Source:http://dwz.date/afUd
1. Basic Concepts of Encryption
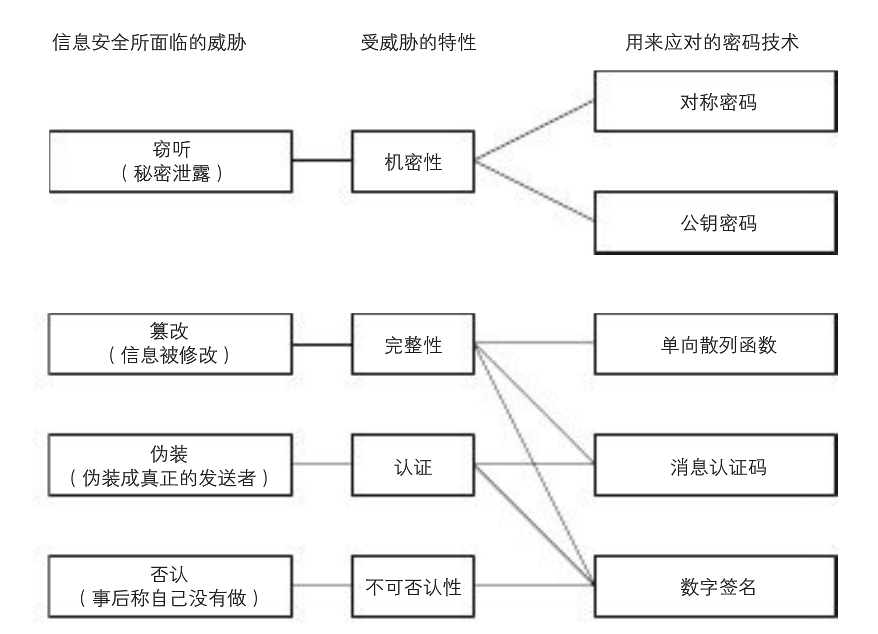
2. Applications of Data Encryption
3. Trends in Encryption Technology Development
4. Classification of Encryption Technologies
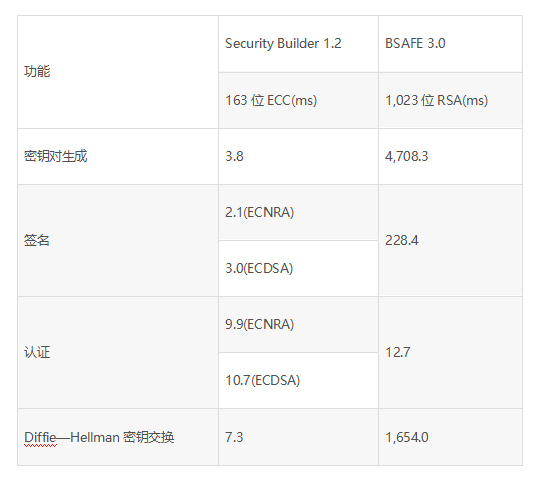
5. Introduction to Encryption Algorithms
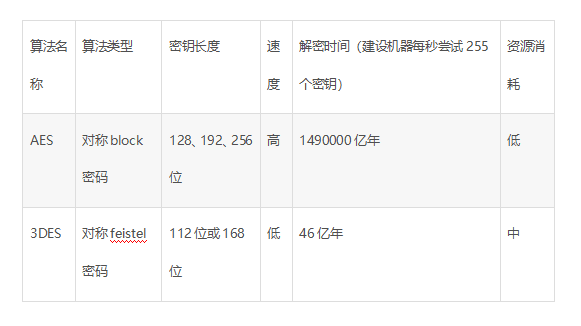
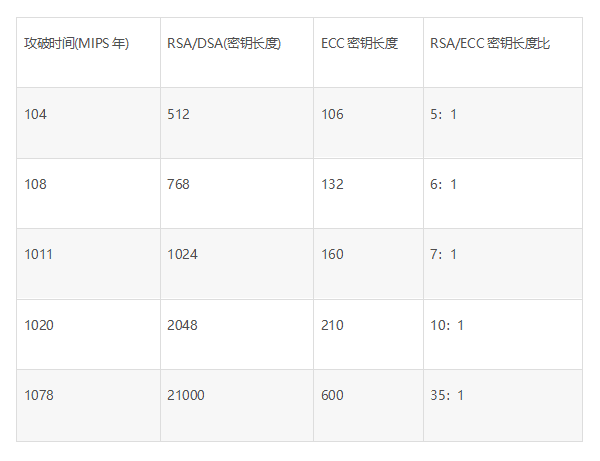
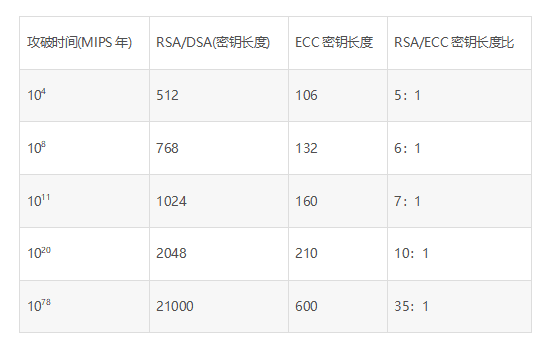
Source:http://dwz.date/afUd




