OpenWrt defaults to using the root account to manage the entire system, and the username information is automatically filled in on the WebUI. However, the home network environment can be quite complex, as the main router assigns public IPv6 addresses to all local network devices.
This is not secure for external access, so we need to harden the SSH configuration and deny external logins.
Configuring a New User
First, SSH into OpenWrt as the root user and execute the command:
opkg install ss vim sudo shadow-useradd shadow-usermod shadow-groupaddThen create a user and configure it (using kane as an example; replace it with the desired username).
groupadd -g 27 sudo
useradd -m -s /bin/ash kane
usermod -a -G sudo kaneNext, configure passwordless sudo permissions for the user.
visudoFind the line starting with %sudo, uncomment it, and modify it to:
%sudo ALL=(ALL:ALL) NOPASSWD: ALLConfiguring Key-Based Login
First, generate a ed25519 formatted key.
ssh-keygen -t ed25519 -C somethingThen paste the information into the OpenWrt management interface under System -> Administration -> SSH-Keys to configure the key for the root user.
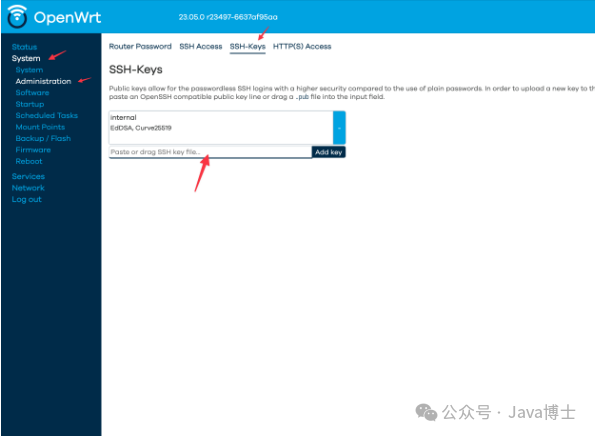
Note: Even if you change the WebUI login user, regardless of the identity used to log in, the key modified here is for the root user’s key, not the login user’s key.
Then change the listening network card to lan to prevent external access, and disable password login for the root user. However, it is still recommended to configure a complex password for the root user.
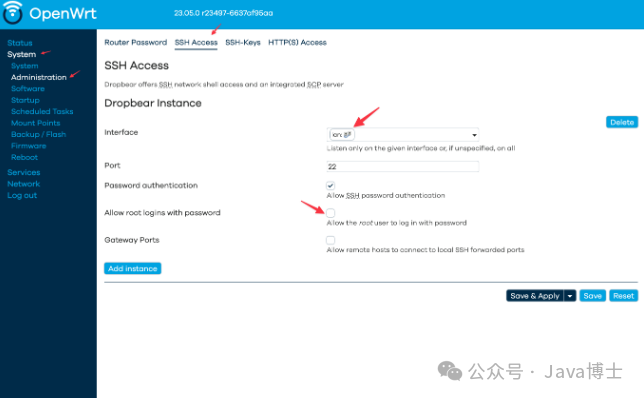
Although OpenWrt is also a Linux distribution, it differs from common distributions in that it uses the Dropbear SSH service instead of OpenSSH. Its key files are located in /etc/dropbear/authorized_keys, and after the above configuration, the public key file can be found in this path.
User Keys
In OpenWrt, the keys for regular users are stored in the normal path, located at ~/.ssh/authorized_keys. Simply copy the public key here.