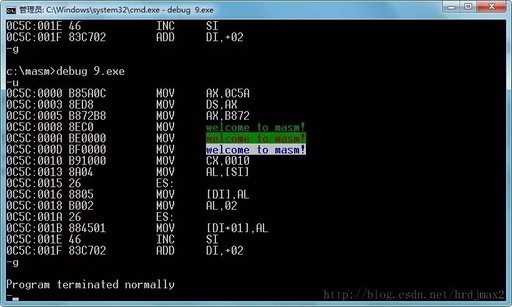
Setting Up an Assembly Language Development Environment on Windows 10 (Using DOSBOX and MASM32)
Limited Time Resource Download: Reply “Tutorial” to obtain a microcontroller eBook, reply “Simulation“ to get Proteus simulation materials, the Baidu Drive group sharing link update time: 2017-07-12, if it is invalid, please leave a message at the end of the article, do not leave a message in the background, you can also search for more … Read more