Common Encryption Algorithms Implemented in Python
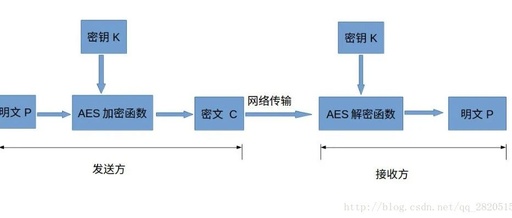
In our daily lives, we often encounter various encryption algorithms. Today, let’s discuss the Python implementations of these encryption algorithms. Most commonly used encryption methods have corresponding Python libraries, so we generally no longer need to implement specific algorithms with code. MD5 Encryption Full name: MD5 Message-Digest Algorithm, a widely used cryptographic hash function that … Read more