“PLC Data Encryption: Zero Trust Architecture + 5G Protection, Reducing Information Leakage Risk by 98%!”
Hello everyone! Today we will address the soul-searching question that keeps industrial control professionals awake at night: Has your PLC program ever been cracked? Has your production data ever been intercepted? Has the control of your devices ever been in the hands of hackers? Don’t panic, after reading this article, your PLC will be “bulletproof”!
First, let’s look at three bloody lessons:
In 2020, the Israeli water supply system was attacked by hackers, forcing an emergency change of all passwords, resulting in direct losses exceeding $5 million!
In 2003, the Slammer worm caused American automotive manufacturers to halt production, with daily losses reaching $20 million!
A food factory suffered a production line shutdown for 12 hours due to tampering with the PLC program, resulting in losses of millions and even making it to CCTV’s 315 program!
Traditional firewalls are like paper gates, while zero trust architecture is like a bodyguard. The AiTrust solution from Anheng Information employs triple verification:
Authentication: Fingerprint + Dynamic Token + Device Fingerprint, even our own engineers must “face-scan” to enter.
Dynamic Authorization: Permissions are reassessed every 30 seconds, like putting a “tightening spell” on visitors.
Behavior Analysis: Automatically identifies abnormal operations, such as downloading programs at 3 AM? Directly locks out!
Traditional WiFi is like “running naked”, while 5G+TSN is like an “armored vehicle”:
Deterministic Transmission: 10ms-1ms latency, with jitter at the microsecond level, faster than a blink.
End-to-End Encryption: National secret SM2/SM4 algorithms, data is “cloaked” throughout the process.
Network Slicing: Production data, management data, and video surveillance are separated.
Solution Comparison:
Three, PLC Firmware Protection: Blocking vulnerabilities from the source.
Three “tricks” from Siemens engineers:
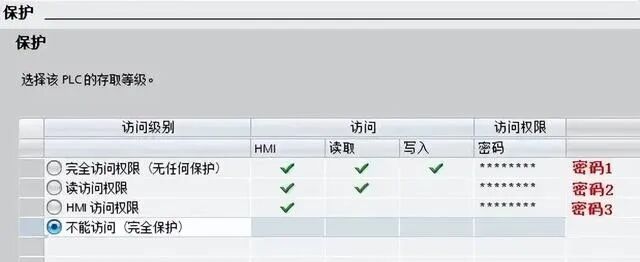
KNOWHOW Encryption: Code blocks are encrypted so that even the creator cannot unlock them; the client can only view but not modify.
High-Level Language Programming: Core logic is written in SCL and S7-GRAPH, which 90% of engineers cannot understand.
Data Traps: Hiding “landmines” in data blocks, causing pirated programs to crash.
Risk Assessment: Using Nessus to scan for vulnerabilities, creating a “hacker attack map”.
Solution Selection: Choose a combination of zero trust / 5G / firmware encryption based on the scenario.
Pilot Testing: First, use one production line as a “guinea pig” for 724-hour stress testing.
Full Promotion: Complete factory deployment within 3 months, along with security training.
Six, Interactive Session: Is your factory safe?
Has your PLC program ever been decrypted?
Is your production data directly connected to the internet?
Can engineers access the system after leaving?
Welfare Time: Like + Comment “Safety First”, the first 3 will receive the “Industrial Protocol Encryption Practical Manual”!
Finally, let me leave you with a harsh truth: Data security is not a multiple-choice question, but a matter of survival! Don’t let PLCs become cash cows for hackers; today’s investment in protection is tomorrow’s profit guarantee!