★ Xi’an Jiaotong University Wang Xiangming
★ Xi’an Thermal Engineering Institute Liu Pengfei
★ Xi’an Jiaotong University Liu Yang, Liu Ting
Abstract:With the advancement of digitalization and intelligent transformation of industrial control systems, the integration of information network technology and traditional physical control systems is deepening. In the context of frequent interactions among various businesses, a massive number of sensors and actuators are ubiquitously connected, resulting in system boundary networks that are widely distributed, unattended, and have weak physical protection measures, providing attackers with a means of physical intrusion through unauthorized access devices. Attackers can use silent intrusion devices to remain hidden in the system for a long time to carry out information theft, posing a significant security threat to industrial control systems. This paper analyzes security threat cases and evolution trends in industrial control systems, proposes a threat model for physical intrusion attacks, compares detection methods for physical intrusion devices, and discusses the challenges faced in this field and future research directions.
Keywords:Industrial Control Systems; Fieldbus Networks; Physical Intrusion Attacks; Channel State Fingerprints
1 Industrial Control System Architecture
Industrial Control Systems (ICS) are automatic control systems centered around production, manufacturing, and operational processes in the industrial sector, covering industries such as power energy, petrochemicals, aerospace, and urban public utilities. The integration of advanced scientific technologies such as distributed control, computer networks, and intelligent sensing has played a significant role in the evolution of the ICS structure. Currently, the hierarchical structure of ICS can be simply divided into process monitoring layer, field control layer, and field device layer, as shown in Figure 1.
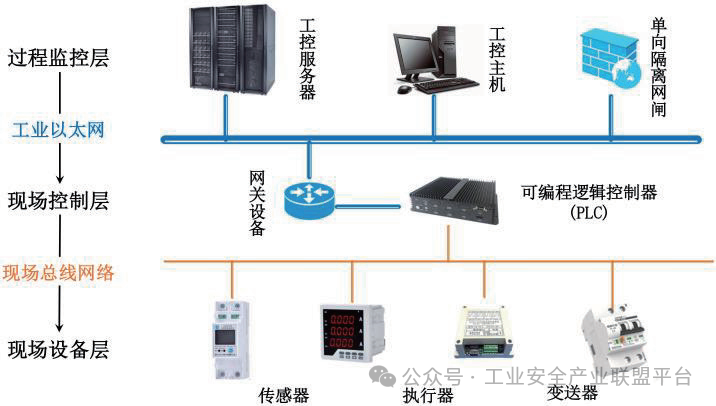
Figure 1 Hierarchical Structure of Industrial Control Systems
1.1 Process Monitoring Layer
The process monitoring layer mainly consists of engineer stations, operator stations, and various industrial control servers, centered around high-bandwidth industrial Ethernet, responsible for integrating, analyzing, and processing real-time data from the production site to monitor and control the industrial production process. Since the 21st century, internet technology has continuously penetrated various application fields of ICS, with industrial Ethernet supporting high-speed and reliable transmission of massive data based on Ethernet/IP communication protocols.
1.2 Field Control Layer
The field control layer serves as a bridge connecting the monitoring stations and field devices in ICS, with its core device being the field controller, such as Programmable Logic Controllers (PLC), responsible for receiving data from field sensors and generating corresponding control commands sent to field actuators based on preset configuration programs and execution strategies.
1.3 Field Device Layer
The field device layer includes various sensors, actuators, transmitters, and other infrastructure in the production site, typically constructed and implemented using fieldbus networks. To overcome the complexity and high costs of point-to-point wiring in distributed control systems, the field device layer utilizes open protocol and highly interoperable fieldbus networks to achieve bidirectional, serial, one-to-many digital communication between field devices, significantly reducing installation and maintenance costs. However, due to significant differences in bus protocols established by different manufacturers, there are practical issues of protocol incompatibility and non-uniform standards in fieldbus networks used in different application areas. Additionally, under the architecture of distributed control systems, the fieldbus networks of the lower-level systems are mostly relatively closed and isolated, making it difficult to achieve network interconnection and data sharing between lower-level systems. Nevertheless, to ensure efficient, real-time, and stable data communication between lower-level devices, fieldbus networks are still widely used in today’s ICS, utilizing PLCs or protocol conversion gateways to achieve data and command conversion between industrial Ethernet and fieldbus networks.
2 Physical Intrusion Threats to Industrial Control Systems
In the development of ICS, information network technology has played a significant role in transforming the structure and model of ICS, while also increasing inherent vulnerabilities and attack surfaces. Despite the establishment of relevant standards and guidelines internationally to enhance the information security capabilities of ICS, such as NIST SP800-82, IEC62443, and NAMUR NA115, numerous serious information security incidents have still occurred in industrial control fields worldwide, such as power energy systems.
2.1 Evolution Trends of Threats Faced by Industrial Control Systems
The typical cases of the Stuxnet worm attack on the Iranian nuclear power plant in 2010 and the BlackEnergy virus attack on the Ukrainian power system in 2015 have attracted significant attention from hackers and political military figures worldwide. Security incidents over the past decade have shown that the vulnerability of information security makes it difficult for ICS to defend against and counter network intrusion attacks. As a result, many researchers and industry personnel have conducted extensive foundational research on information security protection against network intrusion threats, especially concerning Supervisory Control and Data Acquisition (SCADA) systems, with many studies proposing deployment schemes for Intrusion Detection Systems (IDS) to detect malicious attacks and enhance ICS network security. Consequently, with the continuous improvement of boundary firewall technology and the strengthening of information protection measures, the cost of implementing network intrusion attacks in ICS has become increasingly high.
As the upper-level information networks become more secure and reliable, the lower-level field device layer is more likely to become the primary target for malicious attackers. In 2017, a research team from the University of Tulsa infiltrated a wind farm in the central United States and successfully gained control over the wind turbine blades. The team physically pried open the metal lock at the bottom of the turbine and connected a homemade Raspberry Pi microcomputer to the control network in the server cabinet. They later intercepted communication commands to crack the address information of all wind turbines in the wind farm and sent attack commands to control the rotation speed of each wind turbine. This security incident demonstrates that even with enhanced protective measures in the upper-level information networks of ICS, it is still challenging to ensure the operational safety of the infrastructure in the lower-level fieldbus networks.
As various ICS continue to transform towards digitalization and intelligence, a massive number of distributed field sensing and execution terminals are widely connected to fieldbus networks in response to the demand for frequent business interactions. These terminals include new devices and legacy systems, coexisting and interconnected, leading to a diverse range of terminal types and functions. The resulting fieldbus networks exhibit the following characteristics: widely distributed physical domain boundaries, unattended operation, and weak physical protection measures. Additionally, common fieldbus protocols (such as Modbus, DNP3, CAN, etc.) generally lack encryption and identity authentication mechanisms. For the increasingly complex distributed ICS systems, protecting the physical security of widely distributed field devices and their infrastructure components faces significant challenges and protection costs, and current research on security protection for critical infrastructure remains relatively limited. In this context, attackers can more easily compromise the physical boundary protection of lower-level fieldbus networks, using physical intrusion methods to gain access to the closed internal networks of lower-level systems through unauthorized intrusion devices for information theft and malicious attacks.
2.2 Definition and Process of Physical Intrusion
Based on the above analysis, physical intrusion refers to the act of bypassing the physical access restrictions and lateral isolation security mechanisms of the ICS fieldbus network through physical proximity, social engineering, etc., to gain unauthorized access to intrusion devices, resulting in infrastructure terminals being improperly connected, illegally accessed, and maliciously controlled.
As shown in Figure 2, the attack implementation process initiated by the attacker after unauthorized access to intrusion devices can be divided into two stages:
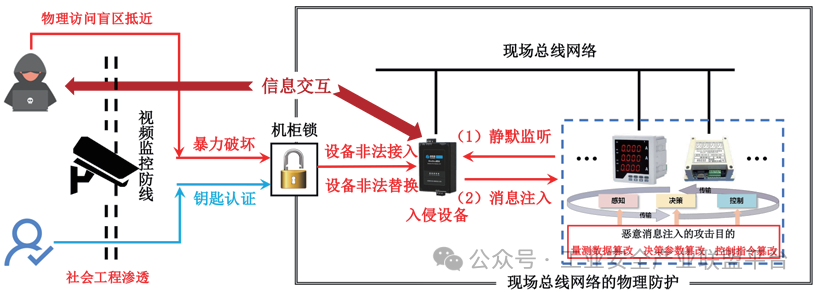
Figure 2 Threat Model of Physical Intrusion
(1) Silent Listening: First, the intrusion device remains hidden in the network for an extended period, eavesdropping on key system information such as device addresses, register data, request intervals, and response delays. During this stage, the intrusion device does not actively participate in bus communication and does not generate any abnormal communication traffic.
(2) Message Injection: After collecting sufficient communication data, the attacker can infer critical privacy information about the system and subsequently send false messages by mimicking normal terminal address information and command upload frequencies, ultimately achieving the goal of tampering with measurement data, decision parameters, or control commands in the fieldbus network.
Compared to traditional network intrusion methods that are commonly focused on, physical intrusion methods that breach physical defenses can also cause severe damage to ICS, threatening the stable operation of the system at a lower attack cost. For example, in power systems, attackers can control electrical devices in distribution cabinets through physical intrusion methods to cause localized power outages or tamper with smart meter electricity measurement data and historical usage data to steal electricity, affecting the safety and economic operation of the national grid.
3 Defense Measures and Challenges Against Physical Intrusion
IDS is the mainstream defense method against intrusion attacks on ICS. IDS is deployed in various layers of the ICS network in a bypass monitoring manner, detecting malicious traffic generated by intrusion devices during the message injection stage (stage (2) in Figure 2) by observing abnormal delays between communication frames, abnormal traffic cycles, or fluctuations in information entropy. However, such IDS primarily relies on analyzing abnormal communication traffic within the network, which may result in a high false negative rate when identifying covert injection attacks with high camouflage characteristics, and cannot detect unauthorized silent intrusion devices that do not actively participate in communication during the silent listening stage (stage (1) in Figure 2).
To detect silent intrusion devices that have not yet actively participated in communication at stage (1) as early as possible, existing physical protection measures mainly rely on video surveillance to identify abnormal behavior of personnel, which carries the risk of intrusion personnel damaging facilities and connecting infected devices due to negligence or absence of monitoring personnel in the video surveillance system.
To further enhance the network’s ability to monitor device connection states, some researchers have proposed intrusion device detection methods based on network channel state fingerprints. As shown in Figure 3, unauthorized access and replacement behaviors of intrusion devices will affect the topology of the communication network, inevitably leading to changes in network load. Even if the intrusion device remains in a long-term silent state, its access or replacement behavior can still be observed through changes in the physical characteristics of channel communication signals. Therefore, such research primarily explores the physical characteristics of communication signals that can reflect the connection state of network devices, constructs channel state fingerprints that indicate the security of the network channel, and then detects unauthorized access and replacement behaviors of external malicious devices by identifying changes in channel state fingerprints. This method does not rely on abnormal traffic data and can detect silent intrusion devices that are still in a dormant stage within the network. Based on the signals or physical characteristics used in constructing channel state fingerprints, existing studies categorize channel state fingerprints into three types: square wave signal fingerprints, amplitude feature fingerprints, and pulse signal fingerprints.
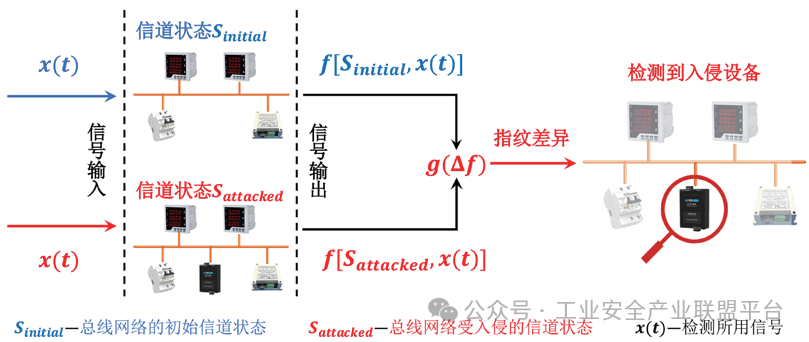
Figure 3 Detecting Intrusion Devices in the Network Using Anomalies in Channel State Fingerprints
3.1 Square Wave Signal Fingerprints
Constructing square wave signal fingerprints requires using a signal generator to send periodic square waves during idle times of the bus network. At a fixed observation location, the observed signal received by the observation device acting as an oscilloscope remains a square wave signal, and the observed signal’s high and low voltage amplitudes maintain a certain proportional relationship with the source square wave signal’s voltage amplitude, determined by the impedance set of various electronic components in the network. If the fieldbus network is subjected to a physical intrusion attack, the attacker must unauthorizedly connect intrusion devices to the network, which will affect the network’s impedance set, thereby altering the entire square wave signal voltage amplitude transmission process in the network.
The detection process based on square wave signal fingerprints can be summarized as follows: First, under the initial state of the network (e.g., during the initial deployment phase or after strict security checks), a stable square wave signal with specified parameters (including amplitude, frequency, phase, etc.) is used to generate a channel fingerprint containing channel security state information. Next, under the state of the network to be tested, the specified parameter square wave signal is sent again, and the observed signal obtained at the same observation location in the initial state is aligned in the time domain and differentiated with the channel fingerprint to obtain the differential signal to be tested. If the network has suffered a physical intrusion, the differential signal will contain the intrusion amplitude square wave signal. If the network has not been intruded, the differential signal will be a white noise signal containing measurement errors. The final detection decision can be made using classifiers such as support vector machines or neural networks based on signal sample training.
3.2 Amplitude Feature Fingerprints
Amplitude feature fingerprints rely solely on the high-level amplitude characteristics of normal communication signals in the bus network. According to the electrical specifications of the physical layer of the fieldbus, digital TTL level signals are converted into voltage signals with constant amplitude that propagate along the transmission line. When the signal is in a stable high-level state, the transmission line can be regarded as a constant DC impedance participating in the voltage amplitude transmission of steady-state signals at different locations along with the input impedance of various devices in the network. Thus, the fixed relationship presented by the transmission line and various devices in the network can be reflected in the high-level voltage amplitude of the signal under steady-state conditions.
When the fieldbus network is in its initial state, the observation device passively samples the normal communication signals of any authorized terminal, extracting only the high-level sampling points as the channel fingerprint. Under the state of the network to be tested, the high-level sampling points obtained are directly differentiated with the channel fingerprint to obtain the differential signal. If the network has suffered a physical intrusion, the differential signal will contain the intrusion amplitude DC voltage signal. If the network has not been intruded, the differential signal will be a white noise signal containing measurement errors. Since this differential signal does not contain waveform characteristics, and the analysis of DC voltage characteristics is simple, a lightweight detection model based on dynamic thresholds can be constructed to complete the detection decision under the constraint of a constant false alarm rate.
3.3 Pulse Signal Fingerprints
Constructing pulse signal fingerprints requires using a signal generator to send short pulse signals during idle times of the bus network. Due to the transient propagation characteristics of pulse signals, reflections will inevitably occur at the connection points of devices in the network due to discontinuities in transmission line impedance, and the time delay of each reflected signal reaching a fixed observation location contains information about the corresponding device’s location.
When the fieldbus network is in its initial state, a signal generator sends specified parameter (including amplitude, pulse width, rise time, etc.) short pulse signals into the network, and the observed signal received at the observation location can reflect the impedance characteristics and absolute positions of various devices under the current state of the network, thus this observed signal can be regarded as the channel fingerprint. If an unauthorized intrusion device appears in the network, a new reflection node will form at the connection point of the intrusion location, and under the premise of the same pulse signal and observation location, the observed signal will inevitably produce new reflection signals caused by the intrusion device, along with abnormal changes in the amplitudes of other normal reflection signals. Therefore, these abnormal features in the observed signal can be used to detect the presence of intrusion devices in the network and further determine the spatial location of the intrusion device in the fieldbus network. The extraction of abnormal reflection components can rely on feature sequence matching algorithms, finding multiple longest common subsequences in two sequences through scoring and penalty mechanisms to identify mismatched or empty matching abnormal sequence locations, such as the Needleman-Wunsch matching algorithm.
3.4 Comparison and Challenges
This section evaluates different channel state fingerprint construction methods based on construction methods, resource requirements, and detection capabilities. The evaluation overview is shown in Table 1.
Table 1 Comparison and Evaluation of Different Channel State Fingerprints
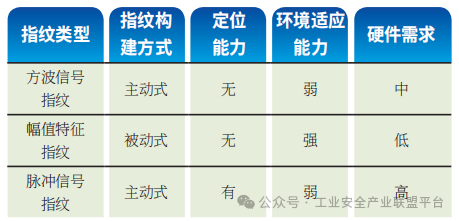
The detection method based on square wave signal fingerprints requires utilizing idle times of bus communication, which not only impacts the normal operational processes of ICS but also risks causing other authorized terminals to produce unintended actions due to the square wave detection signals sent. Additionally, detection requires the deployment of dedicated signal generators in the bus network and the deployment of digital oscilloscopes at specific observation locations, with the entire detection setup needing to be deployed separately and incurring high hardware costs. In practical working environments, the aging and wear of hardware during long-term operation can lead to changes in their impedance characteristics, while external environmental factors such as temperature and humidity can also affect the electrical characteristics of the physical channel. The construction of the detection model based on square wave signal fingerprints relies on training data samples, meaning that model updates require the re-acquisition of a large number of data samples, and the high computational costs and time overhead make its usability in practical working environments poor.
The detection method based on amplitude feature fingerprints achieves physical intrusion detection in a passive listening and non-intrusive mode. Since it only focuses on the high-level amplitude characteristics of normal communication instructions, the sampling of detection devices does not require restoring the waveform of communication signals, and the lower hardware requirements for sampling can free the detection method from reliance on dedicated digital oscilloscopes, meeting the hardware design conditions for board-level detection devices. Furthermore, since the high-level amplitude characteristics of communication instructions are independent of communication protocols, the detection method does not require method adaptability adjustments when applied in different bus protocol scenarios, allowing the detection device to achieve plug-and-play functionality. Under changes in external environmental factors, the amplitude feature fingerprints and detection models based on dynamic thresholds can achieve lightweight and rapid updates due to their low computational costs.
Essentially, both square wave signal fingerprints and amplitude feature fingerprints are steady-state channel fingerprints reflecting the impedance distribution characteristics of fieldbus networks; however, steady-state channel fingerprints cannot assist in locating physical intrusion attacks. In ICS, constrained by terminal layout wiring environments and design schemes, most fieldbus networks adopt a building wiring networking form, which extends the actual communication transmission distance. To address the need for locating intrusion devices in complex scenarios, pulse signal fingerprints that utilize transient propagation characteristics to generate reflection signals reflecting device location information have been proposed, which are more beneficial for maintenance personnel to promptly repair systems and investigate physical intrusion threats. However, detection methods based on pulse signal fingerprints, in addition to interfering with normal communication on the bus, require high-cost dedicated oscilloscope equipment for sampling nanosecond-level short pulse signals, and coupled with signal generators that send short pulse functions, the entire detection setup will be very expensive, while the attack costs for the physical intrusion threats being addressed are very low.
To achieve low-cost passive localization of physical intrusions, this paper suggests utilizing the characteristics of amplitude feature fingerprints that are simple to obtain and process, and low-cost, analyzing the different impacts of intrusion device access locations on the high-level amplitude characteristics of normal communication signals from different authorized terminals, constructing channel state group fingerprints based on the high-level amplitude characteristics of normal communication signals from each authorized terminal, and collaboratively utilizing the channel state fingerprints generated by signal sources at different spatial locations to locate intrusion devices.
4 Conclusion
This paper discusses the evolution trends of threats faced by ICS in light of recent security cases and analyzes the threats and challenges posed by physical intrusion attacks using external devices as a means of intrusion against the backdrop of security vulnerabilities in lower-level fieldbus networks. By comparing existing physical intrusion detection methods based on channel state fingerprints, this paper summarizes the advantages and disadvantages of these methods, providing a reference for researchers to quickly assess the applicability of these methods.
With the promotion of applications such as smart manufacturing, intelligent transportation, and smart logistics, the physical boundaries of industrial control systems will further expand and blur, and the demand for physical intrusion defenses will continue to grow, raising higher requirements for the economic efficiency and stability of methods. Therefore, future research and practice can consider the following issues: (1) further reducing the hardware configuration and computational resource requirements for physical intrusion detection and localization to meet large-scale deployment needs; (2) extending evaluations to applications across various fieldbus protocols while observing longer time windows to analyze the robustness of detection methods in complex scenarios; (3) finding suitable model update methods that can dynamically adapt to channel state feature drift caused by hardware aging or changes in external environmental factors.
References omitted.
Author Information
Wang Xiangming (1998-), male, from Jiaozuo, Henan, PhD, currently studying at the School of Cyberspace Security, Xi’an Jiaotong University, with research interests in information security of industrial control systems and intrusion detection.
Liu Pengfei (1994-), male, from Wuhai, Inner Mongolia, engineer, PhD, currently working at Xi’an Thermal Engineering Institute, mainly engaged in network security related work for industrial control systems.
Liu Yang (1990-), male, from Fuzhou, Jiangxi, associate professor, PhD, currently teaching at the School of Cyberspace Security, Xi’an Jiaotong University, mainly engaged in research on the security of cyber-physical integrated systems.
Liu Ting (1981-), male, from Changsha, Hunan, professor, PhD, currently teaching at the School of Cyberspace Security, Xi’an Jiaotong University, mainly engaged in research on software engineering and the security of cyber-physical integrated systems.
· end ·
Source | “Automation Expo” 2025 First Issue and “Special Issue on Information Security of Industrial Control Systems (Volume 11)”
Editor | He Min
Statement: This article is forwarded by the Industrial Safety Industry Alliance platform WeChat public account (WeChat ID: ICSISIA). If there are any copyright issues, please contact for deletion.

For cooperation or consultation, please contact the secretary of the Industrial Safety Industry Alliance platform WeChat ID: ICSISIA20140417
Recommended Readings
Heavyweight | “Automation Expo” 2025 First Issue and “Special Issue on Information Security of Industrial Control Systems (Volume 11)” Online
Must-Read for the 2025 Two Sessions | These Industrial Information Security Proposals Will Rewrite Industry Rules
Ministry of Industry and Information Technology | Risk Warning on Preventing Network Attacks Targeting DeepSeek Local Deployment
Insights | Security Protection of Long-Distance Oil and Gas Pipeline Industrial Control: Strategies, Practices, and Prospects
DeepSeek Analysis | Current Status and Future Prospects of Zero Trust Security Architecture in the Industrial Field
White Paper | Northeast University: 2024 Industrial Control Network Security Situation White Paper (Download Attached)
Recommended Read | The Five Network Security Technologies That Are About to Become Obsolete
Insights | Research on Encryption Technology for Industrial Programmable Control Systems
Recommended Read | Insights and Thoughts from the Perspective of Security Personnel on DeepSeek
Ministry of Industry and Information Technology | In 2024, China’s Information Security Sector Revenue Will Reach 229 Billion Yuan
Attention | Results of Security Testing for Key Network Devices (19th Batch)
Power Safety | 2024 New Power System Safety Construction Guidelines Report (Download Attached)
Ministry of Industry and Information Technology and Thirteen Departments | 2024 List of Typical Cases for Network Security Technology Applications
Attention | Joint Issuance of the “Implementation Plan for Improving Data Flow Security Governance to Better Promote the Marketization and Value of Data Elements” by the National Development and Reform Commission, the National Data Bureau, and Six Other Departments