
Attention:A gathering place for programmers to relax and share news
According to the analysis report of China’s internet network security monitoring data in the first half of 2020, malicious program control servers, denial of service attacks (DDoS), and other network attacks have been on the rise. To this day, network attacks have become one of the main factors affecting network information security and business information security.
Network attacks refer to actions that exploit vulnerabilities and security flaws in networks to attack the hardware and software of network systems and their data. The TCP/IP protocol, as the foundational protocol of the network, did not consider the numerous threats that networks would face from the very beginning of its design, leading to many attack methods. Since communication in networks originates from data packets, automatic collection and decoding analysis of these packets can quickly discover and trace network attacks.
TCP/IP Protocol
The industry typically divides the TCP/IP protocol stack into four layers: the Link Layer, Network Layer, Transport Layer, and Application Layer.
-
The Link Layer is primarily responsible for handling data transmission over physical media (such as Ethernet, Token Ring, etc.) and implementing network driver programs for network interface cards;
-
The Network Layer, which uses the IP protocol, is the core of the entire protocol stack. Its main functions include routing and forwarding data packets, achieving internetworking and congestion control;
-
The Transport Layer provides end-to-end communication for applications between hosts, defining two protocols: TCP and UDP;
-
The main function of the Application Layer is to handle the logic of applications, such as file transfer, name resolution, and network management. Protocols at this layer include the FTP file transfer protocol based on TCP, the HTTP hypertext transfer protocol, and the DNS domain name service based on UDP.
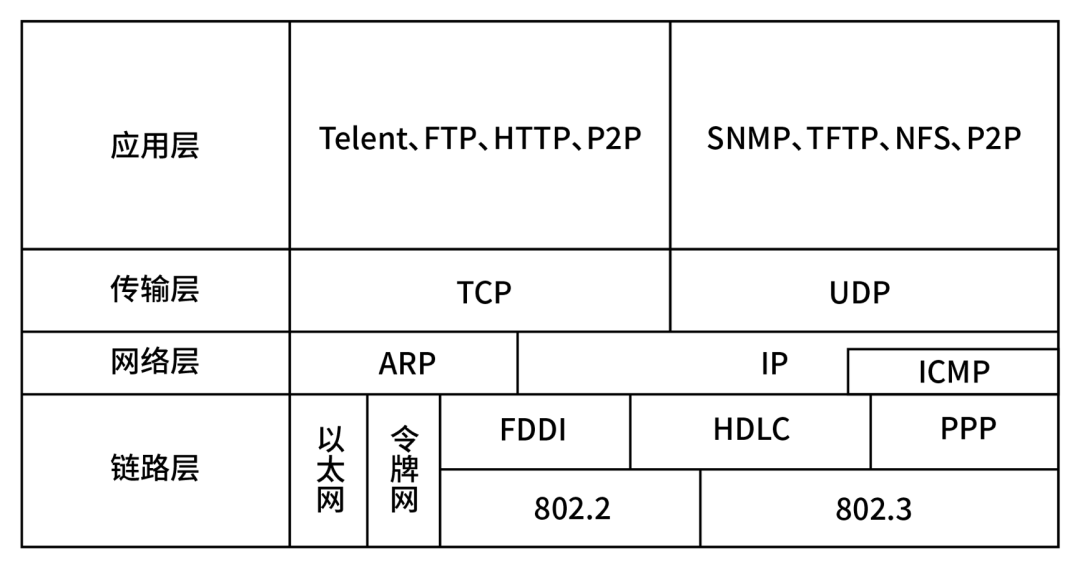
Since the TCP/IP protocol has four layers, each with different functions and protocols, the attack methods for different protocol layers also vary:
Attacks on the Link Layer mainly involve physical damage to network hardware and infrastructure or forcibly altering router routes; the IP protocol and ARP protocol are the two most important protocols at the Network Layer, with attacks on this layer including IP fragmentation attacks and ARP spoofing;
Since TCP and UDP are the two main protocols at the Transport Layer, there are many attacks targeting this layer, including DoS attacks; the Application Layer has the most protocols in the entire protocol stack, so the number of attacks on this layer is extremely large, with common examples such as DNS spoofing.
ARP Attacks
ARP (Address Resolution Protocol) resolves the IP addresses of network hosts into MAC addresses. Each host device has an ARP cache, which checks its own ARP cache to determine whether to map directly (if present) or broadcast an ARP request packet (if absent);
It then checks whether the target IP address in the data packet matches its own IP address. If they match, it can send an ARP response to inform the MAC address; when the source node receives the ARP response packet, it can add the obtained target host IP address and MAC address mapping to its own ARP cache.
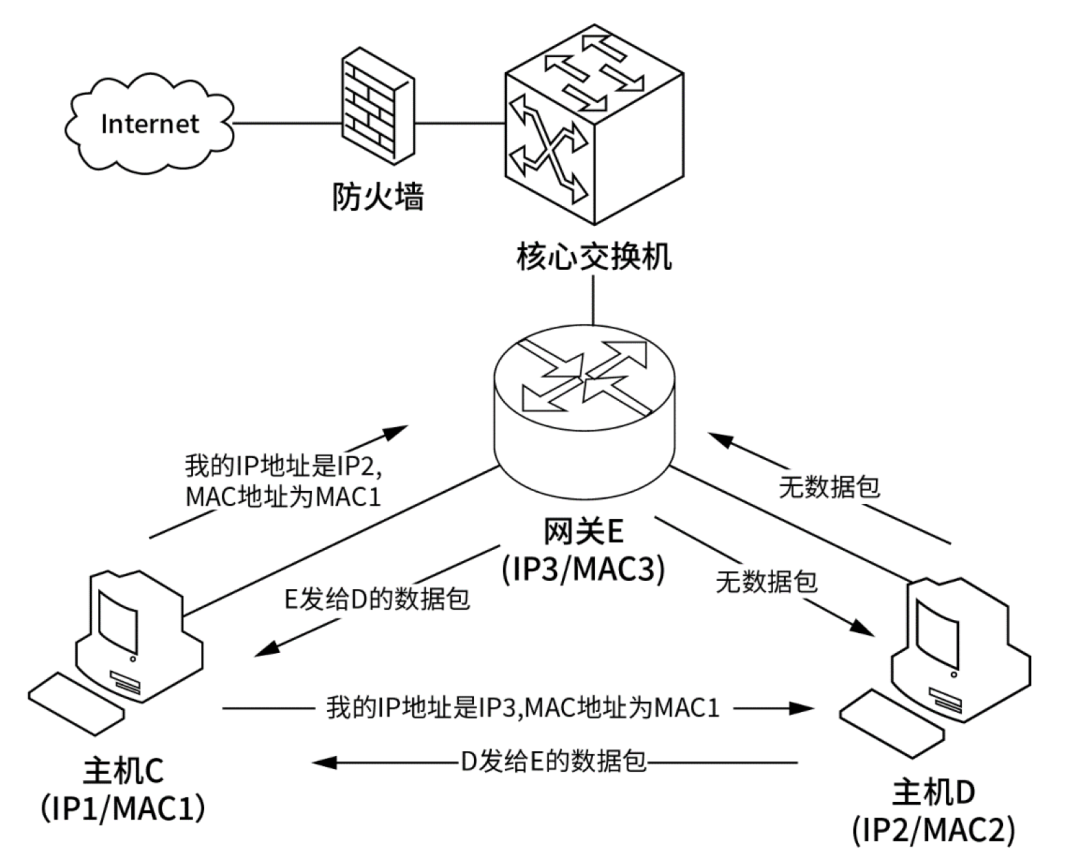
ARP attacks involve forging IP addresses and MAC addresses to achieve ARP spoofing. By generating a large volume of ARP communications in the network, the attacker can continuously send forged ARP response packets to change the IP-MAC entries in the target host’s ARP cache, causing network interruptions or man-in-the-middle attacks. Therefore, ARP attacks are often referred to as ARP spoofing.
Although ARP attacks can only occur on Ethernet and have a low threshold, their impact can be significant, leading to issues such as network disconnection, traffic limitations, and account theft. Network operations can implement ARP defense mechanisms, such as deploying network mirroring on switches to capture and analyze suspicious packets, and combining technologies like DHCP snooping and IP source protection to maintain network security.
DoS Attacks
The TCP protocol is a connection-oriented, reliable communication method based on streams, which can reduce bandwidth overhead due to retransmissions in poor network conditions.
Specifically, the TCP connection establishment process involves three steps, with each step simultaneously connecting the sender and receiver, commonly known as the “three-way handshake”: the sender sends a SYN packet, enters the SYN_SENT state, indicating the server port it plans to connect to and the initial sequence number, and waits for the receiver’s confirmation; the receiver receives the SYN packet and sends a SYN_ACK to confirm with the sender, entering the SYN_RECV state; the sender receives the SYN_ACK packet and sends an ACK to the receiver, completing the connection establishment.
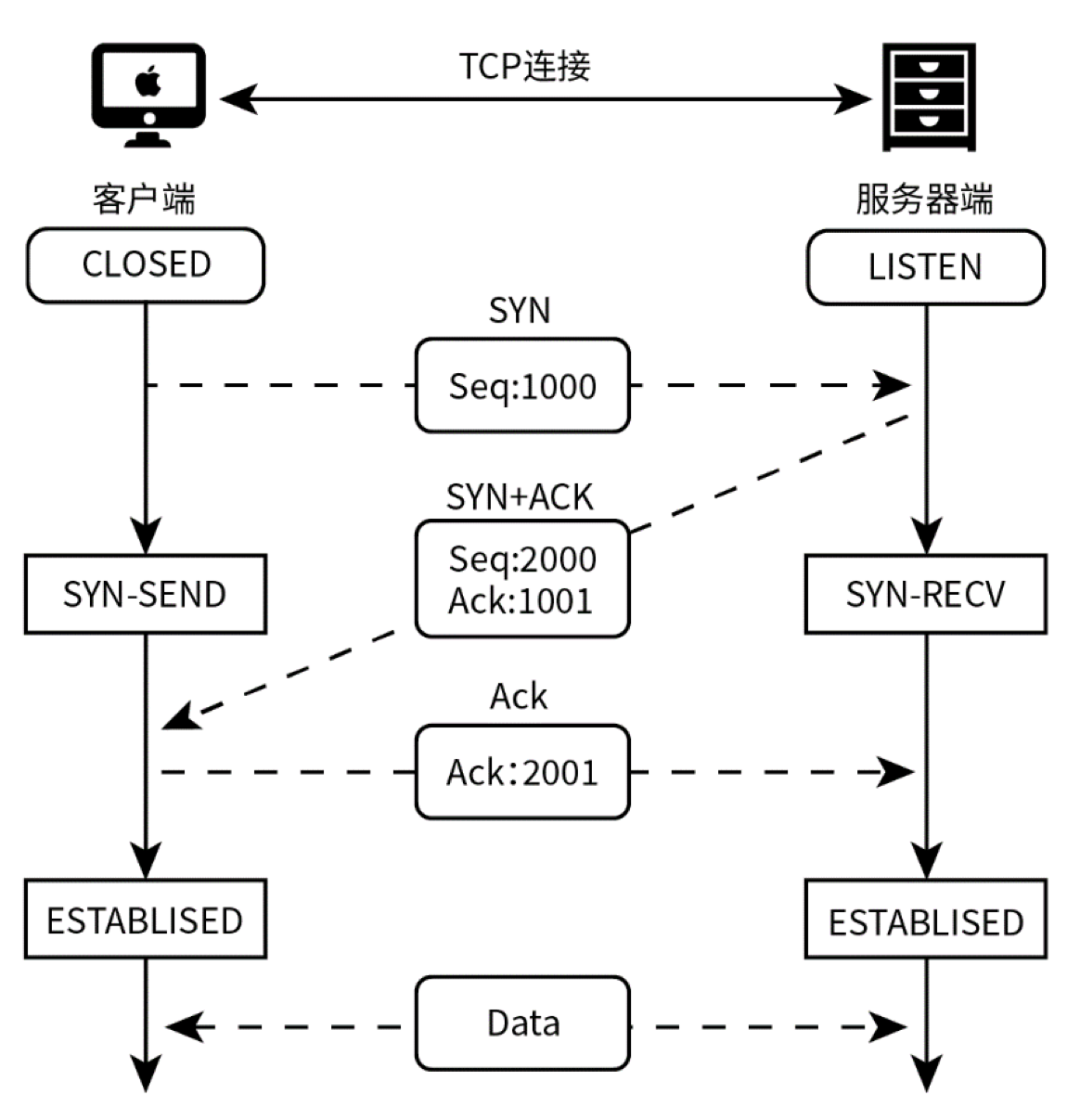
Since the TCP protocol is a connection-oriented transport control protocol, the main purpose of DoS attacks is to prevent user hosts or networks from receiving or processing external requests. For example, by generating a large volume of useless data, the network becomes congested, preventing the attacked host from communicating normally with the outside; exploiting connection flaws by repeatedly sending duplicate service requests, preventing it from processing other requests; or exploiting protocol flaws by repeatedly sending attack data, occupying host or system resources, leading to crashes.
In simple terms, a DoS (Denial of Service) attack typically uses packet flooding to disrupt or severely hinder the local system’s ability to respond to legitimate external requests, causing the local system to crash. SYN flood attacks are the most common type of DoS attack.
The attacker disguises their own IP source address and sends TCP connection requests to the local system; the local system replies with SYN-ACK to the disguised address, resulting in the local system not receiving the RST message and being unable to receive the ACK response, remaining in a half-connected state until resources are exhausted. The attacker sends connection requests faster than the TCP timeout release of resources, repeatedly requesting connections, causing the local service to be unable to accept other connections.
The best way to mitigate SYN flood attacks is to implement preventive strategies, using network performance management tools to automatically filter suspicious packets, shorten SYN Timeout periods, and set SYN Cookies. For each request, a cookie is set, and if a repeated SYN packet from a certain IP is received within a short time, it is deemed an attack, and that IP address is discarded.
DNS Attacks
The IP protocol relies on IP addresses and IP routers to transmit data packets from the source device to the destination device. IP addresses are machine-readable and usually long, making them unique but inconvenient to remember and use. Therefore, DNS was invented based on this need. DNS (Domain Name System) provides shorter, more readable, and practical domain names. Since domain names correspond one-to-one with IP addresses, users only need to enter the domain name in the address bar, and the system will directly resolve the domain name into an IP address.
After executing a domain search, the domain server saves the domain records, each containing a domain name and its corresponding IP address. If a record in the domain server is manually modified, it can manipulate the user’s access address, a behavior known as “domain hijacking.” The initiators of “domain hijacking” are domain server providers, so the effective solution to this problem is to abandon or switch domain servers.
In addition to “domain hijacking,” another common DNS attack is called “domain pollution” or “domain spoofing.” When a computer sends a “domain query” to the domain server, the server responds back to the computer. The process of sending requests and receiving information involves a time difference, during which a network attack can forge an erroneous response to the computer before the correct information is received, resulting in the computer receiving incorrect IP information.
In the face of network attacks, we need to enhance security awareness, actively maintain systems, strengthen firewall settings, and analyze data packets to trace network attacks. By collecting and decoding network data, we can grasp the most subtle changes in the network and configure effective alert information based on the characteristics or behaviors of network attacks, allowing for quick localization of attacks. We can also use network performance management tools with security features, such as TianDan Network Performance Management (NPM), which supports automatic analysis of suspicious packets like TCP port scanning, ARP attacks, and DoS attacks, achieving automatic alerts to ensure the normal transmission and use of data information.
Thank you for reading, hope this helps you 🙂
Source: blog.csdn.net/daocaokafei/article/details/116176790
 Mainstream Java Advanced Technologies (Learning Material Sharing)
Mainstream Java Advanced Technologies (Learning Material Sharing)
与其在网上拼命找题? 不如马上关注我们~
PS:因为公众号平台更改了推送规则,如果不想错过内容,记得读完点一下“在看”,加个“星标”,这样每次新文章推送才会第一时间出现在你的订阅列表里。点“在看”支持我们吧!