Analysis of Security Risks in Vehicle Networking Systems
Intelligent connected vehicles have transitioned from using 2G/3G/4G cellular communications for positioning, navigation, remote management, and e-call services to an era dominated by DSRC (EU) and C-V2X (China, North America, etc.) technologies for vehicle-road collaboration. As the connectivity and intelligence of vehicles continue to upgrade, cars are increasingly shedding their “mechanical” attributes and resembling “mobile computers”. The expansion of onboard ECUs, software, and networks has led to an explosive increase in the complexity of automotive electronics. Consequently, vehicles face layers of threats related to data security, which are closely tied to every road user.
From the overall architecture of vehicle networking, we can discuss data security risks from three perspectives: terminals, communication networks, and cloud platforms.
-
Terminal Security Risks
The onboard unit (OBU) and roadside unit (RSU) face different security risks.
OBUs are installed inside vehicles and interact with the vehicle through interfaces such as CAN bus or onboard Ethernet, allowing them to obtain the overall driving status information. In L3 and higher-level autonomous driving systems, they can even participate in vehicle control, making them more susceptible to malicious attacks. Identity theft, unauthorized operations, personal information leaks, vehicle driving information leaks, illegal vehicle control, and even malicious vehicle control are security risks that each vehicle owner must face, seriously threatening the privacy and safety of all passengers.
RSUs do not have privacy settings but, as core roadside devices in vehicle networking, they face risks such as unauthorized access, uncertain operating environments, device vulnerabilities, remote upgrade risks, and deployment maintenance risks.
-
Communication Network Security Risks
Communication networks primarily face user-side risks such as false information, information eavesdropping/theft, data tampering/replay, unauthorized intrusion, access control, spoofed terminals, and privacy leaks. For example, during the recently concluded 2021 C-V2X industry event, four scenarios were validated regarding vehicle networking security, including defenses against forged speed limit warnings, forged traffic light information, forged emergency vehicle alerts, and forged forward collision warning defenses.
-
Vehicle Networking Cloud Platform Security Risks
The cloud platforms we generally refer to can include central business clouds, regional clouds, and edge clouds. Risks include web crawlers, network vulnerabilities, illegal data retention, viruses and trojans, information leaks, DDoS attacks, APT attacks, and even illegal vehicle control through cloud platforms.
This article focuses on the security technologies at the network layer of vehicle networking, commonly referred to as “vehicle networking CA technology”.

Vehicle Networking CA Technology Architecture
As we know, C-V2X vehicle networking technology includes two communication modes: cellular Uu (4G/5G) and PC5. Currently, the C-V2X security based on the Uu interface employs the security mechanisms provided by existing mobile cellular systems, which are relatively mature and well-established, provided by cellular network operators. In the LTE system, the PC5-based C-V2X system uses broadcasting for communication, so there are no defined security mechanisms at the network layer for protection; this is entirely implemented by application layer security. Currently, the C-V2X system mainly considers using digital certificates (PKI system) for digital signing and encryption of service messages at the application layer, managing the entire lifecycle of digital certificates through a Certificate Authority (CA) platform.
When communicating, vehicle networking terminals need to download the corresponding digital certificates from the CA platform, sign the messages they are about to send with the digital certificate, and verify the received service messages to ensure the integrity of the messages and the legitimacy of the message sources.
The architecture of China’s vehicle networking security management system and trusted model is composed top-down of the “ITS management agency”, a “root CA” based on trusted relationships, “registration and authorization CAs”, and secure components on the device side. In simple terms, the ITS management agency generates a trusted root certificate list, which includes multiple root PKI relationships, such as registration root CA, pseudonym root CA, and application root CA, which can operate independently and interconnect. The root CAs in the trusted list authorize the corresponding CA certificates step by step downwards.
In C-V2X services, vehicle networking terminals first need to obtain a registration certificate, i.e., ECA. The registration certificate corresponds one-to-one with terminal devices. Generally, both RSUs and OBUs need to apply for ECA from the registration authority during the security initialization phase of their systems, which is usually completed when the device is manufactured. Then, they use ECA to request other certificates, such as pseudonym certificates PCA and application certificates ACA.
In practical applications, to protect user privacy and avoid tracking of vehicle trajectories, the onboard unit (OBU) needs to use the pseudonym certificate PCA to sign messages. An OBU can have many pseudonym certificates that can be randomly selected for use within a certain time period, effectively granting the vehicle a nickname for connected communication, changing to a new PCA every few minutes to avoid trajectory leaks due to long-term use of a single signing certificate.
Another important digital certificate is the application certificate ACA. It is issued to roadside devices (RSUs) and business applications for issuing application messages, such as traffic light states and traffic conditions. Since roadside devices and business applications do not have privacy restrictions, unlike onboard terminals, each vehicle networking business application has only one real and valid application certificate ACA.
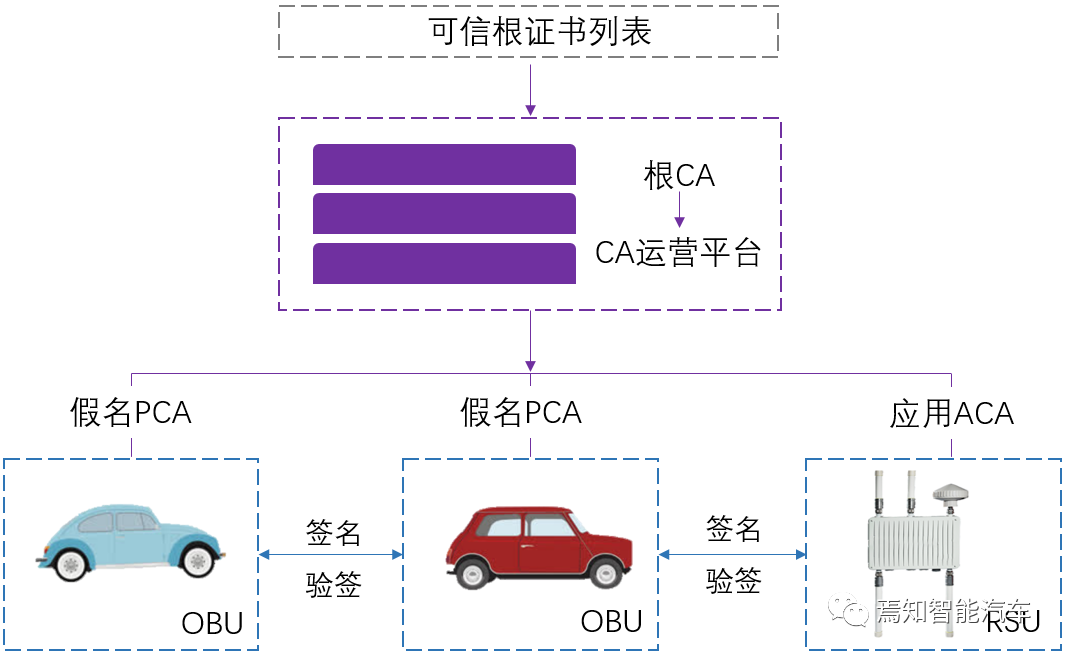
First, the certificate management system issues the public key certificate used by the vehicle networking V2X device for signing messages. The sender device uses the private key corresponding to the issued public key certificate to digitally sign the message and broadcasts the signed message along with the public key certificate or certificate chain. As the receiving V2X terminal, it first verifies whether the certificate chain of the message sender is valid, and then uses the digital certificate to verify the signed message. During the verification process, it also needs to check whether the signed message is within the permissions specified by the signing certificate; messages that fail verification will be ignored by the device.

Vehicle Networking CA Industry Layout
As mentioned in the previous section, at this stage, the main participants in the V2X security industry include: the vehicle networking security trust root management platform, industry-level root CA, operational service CA, and terminal-side CA (security chips).
The “vehicle networking security trust root management platform” refers to the “trusted root certificate list” issued by the ITS management agency, allowing for the establishment of trusted relationships among multiple independent PKI systems, enabling mutual recognition of certificates as needed. In China, this platform is established by the China Academy of Information and Communications Technology (CAICT), which issues the trusted root certificate list.
The “industry-level root CA” is the security anchor point of a specific independent PKI system, used to issue sub-CA certificates to lower-level sub-CAs. Currently, only companies such as National Automotive Intelligent Network, Datang Telecom, China Automotive Center, Jiangsu ITS, and China Communications Construction can provide industry-level root CAs.
The “CA operational platform” is a platform specifically for the full lifecycle management of digital certificates, mainly providing certificate download services to vehicle networking terminals. Many manufacturers providing security services have entered this field, and some of them will be briefly introduced in the following sections.
The “terminal-side CA” refers to the security components integrated into vehicle networking devices, specifically the encryption chips (HSM) that support reliable and efficient signing and verification processes for OBUs and RSUs.
Due to the many uncertainties in the current vehicle networking industry model, the “vehicle networking security trust root management platform” and “industry-level root CA” are still in the discussion and determination phase. This article will not focus on these aspects.

CA Platforms and Terminal-Side HSM Entering Commercialization Phase
According to the registration and team formation situation of the “X Cross” industry event in 2020 and 2021 and the author’s latest market research, examples of relatively mature CA platform operators in the market include:

Most of these companies have established partnerships with mainstream domestic automobile manufacturers, but since the entire vehicle networking V2X industry is still on the eve of large-scale commercial deployment, most companies are still exploring business processes, and the entire industry has not yet formed a well-established commercial system.

Under the Guidance of the Ministry of Industry and Information Technology, Vehicle Networking CA Pilot Work is Progressing Steadily
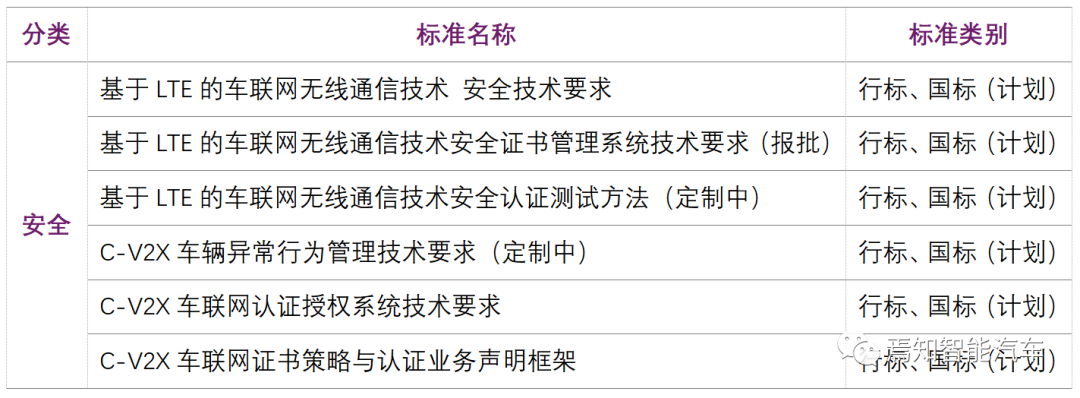
In recent years, the Ministry of Industry and Information Technology has jointly issued a series of documents such as the “National Vehicle Networking Industry Standard System Construction Guidelines (Overall Requirements)”, “National Vehicle Networking Industry Standard System Construction Guidelines (Information Communication)”, and “National Vehicle Networking Industry Standard System Construction Guidelines (Vehicle Intelligent Management)” with the National Standardization Administration.
However, due to limitations in bandwidth, computing power, and storage space of the direct communication network based on V2X vehicle networking, traditional digital certificates are increasingly inadequate to meet the security authentication and communication requirements in C-V2X scenarios. The scale of certificate issuance is vast, and the requirements for efficiency and performance in terminal signing and verification are rapidly increasing, along with issues related to abnormal behavior management that need to be resolved. Recently, some vehicle networking security working groups are designing PKI system digital certificates that meet the latest national standards and industry standards for C-V2X scenarios to support the service demands of large-capacity, high-performance PKI certificates in V2X scenarios. Over 20 participating units include automotive, communication, security, and cryptography-related enterprises, covering overall requirements for C-V2X vehicle networking security, certificate management systems, testing methods, and abnormal behavior identification.

Future Outlook for Vehicle Networking Security
In light of the new system components and application scenarios of vehicle networking services, the LTE-based V2X vehicle networking system needs to adopt effective security mechanisms in network communication, business applications, terminal devices, and other aspects to ensure the communication security of vehicle networking business data and the safety of user privacy information.
To effectively support application layer security authentication and communication mechanisms based on the PKI public key system, LTE-V2X needs to establish a complete certificate management system. Through practical experience, there are still several aspects of the V2X security authentication and management system that require multi-party discussion and negotiation to support the marketization of V2X.
-
The deployment of CA is closely related to the management model of vehicle networking services; it is difficult to provide precise deployment plan recommendations without a clear management model.
-
Which security authentication system top-level trust mechanism can more effectively achieve “cross-root mutual recognition”;
-
Vehicle networking security should prioritize meeting the needs of automotive production and applications; the next step should involve close collaboration with automotive manufacturers to discuss what testing content should be included in the V2X vehicle “network access” testing mechanism, focusing on industry demands from automakers and seeking efficient and convenient security technology solutions.
-
The interoperability of certificates still needs improvement. Suppose the OBU or RSU integrates an encryption chip provided by manufacturer A, while the owner of the equipment (demonstration area, highway, mining area, etc.) deploys manufacturer B’s CA operational platform. In that case, there will be a situation where the CA systems of the two companies cannot directly connect, meaning that manufacturer A’s HSM chip cannot directly download digital certificates from manufacturer B’s CA platform for message signing and verification processing.
-
In future development, LTE-V2X vehicle networking will also combine with mobile edge computing technology to form a layered, multi-level edge computing system to meet the needs for more complex, high-speed, low-latency vehicle networking business processing and response. How to iterate lightweight security technologies, improve operational efficiency, and reduce the bandwidth occupation and cryptographic computation overhead of security information will be crucial topics for discussion.

Conclusion
C-V2X in vehicle networking has begun to accelerate into the stage of large-scale deployment, transitioning from demonstration areas to commercial use, from auxiliary warnings to autonomous driving, and entering the daily lives of the public. Vehicles, traffic, urban management, and cloud platforms—this major interdisciplinary field of vehicle networking requires collective efforts to clarify the industrial operation model and make substantial progress. Data security, as a key issue, relates to personal user privacy and the safe and stable operation of the entire traffic system, necessitating ongoing in-depth research and design by all participants in the overall system architecture and certificate management mechanisms.