Click the blue text Follow us
Follow us
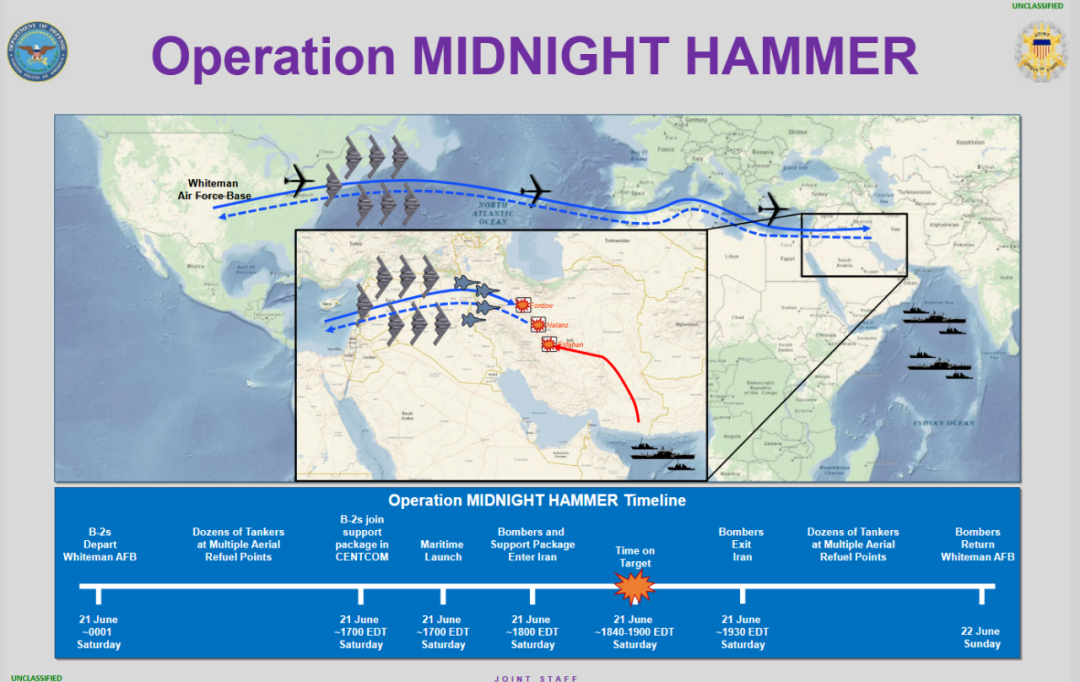
According to a report by Warriormaven on June 22, 2025, General Dan Kane, Chairman of the Joint Chiefs of Staff, stated to reporters that during the “Midnight Hammer” operation, after entering the land airspace, the B-2 fleet and escort support aircraft implemented complex coordinated maneuvers in a narrow airspace, requiring precise synchronization among multiple platforms while maintaining minimal communication throughout. Kane’s remarks on “cross-platform precise synchronization” and “minimal communication” indicate that real-time data sharing and operational coordination across joint platforms were not only achieved but were also “enhanced” or protected through security measures and limited communication capabilities.
The U.S. Department of Defense has made significant progress in advancing the “Joint All-Domain Command and Control” (JADC2) initiative. This program aims to enable seamless real-time information sharing among various equipment using incompatible transport layer communication technologies by constructing interfaces, IP protocols, and gateways. After years of development and validation, the core elements of JADC2 launched an “implementation plan” several years ago and now possess mature operational capabilities. Specifically, JADC2 integrates RF, GPS, and heterogeneous military data links to collect, organize, and convert multi-source sensor and communication information through a common infrastructure. Achieving secure interoperability across domains and military branches is the core goal of JADC2, and the “Midnight Hammer” operation may benefit from these breakthrough technologies developed over many years in these fields.
Kane’s description of the operation suggests that this strike not only utilized a new generation of multi-domain, multi-platform operational networking technology but also maximized the “security” and “efficiency” of communications. The B-2, satellites, ground control stations, and frontline aircraft such as the F-15 and F-35 were able to network and transmit time-sensitive operational information throughout the operation without radiating easily detectable electromagnetic signature signals. For instance, it is possible that the F-35 identified and destroyed enemy air defense units, and the success of the operation indicates that target and threat information was securely transmitted between the aircraft and the B-2. Drones likely also participated in the networking, which may have reduced the vulnerability of the B-2 and helped it evade ground threats.
In the context of the adversary’s recent demonstration of radar and RF tracking capabilities against drones, the achievement of secure communication in the “Midnight Hammer” operation is a significant tactical accomplishment. Although recent operations have weakened the adversary’s tracking capabilities, ensuring the “security enhancement” of multi-domain, multi-platform networking for air-to-air and air-to-ground operations remains highly significant. Broader network connectivity can exponentially enhance operational effectiveness but also poses exposure risks due to signal radiation, increasing system vulnerability. While built-in redundancy mechanisms can ensure continued operations in the event of an attack, in some cases, multiple operational nodes may rely on the same information. Therefore, it becomes particularly important to “encrypt,” “enhance,” or protect this information.
Through electronic warfare, IP protocols, frequency hopping, and even AI-enabled information collection and analysis, networks can be strengthened from multiple dimensions. When algorithms can identify and analyze the most relevant information accurately, only a “minimal” amount of actual transmission is needed to achieve operational effectiveness. Data can be collected, analyzed, and processed at the tactical edge where the collection point is located, thereby reducing connections and ensuring that only the most necessary information is transmitted. The transport layer itself can be strengthened against interference through techniques such as frequency hopping. For example, in recent years, the U.S. Air Force has made breakthroughs in the networking technology of the F-22/F-35 aircraft in “stealth mode,” allowing them to transmit networked information while maintaining “stealth” mode through advanced RF reinforcement and security technologies. Similarly, it would not be surprising if the B-2 strike group employed “passive electronic warfare” technology, which can “listen” to enemy electronic signals without radiating detectable signals. This means that the attack aircraft group can “perceive” the location of enemy radar and RF signals to evade detection.

(This article is compiled and organized based on internet materials for reference only; the views expressed in the article do not represent the position of this public account)
 Scan to follow usLearn about global military electronics developmentStay updated on the latest technology and equipment trends
Scan to follow usLearn about global military electronics developmentStay updated on the latest technology and equipment trends