Click the entrance above to immediately [Build Freely, Explore Limitlessly]
Join us for the annual technology feast!
Introduction
With the accelerated development of intelligence and connectivity in the automotive industry, automotive software represented by intelligent cockpits, assisted driving, autonomous driving, and vehicle networking is constantly innovating. Traditional distributed electronic and electrical architectures centered around ECUs struggle to meet consumer demands in the era of intelligent connectivity. The next generation of electronic and electrical architectures is evolving towards centralization, with domain controllers becoming mainstream, and a centralized computing platform for vehicles expected to emerge in the future. Automotive hardware will develop towards standardization, and the differentiation of vehicle functions and user experiences will rely on onboard software and cloud services. The decoupling of hardware and software, hardware embedding, and software upgrades will continuously release value throughout the longer lifecycle of vehicles.
Software-defined vehicles have become a consensus in the industry, but companies need to build new software development capabilities to meet the challenges of the software-defined era. For example, to improve development efficiency and avoid developing on expensive and limited embedded platforms, a more powerful and resource-efficient general-purpose computing platform should be adopted; agile development capabilities are required, where software code construction, continuous integration, and verification work need to be automated for quick validation to meet software iteration requirements; enhancing software portability, programs compiled in the development environment need to run on different embedded devices, including hardware test benches, boards, and vehicle ends, avoiding the need for code restructuring and recompilation due to environmental differences; managing massive data, including data storage, retrieval, and processing, to accelerate the AI/ML model training process; reducing interdependencies between software components to minimize the impact of software upgrades on other functions, with software requiring different security and real-time requirements being isolated and independent; with an increasing amount of onboard software code, effective management and maintenance of this code is necessary, utilizing a broader ecosystem of resources and capabilities for collaborative software development.
In 2021, Arm, AWS, and other founding members jointly announced the establishment of the Scalable Open Architecture For Embedded Edge (SOAFEE) Special Interest Group (SIG) to collaborate with automakers, semiconductor companies, software companies, and leading cloud technology enterprises to define a new open standard architecture to realize the lowest level technology stack for software-defined vehicles, providing a reference implementation that combines cloud-native technologies (such as microservices, containers, and orchestration systems) with automotive functional safety for the first time, thereby maintaining environmental parity.
Based on the services and cloud-native technologies on AWS, combined with the environment parity technology stack provided by SOAFEE, we can move the development of onboard software to the cloud, leveraging the elastic resource supply and accessibility of the cloud to enable developers to conduct parallel development and testing, meeting the computational power required for massive data processing, training, and testing verification work; through a continuous integration/continuous deployment (CI/CD) toolchain, the code can be automatically completed from submission to compilation verification, and then deployed to target embedded devices, improving iteration efficiency; microservices and containerization technologies ensure that application systems designed with a service-oriented architecture run in containers, with independent running environments, allowing for independent updates and deployments, while utilizing the hybrid task orchestrator provided by SOAFEE to ensure that the functional safety and real-time requirements for container operations are met; AWS’s Amazon Graviton provides an instruction set architecture (ISA) environment that is equivalent to that of the vehicle, allowing the compiled and verified software to run smoothly on HPC, hardware test benches, and vehicles based on Arm IP-licensed chips; SOAFEE’s open architecture, along with AWS’s support for open-source ecosystems, can empower the development of automotive software using open-source technologies, accelerating the development efficiency of automotive software and significantly reducing R&D costs, making software-defined vehicles a reality.
This article will introduce how to build cloud-native software-defined vehicles based on SOAFEE on AWS. It is based on ARM architecture Amazon Graviton instances to build a cloud environment that meets SOAFEE specifications, utilizing AWS’s native CI/CD toolchain for building and verifying automotive software in the cloud, and deploying it to the peer environment of the AVA developer platform on the edge through Amazon IoT Greengrass, achieving a cloud-native automotive software development process that integrates vehicle and cloud.
AboutAmazon Graviton,
Amazon CodePipeline,
Amazon CodeBuild, Amazon ECR,
Amazon IoT Greengrass
Amazon Graviton processors, custom SoCs based on ARM IP by AWS, provide the best price-performance ratio for cloud workloads running on Amazon EC2, making them ideal for running advanced compute-intensive workloads. This includes workloads such as high-performance computing (HPC), batch processing, ad serving, video encoding, gaming, scientific modeling, distributed analytics, and CPU-based machine learning inference.
Amazon CodePipeline is a fully managed continuous integration and continuous delivery service that helps you automate your release pipeline for fast and reliable application and infrastructure updates.
Amazon CodeBuild is a fully managed continuous integration service that compiles source code, runs tests, and produces software packages that are ready for deployment. With CodeBuild, you do not need to provision, manage, and scale your own build servers.
Amazon Elastic Container Registry (Amazon ECR) is a fully managed container registry that provides high-performance hosting, enabling you to reliably deploy application images and artifacts anywhere.
Amazon IoT Greengrass is an open-source edge runtime and cloud service for building, deploying, and managing device software. With pre-built or custom modular components, you can complete builds faster, easily adding or removing components to control device software deployment. It allows for large-scale remote deployment and management of device software and configurations without firmware updates. Amazon IoT Greengrass can easily bring intelligence to edge devices.
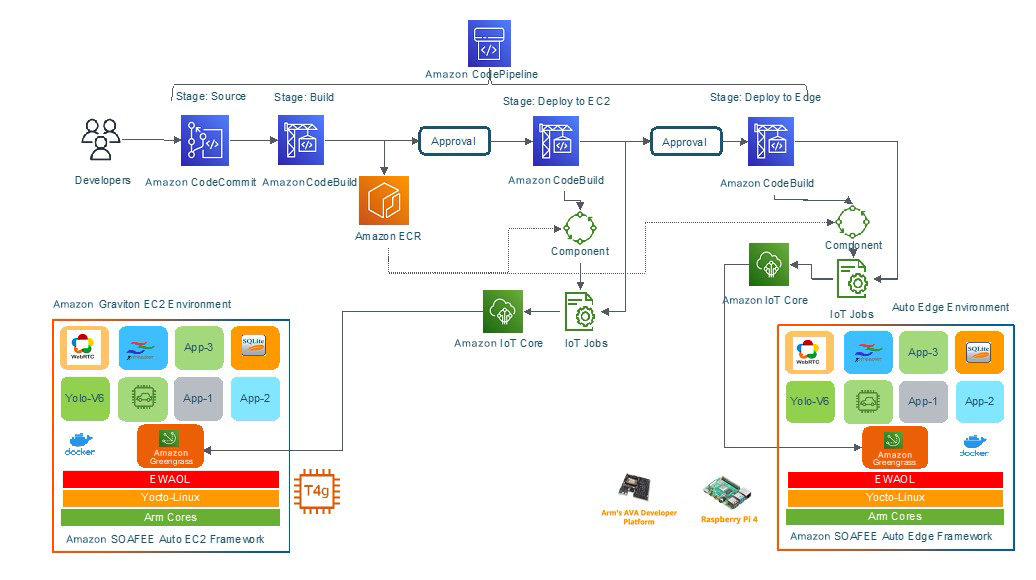
Solution Architecture Overview
This solution outlines how to build a software-defined vehicle based on the SOAFEE open architecture and cloud-native concepts on AWS. It builds a cloud environment that meets SOAFEE specifications based on ARM architecture Amazon Graviton instances, using AWS’s native DevOps CI/CD toolchain to build application images in the cloud, deploy them to the cloud environment for running and testing via Amazon IoT Greengrass, and then deploy them to the edge, which also meets SOAFEE specifications, AVA Developer Platform(https://docs.ipi.wiki/COMHPC/ava/index.html) or Raspberry Pi peer hardware environments for running and testing. This achieves a cloud-native software development process that integrates vehicle and cloud environments.
The overall architecture of the solution is as follows:
Prerequisites
-
An AWS account with Admin user permissions and the corresponding Access Key/Secret Key
-
A development host or EC2 virtual machine, Mac or Linux, with Amazon Command Line Interface installed
-
AVA Developer Platform
-
A Raspberry Pi 4B
Hands-on Operation Steps
This hands-on operation consists of four parts:
-
Deploying CI/CD pipeline on AWS
-
Deploying SOAFEE-compliant cloud Graviton instance environment
-
Configuring vehicle-side SOAFEE-compliant AVA Developer Platform or Raspberry Pi environment
-
Triggering the CI/CD pipeline to run the YOLO-V6 application in the cloud-vehicle peer environment
1
Deploying CI/CD Pipeline on AWS
This part will deploy the CI/CD pipeline in the Amazon cn-north-1 region using CDK.
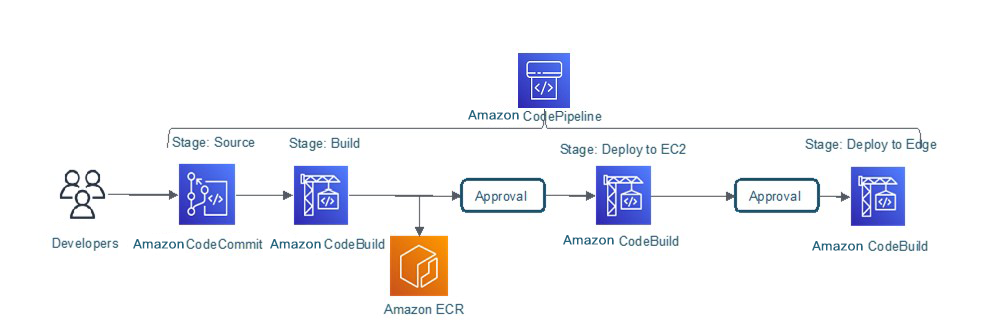
a). Clone the CDK code on the development host:
https://github.com/gaoykxp/aws-automotive-soafee-env-parity-blog
git clone https://github.com/gaoykxp/aws-automotive-soafee-env-parity-blog.git
Swipe left for more
b). Configure account access key and secret key using amazon configure:
aws configure
AWS Access Key ID [****************WO5D]:
AWS Secret Access Key [****************cJ8M]:
Default region name [cn-north-1]:
Default output format [json]:
Swipe left for more
c). Configure the CDK environment:
export ACCOUNT_ID=<account_id>
export AWS_REGION=cn-north-1
cd aws-automotive-soafee-env-parity-blog/
python3 -m venv .venv
source .venv/bin/activate
pip install --upgrade aws-cdk.core==1.99.0 wheel pandas pillow cython pycocotools matplotlib
pip install -r requirements.txt
cdk bootstrap aws://$ACCOUNT_ID/$AWS_REGION
cdk synth
cdk ls
</account_id>Swipe left for more
The output result is shown in the figure:
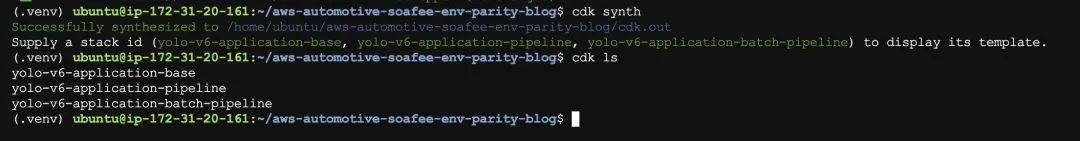
d). Build the CI/CD pipeline:
cdk deploy yolo-v6-application-pipeline
Swipe left for more
During the build process, type “y” to confirm the build, which will last a few minutes.
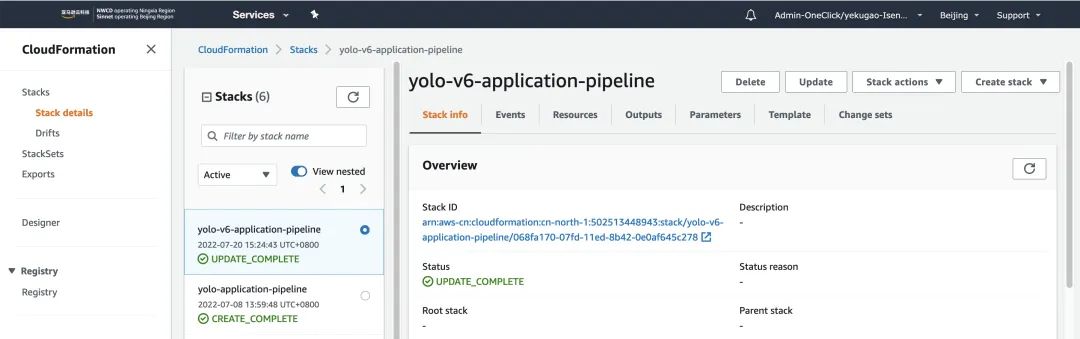
You can see the successful build of yolo-v6-application-pipeline in the CloudFormation Console.
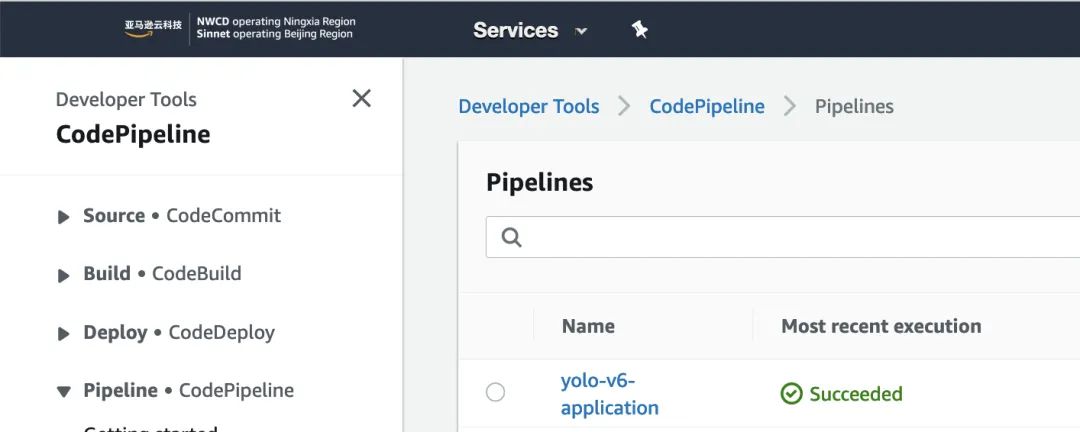
In the CodePipeline Console, you can see the pipeline for yolo-v6-application.
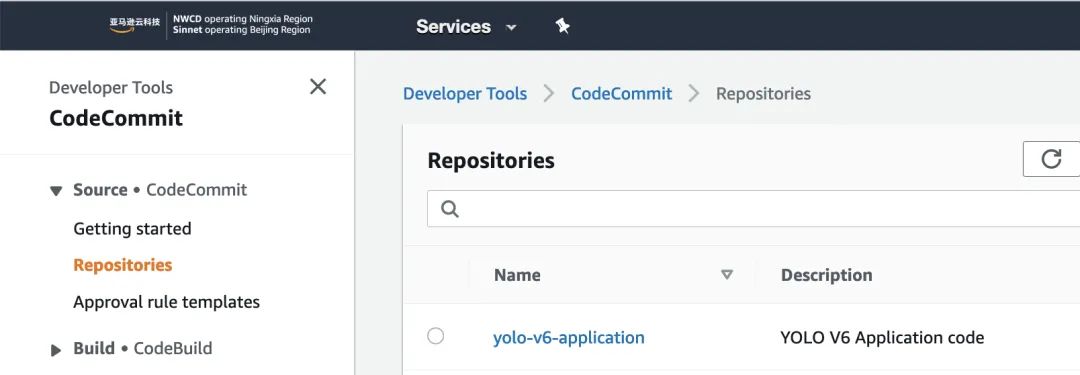
In CodeCommit, you can see that an empty yolo-v6-application repository has been built.
2
Deploying SOAFEE-compliant
Cloud Graviton Instance Environment
In this section, you will deploy a Yocto – EWAOL Linux AMI that supports the SOAFEE specification to an EC2 instance based on Amazon Graviton2. We have pre-built an AMI based on the guide and shared it with the community. You can also follow the guide to build your own AMI and deploy it in other AWS regions to practice this article.
Yocto:
https://www.yoctoproject.org
EWAOL:
https://gitlab.arm.com/ewaol/meta-ewaol
guide:
https://aws.amazon.com/cn/blogs/industries/building-an-automotive-embedded-linux-image-for-edge-using-arm-graviton-yocto-project-soafee/
a). Log in to the EC2 console in Amazon cn-north-1:
Click Launch instance,
In Step 1: Choose an Amazon Machine Image (AMI), enter AMI: ami-055b51e617a37d3c9 in the search box, and you will find this AMI image in Community AMIs.
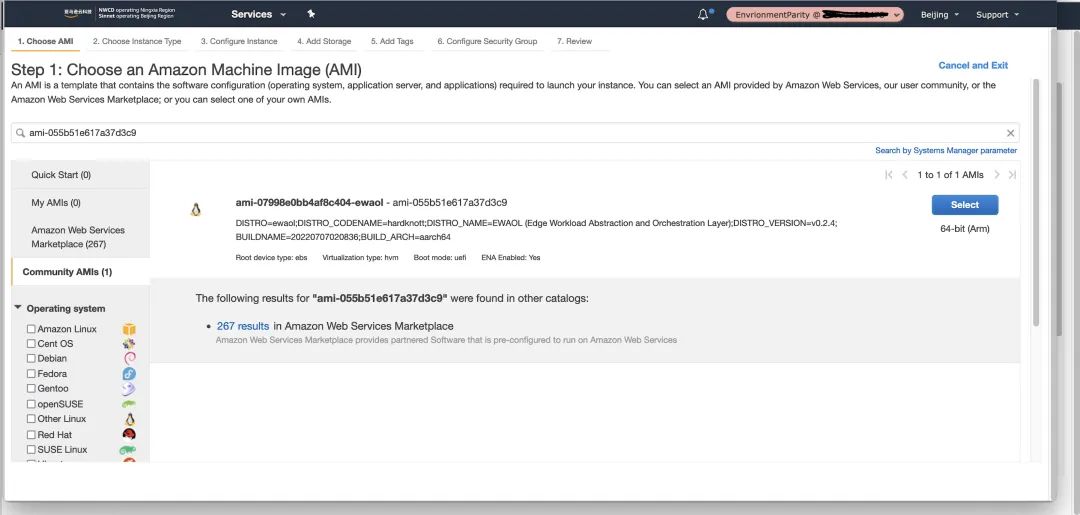
b). Select Select to build the EC2 instance:
Instance type: t4g.medium
Storage: 32GB
Other options set to default.
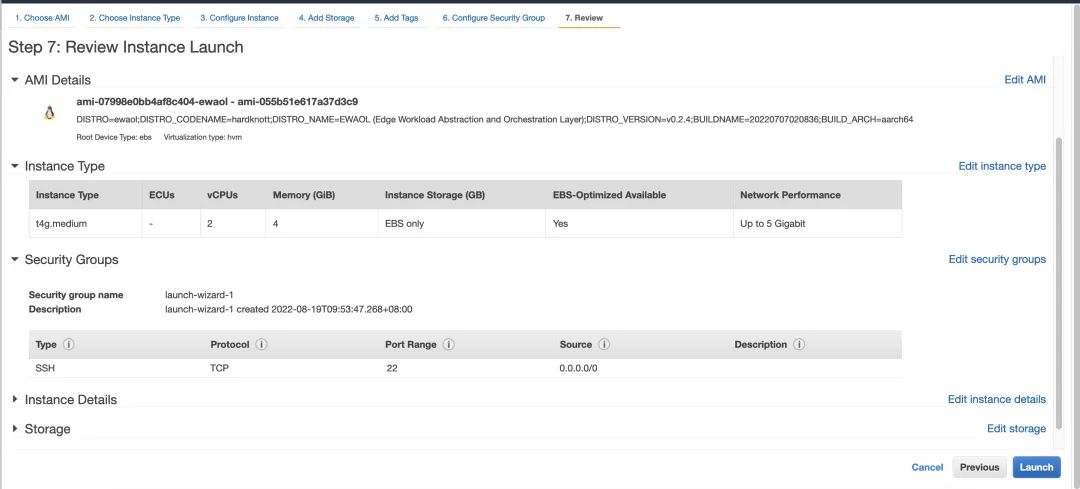
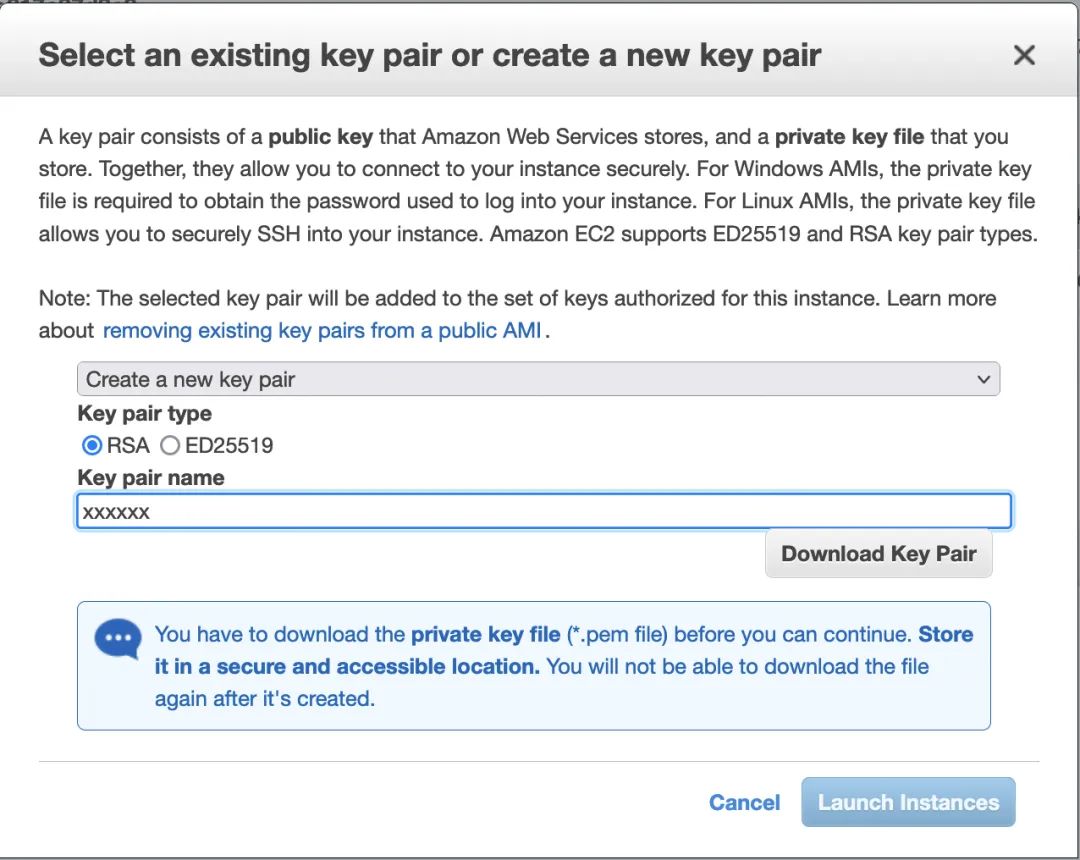
Launch,
Select an existing key pair or create a new key pair, which will be used for subsequent login to EC2 for related work.
Launch Instance, and you can see that the SOAFEE-compliant ARM-based Amazon Graviton2 t4g instance has been successfully built.
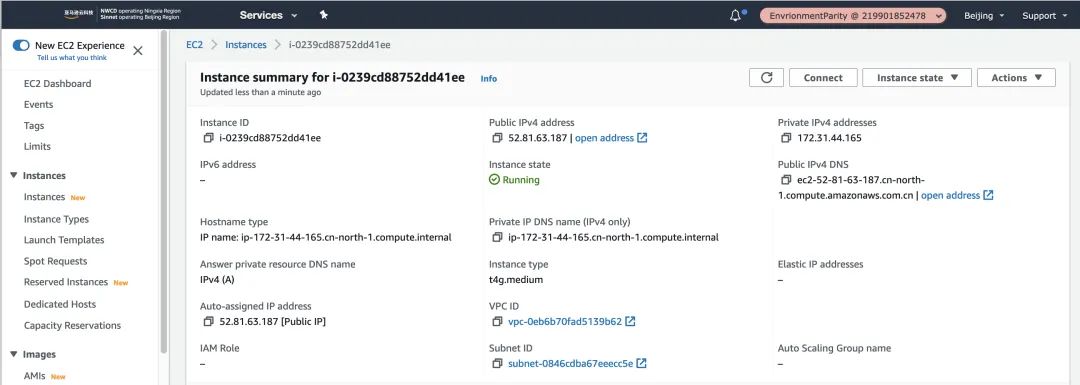
c). Log in to EC2:
Refer to the guide to log in to your EC2, you can use the recommended method in the guide or other SSH clients, using the key saved in step b), username: ewaol, log in to EC2.
Guide:
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/AccessingInstances.html
d). Adjust the size of the root partition:
You can execute each command one by one, or create a batch script and check the adjustment results before and after using the df -h command.
#!/bin/sh
# disabling swap
swapoff -a
sed -i '/.*swap.*/d' /etc/fstab
# trick to fix GPT
printf "fix\n" | parted ---pretend-input-tty /dev/nvme0n1 print
# remove partition 3 (swap)
parted -s /dev/nvme0n1 rm 3
# resize partition 2 to use 100% of available free space
parted -s /dev/nvme0n1 resizepart 2 100%
# resizing ext4 filesystem
resize2fs /dev/nvme0n1p2
Swipe left for more
e). Pull Greengrass docker image:
docker login -u gaoykxp
password: dckr_pat_V2EdQvcBONakG2HBcTan168yi14
Swipe left for more
docker pull gaoykxp/greengrass-v2-ubuntu-2204-aarch64:0.2
Swipe left for more
f). Create a Greengrass core device:
Run the following command to run the Greengrass docker container:
docker run -it -v /var/run/docker.sock:/var/run/docker.sock -v /usr/bin/docker:/usr/bin/docker --user root gaoykxp/greengrass-v2-ubuntu-2204-aarch64:0.2 /bin/bash
Swipe left for more
Set environment variables, using access key and secret key:
cd /home
export AWS_ACCESS_KEY_ID=xxxxxxxxxxxxx
export AWS_SECRET_ACCESS_KEY=xxxxxxxxxxx
Swipe left for more
Execute the following command to create and register the Greengrass core device:
java -Droot="/greengrass/v2" -Dlog.store=FILE \
-jar ./GreengrassInstaller/lib/Greengrass.jar \
--aws-region cn-north-1 \
--thing-name MySOAFEE-EC2-GreengrassCore \
--thing-group-name MySOAFEE-EC2-GreengrassCoreGroup \
--thing-policy-name GreengrassV2IoTThingPolicy \
--tes-role-name GreengrassV2TokenExchangeRole \
--tes-role-alias-name GreengrassCoreTokenExchangeRoleAlias \
--component-default-user ggc_user:ggc_group \
--provision true \
--setup-system-service true
Swipe left for more
/greengrass/v2/alts/current/distro/bin/loader
Swipe left for more
Start Greengrass.
In the IoT Core console, you can see the newly created Greengrass core device.
3
Configuring Vehicle-Side SOAFEE-compliant
AVA Developer Platform
or Raspberry Pi Environment
AVA Developer Platform is an automotive developer platform from ADLINK Technology, equipped with an ARM Neoverse-based Ampere processor, serving as a high-performance 32-core computing system capable of running autonomous workloads. It allows developers to leverage accelerator hardware (such as GPUs) to complement high-performance central processing units (CPUs). It is closer to the actual computing platform for automotive operations. If you have the opportunity to obtain the AVA development platform, you can follow the steps below to operate the Yocto-EWAOL environment on the AVA environment.
AVA Developer Platform:
https://docs.ipi.wiki/COMHPC/ava/index.html
a). Set up the AVA environment that complies with SOAFEE specifications:
Yocto and EWAOL are implementations of the ARM SOAFEE specification. Please follow the content of the guide to set up the AVA Developer Platform; due to space limitations, detailed introductions are not provided here.
Yocto:
https://www.yoctoproject.org
EWAOL:
https://gitlab.arm.com/ewaol/meta-ewaol
Guide:
https://docs.ipi.wiki/COMHPC/ava/YoctoInstallation.html
b). Log in to create a Greengrass core device:
SSH log in to the AVA control terminal, username root, password empty.
Follow the steps in section “2, Deploying SOAFEE-compliant Cloud Graviton Instance Environment,” steps e) Pull Greengrass docker image, f) Create Greengrass core device.
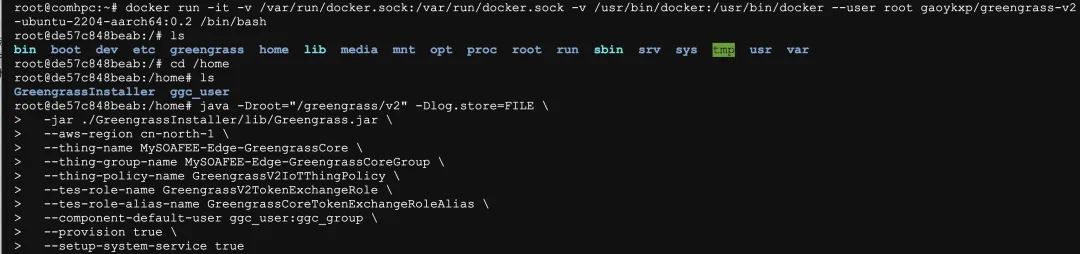
Remember to modify the thing-name to distinguish it from the Greengrass core device on the cloud EC2.
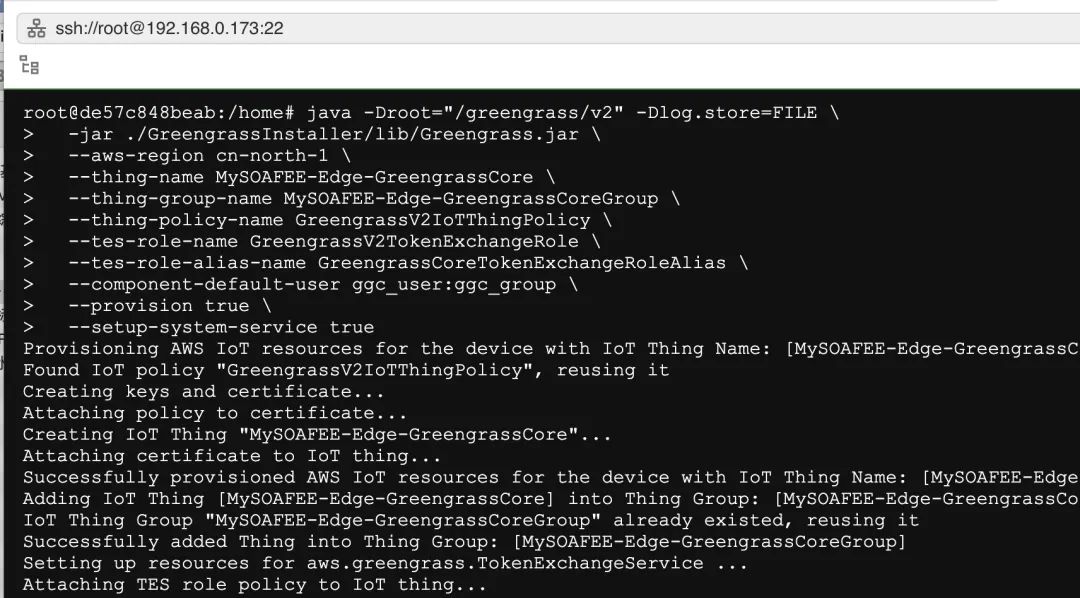
java -Droot="/greengrass/v2" -Dlog.store=FILE \
-jar ./GreengrassInstaller/lib/Greengrass.jar \
--aws-region cn-north-1 \
--thing-name MySOAFEE-Edge-GreengrassCore \
--thing-group-name MySOAFEE-Edge-GreengrassCoreGroup \
--thing-policy-name GreengrassV2IoTThingPolicy \
--tes-role-name GreengrassV2TokenExchangeRole \
--tes-role-alias-name GreengrassCoreTokenExchangeRoleAlias \
--component-default-user ggc_user:ggc_group \
--provision true \
--setup-system-service true
Swipe left for more
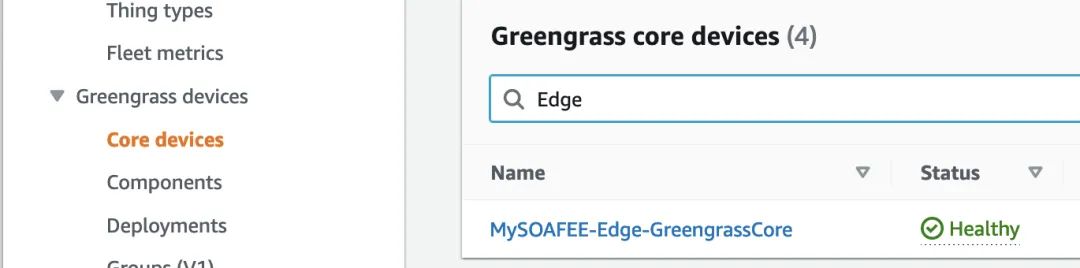
After successful creation, you can see the newly created Greengrass core device in the IoT Core console.
The Raspberry Pi is a low-cost embedded single-board computer with an ARM-based integrated CPU. For this article, if you do not have the AVA development platform, it can serve as a quick development validation target for the cloud-vehicle peer concept introduced.
a). Set up the Raspberry Pi 4B to comply with SOAFEE specifications for the Yocto-EWAOL environment:
Please follow the workshop(https://catalog.us-east-1.prod.workshops.aws/workshops/12f31c93-5926-4477-996c-d47f4524905d/en-US/10-getting-started/setup-rpi) content to set up the Raspberry Pi 4B; due to space limitations, detailed introductions are not provided here.
b). Create a Greengrass core device:
SSH log in to the Raspberry Pi control terminal, username: root, password: aws_workshop.
Follow the steps in section “2, Deploying SOAFEE-compliant Cloud Graviton Instance Environment,” steps e) Pull Greengrass docker image, f) Create Greengrass core device.
Remember to modify the thing-name to distinguish it from the Greengrass core device on the cloud EC2.
Other operations are the same as on the AVA platform.
java -Droot="/greengrass/v2" -Dlog.store=FILE \
-jar ./GreengrassInstaller/lib/Greengrass.jar \
--aws-region cn-north-1 \
--thing-name MySOAFEE-Edge-GreengrassCore \
--thing-group-name MySOAFEE-Edge-GreengrassCoreGroup \
--thing-policy-name GreengrassV2IoTThingPolicy \
--tes-role-name GreengrassV2TokenExchangeRole \
--tes-role-alias-name GreengrassCoreTokenExchangeRoleAlias \
--component-default-user ggc_user:ggc_group \
--provision true \
--setup-system-service true
Swipe left for more
4
Triggering CI/CD Pipeline,
Running YOLO-V6 Application in the Cloud-Vehicle Peer Environment
This part will demonstrate how to submit the YOLO-V6 application code, the build configuration file for CodeBuild, to CodeCommit, and trigger the CodePipeline to build the YOLO-V6 Docker image and push it to ECR. After Manual Approval, deploy the YOLO-V6 application to the cloud environment via IoT Core and Greengrass for testing and verification. Finally, after Manual Approval, deploy it to the vehicle edge environment for testing.
First Part: Cloud EC2 Peer Environment Deployment and Testing:
a). Copy the build file, YOLO-V6 application code, and inference images to the local repository of yolo-v6-application:
git clone https://git-codecommit.cn-north-1.amazonaws.com.cn/v1/repos/yolo-v6-application
cp -r ~/aws-automotive-soafee-env-parity-blog /yolo_v6_image_src /* ~/yolo-v6-application/
Swipe left for more
b). Submit the code to trigger the pipeline:
CodeCommit username and password can be obtained from IAM, Users, Security Credentials, HTTPS Git credentials for Amazon CodeCommit.
cd ~/yolo-v6-application
git add .
git commit -m "First commit yolo v6 sample application."
git push
Swipe left for more
c). Build the YOLO-V6 application image and push it to ECR:
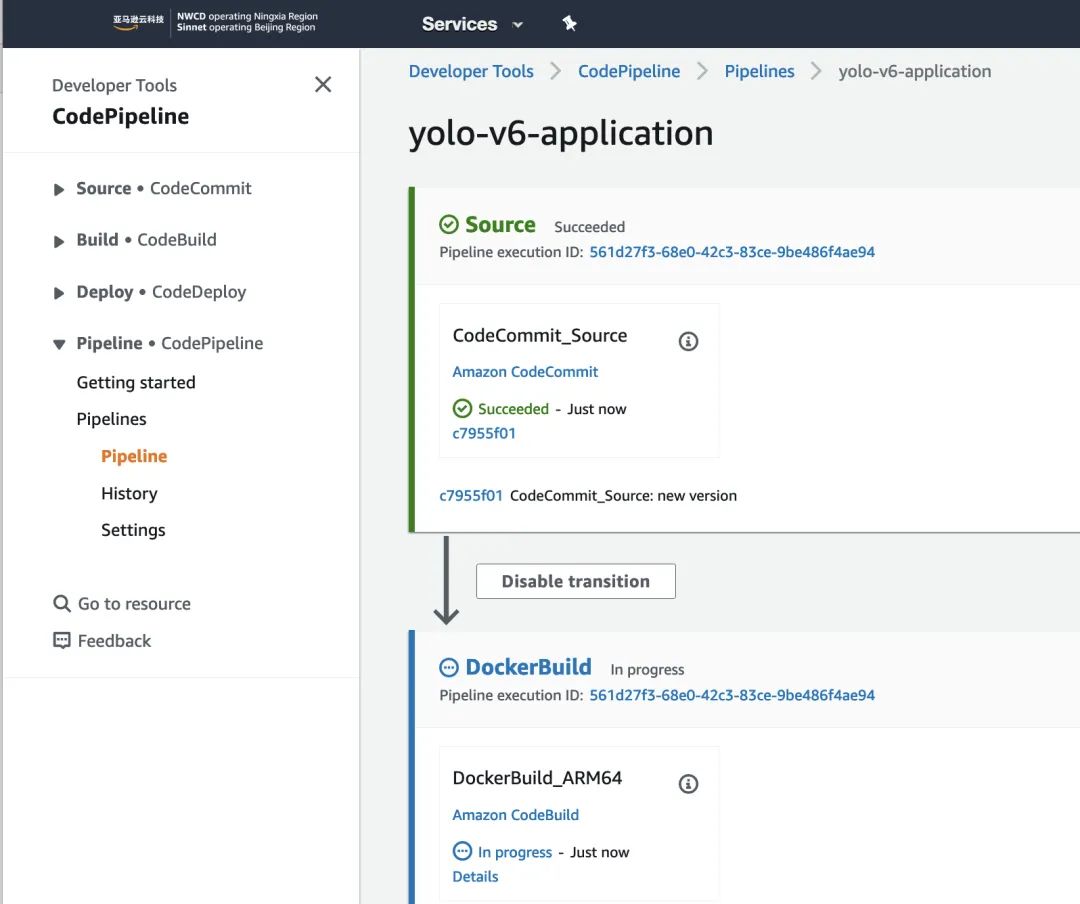
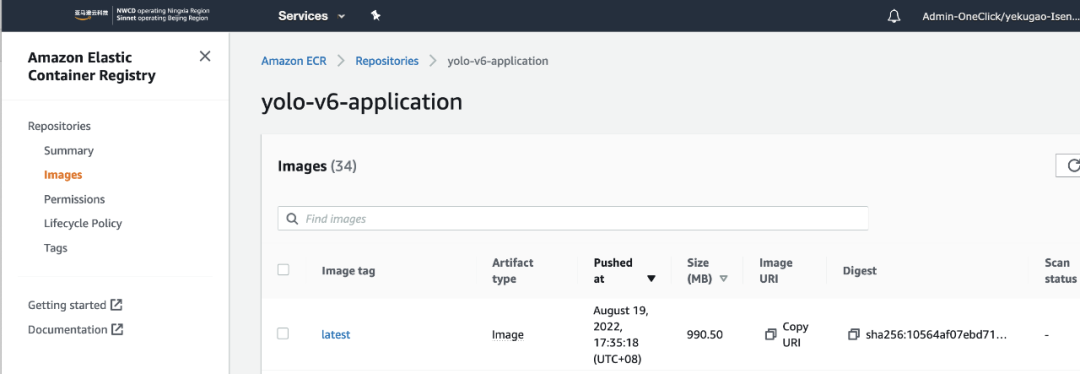
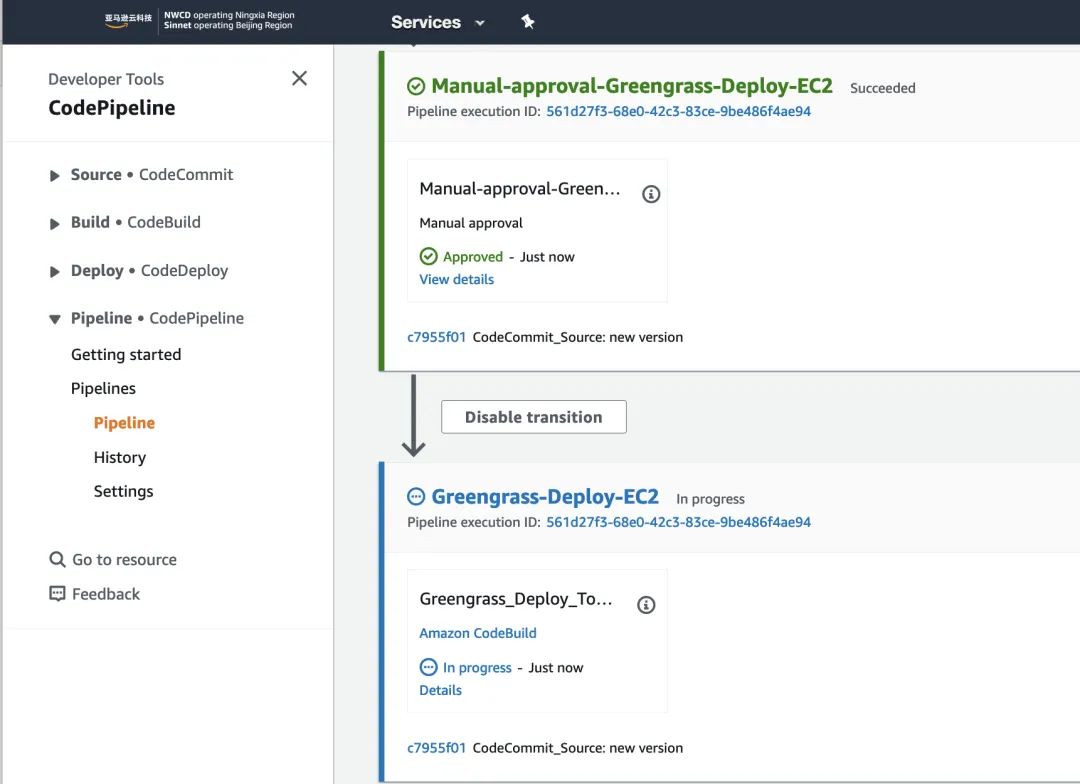
d). In CodePipeline, approve in Manual Approval to deploy YOLO-v6 to the cloud EC2 SOAFEE environment.
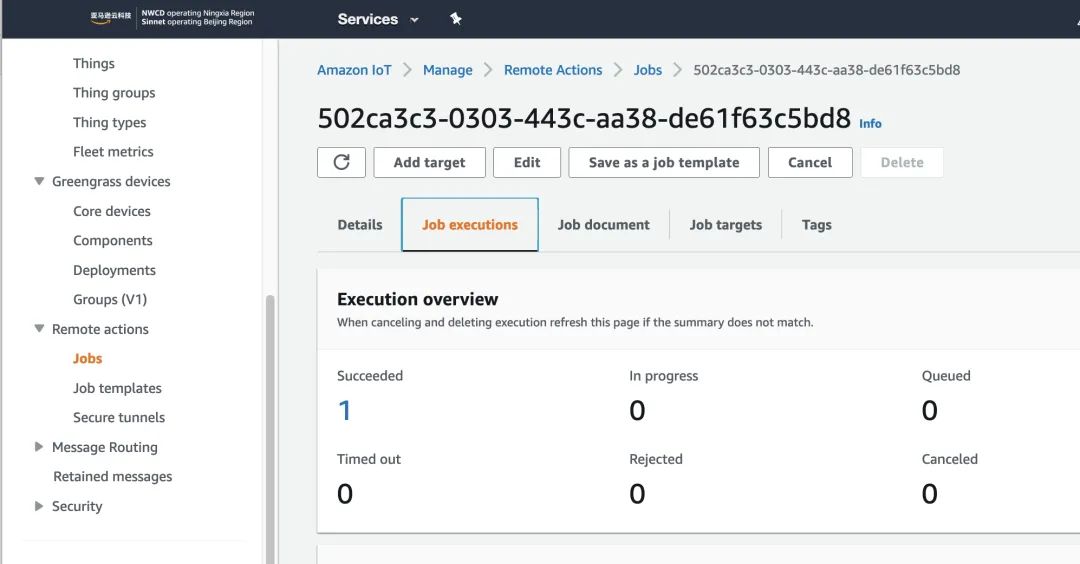
This process builds the Docker image for YOLO-v6 as a Greengrass Component and deploys it to EC2 via IoT Core. Ensure that Greengrass from the section “2, Deploying SOAFEE-compliant Cloud Graviton Instance Environment” is running normally. Check the deployment status in IoT Core.
e). After successful deployment, log in to the EC2 control terminal to verify the YOLO-v6 application.
Check whether the new YOLO-v6 image has been pulled to EC2.
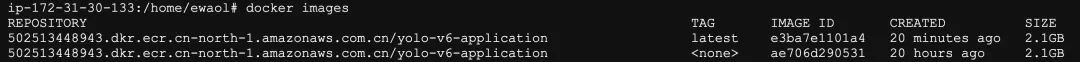
Run the command to execute the YOLO-v6 application, which will perform image inference operations and save the inference results in the ~/predictions folder of the EC2 host:
docker run -v ~/predictions:/home/YOLOv6/runs 501234xxxxxx.dkr.ecr.cn-north-1.amazonaws.com.cn/yolo-v6-application:latest
Swipe left for more
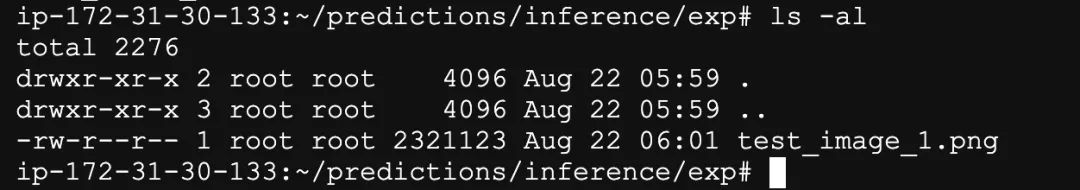
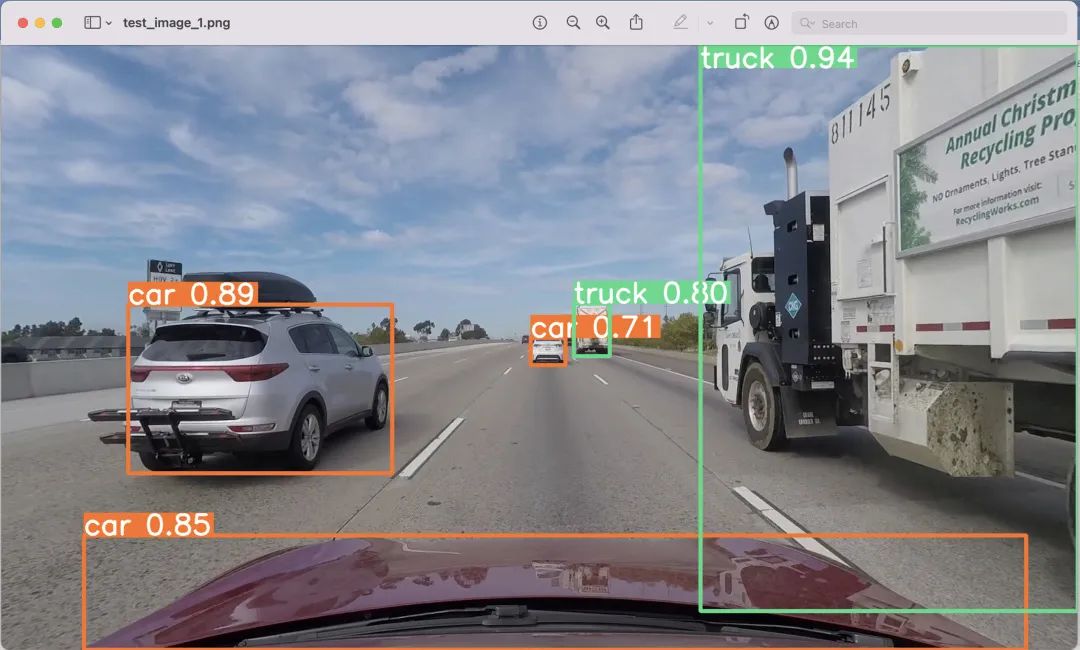
Download the inferred images from EC2 to your local computer using the scp command or SFTP client.
Second Part: Vehicle-Side Peer Environment Deployment and Testing:
a). Approve in Manual Approval in CodePipeline to deploy YOLO-v6 to the edge SOAFEE environment.
Ensure that Greengrass from the section “2, Deploying SOAFEE-compliant Cloud Graviton Instance Environment” is running normally. Check the deployment status in IoT Core.
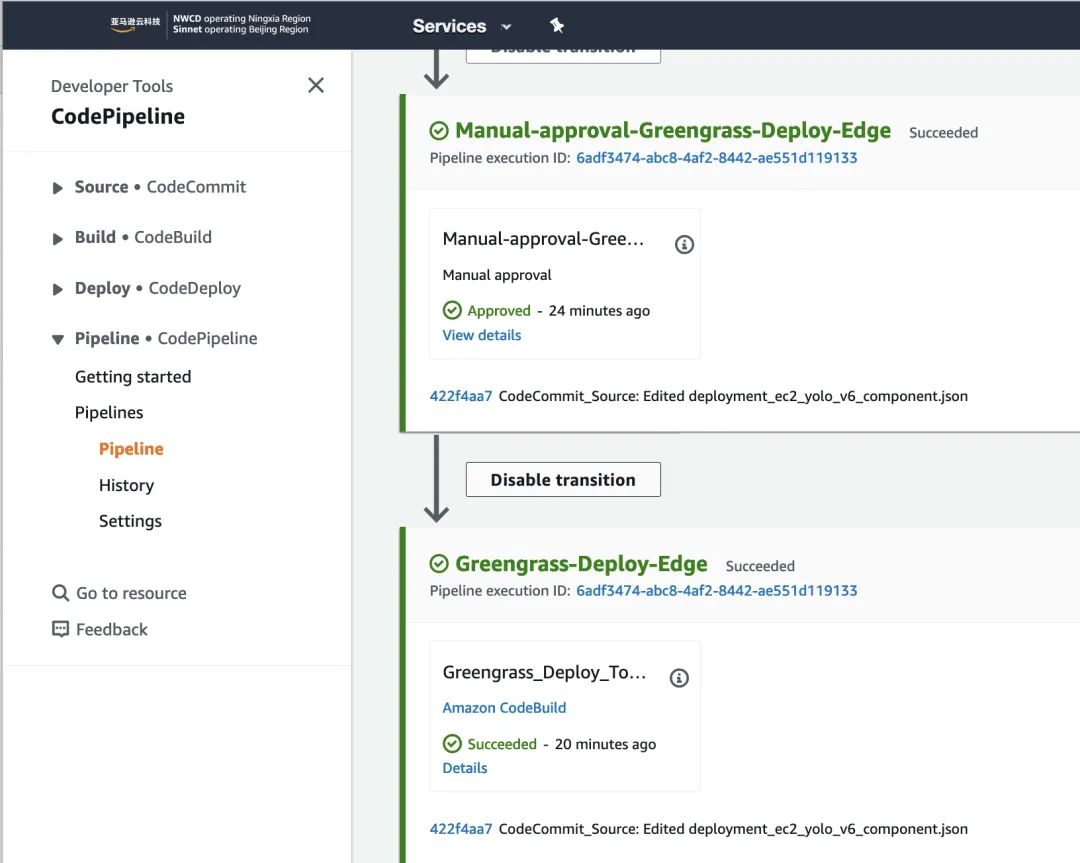
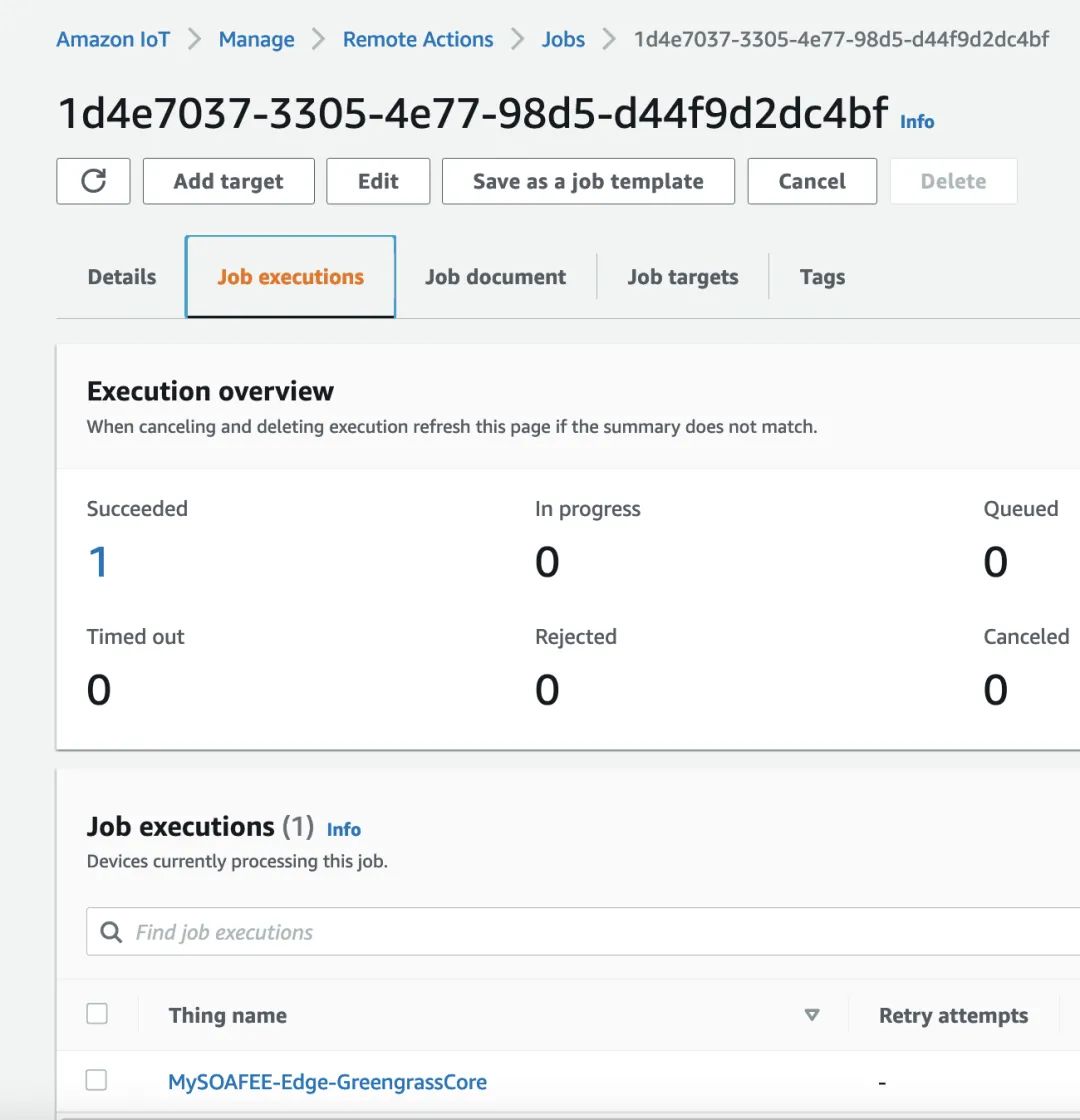
b). After successful deployment, log in to the vehicle edge device control terminal to verify the YOLO-v6 application.
Here we take AVA operations as an example, and the steps for Raspberry Pi are the same.
Open another scp client, log in to the AVA platform, and check the YOLO-v6 docker application image that was just deployed.
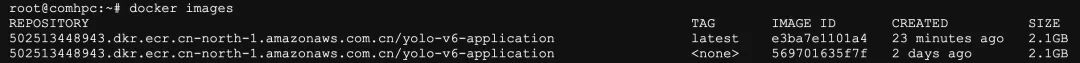
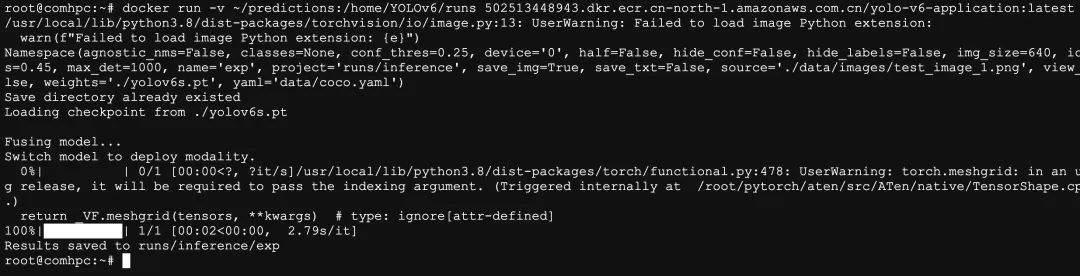
Run the command to execute the YOLO-v6 application, which will perform image inference operations:
docker run -v ~/predictions:/home/YOLOv6/runs 501234xxxxxx.dkr.ecr.cn-north-1.amazonaws.com.cn/yolo-v6-application:latest
Swipe left for more
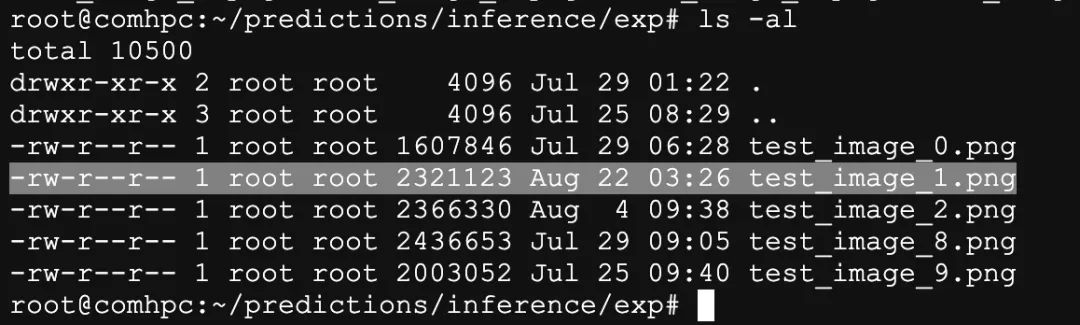
Find the inferred photos in the ~/predictions folder, similar to the operations in the cloud EC2, and you can download them to your local computer using scp.
Clean Up the Environment
After the practice, please shut down the relevant service resources.
In the aws-automotive-soafee-env-parity-blog folder, execute the command to clean up the resources created by cdk:
cdk destroy
In the EC2 console, terminate the EC2 instance.
Summary
In this article, we have step-by-step introduced how to build a software-defined vehicle based on the SOAFEE open architecture and cloud-native concepts on AWS. This includes building a cloud environment that meets SOAFEE specifications based on Amazon Graviton instances and building vehicle edge environments that comply with SOAFEE specifications on the AVA platform and Raspberry Pi peer environments. We also used AWS’s native DevOps CI/CD toolchain to build applications in the cloud, run and test in the cloud environment, and run and test in the vehicle peer hardware environment, achieving a cloud-native software development process that integrates vehicle and cloud environments.
References
Getting Started with Cloud-Native Automotive Software Development:
https://catalog.us-east-1.prod.workshops.aws/workshops/12f31c93-5926-4477-996c-d47f4524905d/en-US
This Article’s Authors

Gao Yekun
IoT architect of the AWS Professional Services team. Responsible for consulting, architecture, and delivery of solutions based on Amazon IoT, deeply involved in consulting and delivering IoT solutions in industries such as smart factories. He has over ten years of software development management experience in the IoT industry, including smart home and smart security.

Li Yan
Enterprise service manager of the AWS Professional Services team, with 20 years of experience, having served in various roles such as software engineer, solutions manager, and business development manager. He has rich experience in automotive industry solutions and business development and is currently responsible for designing and promoting software-defined vehicle solutions.

Click the entrance above [Sign Up Now]
Directly to the Amazon Cloud Technology China Summit with great speakers!

I’ve heard that clicking the four buttons below
will prevent you from encountering bugs!