Environment Setup
We previously introduced the data packets and the various layers of the protocol. Next, we will use the Ubertooth One to capture Bluetooth packets during the communication process.

(1) Install lib Library
apt-get install python-software-properties
add-apt-repository ppa:pyside
apt-get update
apt-get install libnl-dev libusb-1.0-0-dev pyside-tools
(2) Install libbtbb
wget https://github.com/greatscottgadgets/libbtbb/archive/2015-09-R2.tar.gz -O libbtbb-2015-09-R2.tar.gz
tar xf libbtbb-2015-09-R2.tar.gz
cd libbtbb-2015-09-R2
mkdir build
cd build
cmake ..
makesudo make install
(3) Install Ubertooth
wget https://github.com/greatscottgadgets/ubertooth/releases/download/2015-09-R2/ubertooth-2015-09-R2.tar.xz -O ubertooth-2015-09-R2.tar.xz
tar xf ubertooth-2015-09-R2.tar.xz
cd ubertooth-2015-09-R2/host
mkdir build
cd build
cmake ..
makesudo make install
sudo ldconfig
(4) Install Wireshark
sudo apt-get install checkinstall
wget https://www.wireshark.org/download/src/wireshark-2.0.3.tar.bz2
tar -xvf wireshark-2.0.3.tar.bz2
cd wireshark-2.0.3
./configure
makemake install
(5) Install Kismet
wget https://kismetwireless.net/code/kismet-2013-03-R1b.tar.xz
tar xf kismet-2013-03-R1b.tar.xz
cd kismet-2013-03-R1b
ln -s ../ubertooth-2015-09-R2/host/kismet/plugin-ubertooth ../configure
make && make plugins
sudo make suidinstall
sudo make plugins-install
(6) Install BLE Decryption Tool Crackle
crackle (Open Source Project Address)
git clone https://github.com/mikeryan/crackle.git
cd cracklemakemake install
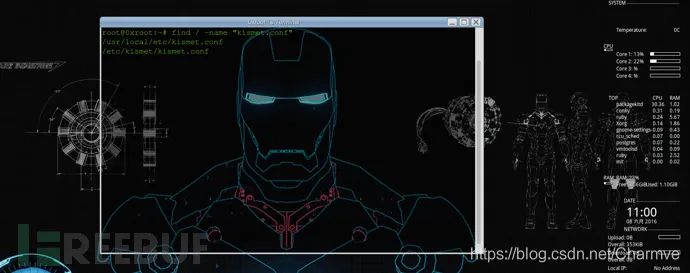
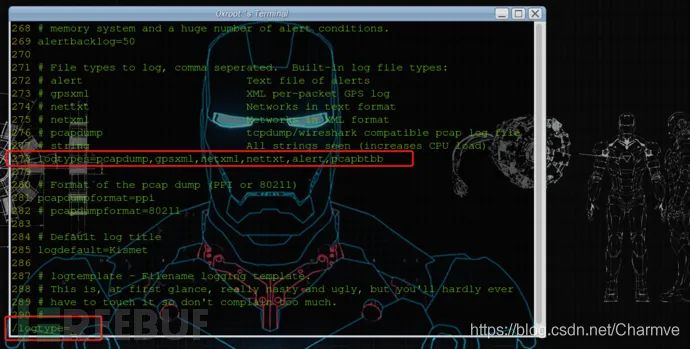
Find the Kismet configuration file kismet.conf and add “pcapbtbb” to the logtypes in kismet.conf.
Sniffing and Scanning
(1) spectool
spectool_curses
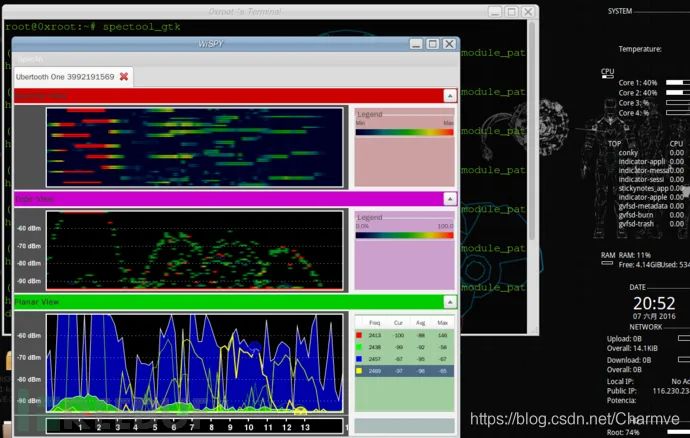
 spectool_gtk scans nearby signals and displays them on the spectrum:
spectool_gtk scans nearby signals and displays them on the spectrum:
spectool_raw means “raw materials” or “unprocessed items”, here it likely refers to displaying the unprocessed signal data captured by the device:
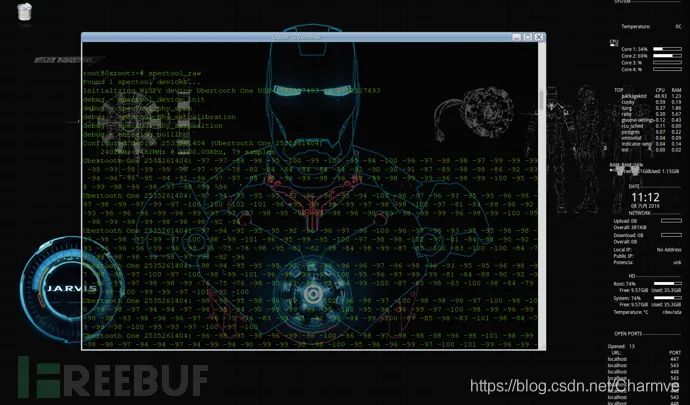
spectool_net uses Ubertooth One as a “hardware server” and listens on TCP: 30569 port. Any PC that can communicate with the host on the local network can access the Ubertooth host IP + 30569 to share the device. Connection method: On another host terminal, execute: spectool_gtk
—> Select Open Network Device —> Enter IP and port.

(2) hcitool
root@0xroot:~# hcitool --help
hcitool - HCI Tool ver 4.99
Usage: hcitool [options] <command> [command parameters]
Options: --help Display help -i dev HCI device
Commands: dev Display local devices inq Inquire remote devices scan Scan for remote devices name Get name from remote device info Get information from remote device spinq Start periodic inquiry epinq Exit periodic inquiry cmd Submit arbitrary HCI commands con Display active connections cc Create connection to remote device dc Disconnect from remote device sr Switch master/slave role cpt Change connection packet type rssi Display connection RSSI lq Display link quality tpl Display transmit power level afh Display AFH channel map lp Set/display link policy settings lst Set/display link supervision timeout auth Request authentication enc Set connection encryption key Change connection link key clkoff Read clock offset clock Read local or remote clock lescan Start LE scan lewladd Add device to LE White List lewlrm Remove device from LE White List lewlsz Read size of LE White List lewlclr Clear LE White list lecc Create a LE Connection ledc Disconnect a LE Connection lecup LE Connection Update
hcitool scan: Scan for nearby Bluetooth devices
hcitool lescan: Scan for nearby low energy Bluetooth devices
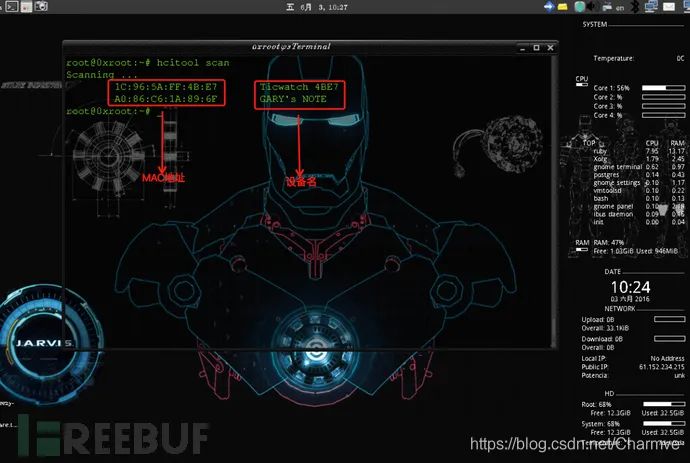
(3) gatttool
root@0xroot:~# gatttool -h
Usage: gatttool [OPTION...]
Help Options: -h, --help Show help options --help-all Show all help options --help-gatt Show all GATT commands --help-params Show all Primary Services/Characteristics arguments --help-char-read-write Show all Characteristics Value/Descriptor Read/Write arguments
Application Options: -i, --adapter=hciX Specify local adapter interface -b, --device=MAC Specify remote Bluetooth address -m, --mtu=MTU Specify the MTU size -p, --psm=PSM Specify the PSM for GATT/ATT over BR/EDR -l, --sec-level=[low | medium | high] Set security level. Default: low -I, --interactive Use interactive mode
gatttool -b 1C:96:5A:FF:4B:E7 -I
[ ][1C:96:5A:FF:4B:E7][LE]> help
help Show this help
exit Exit interactive mode
quit Exit interactive mode
connect [address] Connect to a remote device
disconnect Disconnect from a remote device
primary [UUID] Primary Service Discovery
characteristics [start hnd [end hnd [UUID]]] Characteristics Discovery
char-desc [start hnd] [end hnd] Characteristics Descriptor Discovery
char-read-hnd <handle> [offset] Characteristics Value/Descriptor Read by handle
char-read-uuid <UUID> [start hnd] [end hnd] Characteristics Value/Descriptor Read by UUID
char-write-req <handle> <new value> Characteristic Value Write (Write Request)
char-write-cmd <handle> <new value> Characteristic Value Write (No response)
sec-level [low | medium | high] Set security level. Default: low
mtu <value> Exchange MTU for GATT/ATT
[ ][1C:96:5A:FF:4B:E7][LE]>
(4) ubertooth-scan
root@0xroot:~# ubertooth-scan --help
ubertooth-scan: invalid option -- '-'
ubertooth-scan - active(bluez) device scan and inquiry supported by Ubertooth
Usage: -h this Help -U<0-7> set ubertooth device to use -s hci Scan - perform HCI scan -t scan Time (seconds) - length of time to sniff packets. [Default: 20s] -x eXtended scan - retrieve additional information about target devices -b Bluetooth device (hci0)
ubertooth-scan -s
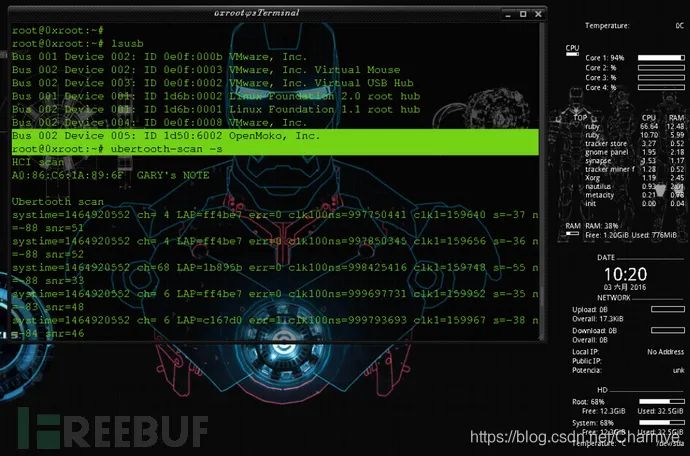
(5) ubertooth-btle
ubertooth-btle - passive Bluetooth Low Energy monitoring
Usage: -h this help
Major modes: -f follow connections -p promiscuous: sniff active connections -a[address] get/set access address (example: -a8e89bed6) -s<address> faux slave mode, using MAC addr (example: -s22:44:66:88:aa:cc) -t<address> set connection following target (example: -t22:44:66:88:aa:cc)
Interference (use with -f or -p): -i interfere with one connection and return to idle -I interfere continuously
Data source: -U<0-7> set ubertooth device to use
Misc: -r<filename> capture packets to PCAPNG file -q<filename> capture packets to PCAP file (DLT_BLUETOOTH_LE_LL_WITH_PHDR) -c<filename> capture packets to PCAP file (DLT_PPI) -A<index> advertising channel index (default 37) -v[01] verify CRC mode, get status or enable/disable -x<n> allow n access address offenses (default 32)
If an input file is not specified, an Ubertooth device is used for live capture. In get/set mode no capture occurs.
ubertooth-btle -f -c test.pcap captures packets & saves to local
Using this command, we can save the packets captured by the device locally, and after that, we can import them into Wireshark for packet and protocol analysis.
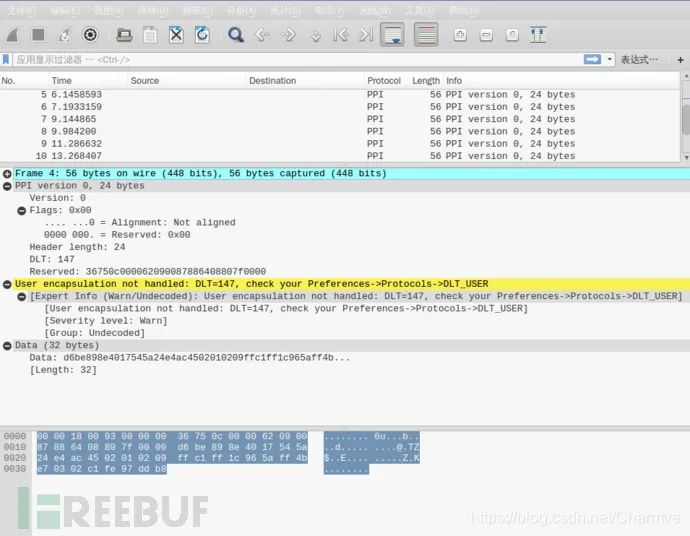
Importing Bluetooth packets sniffed by Wireshark requires some processing to view them correctly; otherwise, they cannot be analyzed normally:
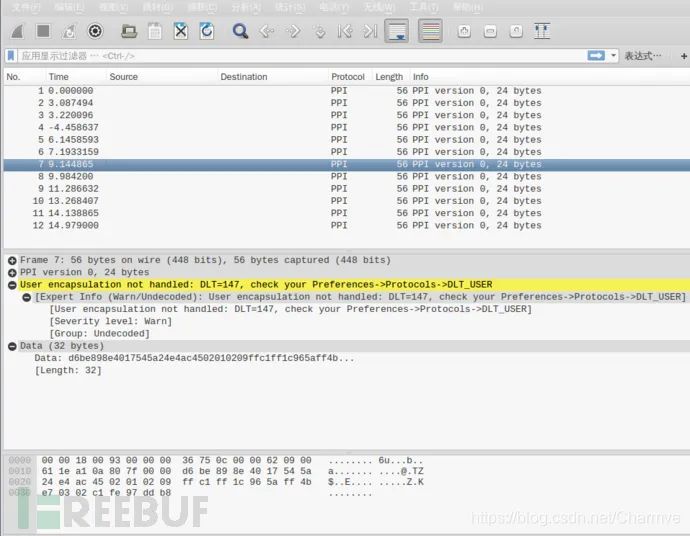
Edit → Preferences → Protocols → DLT_USER → Edit → New
In the payload protocol, enter btle
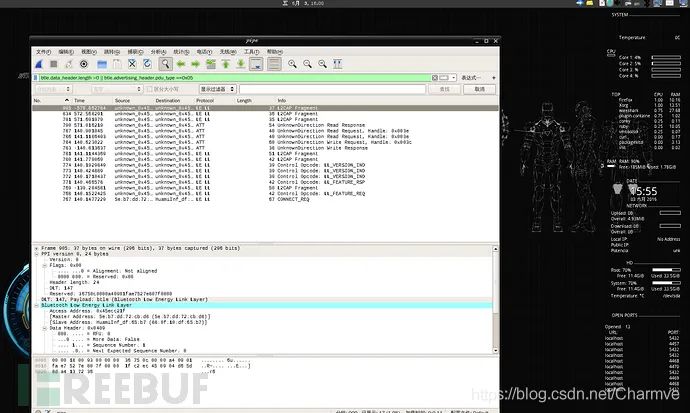
Use rules to filter packets: Refer to Capturing BLE in Wireshark
btle.data_header.length > 0 || btle.advertising_header.pdu_type == 0x05
(6) crackle
If enough packets are captured, especially btsmp, we can use crackle to crack tk and ltk:
crackle -i <file.pcap>
Decrypt packets and save the decrypted packets:
crackle -i <file.pcap> -o <output.pcap>
crackle -i <file.pcap> -o <out.pcap> -l <ltk>
References & Thanks
Reference Book: Robin Heydon. Bluetooth Low Energy the Developer’s Handbook, Net Disk Password: Reply “8001” on WeChat Official Account. Link: https://pan.baidu.com/s/1xneDTzdejtA91go5YuDhnQ
Sniffing and decoding NRF24L01+ and Bluetooth LE packets for under $30
Bluetooth sniffing with Ubertooth: https://dominicspill.com/kiwicon/Spill-Ubertooth-Kiwicon-2012.pdf
Now I wanna sniff some Bluetooth: Sniffing and Cracking Bluetooth with the UbertoothOne
http://j2abro.blogspot.com.au/2014/06/understanding-bluetooth-advertising.html
Roadman A@乌云drops: Bluetooth Low Energy Sniffing
Mad Dog@乌云drops: IoT Security Extraction Practice—Exploring Low Energy Bluetooth (BLE)
http://j2abro.blogspot.com.au/2014/06/understanding-bluetooth-advertising.html
http://j2abro.blogspot.com.au/2014/06/analyzing-bluetooth-advertising-with.html
http://cerescontrols.com/tutorials-3/sniffing-bluetooth-packets-with-kismet-and-wireshark-in-ubuntu-12-04/
https://github.com/greatscottgadgets/ubertooth/wiki/Build-Guide
https://github.com/greatscottgadgets/ubertooth/wiki/Capturing-BLE-in-Wireshark
http://stackoverflow.com/questions/23877761/sniffing-logging-your-own-android-bluetooth-traffic
https://lacklustre.net/bluetooth/wireshark.html
https://blog.lacklustre.net/posts/BLE_Fun_With_Ubertooth:_Sniffing_Bluetooth_Smart_and_Cracking_Its_Crypto/
http://superuser.com/questions/947593/how-can-i-sniff-bluetooth-traffic-coming-from-my-and-another-device
http://www.backtrack-linux.org/forums/showthread.php?t=41552
http://www.splitbits.com/2014/05/14/ubertooth-spectools-chromebook/
http://ubertooth.sourceforge.net/usage/start/
http://hackerific.net/2012/01/28/Spectrum-Tools-and-Ubertooth-One/
https://blog.lacklustre.net/
Recommended