SAE J3101 Vehicle Hardware Protected Security Standard
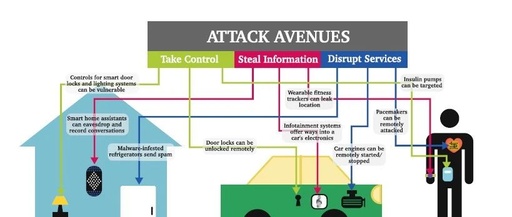
SAE-2020-J3101 “ Hardware Protected Security for Ground Vehicle” is a standard released by the American Automotive Association in 2016 regarding vehicle hardware security, which stipulates the hardware protection security requirements for ground vehicle applications.The hardware here specifically refers to hardware such as HSM. SAE J3101 specifies the requirements for these hardware components. SAE J3101 is … Read more