Author: Dou Er Bi’s Daily Link: https://www.jianshu.com/p/05a0f2ec935b
Security prevention technologies established and adopted for data processing systems to protect computer hardware, software, and data from accidental and malicious destruction, alteration, and leakage.
Main Cybersecurity Threats
• Unauthorized access • Information leakage or loss • Data integrity destruction • Denial of Service (DoS) attacks • Spreading viruses over the network, etc.
Five Basic Elements of Cybersecurity
• Confidentiality • Integrity • Availability • Controllability • Auditability
Classification of Cybersecurity
Divided into the following parts based on security needs: • Data confidentiality • Data integrity • Authentication • Authorization • Non-repudiation, for example, A cannot deny having sent data to B.
Based on solutions, it can be divided into the following: • Virus prevention • Firewalls • Access control (whether users can read, write, or have both functions) • Identity verification • Comprehensive security solutions • Classified by threat sources into network attacks, security vulnerabilities, and malicious code.
Cryptography
Cryptography includes cryptographic coding and cryptanalysis • Cryptographic coding: the design of cryptographic systems • Cryptanalysis: the technique of deducing plaintext from ciphertext without knowing the key.
Related Terms
Plaintext: The original form of information (plaintext, denoted as P) Ciphertext: The form of plaintext after encryption (ciphertext, denoted as C) Encryption: The process of converting plaintext into ciphertext (encrypt, denoted as E), usually implemented by encryption algorithms Decryption: The process of restoring ciphertext to plaintext (decrypt, denoted as D), usually implemented by decryption algorithms Key: Special information that both communicating parties must possess to effectively control the implementation of encryption and decryption algorithms; this information is called a key (key, denoted as K).
Based on Key Characteristics, Cryptographic Systems Are Divided Into
Asymmetric key systems and symmetric key systems.
1. Symmetric Key
Also known as traditional key, secret key, private key encryption (kept secret by both encryption and decryption parties, cannot be obtained by third parties), single-key encryption algorithm. The sender and receiver use the same key to encrypt and decrypt data. Its greatest advantage is the fast speed of encryption/decryption, suitable for encrypting large amounts of data. A major disadvantage of symmetric encryption is key management and distribution; in other words, how to send the key to the person who needs to decrypt your message is a problem. During the key transmission process, there is a significant risk that the key may be intercepted by hackers. The common practice is to asymmetrically encrypt the symmetric encryption key and then send it to the person who needs it. The core of symmetric key systems is that the same key is used for both encryption and decryption. Confidentiality depends solely on keeping the key secret, while the algorithm is public.
Execution Process of Symmetric Key Encryption Algorithm
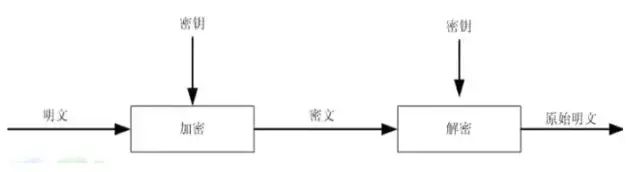
❀ Only the sender and receiver can obtain the plaintext; it remains in ciphertext form during network transmission.
Substitution Cipher keeps the natural order of letters a, b, c, d, …, w, x, y, z unchanged but corresponds them to D, E, F, G, …, X, A, B, C respectively: key is 3. For example, the plaintext caesar cipher corresponds to the ciphertext FDHVDU FLSKHU.
Transposition Cipher rearranges the bits or characters in the message according to a certain rule; the key’s purpose is to reorder the numbers: CIPHER order: 145326. For example: plaintext attackbeginsattwo corresponds to the ciphertext abaaitcnwtgtetkso.
Symmetric Key Encryption Algorithms Are Divided Into Two Categories:
• Algorithms that operate on a single bit (or byte) of plaintext at a time, known as stream ciphers. • Algorithms that operate on a group of bits (these groups are called blocks), known as block ciphers.
Block Cipher Systems
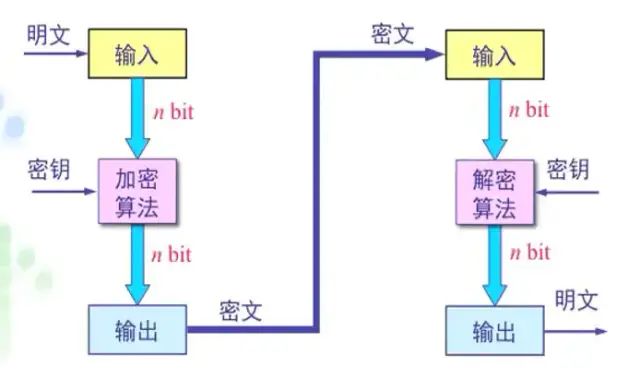
Data Encryption Standard (DES)
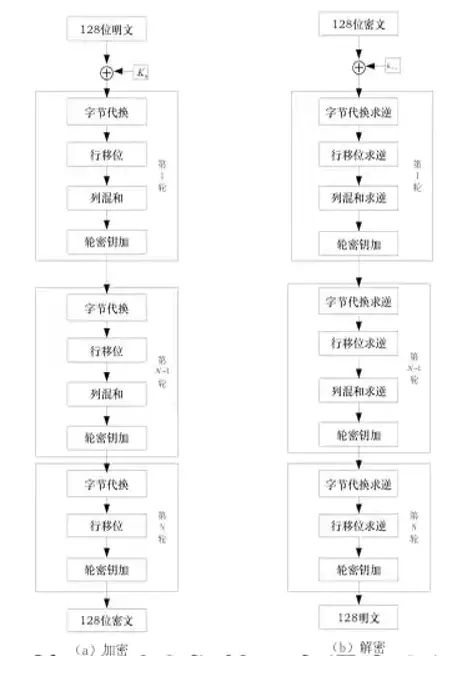
DES is the world’s first recognized practical cryptographic algorithm standard and is a typical block encryption algorithm. Before encryption, the entire plaintext is divided into blocks, each 64 bits long; using a 64-bit key, each 64-bit block is encrypted. Finally, the ciphertext blocks are concatenated to produce the entire ciphertext.
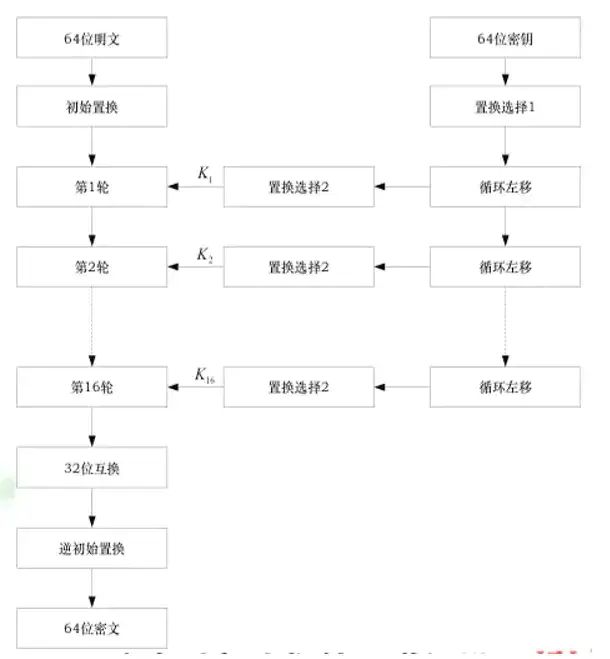
After a total of 16 rounds of substitution and permutation transformations, DES prevents cryptanalysts from gaining more information beyond the general characteristics of the algorithm.
Next Generation Encryption Standard (AES)
AES is an iterative, symmetric key block cipher. The algorithm can use 128, 192, or 256-bit keys and encrypts and decrypts data in 128-bit blocks, with the number of iterations determined by both block length and key length.
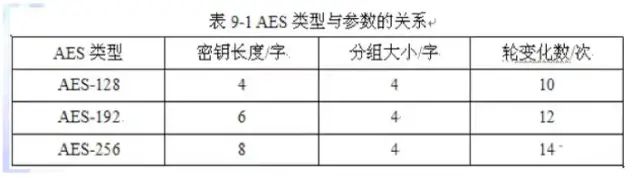
AES performs a series of operations on the input state array, arranged as a 4×4 byte matrix, processing the entire data block in parallel during each round.
2. Asymmetric Encryption Algorithms
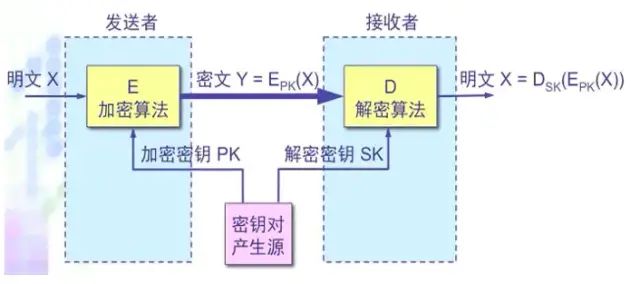
Public key systems are also called asymmetric encryption algorithms, requiring both a public key and a private key. Asymmetric encryption provides a very secure method for data encryption and decryption, using a pair of keys, the public key and the private key. The private key is securely kept by one party and cannot be leaked, while the public key can be given to anyone who requests it. Asymmetric encryption uses one of these keys for encryption, while decryption requires the other key. The public key (encryption key) and the asymmetric decryption algorithm are public, but the private key (decryption key) is confidential and kept securely by the key owner. The most famous public key mechanism is the RSA algorithm.
For example, if you request the public key from a bank, the bank will send you the public key, which you can use to encrypt messages, and only the holder of the private key—the bank—can decrypt your messages. Unlike symmetric encryption, the bank does not need to send the private key over the network, greatly improving security. Currently, the most commonly used asymmetric encryption algorithm is RSA. The public key mechanism is flexible, but encryption and decryption speeds are much slower than symmetric key encryption.
Public Key Cryptosystem
Characteristics of Public Key Algorithms:
• The sender encrypts plaintext X with the encryption key PK, and the receiver uses the decryption key SK to decrypt it, recovering the plaintext, or written as DSK(EPK(X)) = X • The encryption key is public, but it cannot be used for decryption, i.e., DPK(EPK(X)) ≠ X • A pair of PK and SK can be easily generated on a computer • It is practically impossible to derive SK from the known PK • Both encryption and decryption algorithms are public.
Although asymmetric encryption is very secure, it is much slower than symmetric encryption. Therefore, we still use symmetric encryption to transmit messages, but we can use asymmetric encryption to send the keys used for symmetric encryption. To explain this process, consider the following example: (1) Alice needs to make a transaction on the bank’s website. Her browser first generates a random number as the symmetric key. (2) Alice’s browser requests the public key from the bank. (3) The bank sends the public key to Alice. (4) Alice’s browser encrypts her symmetric key using the bank’s public key. (5) Alice’s browser sends the encrypted symmetric key to the bank. (6) The bank uses its private key to decrypt and obtain Alice’s symmetric key. (7) Alice and the bank can use the symmetric key to encrypt and decrypt their communication.
Digital Signatures and Message Authentication
In addition to the confidentiality of information, it is also very important to ensure that the source of the information is authentic and that the received information is reliable and has not been tampered with. Authentication includes two methods: user identity authentication and message correctness authentication. User authentication is used to verify whether the user’s identity is legitimate, which can be implemented using digital signature technology. Message authentication (also known as message integrity) is mainly used to verify that the received message is indeed from the true sender and has not been modified; it can also verify the order and timeliness of the message.
Message Authentication
The most commonly used methods for message authentication are Message Authentication Codes (MAC) and hash functions. MAC maps messages of arbitrary length to a short fixed-length data block under the control of a key, which is then attached to the message. The receiver authenticates the message by recalculating the MAC.
Digital Signatures
Also known as public key digital signatures, they are a string of digits that can only be generated by the sender of the information and cannot be forged by others. This string also serves as an effective proof of the authenticity of the information sent by the sender. It is similar to a physical signature written on paper but uses public key cryptography technology to implement it, serving as a method for verifying digital information. A set of digital signatures usually defines two complementary operations, one for signing and the other for verification. Digital signatures are applications of asymmetric key encryption technology and digital hashing technology.
Digital signature technology can resolve disputes arising in the following situations: Denial: The sender denies having sent a certain message; Forgery: The receiver forges a message and claims it is from the sender; Impersonation: A user on the network impersonates another user to receive or send messages; Tampering: The receiver modifies the received information.
Everyone has a pair of “keys” (digital identity), one of which only they know (the private key), and the other is public (the public key). The private key is used for signing, and the public key is used for verifying the signature. Since anyone can claim to be you, the public key must be registered with a trusted entity (certificate authority). After registration, the certificate authority issues a digital certificate. After signing a document, you send this digital certificate along with the document and signature to the receiver, who verifies with the certificate authority whether the document was indeed signed with your key.
Currently, the Most Widely Used Digital Signatures Include
• Hash signature • DSS signature • RSA signature • ElGamal digital signature.
Public Key Digital Signature

If Alice wants to deny having sent a message to Bob, Bob can present P and DA(P) to a third party. The third party can easily verify that Alice indeed sent X to Bob.
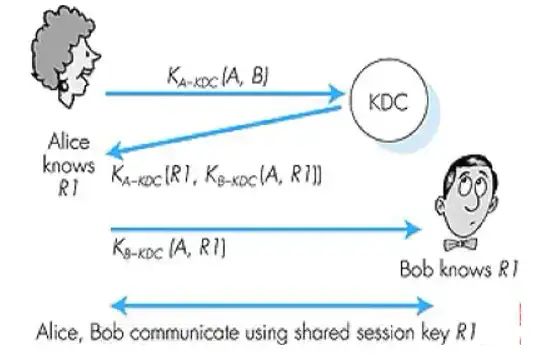
How can two entities achieve shared symmetric keys over a network? A trusted key distribution center (KDC) serves as an intermediary among many entities.
Key Distribution Center (KDC)
Alice and Bob need to share a symmetric key with KDC: providing different key services for each registered user. After registering with KDC, Alice and Bob obtain their symmetric keys, KA-KDC and KB-KDC.
When Alice obtains Bob’s public key (which can be from a website, email, or even a floppy disk), how can she trust that this is indeed Bob’s public key and not Trudy’s? A trusted certificate authority (CA) manages public keys for specific entities. Entities (individuals or routers) can register their public keys with the CA, which creates a certificate binding the entity to the public key, digitally signing the certificate.
When Alice needs Bob’s public key: she obtains Bob’s certificate (from Bob or elsewhere), verifies and decodes the CA-provided public key against Bob’s certificate to obtain Bob’s public key.

❀ Since encryption is meant to keep messages secret, only I can decrypt them, we conclude that the public key is responsible for encryption, and the private key is responsible for decryption. Similarly, since signing is meant to prevent impersonation, only I can issue this signature, we conclude that the private key is responsible for signing, and the public key is responsible for verification.
Overall Process
1. Bob has two keys, one public key and one private key.
2. Bob gives his public key to his friends—Patty, Doug, and Susan—one each.

3. Susan wants to send Bob a confidential letter. After writing, she encrypts it using Bob’s public key, achieving confidentiality.

4. Upon receiving the letter, Bob decrypts it with his private key and reads the content. It is essential to emphasize that as long as Bob’s private key is not leaked, the letter remains secure, even if it falls into the wrong hands.

5. Bob replies to Susan, deciding to use a “digital signature.” After writing, he first uses a hash function to generate a summary (digest) of the letter.
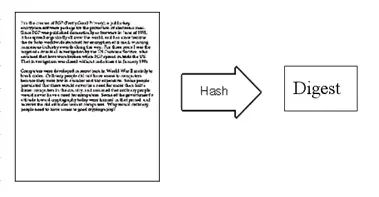
6. Then, Bob encrypts this digest with his private key, generating a “digital signature”.
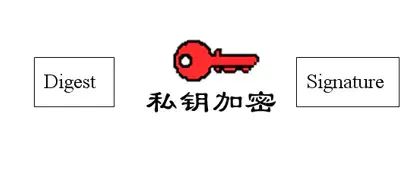
7. Bob attaches this signature to the letter and sends it to Susan.
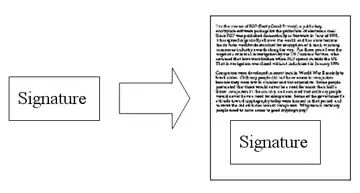
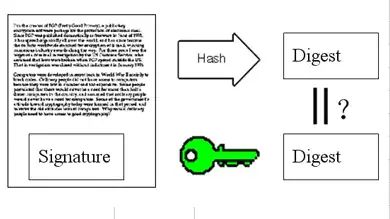
8. Upon receiving the letter, Susan removes the digital signature and decrypts it using Bob’s public key to obtain the letter’s digest. This proves that the letter was indeed sent by Bob.

9. Susan then applies the hash function to the letter itself, comparing the result with the digest obtained in the previous step. If they match, it proves that the letter has not been modified. The digest cannot be reversed to reveal the content, but some malicious individuals may not care about the content; they just want you to believe that the content is from them. However, if the digest needs to be encrypted, malicious individuals cannot decrypt it using the real sender’s public key. Therefore, digital signatures ensure that the content is genuinely sent by the sender and has not been tampered with.
10. A complex situation arises. Doug tries to deceive Susan by secretly using her computer to swap Bob’s public key with his own. At this point, Susan actually has Doug’s public key but still believes it to be Bob’s. Therefore, Doug can impersonate Bob, using his own private key to create a “digital signature” and write to Susan, allowing her to decrypt with the fake Bob’s public key.
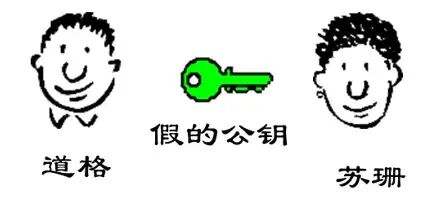
11. Later, Susan feels something is off and realizes she cannot determine whether the public key truly belongs to Bob. She thinks of a solution: she asks Bob to find the