1. Introduction
1.1 Ransomware
Ransomware is a type of malicious software that runs on computers, kidnapping user files and rendering user data assets or computing resources unusable, and extorting money from users as a condition for restoring access. These user data assets include various files such as documents, databases, source code, images, and compressed files. The ransom is usually demanded in Bitcoin, with a few cases involving real currency or other virtual currencies.
According to existing documentation, the first ransomware emerged as early as 1989, but this is not relevant to the content of this article, so it will not be discussed. Recent ransomware began to gain popularity in 2012 and drew widespread attention in 2013. As of now, there have been millions of victims of ransomware, making it increasingly rampant.
1.2 Content of This Article
Considering the profound impact of ransomware, it is necessary to write an article that can help both non-technical personnel understand ransomware and encryption algorithms and assist technical personnel in conducting in-depth analysis. The author will organize and summarize recent work on ransomware and select 10 representative ransomware samples for in-depth discussion.
It should be noted that this article focuses on discussing the encryption algorithms of the 10 ransomware samples, without discussing their respective packing methods, anti-sandbox techniques, privilege escalation methods, and hiding techniques. Therefore, this article is positioned to introduce how these ransomware encryption algorithms work and whether they can be decrypted, among other related issues. Other issues, such as DLL injection, will be left for others to analyze.
In order to make it understandable for more non-technical personnel, the author prefers to use more colloquial language and descriptions to organize various issues related to ransomware, but this may lead to some imprecise or inaccurate points, which the technical personnel can grasp the general idea.
Finally, the author sincerely hopes that this article can help more victims recognize ransomware and rationally deal with encrypted files. It is also hoped that it can shorten the analysis time for other technical personnel and improve analysis efficiency. However, limited by the author’s personal knowledge, the author humbly asks readers to tolerate and point out any inappropriate or erroneous parts in the text.
1.3 Structure of the Article
The first chapter introduces the text of this article, allowing readers to judge whether the content discussed is relevant to their needs; the second chapter introduces the encryption algorithms of each sample one by one; the third chapter analyzes the reasons why ransomware has been decrypted, along with many other ransomware that have not been cracked; the fourth chapter provides the author’s opinions on the current trends in ransomware development.
2. Sample Analysis
Starting from this chapter, the author will introduce various ransomware to readers, with the 10 displayed ransomware sorted in alphabetical order. For each ransomware, the focus will be on its encryption process; if other aspects are of concern, corresponding materials can be sought separately.
In addition, each ransomware also has a large number of hash algorithms besides the encryption algorithms. Since these hash algorithms can increase the difficulty of understanding, they will be omitted in this article. Interested readers can analyze the various hash algorithms on their own.
2.1 Apocalypse
2.1.1 Overview of Apocalypse
The Apocalypse ransomware appeared in June 2016 and was cracked before it spread widely. However, the author still decided to analyze this ransomware because it can also serve as a representative of a certain type of ransomware encryption algorithm. The contents of a folder encrypted by Apocalypse ransomware are as follows:
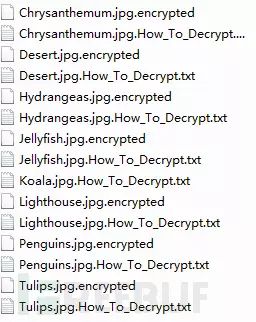
From the image, it is clear that all encrypted files have the extension .encrypted and a similarly named .txt file is generated to inform users that they have been infected by Apocalypse ransomware and to demand a ransom.
2.1.2 Apocalypse Encryption Process
Unlike all other ransomware, Apocalypse uses a custom encryption algorithm and embeds its key within the sample:
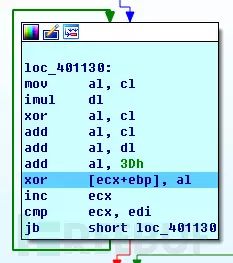
Here, dl holds the key used by this sample, and cl is the counter. After completing the encryption, the encrypted content is rewritten into the user file, and its suffix is changed to complete the encryption process.
2.1.3 Apocalypse Decryption Process
Through Apocalypse’s encryption algorithm, it can be understood that its custom encryption algorithm is a symmetric encryption algorithm. Therefore, its decryption algorithm is completely identical to the encryption algorithm.
More details about symmetric encryption algorithms can be found on wiki: <click to view the original link>
2.2 Cerber
2.2.1 Overview of Cerber
Cerber ransomware began to spread widely in March 2016. Files encrypted by Cerber have the extension Cerber, and as of the time of writing this section (September 2016), the latest version of Cerber has appeared with the extension Cerber2, which can be identified by its extension as belonging to the Cerber series. The Cerber ransomware sample analyzed in this section is not the latest sample; readers interested in the latest encryption samples can analyze them on their own.
Additionally, after being infected by Cerber ransomware, three additional files will be generated in each directory: # DECRYPT MYFILES #.txt, # DECRYPT MY FILES #.html, and # DECRYPT MY FILES #.vbs. These three files serve to inform users that they have been infected by Cerber ransomware and demand a ransom.
A folder infected with Cerber ransomware is shown in the image below:
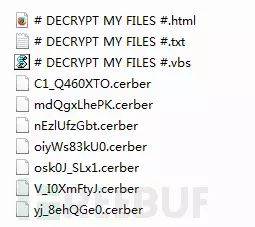
2.2.2 Cerber Encryption Process
The encryption algorithm of Cerber ransomware is based on RSA and RC4 algorithms. The encryption process is quite complex, and it cannot be fully displayed here, so only a few key points will be discussed. More details about RSA and RC4 algorithms can be found on wiki:
RSA: <click to view the original link>
RC4: <click to view the original link>
In brief, Cerber adopts a three-layer encryption method: first, the built-in RSA key is used to encrypt a randomly generated RSA key; then, the randomly generated RSA key is used to encrypt a randomly generated RC4 key; finally, the randomly generated RC4 key is used to encrypt user files.
Each Cerber sample has a built-in configuration file that is encrypted and stored in the resource section of the Cerber sample. Once decrypted, it reveals an RSA public key, as shown in the screenshot below:

At this point, the RSA public key is base64 encoded, which needs to be decoded before use.
A pair of randomly generated RSA keys is encrypted using this RSA public key. Subsequently, the randomly generated RSA key is used to encrypt a randomly generated RC4 key. This randomly generated RC4 key is the final key used for encrypting user files, and the core code for the RC4 algorithm that encrypts user files is as follows:
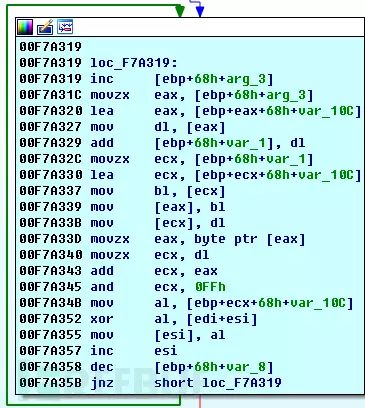
Additionally, it should be noted that Cerber ransomware does not encrypt the entire user file; instead, it randomly divides the user files into several parts and selects a portion of them for encryption. The final files generated by Cerber are slightly larger than the original user files, retaining block information and other key information needed for decryption.
2.2.3 Cerber Decryption Process
If one can correctly understand the encryption algorithm of Cerber ransomware, it is not difficult to derive its decryption algorithm. Ignoring some detailed issues, the decryption algorithm can be summarized as follows: first, obtain the RSA private key from the attacker’s C&C server, use that private key to decrypt the RC4 key, and then use the RC4 key to decrypt the user files.
2.3 CryptoWall
2.3.1 Overview of CryptoWall
CryptoWall is a ransomware that has spread widely abroad. The first version of CryptoWall appeared in 2014, and as of the time of writing this section, the latest version of CryptoWall is the fourth version. This section analyzes the third version of CryptoWall, and a directory infected with CryptoWall is shown in the image below:
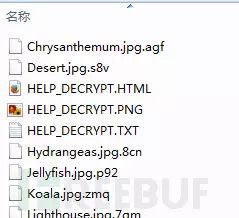
The file extension consists of three randomly generated characters. The three additional files generated in the folder are: HELP_DECRYPT.HTML, HELP_DECRYPT.PNG, HELP_DECRYPT.TXT. These three files are mainly used to inform users that their machine has been infected by CryptoWall ransomware and to demand a ransom.
2.3.2 CryptoWall Encryption Process
CryptoWall implements encryption using RSA and AES algorithms, and its encryption process primarily relies on the CryptAPI provided by Microsoft. Since the CryptoWall encryption public key needs to be obtained from the attacker’s C&C server, and several of the attacker’s C&C servers were quickly taken down, this somewhat suppressed the spread of CryptoWall.
More details about the AES algorithm and CryptAPI can be found on wiki:
AES: <click to view the original link>
CryptoAPI: <click to view the original link>
As previously mentioned, CryptoWall obtains the RSA public key from the C&C server, which is used to encrypt a randomly generated AES key:
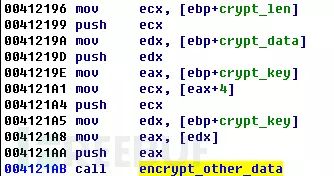
Then, the randomly generated AES key is used to encrypt the victim’s user files:
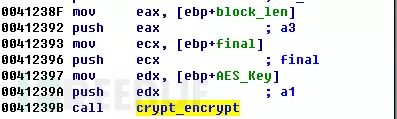
Finally, the encrypted user files and other additional information are written together into the final generated file.
2.3.3 CryptoWall Decryption Process
The decryption process of CryptoWall ransomware is very similar to the encryption process. The first step is also to obtain the key from the attacker’s C&C server, but this time the RSA private key is obtained. Then, the AES key is decrypted using that private key. Each user file has a randomly generated AES private key, which is then used to decrypt the final victim’s user files.
2.4 CTB_Locker
2.4.1 Overview of CTB_Locker
CTB_Locker ransomware also began to spread in 2014. User files encrypted by CTB_Locker have the same extension, all with a random suffix of 7 letters. A folder of user files encrypted by CTB_Locker ransomware is shown below:
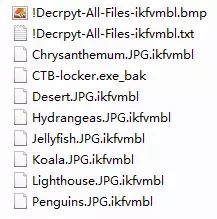
Among them, the last two files are in image and text format to inform users that they have been infected by CTB_Locker ransomware and demand a ransom.
2.4.2 CTB_Locker Encryption Process
The encryption algorithm of CTB_Locker ransomware is relatively complete and complex. Similar to Cerber, this section will describe its complete encryption algorithm in a non-technical manner. Professionals can understand the author’s meaning without delving too deeply.
The encryption algorithms used by CTB_Locker ransomware to encrypt user files are mainly AES and ECDH algorithms. The ECDH algorithm selects the curve25519 curve.
More details about the ECDH algorithm and curve25519 curve can be found on wiki:
ECDH: <click to view the original link>
curve25519: <click to view the original link>
It must be pointed out that ECDH is a key negotiation algorithm, but for non-technical personnel, understanding this algorithm can be challenging. Therefore, the author tentatively compares the ECDH algorithm to the RSA algorithm. Although this analogy is not entirely accurate, it can help us understand ransomware better.
The encryption process of CTB_Locker ransomware can be roughly understood as three layers of encryption. The first layer uses the public key embedded in the sample to encrypt a randomly generated ECDH key:
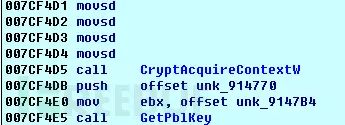
In the image above, PblKey is the randomly generated ECDH key; the second layer’s result encrypts a randomly generated AES key using the randomly generated ECDH key;
The third layer uses the randomly generated AES key to encrypt user files.
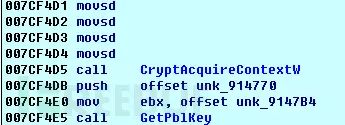
Finally, the encrypted user files and other additional information needed for decryption are overwritten and saved in the user’s files.
2.4.3 CTB_Locker Decryption Process
The normal decryption process of CTB_Locker ransomware cannot obtain its main key. That is, the normal decryption process of CTB_Locker ransomware only includes two layers: first, obtain the random ECDH key-related information from the attacker’s C&C server, and use the ECDH algorithm to obtain the randomly generated AES key; then, use the randomly generated AES key to decrypt the user files.
2.5 Jigsaw
2.5.1 Overview of Jigsaw
Jigsaw ransomware is also a .net hosted ransomware that began to circulate in April 2016. As of the time of writing this chapter, two versions of Jigsaw ransomware have appeared, and the version analyzed in this section is the first version, characterized by encrypted user files having the .fun suffix. A folder encrypted by Jigsaw ransomware is shown below:
In addition, Jigsaw ransomware does not generate any extra files to inform users; it only generates a window displaying the ransom demand and related information.
2.5.2 Jigsaw Encryption Process
Jigsaw ransomware uses the AES algorithm as its encryption algorithm, with its encryption key and initialization vector encoded and stored within the sample:
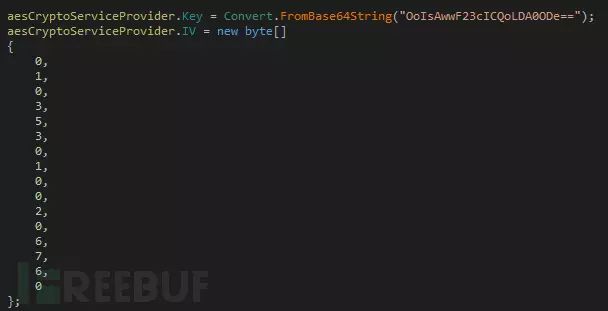
The encryption process of Jigsaw ransomware is straightforward: it first reads the content of the target file, then encrypts it, and finally writes it back to the target file, completing its entire process:
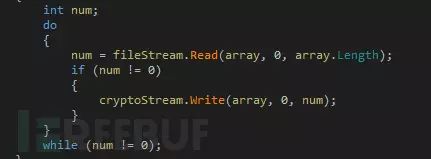
Finally, by adding a file name suffix, the encryption process is completed.
2.5.3 Jigsaw Decryption Process
Jigsaw ransomware carries its own decryption algorithm. When choosing to decrypt, the software first checks if the ransom has been paid. If it has been submitted, it completes the decryption process using the key and initialization vector used during encryption; if the ransom has not been submitted, it continues to count down.
2.6 Locky
2.6.1 Overview of Locky
Locky ransomware is another ransomware that requires requesting a public key from the C&C server. It began to spread in February 2016. Since Locky needs to request a public key from the attacker’s C&C server, and the C&C server was quickly taken down, Locky could not communicate with its C&C server to obtain the key, leading to its inability to continue running.
As of the time of writing this chapter, multiple versions of Locky have appeared, with slight differences among them. Here, an early version of Locky is chosen for analysis, and a folder infected with Locky ransomware is shown below:
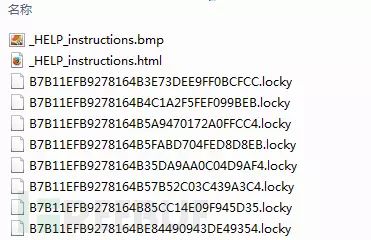
Among them, _HELP_instructions.bmp and _HELP_instructions.html are generated by Locky ransomware to inform users of the infection and demand a ransom.
2.6.2 Locky Encryption Process
Locky ransomware uses RSA and AES as its encryption algorithms. However, the implementation of AES and RSA varies slightly between different samples. In the sample analyzed in this section, the RSA algorithm uses the CryptAPI provided by Microsoft:
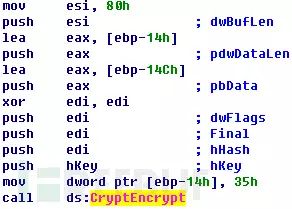
The RSA algorithm is used to encrypt a randomly generated AES key, and the RSA public key is obtained from the attacker’s C&C server when Locky ransomware runs. The AES algorithm is used to encrypt the victim’s user files, primarily implemented by the aesenc instruction, which has high execution efficiency:
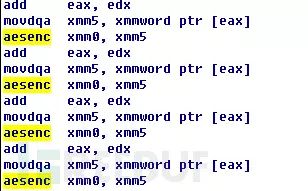
After the encryption is completed, relevant information is written together with the encrypted file content into the user file.
2.6.3 Locky Decryption Process
The decryption algorithm of Locky ransomware is relatively simple. First, it needs to obtain the RSA private key from the attacker’s C&C server to decrypt the AES key, and then use the AES key to complete the decryption of user files. Additionally, it needs to delete the extra retained information in the user files.
2.7 Petya
2.7.1 Overview of Petya
Petya ransomware began to circulate in March 2016. Unlike other ransomware, Petya ransomware does not directly target user files; its main malicious functions can be summarized in two points: first, it destroys the computer’s master boot record, preventing Windows from starting; second, it encrypts the master file table, making files inaccessible. More descriptions of the master boot record and master file table can be found on wiki:
MBR: <click to view the original link>
NTFS MFT: <click to view the original link>
Petya ransomware also has an improved version called Mischa. This section analyzes Petya ransomware. When a computer infected with Petya ransomware starts up, it displays the following content:
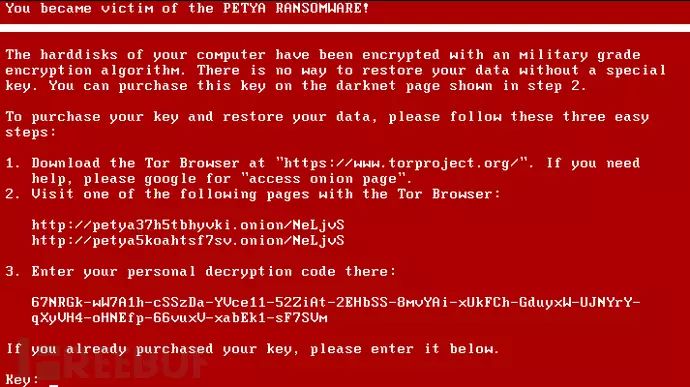
The content mainly informs users that they have been infected by Petya ransomware and demands a ransom.
2.7.2 Petya Encryption Process
The encryption algorithm of Petya ransomware is not complex and can be summarized as ECDH and SALSA20 algorithms. Among them, the ECDH algorithm uses the secp192k1 curve to encrypt the SALSA20 algorithm’s key. More descriptions of the SALSA20 algorithm can be found on wiki:
SALSA20: <click to view the original link>
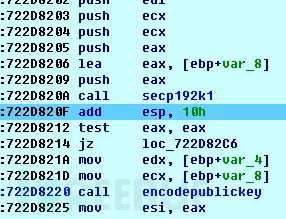
To help more readers understand, this section also compares the ECDH algorithm to the RSA algorithm. Interested readers can continue to study based on this analogy. The image below shows the screenshot of calling secp192k1 to encrypt the randomly generated SALSA20 key:
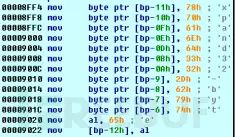
The SALSA20 algorithm is used to encrypt the master file table, and this algorithm runs in a 16-bit environment before the operating system boot, as shown in the screenshot of the boot program calling the SALSA20 algorithm:
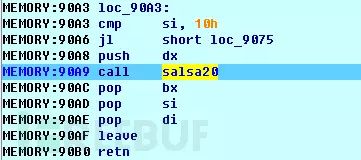
After completing the above encryption steps, the program will display its ransom page and demand payment.
2.7.3 Petya Decryption Process
The decryption algorithm of Petya ransomware consists of a single step: obtaining the SALSA20 key from the attacker’s C&C server and using it to decrypt the master file table, finally restoring the boot sector to normal boot.
2.8 TeslaCrypt
2.8.1 Overview of TeslaCrypt
TeslaCrypt ransomware first appeared in February 2015. As of the time of writing this chapter, TeslaCrypt has a total of four main versions. Different versions of TeslaCrypt encryption samples have different extensions, such as .ecc, .ezz, .zzz, .vvv, .abc, etc. This article selects the fourth version of TeslaCrypt for analysis, which does not change the file name after encryption. A folder infected with TorrentLocker ransomware is shown in the image below:
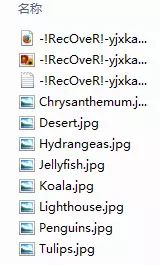
The files -!RecOveR!-yjxka++.Htm, -!RecOveR!-yjxka++.Png, and -!RecOveR!-yjxka++.Txt are used to inform users that they have been interfered with by TeslaCrypt ransomware and demand a ransom.
2.8.2 TeslaCrypt Encryption Process
Different versions of TeslaCrypt ransomware use slightly different encryption algorithms. Similar to CTB_Locker ransomware, the TeslaCrypt version analyzed in this section also uses ECDH and AES, but the ECDH uses the secp256k1 curve.
Again, to make it understandable for more non-technical personnel, this section also compares the ECDH algorithm to the RSA algorithm. Professionals can grasp the general idea here.
Roughly, TeslaCrypt ransomware also adopts a three-layer encryption method. In the first layer, the built-in ECDH public key in the sample encrypts a randomly generated ECDH key. In the second layer, the randomly generated ECDH key encrypts a randomly generated AES key:
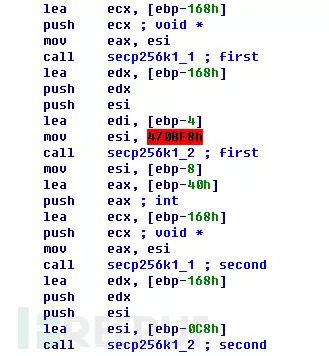
In the third layer, the randomly generated AES key encrypts user files:

After the encryption is completed, TeslaCrypt overwrites the encrypted content into the user file, and the relevant information needed for decryption is also saved within it.
2.8.3 TeslaCrypt Decryption Process
Similar to CTB_Locker ransomware, it is generally impossible to obtain the main key of TeslaCrypt ransomware. Therefore, its decryption process only includes two steps: obtaining the AES key through the ECDH algorithm and then using that AES key to decrypt the user files.
2.9 TorrentLocker
2.9.1 Overview of TorrentLocker
TorrentLocker ransomware began to wreak havoc in 2014. Most versions of TorrentLocker ransomware have the extension .encrypted, but different versions of TorrentLocker have slightly different final encrypted file formats. This chapter selects an early version of TorrentLocker for analysis. In this sample, the user files are encrypted without changing the original file size, which can be used to distinguish this version from other versions of TorrentLocker ransomware.
A folder infected with TorrentLocker ransomware is shown in the image below:
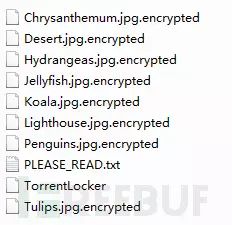
The PLEASE_READ.txt file is automatically generated by TorrentLocker ransomware. After being infected by TorrentLocker, this file is generated in each directory to inform users of the infection and display decryption-related information.
2.9.2 TorrentLocker Encryption Process
TorrentLocker ransomware uses RSA and AES as its encryption algorithms. The RSA algorithm is used to encrypt the AES key, while the AES algorithm is used to encrypt user files. The AES key is randomly generated using the Yarrow algorithm. More details about the Yarrow algorithm can be found on wiki:
Yarrow algorithm: <click to view the original link>
The random process of TorrentLocker involves multiple functions’ return values, as shown in the image below:
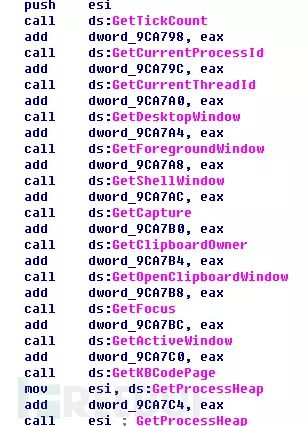
The screenshot content is incomplete, as some functions are not displayed.
The final encrypted user file is shown in the image below:
Each encryption operates on 0x10 bytes until the end.
2.9.3 TorrentLocker Decryption Process
It should be noted that in TorrentLocker samples, all user files are encrypted using the same AES key. During the decryption process, the AES key must be obtained from the attacker’s C&C server, which can then be used to decrypt all user files..
2.10 Unlock92
2.10.1 Overview of Unlock92
Unlock92 ransomware began to spread in June 2016. As of the time of writing this chapter, several versions of Unlock92 ransomware have appeared. This ransomware encrypts user files and adds different extensions, among which the versions with the .CRRRT and .CCCRRRPPP suffixes are more prevalent. Compared to the former, the latter uses a more scientific and rigorous encryption method. This section selects the Unlock92 ransomware with the .CCCRRRPPP suffix for analysis.
Unlock92 is a .net hosted ransomware, and the user folder infected with Unlock92 is shown below:
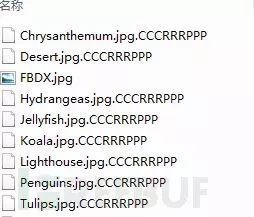
Among them, FBDX.jpg is an automatically generated image file by the ransomware. The name is not fixed, and the image content prompts the user that they have been infected by Unlock92 ransomware.
2.10.2 Unlock92 Encryption Process
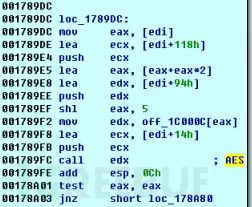
The encryption method used by Unlock92 ransomware is two rounds of RSA algorithm. Each Unlock92 ransomware sample has a built-in RSA public key, as shown in the image below:
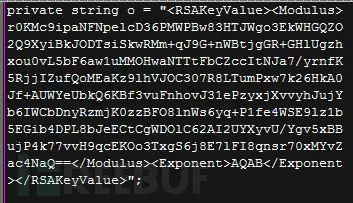
This public key is used to encrypt a randomly generated RSA private key. This randomly generated RSA key pair is used to encrypt all personal files of the user:
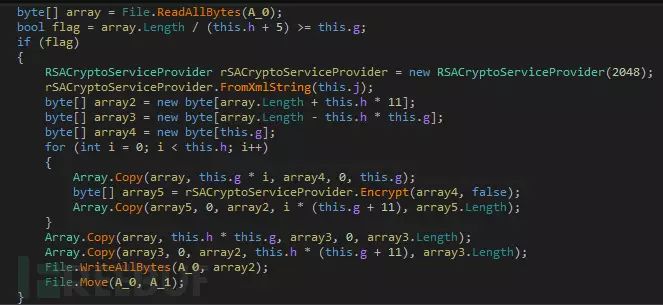
It should be noted that due to the slow execution speed of the RSA algorithm, the authors of Unlock92 did not encrypt all of the user’s files but chose to encrypt only the first 0x300 bytes of each user file.
2.10.3 Unlock92 Decryption Process
Based on the encryption process of Unlock92, it is not difficult to derive its decryption algorithm. First, it is necessary to obtain the private key corresponding to the built-in RSA public key in the sample from the attacker, and then use the obtained private key to decrypt the randomly generated RSA private key. Finally, the decrypted RSA private key can be used to decrypt the user files.
3. Reasons for Decryption
3.1 Summary of Encryption Processes
In the previous text, the encryption processes of various ransomware have been briefly introduced. The main reason for selecting and displaying these 10 ransomware is that they can each represent a certain type of encryption process. These 10 different ransomware encompass 10 different encryption processes. The encryption processes of other ransomware are generally variations of these ten types.
Here is a summary of the various encryption algorithms:
1. Using custom encryption algorithms, such as the ransomware described in Chapter 2.1.
2. Using a single-layer encryption algorithm, as in the ransomware described in Chapter 2.5.
3. Using a two-layer encryption algorithm, such as RSA+AES, as in the ransomware described in Chapter 2.9.
4. Using a three-layer encryption algorithm, such as ECDH+ECDH+AES, as in the ransomware described in Chapter 2.2.
5. Borrowing encryption functions from other normal software, such as: CryptoHost ransomware borrowing WinRAR’s encryption function, Vault ransomware borrowing GnuPG’s encryption function, etc. The author has not analyzed such samples in this article as they are not closely related to the encryption algorithms used by ransomware.
Among all standard encryption and decryption algorithms, the usage rate of the AES algorithm is the highest, followed by RSA, and the ECDH algorithm is also adopted by some ransomware. These standard encryption and decryption algorithms can be considered inherently unbreakable, and the main reason for their breakability is due to improper use, which is also the main reason why ransomware has been decrypted.
3.2 Summary of Decryption Reasons
The main reasons why ransomware has been decrypted do not lie in their encryption algorithms being unscientific, but rather in their improper use of encryption algorithms. Currently, the reasons for the decryption of ransomware can be summarized as follows:
1. Custom algorithms, where the decryption algorithm can be directly derived from the encryption algorithm. The ransomware described in Chapter 2.1 has this issue.
2. Improper key storage methods, such as using a fixed AES key to encrypt user files. The ransomware described in Chapter 2.5 has this issue.
3. Insufficient encryption strength, such as RSA key length being inadequate, allowing it to be factored. Early versions of the ransomware described in Chapter 2.8 had this issue.
4. Poor pseudo-random number generation algorithms, making it possible to predict keys. Early versions of the ransomware described in Chapter 2.10 had this issue.
5. Vulnerabilities in the attacker’s C&C server, allowing keys to be obtained through those vulnerabilities. Early versions of the ransomware described in Chapter 2.2 had this issue.
In addition to the above five points, there are other reasons that can lead to the decryption of ransomware, but since these reasons are not universal (for example, the author of CoinVault ransomware was captured, and TeslaCrypt voluntarily released the keys), they will not be discussed further.
4. Trends and Suggestions
4.1 Trends
According to the author’s understanding, the types and numbers of ransomware are on the rise. Moreover, tools for creating ransomware and the source code of ransomware have begun to be sold on the black market. If effective measures are not taken to curb the growth trend of ransomware, it is difficult to assess how far ransomware will ultimately expand.
However, the anti-ransomware camp is also continuously growing, and various antivirus companies have successively launched software and tools to combat ransomware, and methods to prevent ransomware are constantly being updated and iterated. It is believed that fruitful results will soon be achieved.
4.2 Suggestions
Past ransomware has had various issues regarding the use of encryption and decryption algorithms. However, with the updates to ransomware versions, these issues are becoming less frequent. Once ransomware authors fully master the correct use of these encryption and decryption algorithms, based on current computing capabilities, it can be considered impossible to restore these encrypted files. Therefore, the author suggests that the focus should be on prevention regarding ransomware issues. Regularly back up personal files, and for critical files, additional protective measures should be taken. If infected by ransomware, there is no need to panic, and one should not blindly purchase and pay in Bitcoin; consulting professional personnel can provide more scientific handling methods.
Additionally, tailored defensive measures can be developed based on the main features of ransomware, such as setting up honeypot files. It is believed that through these methods, the spread of ransomware can be effectively curbed.
PS: The author is currently unemployed and welcomes job introductions.
*This article is an original work by: zzz66686, reprinting must indicate the source FreeBuf.COM