In automotive electronic diagnostics, secure access (0x27) and communication control (0x28) are two key technologies. The former protects ECU data security, while the latter optimizes communication efficiency. Mastering these is essential for becoming a diagnostic expert!
1. Secure Access (SID 0x27): The ECU’s ‘Password Lock’ Mechanism
-
The ECU stores critical vehicle data (such as program code and calibration parameters). To prevent unauthorized read/write access, it must be unlocked via the secure access service (0x27).Core Logic: Identity verification through a ‘seed-key’ mechanism, similar to a dynamic password verification process.
-
Four-Step Process for Secure Access
-
Request Seed (Challenge): The diagnostic tool sends sub-functions 0x01/03/05/07 (odd values) to request the ECU to generate a random seed.Message Example:
<span>02 27 01 55 55 55 55 55</span>(Request Seed)<span>06 67 01 BB BB BB BB 55</span>(ECU returns seed 0xBBBBBBBB) -
Generate Key: The diagnostic tool uses a predefined algorithm to calculate Key1 based on the seed.Example Algorithm: Seed + Fixed Offset → XOR Operation → Key.
-
Send Key (Response): The diagnostic tool sends sub-functions 0x02/04/06/08 (even values) to submit Key1.Message Example:
<span>06 27 02 CC CC CC CC 55</span>(Send Key1=0xCCCCCCCC) -
ECU Verification: The ECU generates Key2 using the same algorithm. If Key1=Key2, it unlocks; otherwise, it returns an error code.Successful Response:
<span>06 67 02 55 55 55 55 55</span>(Unlock Successful)Failure Response:<span>03 7F 27 35 55 55 55 55</span>(NRC 0x35=Invalid Key)
Key Details
-
Security State Reset: The ECU automatically relocks when rebooted or when switching sessions.
-
Specific Error Codes:
-
<span>0x35</span>: Key Error (most common) -
<span>0x36</span>: Key Attempt Limit Exceeded (to prevent brute force) -
<span>0x37</span>: Key Generation Timeout
2. Communication Control (SID 0x28): ‘Traffic Control’ During Diagnostics
During ECU upgrades or large data transfers, the communication control service (0x28) is required to temporarily disable non-diagnostic communication to avoid bus congestion.
Core Functions
| Sub-function | Name | Function | Applicable Scenarios |
|---|---|---|---|
| 0x00 | Enable Communication | Restore specified message transmission | Restore communication after diagnostics |
| 0x03 | Disable Transmission | Close specified message transmission | Flashing programs / Transmitting large data |
Message Parameter Analysis
-
Message Type Parameter:
-
<span>0x01</span>: Regular application messages (e.g., vehicle speed, RPM, etc. periodic signals) -
<span>0x02</span>: Network management messages (CAN bus management messages)
Practical Examples
-
Disable Regular Communication: The diagnostic tool requests:
<span>03 28 03 01 55 55 55 55</span>(Sub-function 0x03 + Message Type 0x01)ECU responds:<span>02 68 03 55 55 55 55 55</span>(Operation Successful) -
Restore Communication: The diagnostic tool requests:
<span>03 28 00 01 55 55 55 55</span>(Sub-function 0x00 + Message Type 0x01)ECU responds:<span>02 68 00 55 55 55 55 55</span>(Operation Successful)
Common Errors
-
Session Mode Error: Must be used in **Extended Session (0x03), otherwise returns
<span>7F 28 7E</span>(Current session not supported). -
Invalid Sub-function: If an undefined sub-function is sent, returns
<span>7F 28 12</span>(Sub-function not supported).
3. Dynamic Seed Generation and Anti-Brute Force Control Mechanism for UDS Secure Access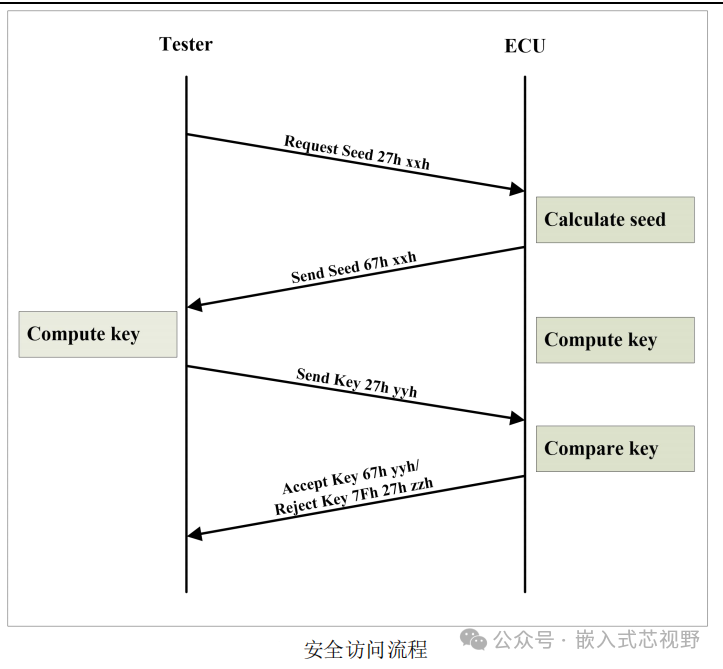
1. Seed Generation Rules
-
Prohibited Values:
-
<span>00000000h</span>: If the ECU is already in an unlocked state, it returns a seed of 0 upon receiving the ‘SecurityAccess-RequestSeed’ request. The tool can determine the ECU’s lock status based on whether the seed is 0. -
<span>FFFFFFFFh</span>: Default value after memory erasure, prohibited as a seed value to prevent potential conflicts.
Randomness Requirement: The seed must be a dynamically generated random number (excluding the above two values)
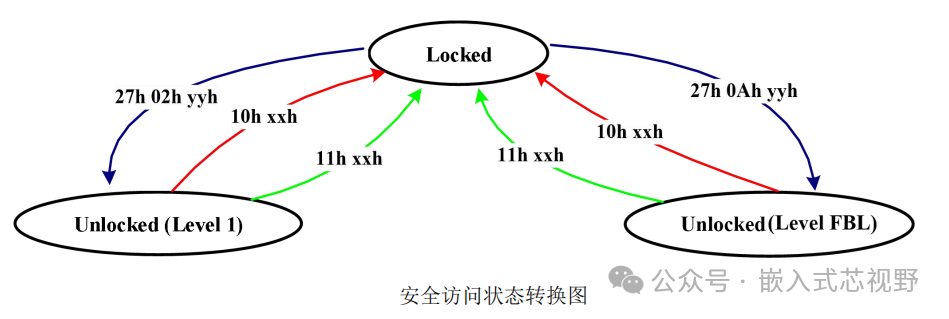
2. Security Level Activation Rules
-
Mutual Exclusivity: Only one security level may be activated at a time (e.g., after unlocking with seed 01h, the permissions associated with the original seed 09h automatically become invalid).
-
No Priority: Security level numbers are assigned arbitrarily, with no high or low permission differences.
3. Conditions for Resetting the Secure Access Process
The seed generation process is forcibly reset and a new random number is generated when the following events occur:
-
The ECU sends a positive or negative response to ‘SecurityAccess-SendKey’;
-
The ECU sends a negative response to ‘SecurityAccess-RequestSeed’;
-
The ECU enters a locked state due to returning to the default session or rebooting.
4. Error Handling and Counter Management
-
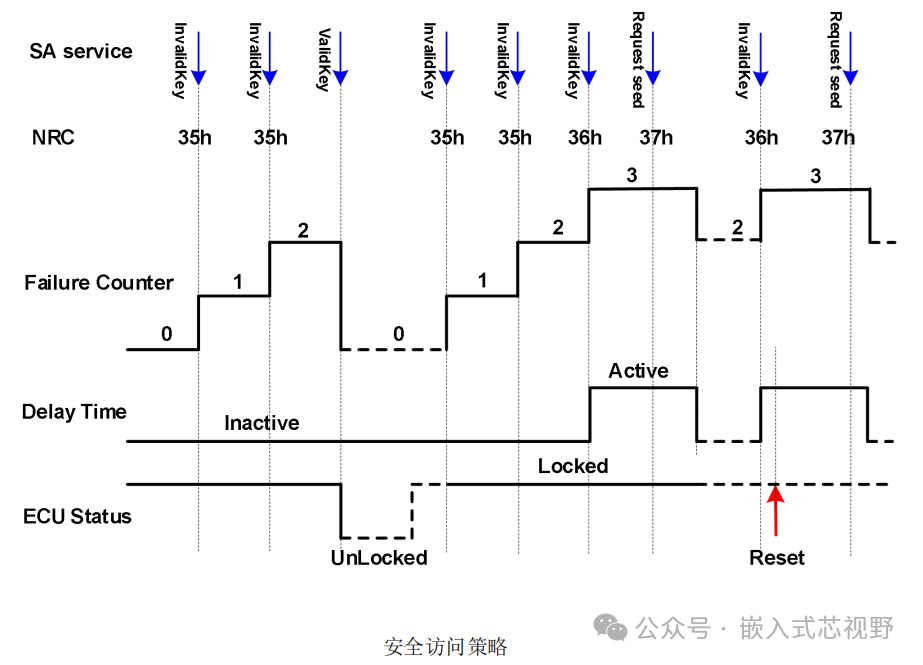
Invalid Key Response:
-
If the key is incorrect, the ECU returns a negative response code
<span>35h</span>(Invalid Key), and the secure access error counter is incremented by 1. -
If ‘RequestSeed’ is sent continuously, the ECU returns the same seed, while the counter is incremented by 1.
-
Locking and Delay Mechanism:
-
When the counter accumulates 3 errors (e.g., 3 invalid keys or 4 consecutive requests for seeds), the ECU returns
<span>36h</span>response, and enforces a 10-second wait before accepting new requests. -
If a request is received during the waiting period, it returns
<span>37h</span>(Delay Not Over), and does not process the request. -
Counter Reset:
-
Any successful unlock (valid key) resets the counter immediately to zero.
-
After waiting 10 seconds, the counter is decremented by 1, allowing another attempt; if it fails again, it re-enters the 10-second wait.
5. Power-Up and Reset Rules
-
Upon power-up or reset, the ECU defaults to locked state.
-
If the counter reached 3 before the reset, the ECU immediately initiates a 10-second delay.
6. Non-Volatile Storage Requirements
-
The secure access error counter must be stored in non-volatile memory, with an initial value of 0, ensuring data is not lost after power failure.