1
Abstract
2
Introduction
Figure 1: Communication System Structure of DSRC V2X Scenario
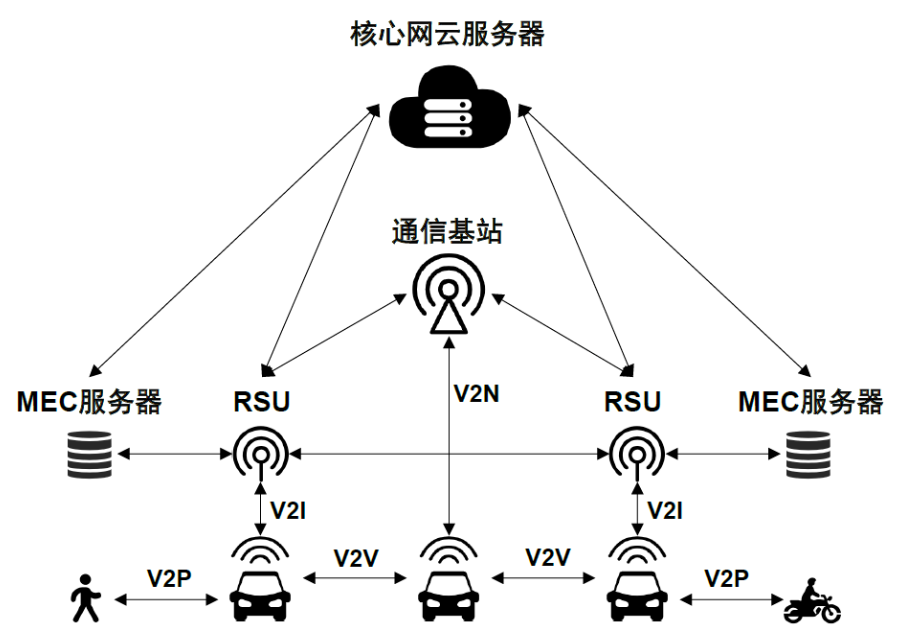
Figure 2: Communication System Architecture of C-V2X V2X Scenario

Figure 3: A Type of RSU
-
Data Collection and Distribution: RSUs are responsible for collecting data from vehicles, pedestrians, and other road infrastructure, such as vehicle location, speed, and environmental conditions. This data can be distributed in real-time to other vehicles, traffic management systems, or cloud platforms to provide dynamic traffic information and assist in driving decisions.
-
Information Relay: RSUs act as information relay stations, extending the communication range between vehicles (V2V), vehicles and infrastructure (V2I), and vehicles and cloud platforms (V2C). They help vehicles share and relay information through RSUs when direct communication is not possible, ensuring continuity and coverage of communication.
-
Traffic Management and Control: RSUs assist in implementing traffic management and control measures, such as traffic signal control, traffic flow monitoring, and emergency alerts. They cooperate with traffic management centers or other intelligent transportation systems to adjust traffic signals in real-time, optimize traffic flow, reduce congestion, and enhance road safety.
-
Edge Computing and Real-Time Processing: Some RSUs have edge computing capabilities, allowing them to process and analyze data locally, reducing reliance on central servers. This enables RSUs to make immediate local decisions upon receiving urgent data, such as issuing emergency braking warnings or obstacle avoidance commands, thereby improving response times.
-
Secure Communication and Data Protection: RSUs are responsible for ensuring secure communication with vehicles, other RSUs, and traffic management systems. They implement measures such as data encryption, identity verification, and integrity protection to prevent data from being stolen, tampered with, or interfered with during transmission, safeguarding the entire V2X system’s security.
3
Air Interface Security
-
Signal Eavesdropping: Malicious attackers may steal data transmitted between vehicles and infrastructure by passively listening to wireless communication signals. This is typically achieved using wireless listeners or software-defined radio (SDR) devices, which can capture and decode wireless signals. Attackers can obtain sensitive information such as location, speed, and travel routes by decrypting captured data packets (if encryption is insufficient), which can be used to track vehicles, conduct social engineering attacks, or serve as a basis for further attacks.
-
Data Tampering: Attackers can forge or tamper with data transmitted wirelessly, sending false information to vehicles or infrastructure. For example, attackers may use wireless transmitters to inject forged data packets into the network, modifying or falsifying existing data. By implementing man-in-the-middle attacks within the communication link, attackers can insert false information, such as incorrect traffic signals or road conditions.
-
Unauthorized Access: Attackers may gain unauthorized access to the V2X wireless interface, obtaining control over RSUs or vehicles. This illegal access often involves cracking weak authentication mechanisms or exploiting known vulnerabilities to bypass security controls. Once access is obtained, attackers can modify device settings or manipulate communication parameters, disrupting normal communication or data transmission.
-
Identity Forgery: Attackers may impersonate legitimate vehicles or RSUs, conducting false authentication that undermines the system’s trust mechanism. This attack typically involves forging device identities or authentication credentials, allowing attackers to masquerade as legitimate communication nodes to gain unauthorized access. Once the system accepts the forged identity, attackers can send false information or engage in other destructive activities, leading to system vulnerabilities and security risks.
-
Wireless Signal Interference: Environmental sources of wireless interference may affect the quality and stability of V2X communication. For example, electromagnetic interference, signals from other wireless devices, or natural environmental factors (such as wind and rain) may cause signal attenuation or interruption. Such interference can reduce the reliability and security of communication, impacting effective data transmission between RSUs and vehicles.
-
Symmetric Encryption: Symmetric encryption uses the same key for both data encryption and decryption. Due to its fast encryption and decryption speed, it is suitable for large-scale data transmission. It is commonly used for real-time data transmission between RSUs and vehicles, ensuring the confidentiality and integrity of communication by protecting sensitive information such as location and speed. -
Asymmetric Encryption: Asymmetric encryption uses a pair of public and private keys for encryption and decryption. Because it requires more complex mathematical computations, it is typically slower than symmetric encryption. It is used for securely exchanging symmetric encryption keys or for identity authentication between RSUs and other devices, ensuring communication security. -
End-to-End Encryption (E2EE): End-to-end encryption encrypts data at the source end of the transmission link, allowing only the destination end to decrypt it. This ensures that even if an intermediate node is compromised, attackers cannot decrypt the data. This technology is applied to communication between RSUs and vehicles, ensuring that all transmitted data remains encrypted throughout the process.
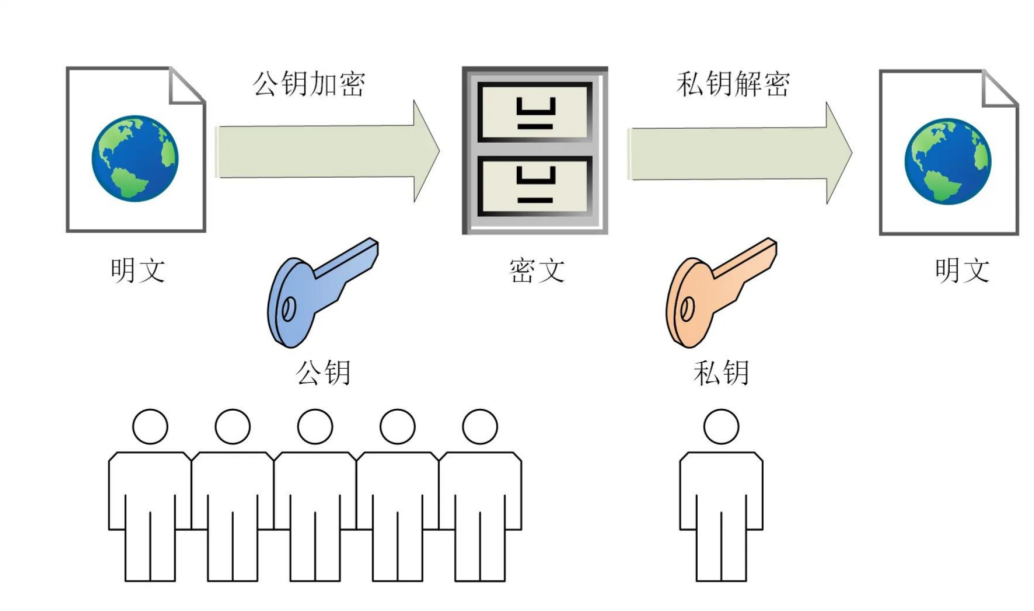
Figure 4: Asymmetric Encryption Process
-
Device Authentication: Device authentication verifies device identity through SIM cards or digital certificates, ensuring that only legitimate devices can connect to RSUs. SIM card authentication ensures the uniqueness of device identity, while digital certificates authenticate device identity through a Public Key Infrastructure (PKI) system, ensuring that communication between RSUs and vehicles is based on a trusted foundation.
-
Two-Factor Authentication (2FA): Two-factor authentication combines different types of verification methods, such as passwords and biometric features or physical tokens, to enhance security. This authentication method is used for access control of RSUs, ensuring that only authorized personnel can operate or configure the devices.
-
Intrusion Detection System (IDS): An intrusion detection system monitors the network and communication activities of RSUs to identify abnormal behaviors or patterns, such as suspicious traffic or unauthorized access attempts. This system continuously monitors RSU network communication, detecting and recording possible attack attempts, such as man-in-the-middle attacks or denial-of-service attacks.
-
Intrusion Prevention System (IPS): An intrusion prevention system actively takes measures to block attacks upon detecting threats, such as blocking malicious traffic or isolating suspicious devices. It responds immediately upon discovering threats, protecting RSU security and preventing malicious communication from compromising the system.
4
Future Prospects
5
Conclusion
References
[1] Jing, X. Analysis of V2X Technology and Applications. Shanghai Automobile, 2019, 4: 9-12.
[2] Huang, Y. Research on V2X Network Security Technology. Electronic World, 2018, 19: 49-50.
[3] Kenney, J. B. Dedicated Short-Range Communications (DSRC) Standards in the United States. Proceedings of the IEEE, 2011, 99(7): 1162-1182.
[4] Chen, S., Hu, J., Shi, Y., et al. A Vision of C-V2X: Technologies, Field Testing, and Challenges with Chinese Development. IEEE Internet of Things Journal, 2020, 7(5): 3872-3881.
[5] Salahuddin, M. A., Al-Fuqaha, A., Guizani, M. Software-Defined Networking for RSU Clouds in Support of the Internet of Vehicles. IEEE Internet of Things Journal, 2014, 2(2): 133-144.
[6] Kim, S. Y., Baik, I. K., Lim, S. S. An Implementation of WLL RSU Based on W-CDMA. 1997 International Conference on Consumer Electronics. IEEE, 1997: 446-447.
[7] Rawashdeh, Z. Y., Mahmud, S. M. Admission Control for Roadside Units Based on Virtual Air-Time Transmissions. 2011 IEEE Global Telecommunications Conference-GLOBECOM 2011. IEEE, 2011: 1-6.
[8] Liao, J., Feng, Z. Analysis of LTE Wireless Air Interface Security Threats. Communication Technology, 2017, 50(6): 1257-1263.
Chinese Association for Confidentiality
Science and Technology Branch
Long press to scan the code to follow us

Author: Feng Xiaoyu, Institute of Information Engineering, Chinese Academy of Sciences
Editor: Cai Beiping
Top 5 Exciting Articles of 2023 Review
Using Sound Masking to Protect Audio Privacy in Mobile Calls
Overview of Integrated Sensing and Communication Technology (ISAC)
Overview of Electromagnetic Fingerprinting Technology
Introduction to Electromagnetic Metamaterials
Overview of Network Attack Traffic Detection Technology
Recent Exciting Article Review
Overview of Direct Mobile-to-Satellite Technology (Part 2)
Overview of Direct Mobile-to-Satellite Technology (Part 1)
Satellite Internet, Security, and Starlink
Research on Elements and Models of High-Dynamic Satellite-Ground Link Communication
Analysis of Types and Impacts of Air Interface Attacks in Wireless Communication Networks