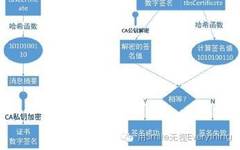
Understanding HTTPS and SSL/TLS Protocols
To clearly explain the implementation principles of the HTTPS protocol, we need to understand at least the following background knowledge. 1. A rough understanding of several basic terms (HTTPS, SSL, TLS) 2. A rough understanding of the relationship between HTTP and TCP (especially “short connection” vs. “long connection”) 3. A rough understanding of the concept … Read more