
This article is an excellent piece from the KX forum.
KX forum author ID: taobluesky
1
Prepare Environment
2
Initial Exploration
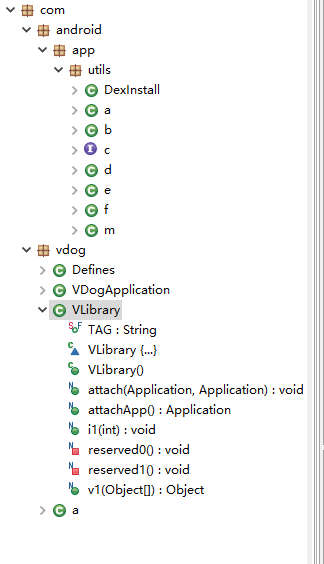 Has anyone encountered the shell of com.vdog.VDogApplication? If you know, please enlighten me on what this shell is! I took a rough look at the Java part of the shell’s code:
Has anyone encountered the shell of com.vdog.VDogApplication? If you know, please enlighten me on what this shell is! I took a rough look at the Java part of the shell’s code: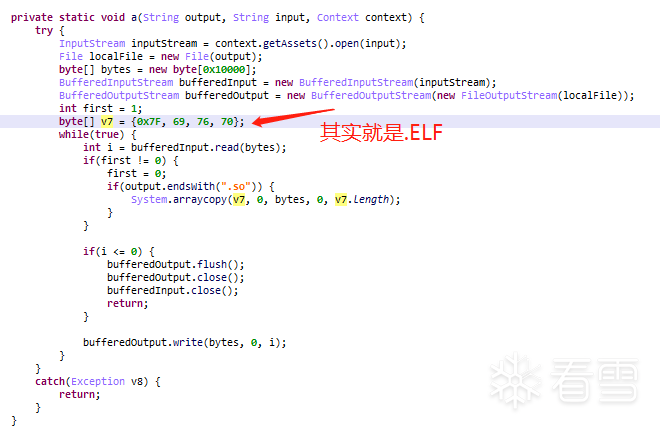
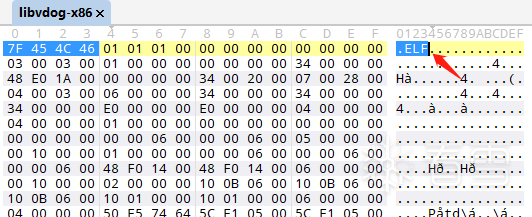
 Then as expected, there was code to detect frida; once spawn or attach, the app’s process immediately terminates.
Then as expected, there was code to detect frida; once spawn or attach, the app’s process immediately terminates.[FRD AL00::com.**.*****]-> Process terminated[FRD AL00::com.**.*****]->
3
Official Start
// okhttp4try { var CertificatePinner = Java.use('okhttp3.CertificatePinner'); CertificatePinner.check.overload('java.lang.String', 'java.util.List').implementation = function(str) { writeFile('! Intercepted okhttp4 in [check()]: ' + str); return; }; try {//.overload('java.lang.String', 'kotlin.jvm.functions.Function0') CertificatePinner.check$okhttp.implementation = function(str, _) { writeFile('! Intercepted okhttp4 in [check$okhttp]: ' + str); return; }; } catch (ex) { writeFile("is this Okhttp3 ?!"); } writeFile('* Setup okhttp4 pinning')} catch (err) { writeFile('* Unable to hook into okhttp4 pinner') writeFile(err);}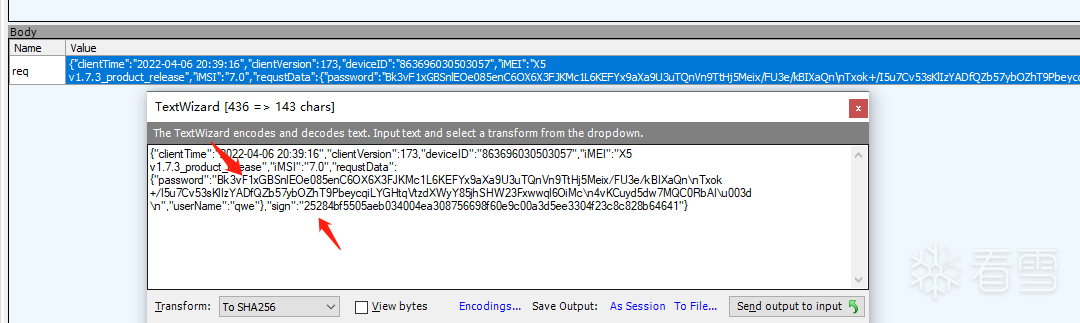 You can see that the password for the login interface is encrypted, along with the sign field. First, look for the key code for password encryption as follows:
You can see that the password for the login interface is encrypted, along with the sign field. First, look for the key code for password encryption as follows: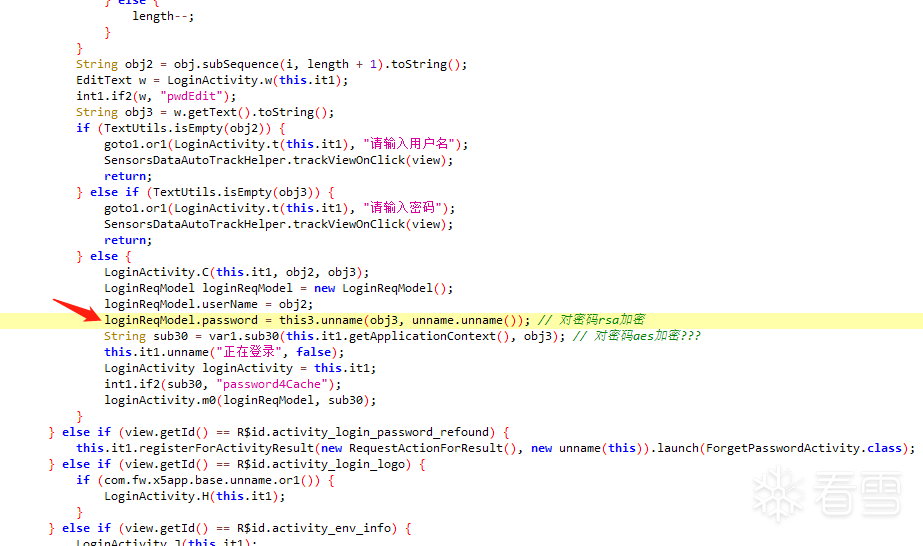 Then follow up:
Then follow up: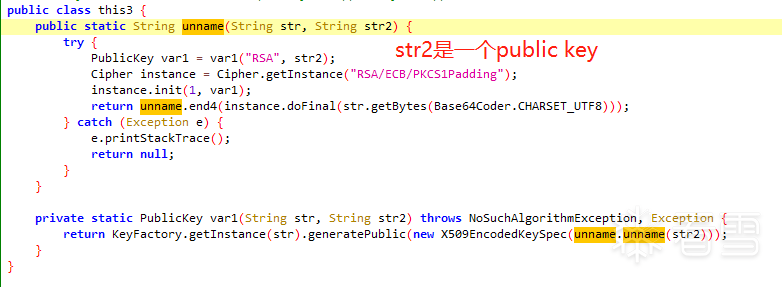 Using RSA to encrypt the password, this unnamed method is a brilliant injection point; here’s the script to obtain the public key:
Using RSA to encrypt the password, this unnamed method is a brilliant injection point; here’s the script to obtain the public key:// Password encryption: output RSA's pubkeyvar this3 = Java.use("com.**.*****.encrypt.this3");this3.unname.implementation = function(str, str2){ writeFile('unname is called'); writeFile("pubkey:" + str2); var ret = this.unname(str, str2); writeFile('unname ret value is ' + ret); return ret;};try { String password = "qed"; String publicKey = "MIGfMA0GCSqGSIb3D********qGWVMv5z6FwIDAQAB"; byte[] decoded = Base64.decode(publicKey, Base64.DEFAULT); RSAPublicKey pubKey = (RSAPublicKey) KeyFactory.getInstance("RSA").generatePublic(new X509EncodedKeySpec(decoded)); Cipher instance = Cipher.getInstance("RSA/ECB/PKCS1Padding"); instance.init(ENCRYPT_MODE, pubKey); String pwdenc = Base64.encodeToString(instance.doFinal(password.getBytes(StandardCharsets.UTF_8)), Base64.DEFAULT); Log.e(TAG, pwdenc); } catch (Exception e) { e.printStackTrace();}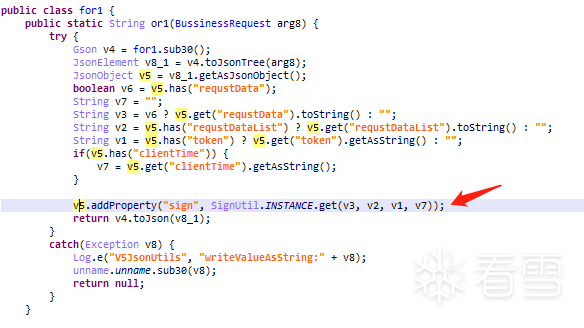 Next, follow into the SignUtil class:
Next, follow into the SignUtil class: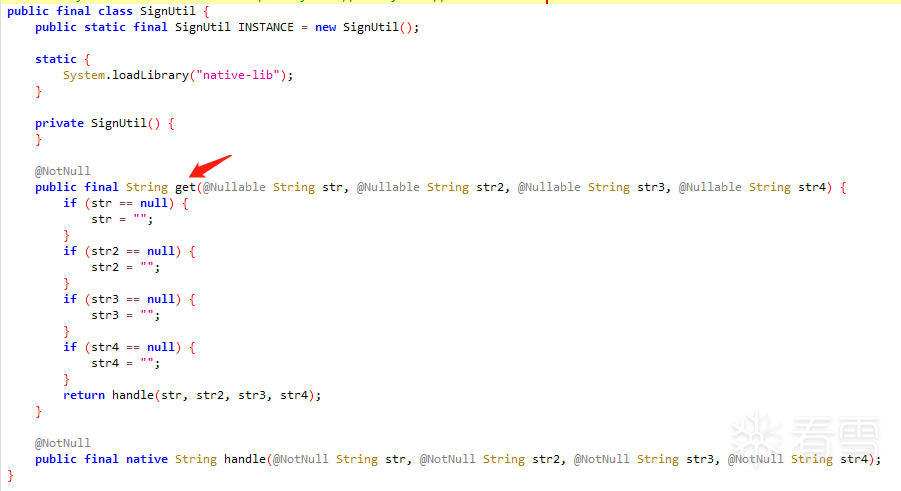 You can see that the key method handle is in native-lib; by hooking the get method, you can obtain the parameters passed for signature verification and the sign result:
You can see that the key method handle is in native-lib; by hooking the get method, you can obtain the parameters passed for signature verification and the sign result:var SignUtil = Java.use("com.**.****.encrypt.SignUtil");SignUtil.get.implementation = function(str, str2, str3, str4){ writeFile('get is called'); writeFile("str:" + str); writeFile("str2:" + str2); writeFile("str3:" + str3); writeFile("str4:" + str4); var ret = this.get(str, str2, str3, str4); writeFile('get ret value is ' + ret); return ret;};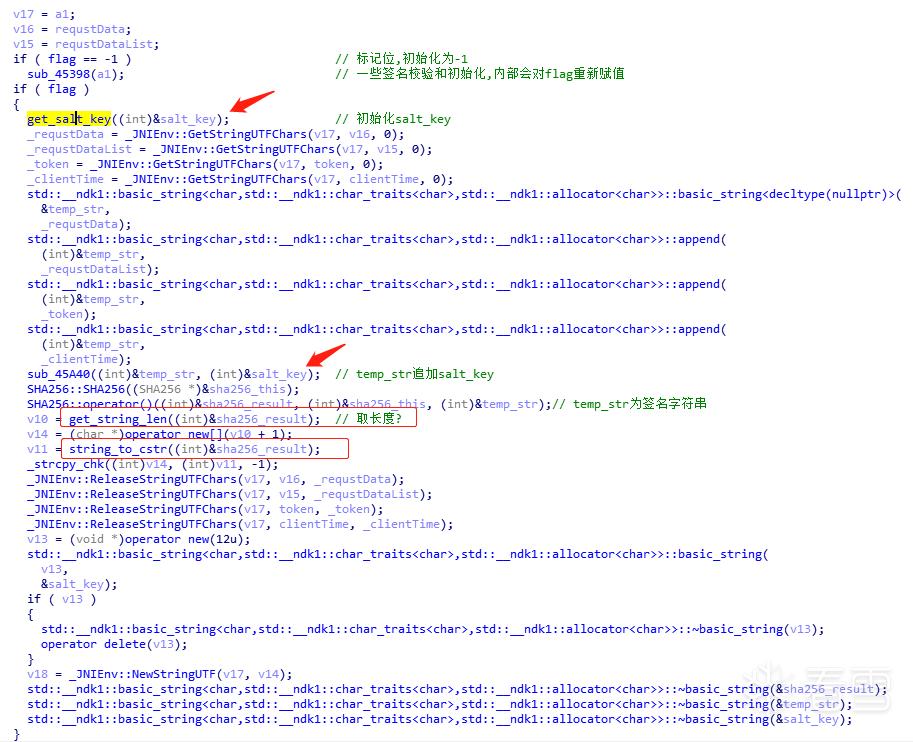 Function sub_45A40:
Function sub_45A40: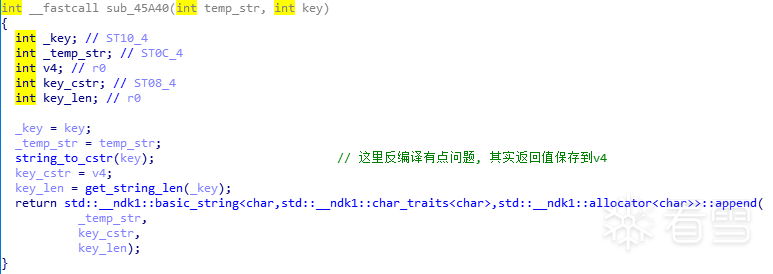 The above figure has annotated the key methods and variables, and the logic is very clear: sign=sha256(_requestData+_requestDataList+_token+_clientTime+salt_key). To verify if the concatenation is correct, you can output temp_str and find a suitable hook point:
The above figure has annotated the key methods and variables, and the logic is very clear: sign=sha256(_requestData+_requestDataList+_token+_clientTime+salt_key). To verify if the concatenation is correct, you can output temp_str and find a suitable hook point: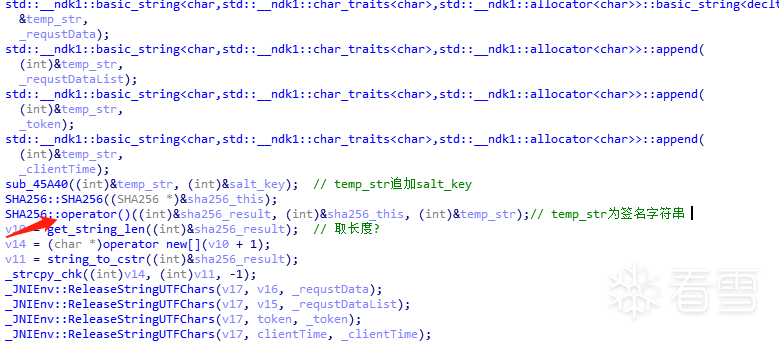 This can be hooked to output; the corresponding asm code is as follows:
This can be hooked to output; the corresponding asm code is as follows: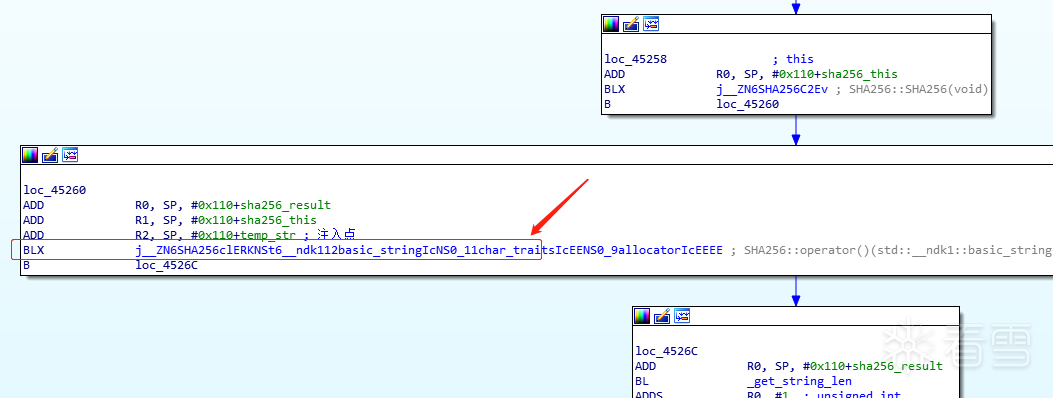 Note that the type of temp_str is std::string; to print output, you need to convert it to cstring. We can use the string_to_cstr function analyzed above for conversion:
Note that the type of temp_str is std::string; to print output, you need to convert it to cstring. We can use the string_to_cstr function analyzed above for conversion: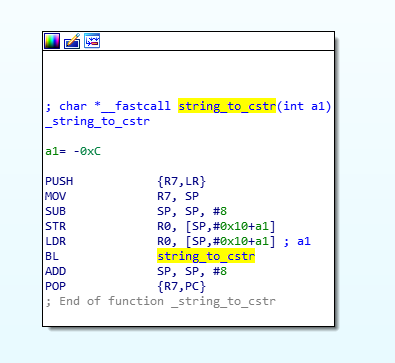 After analysis, let’s write the hook code:
After analysis, let’s write the hook code:var libnative_addr = Module.findBaseAddress("libnative-lib.so")writeFile("libnative_addr is: " + libnative_addr) // Internal std::string to cstring methodvar str_to_c = new NativeFunction(libnative_addr.add(0x45A85), "pointer", ["pointer"]); // Output signature stringtry{ var addr_45266 = libnative_addr.add(0x45267); writeFile("addr_45266: " + addr_45266); Interceptor.attach(addr_45266, { onEnter: function (args) { writeFile("ohwawawa"); var ret = str_to_c(this.context.r2); writeFile("addr_45266 OnEnter sign string:" + Memory.readCString(ret)); }, onLeave: function (retval) { //console.log("retval is :", retval) } });} catch(err) { writeFile("[!!!!!!!!!!!!] " + err);}
KX ID: taobluesky
https://bbs.pediy.com/user-home-65525.htm

# Previous Recommendations
1. CVE-2022-21882 Privilege Escalation Vulnerability Study Notes
2. Wibu Certificate – An Initial Exploration
3. Win10 1909 Reverse Engineering of APIC Interrupts and Experiments
4. Analysis of EAF Mechanism Under EMET and Simulation Implementation
5. SQL Injection Learning Sharing
6. Issues with V8 Array.prototype.concat Function and Their POCs
Share the Ball
Like the Ball
Watch the Ball

Click “Read the Original” for more information!