 strategic bombers), reconnaissance aircraft, and command control aircraft (such as the Air Force’s RC-135 strategic electronic reconnaissance aircraft, E-8 Joint Surveillance Target Attack Radar System aircraft, EC-130 airborne battlefield command and control center, and the Navy’s P-3 reconnaissance patrol aircraft), as well as the Army’s ground command control centers and “Patriot” missile defense systems.
Other Scenarios
1. Natural Disaster Response: After natural disasters such as earthquakes and floods, traditional communication facilities are often damaged. At this time, a decentralized ad hoc network can quickly establish a temporary communication network for communication between rescue teams and reporting disaster conditions to the outside world. Rescue teams can carry portable communication devices (such as handheld terminals, vehicle-mounted base stations, etc.), which can automatically form networks without manual intervention.
2. Emergency Medical Rescue: At disaster sites, medical personnel can quickly establish communication links through decentralized ad hoc networks to share patient information, medical guidance, and other critical data. By connecting with external medical institutions through ad hoc networks, they can obtain remote medical consultations and technical support.
3. Search and Rescue Operations: Rescue team members can use ad hoc networks for real-time location sharing and task assignment, improving search and rescue efficiency. Drones can be part of the ad hoc network to expand communication range and collect information from disaster areas.
4. Public Safety and Law Enforcement: In the event of terrorist attacks, large-scale protests, and other emergencies, police and fire departments can use decentralized ad hoc networks for rapid response and effective command. Different departments can achieve information sharing through ad hoc networks, enhancing the speed and efficiency of emergency responses.
5. Urban Emergency Management Systems: In emergencies, traffic lights and other infrastructure may fail. A decentralized ad hoc network can help coordinate traffic flow and reduce congestion. When power facilities are damaged, ad hoc networks can be used to coordinate the allocation of emergency power resources.
|
Scenario |
Ad Hoc Network |
Cellular Network |
Satellite Communication |
|
Military Field |
Tactical communication, drone swarm coordination[11][104] |
Urban garrison communication |
Ocean-going vessels, theater command[88][104] |
|
Emergency Rescue |
Rapid deployment of temporary communication networks[17][162] |
Dependent on base stations, prone to paralysis after disasters |
Wide area coverage in disaster zones[88][119] |
|
IoT |
Industrial sensor networks[17][162] |
Smart homes, vehicle networks[32][44] |
Agriculture/Marine monitoring[88][119] |
|
Remote Areas |
Limited coverage (requires dense nodes) |
High cost of base station construction |
Only feasible solution (e.g., deserts, polar regions) |
|
Urban High Density |
Prone to interference, low applicability |
Optimal choice (5G millimeter wave supports high density) |
Supplementary coverage (e.g., underground parking lots) |
Comparison
|
Dimension |
Ad Hoc Network |
Cellular Network |
Satellite Communication |
|
Architecture |
Distributed, no central node |
Centralized, reliant on base stations and core networks |
Star topology, reliant on satellites and ground stations |
|
Routing Mechanism |
Dynamic multi-hop routing (e.g., flooding,AODV protocol) |
Single-hop access to base stations, centralized routing in core network |
Inter-satellite links or ground station relays |
|
Frequency Spectrum Management |
Dynamic shared channels, prone to interference |
Fixed frequency band allocation, reuse technology enhances efficiency |
Fixed frequency band allocation, requires coordination of international resources |
|
Mobility Support |
High (supports rapid node movement) |
Medium (relies on base station handover mechanisms) |
Low (terminals must maintain stable connections to satellites) |
|
Resilience |
Extremely strong (no single point of failure) |
Weak (base station failure leads to local paralysis) |
Medium (satellite failure requires backup satellites) |

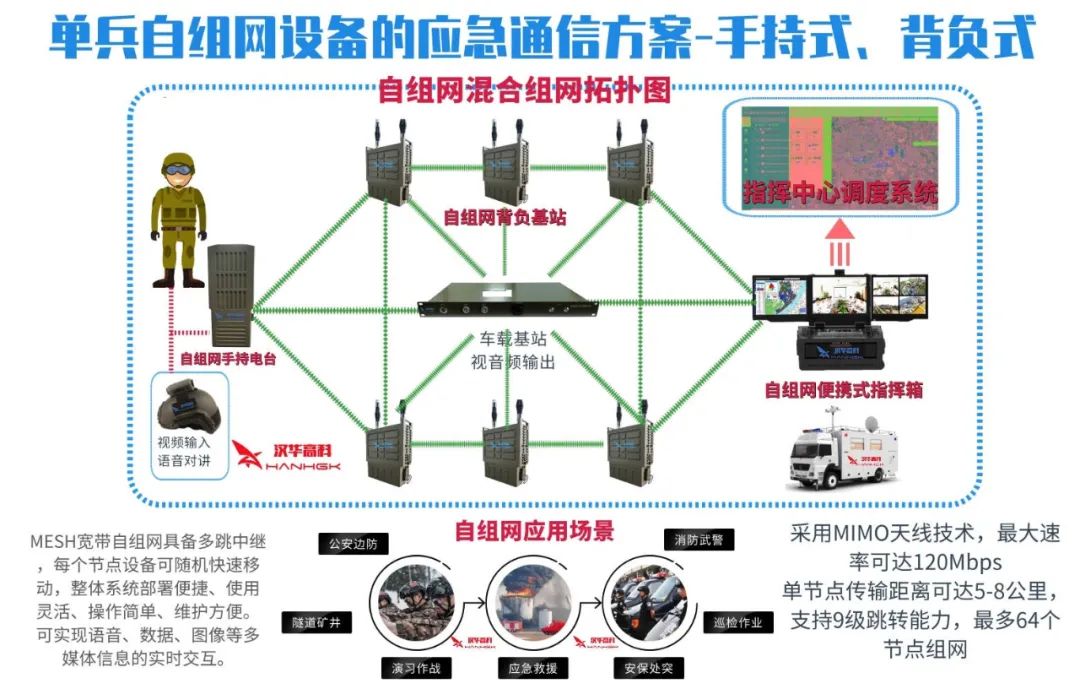
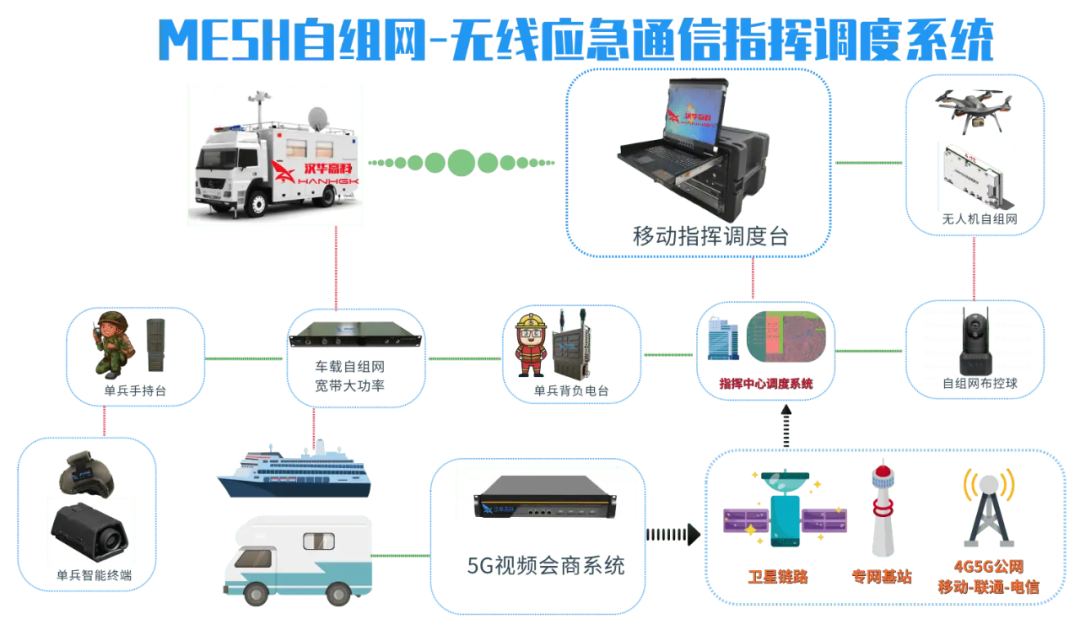 (The above images are sourced from the internet, primarily for academic exchange, not for other uses; please delete if infringing)
(The above images are sourced from the internet, primarily for academic exchange, not for other uses; please delete if infringing)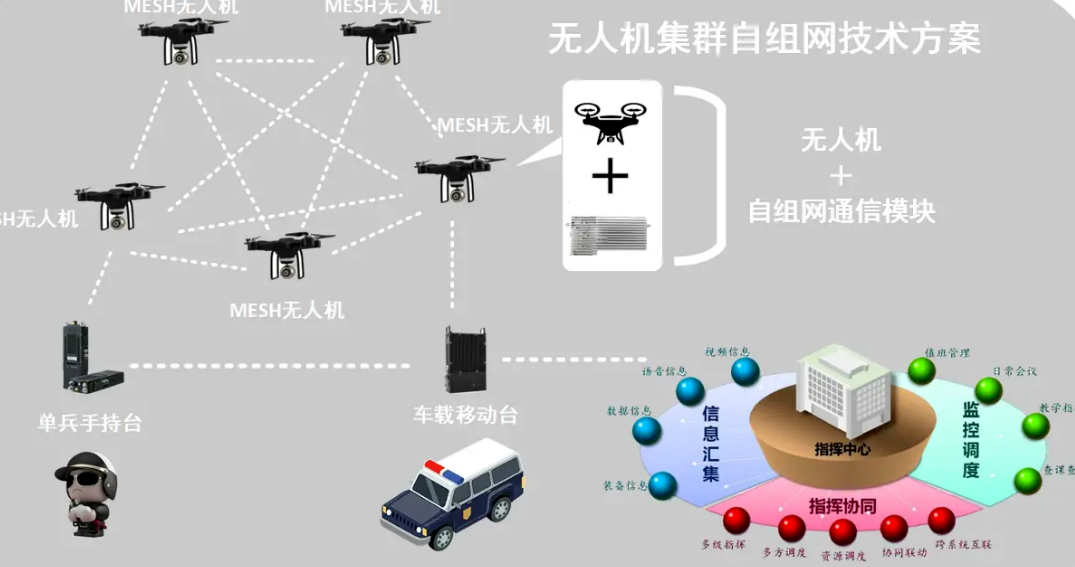
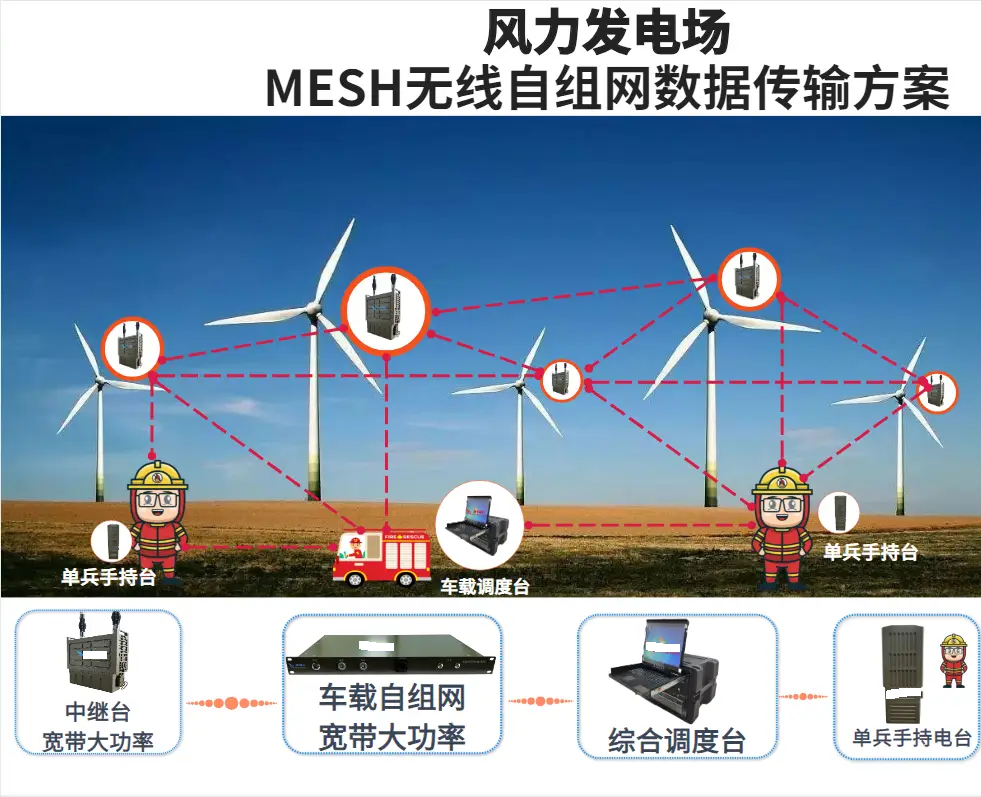
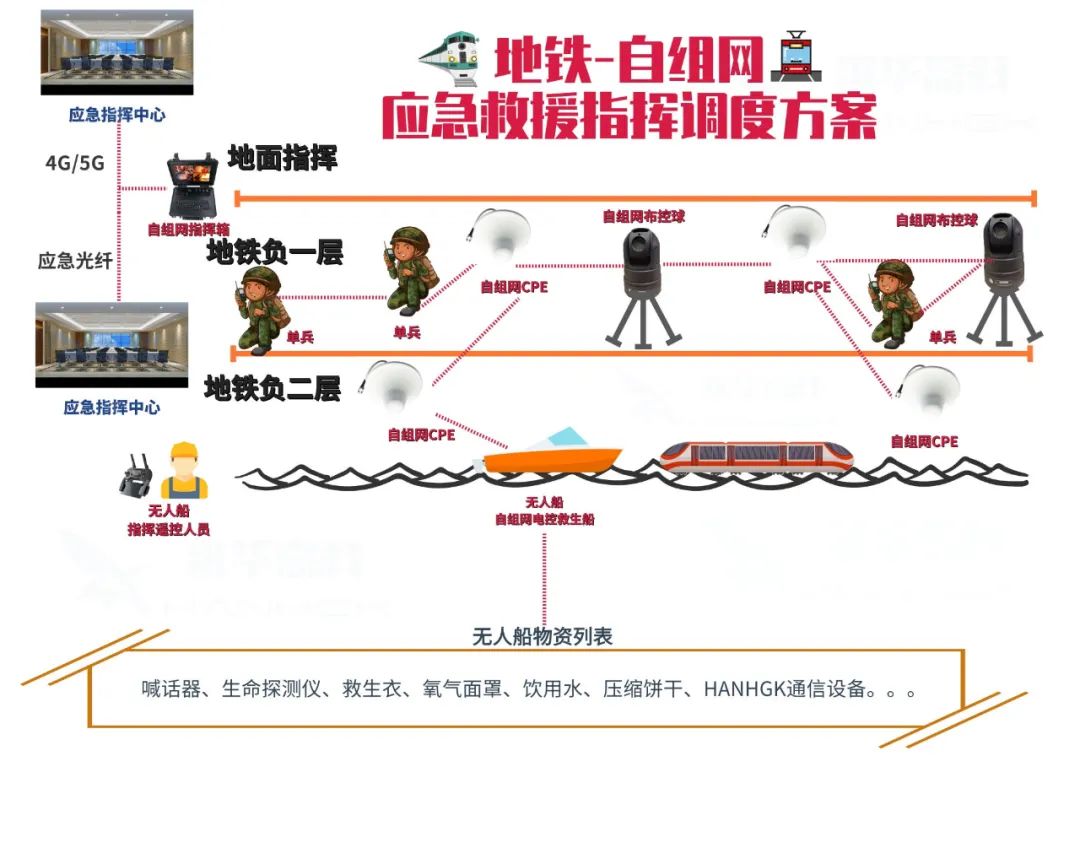
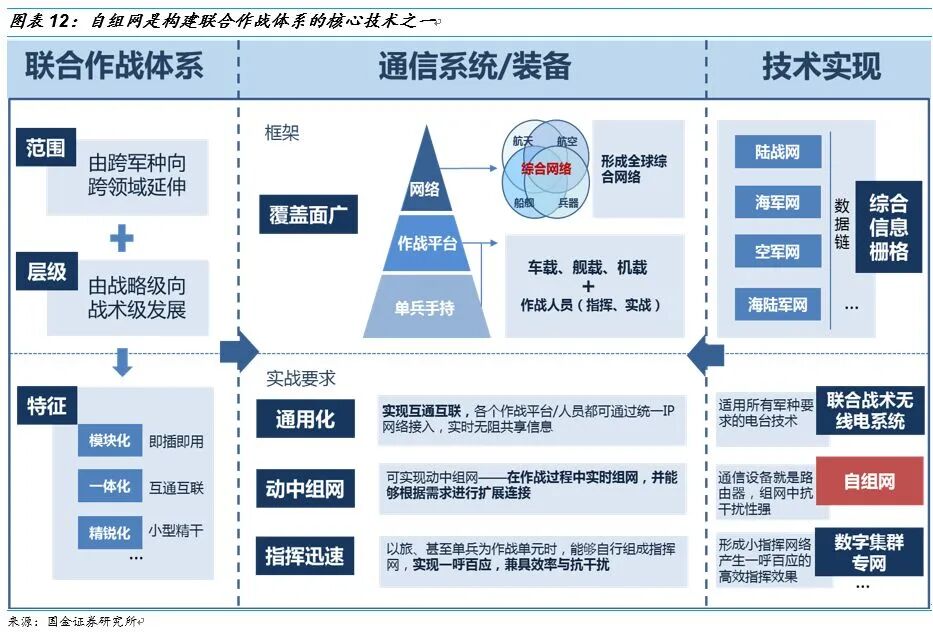
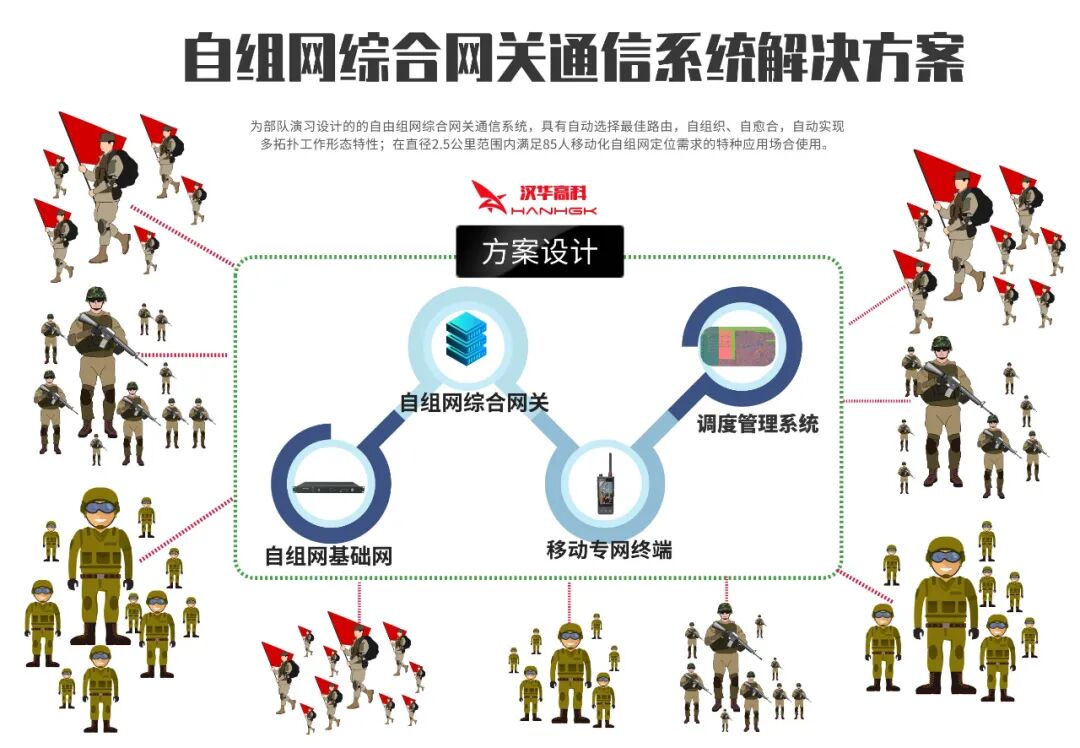 (The above images are sourced from the internet, primarily for academic exchange, not for other uses; please delete if infringing)
(The above images are sourced from the internet, primarily for academic exchange, not for other uses; please delete if infringing)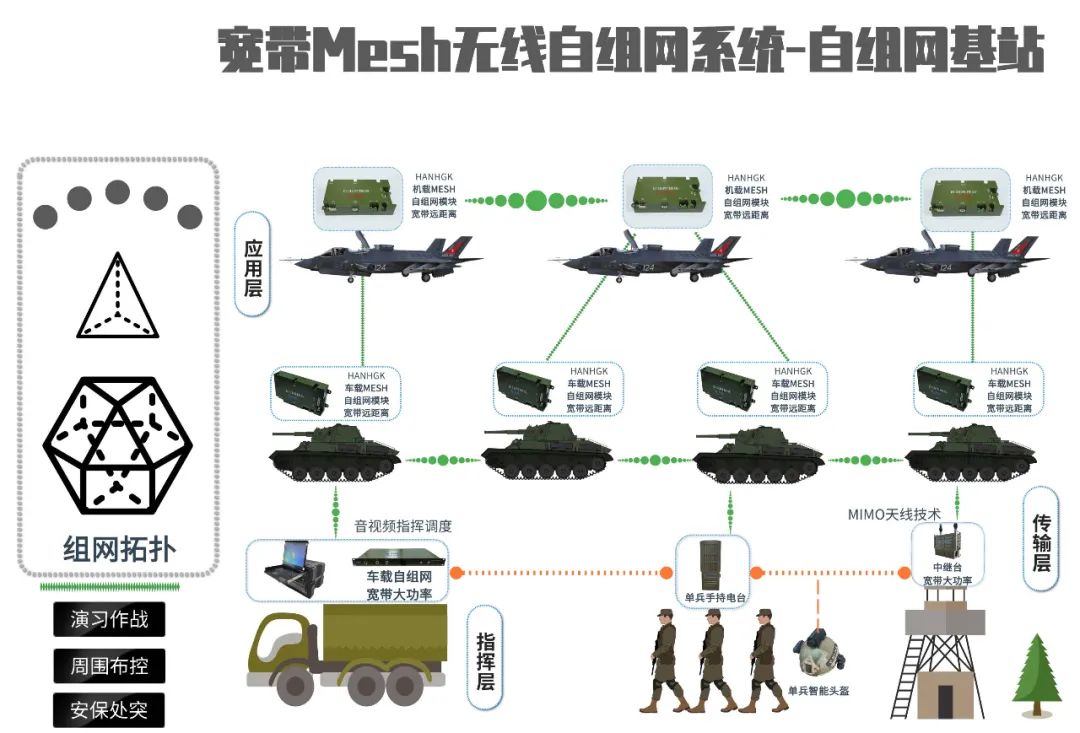 (The above images are sourced from the internet, primarily for academic exchange, not for other uses; please delete if infringing)
(The above images are sourced from the internet, primarily for academic exchange, not for other uses; please delete if infringing)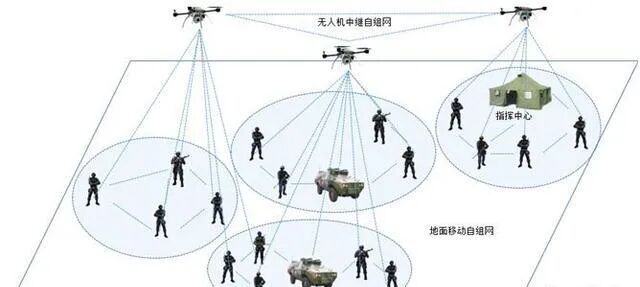
(The above images are sourced from the internet, primarily for academic exchange, not for other uses; please delete if infringing)
Attachment: Wireless Ad Hoc Network System