In May 2022, Dark Reading reported that researchers from Nozomi Networks discovered that common misconfigurations of the Domain Name System (DNS) in enterprise environments could expose air-gapped networks and their high-value assets to external attackers. A blog post by Nozomi Networks’ ICS analyst team explained that this flaw exists in all versions of the widely used IoT device C standard library uClibc and uClibc-ng, a special version of OpenWRT, a “general-purpose operating system for routers deployed in various critical infrastructure domains.” As a result, this vulnerability is present in well-known brand products from Linksys, Netgear, and Axis, as well as in Linux distributions like Embedded Gentoo. Since January 2022, this vulnerability has been disclosed to over 200 vendors and could affect millions of installed devices. As the DNS errors remain unpatched, no further details about the affected devices have been publicly provided, but after the library maintainers were unable to develop a fix, Nozomi provided detailed information about the flaw and its exploitability, hoping to seek help from the community. In DNS poisoning attacks, attackers can deceive DNS clients into accepting forged responses, thereby inducing a program to communicate with an arbitrarily defined endpoint instead of a legitimate one. Nozomi Networks stated that once successful, attackers could alter or intercept network traffic to compromise connected devices.

Researchers from the security company Pentera revealed in a blog post published on December 8 that organizations using air-gapped networks connected to DNS servers may inadvertently expose their assets to threat actors, leading to severe data breaches. Pentera’s researchers disclosed that attackers could use DNS as a command and control (C2) channel to communicate with these networks through DNS servers connected to the Internet, thereby compromising them, even if organizations believe their networks are successfully isolated.
The research from the two security companies indicates that air-gapping, as a commonly used security measure, is based on the idea of establishing an insurmountable barrier between digital assets and malicious actors. Organizations of various sizes across different industries use this technique to isolate sensitive networks. Many defenders may believe that by isolating their most sensitive information, even relying on physical isolation and offline backups, their critical assets are protected. However, the reality is far from it. As demonstrated by the provided example attacks, as long as the air-gapped segment connects to the same DNS server as the rest of the network, the risk of being compromised through DNS attacks is very real.
Air-gapped networks are isolated and cannot access the Internet from public user networks in business or enterprise IT environments. Researchers wrote that they are designed this way to protect the organization’s “crown jewels” (i.e., high-value core assets), using VPNs, SSL VPNs, or user networks to allow others to access them through jump boxes.
However, these networks still require DNS services, which are used to assign domain names for network discoverability. If network administrators do not carefully configure DNS, this represents a vulnerability.
Pentera’s network attack researcher Uriel Gabay told Dark Reading that their research demonstrates how DNS misconfigurations can inadvertently affect the integrity of air-gapped networks.
Gabay stated that this means for enterprises, by abusing DNS, hackers can gain access to air-gapped networks through stable communication lines, allowing them to steal sensitive data while their activities appear completely legitimate to the organization’s security protocols.
Misconfigured DNS Protocols
Gabay said that the most common mistake companies make when setting up air-gapped networks is believing they are creating an effective air gap when they link to a local DNS server. In many cases, these servers can link to public DNS servers, which means “they inadvertently break their own air gap.”
The researchers explained in their post that understanding how DNS works is crucial to understanding how attackers navigate its complexities to breach air gaps.
Common architectures for DNS connected to air-gapped networks:
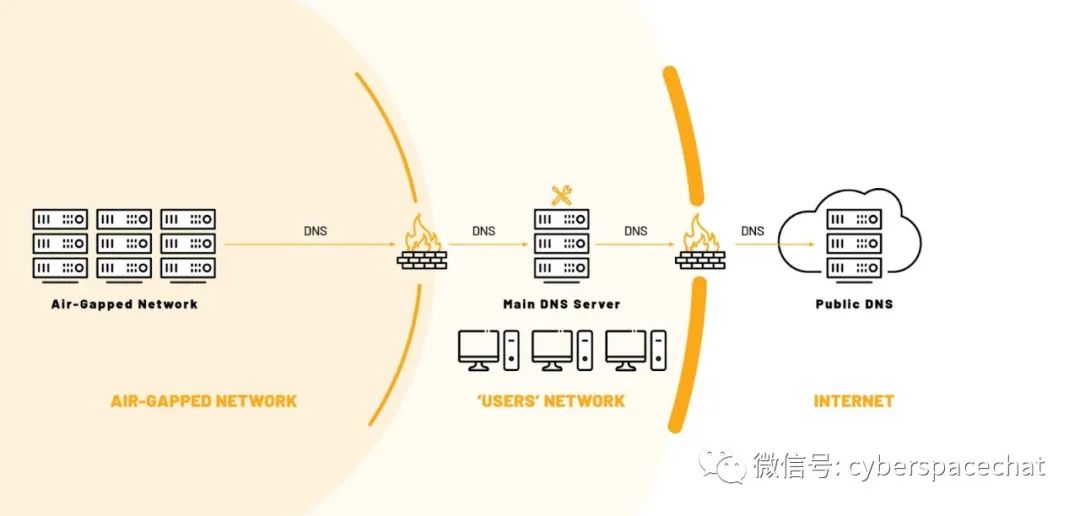
Air-gapped network DNS service directly connected to the main DNS service
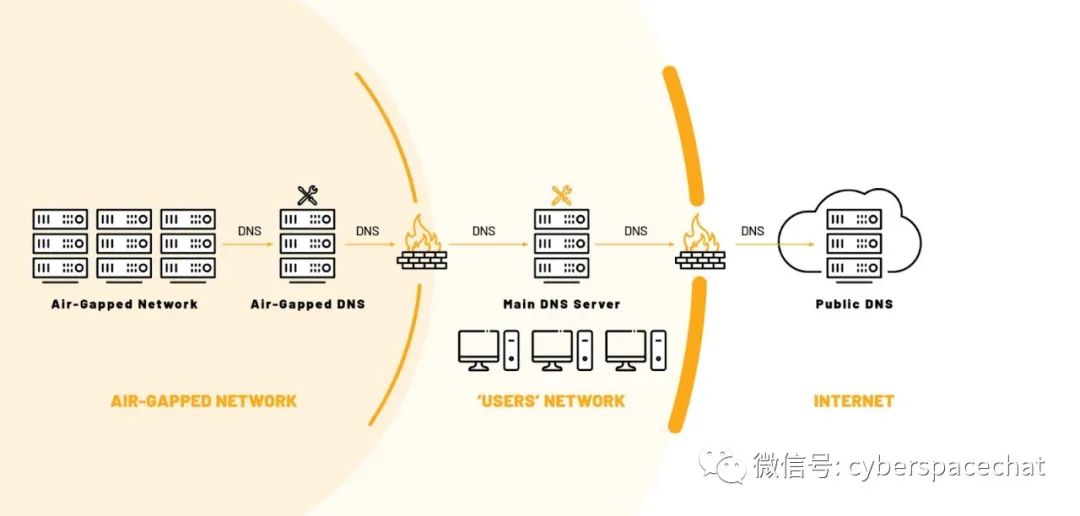
Air-gapped network DNS service connected to air-gapped DNS
In the second architecture, many organizations often mistakenly believe that routing communication through an internal DNS server can prevent potential violations. However, they remain vulnerable to attacks because internal DNS servers can still connect to public DNS servers.
The researchers explained that sending information via DNS can be accomplished by processing records handled by the request protocol (e.g., TXT, text records, or name server records) and placing information in the first part of the record name. Information can be received via DNS by requesting a TXT record and receiving a text response that returns that record.
While the DNS protocol can run over TCP, it primarily relies on UDP, which lacks built-in security mechanisms—this is one of the two key factors that attackers exploit in DNS. In UDP, there is also no control over the flow or order of data transmission.
Researchers explained that due to the lack of error detection in UDP, attackers can compress their payload before sending it and decompress it immediately after sending, which can be accomplished using any other type of encoding, such as base64.
Using DNS to Breach Air Gaps
Nevertheless, threat actors still face challenges in successfully communicating via DNS to breach air gaps. DNS has limitations on the types of characters accepted, so not all characters can be sent; researchers refer to those that cannot be sent as “bad characters.” There are also limitations on the length of characters that can be sent.
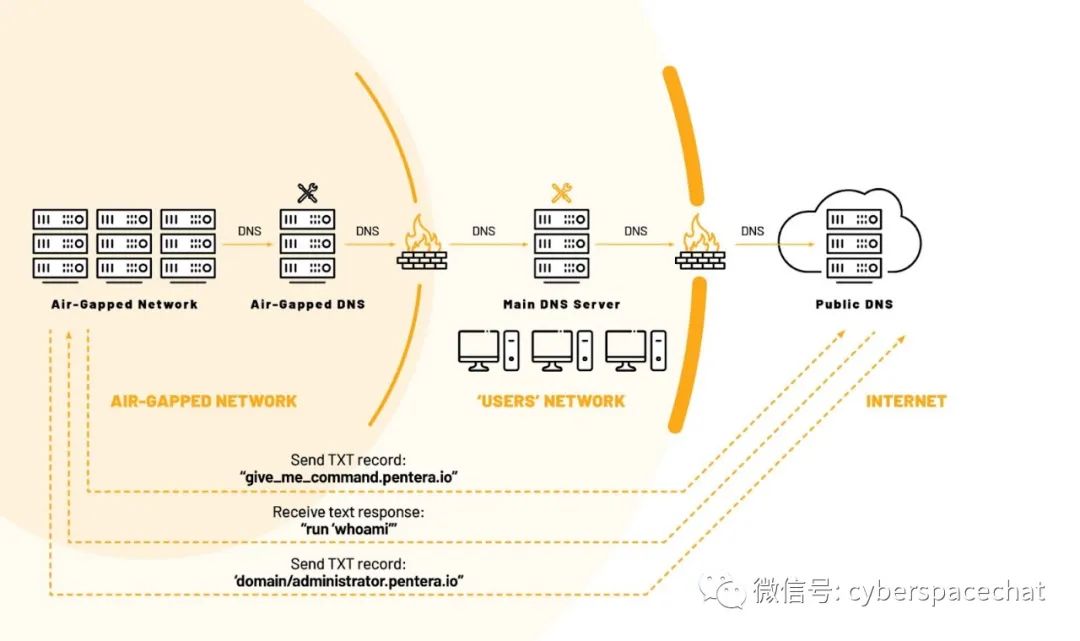
To receive DNS requests for any sub-records under “*.pentera.io,” attackers must have ownership permissions for the pentera.io root record and create a name server record pointing to a defined server. Once established, air-gapped networks with DNS services and Internet access can connect with attackers.
Researchers stated that to overcome the lack of control over data flow in DNS, threat actors can notify the server which packets to buffer and the expected last packet. They said that packets should not be sent until the attacker knows the previous packet has successfully arrived.
To avoid bad characters, attackers should apply base64 encoding to the data before sending it, while they can also split the data into chunks to send to avoid DNS character length limitations.
Researchers explained that to bypass defenders, attackers can generate domain names based on variables that both parties know and expect by blocking access to the server sending the requests.
“While executable files may not be particularly difficult, attackers or organizations need infrastructure to continue purchasing root records,” they noted.
Researchers stated that attackers can also configure malware to generate domains in DNS based on dates, allowing them to continuously send new requests through DNS using newly known root domains. They said that defending against this type of configuration “will be a challenge for organizations using static methods or even basic anomaly detection to detect and prevent.”
Mitigating DNS Attacks on Air-Gapped Networks
As DNS attacks occur more frequently than ever—according to the latest IDC Global DNS Threat Report, 88% of organizations reported some type of DNS attack in 2022—researchers understand that it is crucial for organizations to learn how to mitigate and defend against DNS abuse.
One approach is to create a dedicated DNS server for air-gapped networks, Gabay told Dark Reading. However, organizations must be careful to ensure that this server is not linked to any other DNS servers that may exist within the organization, as this “ultimately links it to DNS servers on the Internet,” he said.
Companies should also leverage IDS/IPS tools to create anomaly-based detection in the network to monitor and identify strange DNS activity, Gabay said. He noted that since all enterprise environments are unique, this type of solution will also be unique to an organization.
However, there are some common examples of what types of abnormal DNS behaviors should be monitored, including: DNS requests to malicious domains; a large number of DNS requests in a short period; and DNS requests made at odd times. Gabay added that organizations should also implement SNORT rules to monitor the length of requested DNS records.
References:
1.https://www.darkreading.com/attacks-breaches/report-air-gapped-networks-vulnerable-dns-attacks
2.https://pentera.io/blog/bypassing-air-gapped-networks-via-dns/?medium=article&campaign=pentera-labs-c2-over-dns
3.https://www.darkreading.com/vulnerabilities-threats/unpatched-dns-poisoning-bug-stumps-researchers
Original Source: NetEase Technology“Submission Contact: Sun Zhonghao 010-82992251 [email protected]”