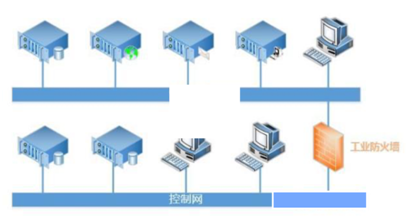
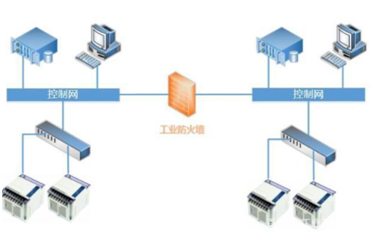
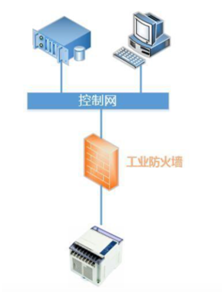
「 4. Performance Requirements of Industrial Firewalls」
The priority order of security goals for industrial control systems primarily considers the availability of all system components, followed by integrity, and confidentiality is usually the last consideration (Figure 4).
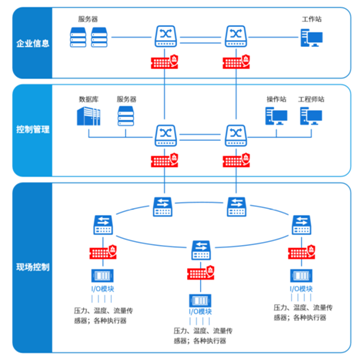
Figure 4: Deployment of Industrial Firewalls
The overall goal of industrial control safety isolation and information exchange products is to resist malicious destruction and attacks on control systems initiated by hackers, viruses, etc., and to prevent failures and damage to industrial equipment caused by information security issues. Specific contents are as follows:
(1) Prevent attacks and intrusions initiated through external boundaries, especially preventing failures of industrial control systems and damage to equipment caused by attacks.
(2) Prevent unauthorized users from accessing the system or illegally obtaining information and performing significant unauthorized operations.
The technical requirements for industrial firewalls are divided into two main categories: security functional requirements and security assurance requirements. Among them, security functional requirements specify the security functions that industrial firewalls should possess, including network layer control, application layer control, and security operation management; security assurance requirements specify the content of development and usage documentation for industrial firewalls. The product security functional requirements mainly stipulate the functions implemented by the product, including network layer control, application layer control, and security operation management.
Due to the unique environments and application scenarios of industrial firewalls, the following requirements must be met during design.
1)Meet the hardware requirements of the industrial environment
The hardware architecture of industrial firewalls needs to meet the requirements of the industrial environment, such as fanless design, wide temperature range (-40~70℃), humidity (5%~95% without condensation), and protection level IP40 (dustproof but not waterproof).
Thus, based on the hardware requirements of the industrial environment, industrial firewalls generally use fanless embedded industrial computers as their carrying platform, and during design, appropriate hardware combination requirements are proposed based on research.
2)Meet the high-speed processing requirements for data packets
Industrial firewalls have predefined rule templates for known protocols and rule templates that are automatically learned and modeled later. Since industrial firewalls process data packets one by one, including packet verification and processing of each layer of the packet header, smaller data packets reach their destination faster, increasing the server’s processing requirements for data packets.
Moreover, the diversity of devices and industrial protocols used in the industrial environment requires industrial firewalls to simultaneously process various industrial protocol messages in parallel within industrial network traffic. Additionally, as time goes on, the number of rules in the rule library continues to increase, all of which require support from firewall processing performance to ensure that the speed of network data transmission and the speed of pattern matching detection meet the real-time requirements of industrial networks.
3)Meet the stability requirements of the industrial environment
From the perspective of meeting the stability requirements of the industrial environment, industrial firewalls need to consider their own stability’s impact on industrial networks from both hardware and software levels.
Industrial firewalls must possess both hardware and software Bypass functionality. In the event of device abnormalities or restarts, the Bypass function will be activated, eliminating concerns about network disconnection due to issues with the industrial firewall itself.
「 5. Industrial Firewall Technologies」
Industrial firewalls are similar in type to general IT firewalls, broadly categorized into packet filtering, stateful packet inspection, and proxy server types.[1].
1)Packet Filtering Technology
Packet filtering technology selects packets at the OSI Layer 3 network layer based on filtering logic set within the system, known as an access control table. By checking each packet’s source address, destination address, port number, protocol status, and other factors, or their combinations, it determines whether to allow the packet through. Packet filtering firewalls based on access control technology can ensure secure communication between different security zones by setting access control rules to manage and control the information flow entering and exiting different security zones, ensuring resources are effectively used and managed within legal bounds.
2)Stateful Packet Inspection Technology
Stateful packet inspection monitors the state of each active connection and decides whether network packets can pass through the firewall based on this information. It intercepts packets at the protocol stack’s lower layer, analyzes them, and compares the current packet’s state information with that of the previous packet to obtain control information for protecting network security.
Stateful inspection does not require rule matching for every packet in a session, only state checks of the packet’s trajectory, which speeds up packet processing. Compared to traditional packet filtering firewall access control rule lists, it offers better performance and security, becoming increasingly prevalent in industrial control applications.
3)Proxy Service Technology
Proxy service technology is introduced to address the shortcomings of packet filtering and application gateway technologies. It divides all network communication links crossing the firewall into two segments. The application layer “links” between internal and external computer systems are established by two terminating proxy servers, allowing external computer network links to reach only the proxy server, thus isolating the internal and external computer systems. Additionally, the proxy service analyzes and logs the packets passing through, generating reports and alerting network administrators upon detecting attack signs while retaining traces of the attack. However, proxy servers may introduce latency, affecting performance.
The above three firewall technologies are relatively traditional; as network security technologies have evolved, firewall technologies are also continuously advancing. Here are some newly developed industrial firewall technologies:
(1) Transparent Access Technology. The primary feature of transparent mode is that it is invisible to users, who are unaware of the firewall’s existence. To achieve transparent mode, the firewall must operate without an IP address, requiring no IP address configuration, and users will not know the firewall’s IP address. When a firewall adopts transparent mode, users do not need to reconfigure or modify routing; the firewall can be directly installed and used in the network like a switch without needing to set an IP address.
(2) Distributed Firewall Technology. Distributed firewalls are responsible for security protection between network boundaries, subnets, and internal nodes, making them a complete system rather than a single product. Depending on the required functions, the distributed firewall architecture includes three parts: ① Network firewall: which can be implemented purely in software or with appropriate hardware support for protection between internal and external networks and between internal subnets; ② Host firewall: for protecting servers and desktops within the network; ③ Central management: responsible for overall security policy planning, management, distribution, and log aggregation. The workflow of distributed firewalls is as follows: first, the central authority that formulates the firewall access control policies converts the policy language description into an internal format to create policy files; then, the center uses system management tools to distribute these policy files to their respective internal hosts, which determine whether to accept the received packets based on both IP security protocol and the server-side policy files.
(3) Intelligent Firewall Technology. The structure of intelligent firewalls consists of internal and external routers, intelligent authentication servers, intelligent hosts, and bastion hosts. Internal and external routers build a secure subnet between the Intranet and Internet, known as a Demilitarized Zone (DMZ). The working principle of intelligent firewalls can be understood as follows: when an Intranet host connects to an Internet host, it uses the same IP address; however, when an Internet host connects to an Intranet host, it must route through a gateway mapped to the Intranet host. This setup keeps the Intranet network invisible to the Internet. At any time, the application filtering management program in the bastion host within the DMZ can communicate confidentially with the intelligent authentication server in the Intranet through a secure tunnel, allowing the intelligent authentication server to modify the routing tables and filtering rules of the internal and external routers through confidential communication. The coordinated operation of the entire firewall system is primarily controlled by specially designed application filtering management programs and intelligent authentication service programs, running on bastion hosts and intelligent servers, respectively.
References
[1] Su Jie, Yuan Junpeng. Firewall Technology and Its Progress. Computer Engineering and Applications, 2004(09): 147-149+160.
[2] Zhang Jian. Network Security for Industrial Control Systems. Beijing: University of Electronic Science and Technology Press, 2017.
[3] Lu Guangming. The Current Situation and Challenges of Industrial Control Security in China. Cyberspace Security, 2018(03).
[4] Stouffer K, Falco J, Scarfone K. Guide to Industrial Control Systems (ICS) Security. NIST Special Publication, 2008: 800-82.
[5] Rafael Ramos Regis Barbosa, Ramin Sadre, Aiko Pras. Exploiting Traffic Periodicity in Industrial Control Networks. International Journal of Critical Infrastructure, 2016.
[6] Security for Industrial Automation and Control Systems: Terminology, Concepts, and Models. ANSI/ISA-99.01.01-2007, 2007.



Scan to Follow Us
“Intelligent Manufacturing Forum”
Inheriting the concept of “advanced manufacturing, manufacturing power,” Tsinghua University Press provides professional knowledge services for everyone!