Author: Shui De
Original: http://blog.csdn.net/jxh_123/article/details/40316081
1. OSI, TCP/IP, and Five-Layer Protocol Architecture
OSI Layers (7 layers): Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, Application Layer.
TCP/IP Layers (4 layers): Network Interface Layer, Internet Layer, Transport Layer, Application Layer.
Five-Layer Protocol (5 layers): Physical Layer, Data Link Layer, Network Layer, Transport Layer, Application Layer.
The function of each layer is as follows:
Physical Layer: Activates, maintains, and deactivates the mechanical, electrical, functional, and procedural characteristics between communication endpoints. This layer provides a physical medium for transmitting data to the upper-layer protocols.Data Link Layer: Provides reliable transmission over unreliable physical media. The functions of this layer include: physical addressing, framing of data, flow control, error detection, retransmission, etc.
Network Layer: Responsible for routing packets between subnets. Additionally, the Network Layer can implement congestion control, internetworking, and other functionalities.
Transport Layer: The first end-to-end layer, i.e., host-to-host. The Transport Layer is responsible for segmenting upper-layer data and providing end-to-end, reliable or unreliable transmission. Furthermore, the Transport Layer must handle end-to-end error control and flow control issues.
Session Layer: Manages the session processes between hosts, i.e., responsible for establishing, managing, and terminating sessions between processes. The Session Layer also uses checkpoints inserted in the data to achieve data synchronization.
Presentation Layer: Transforms upper-layer data or information to ensure that application layer information from one host can be understood by the application program of another host. Data transformations in the Presentation Layer include data encryption, compression, format conversion, etc.
Application Layer: Provides an interface for operating systems or network applications to access network services.
2. Classification of IP Addresses
Class A Address: Starts with 0, first byte range: 0~127;
Class B Address: Starts with 10, first byte range: 128~191;
Class C Address: Starts with 110, first byte range: 192~223;
Class D Address: Starts with 1110, first byte range: 224~239;
3. Working Principle of ARP Protocol
First, each host establishes an ARP table in its ARP buffer to represent the correspondence between IP addresses and MAC addresses. When the source host needs to send a packet to the destination host, it first checks its ARP table for the MAC address corresponding to that IP address. If it exists, the packet is sent directly to that MAC address; if not, it broadcasts an ARP request to the local network segment to query the MAC address corresponding to this destination host. This ARP request packet includes the source host’s IP address, hardware address, and the destination host’s IP address. All hosts in the network receive this ARP request and check whether the destination IP in the packet matches their own IP address. If not, they ignore the packet; if it matches, the host first adds the sender’s MAC and IP address to its ARP table, overriding any existing information if necessary, and then sends an ARP response packet back to the source host, informing it of the MAC address it is looking for. Upon receiving this ARP response packet, the source host adds the destination host’s IP and MAC address to its ARP table and begins data transmission using this information. If the source host does not receive an ARP response packet, it indicates that the ARP query has failed.
4. Routing Devices and Related Layers
Physical Layer: Repeaters (also called amplifiers), hubs.
Data Link Layer: Bridges, switches.
Network Layer: Routers.
Gateway: Devices above the Network Layer.
5. Common Routing Protocols and Their Differences
Common routing protocols include: RIP protocol, OSPF protocol.
RIP protocol: Based on the Bellman-Ford algorithm, it uses hop count as the routing metric, with a maximum of 15 hops; if it exceeds 15 hops, the packet will be discarded.
OSPF protocol: Based on Dijkstra’s algorithm, it is a link-state routing protocol that uses bandwidth and delay as routing metrics.
6. Differences Between TCP and UDP
UDP is a connectionless, unreliable datagram service;
TCP is a connection-oriented, reliable byte stream service.
7. How Does TCP Ensure Reliability?
TCP’s reliability is achieved through sequence numbering and acknowledgment (ACK).
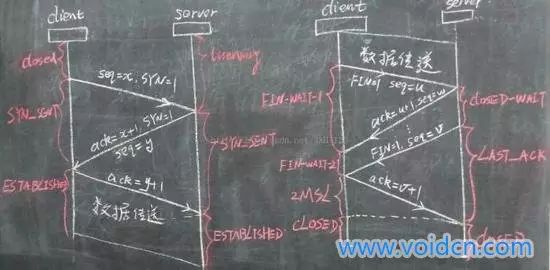
8. The Entire Process of TCP Three-Way Handshake and Four-Way Teardown
9. The Entire Process Executed After Entering www.baidu.com in the Browser
Now assume that if we enter http://www.baidu.com in the client (client) browser, and baidu.com is the server to be accessed, the following is a detailed analysis of the series of protocol operations executed by the client to access the server:
1) The client browser resolves the IP address of www.baidu.com to 220.181.27.48 through DNS, finding the path from the client to the server via this IP address. The client browser initiates an HTTP session to 220.161.27.48, encapsulating data packets through TCP and inputting them into the network layer.
2) In the client’s transport layer, the HTTP session request is segmented into message segments, adding source and destination ports. For instance, if the server listens on port 80 for client requests, the client randomly selects a port like 5000 for exchange, and the server returns the corresponding request to the client’s 5000 port. The destination is then determined using the IP layer’s IP address.
3) The client’s network layer does not concern itself with application or transport layer details; its main job is to find out how to reach the server by looking up the routing table, which may involve passing through multiple routers, a task handled by the routers themselves, so I won’t elaborate further. Essentially, it determines the path to the server by consulting the routing table.
4) In the client’s link layer, the packet is sent to the router through the link layer, using neighbor protocols to find the MAC address for the given IP address, and then sending an ARP request to find the destination address. If a response is received, the IP data packet can now be transmitted using the ARP request-response exchange, and then the IP data packet is sent to the server’s address.
10. What Requests Does the HTTP Protocol Include?
GET: Requests to read information indicated by the URL.
POST: Adds information to the server (such as comments).
PUT: Stores a document at the given URL.
DELETE: Deletes the resource indicated by the given URL.
11. Differences Between POST and GET in HTTP
(1) GET retrieves data from the server, while POST sends data to the server.
(2) GET appends parameter data to the URL specified in the Action attribute of the submitted form, with values corresponding to each field in the form, which can be seen in the URL.
(3) GET has a small amount of data that cannot exceed 2KB; POST can transmit a larger amount of data, generally considered to have no limit.
(4) According to HTTP specifications, GET is used for information retrieval and should be safe and idempotent.
I. The term safe means that the operation is intended for information retrieval rather than modification. In other words, GET requests should generally not have side effects; they merely retrieve resource information, similar to a database query, without modifying or adding data or affecting the state of the resource.
II. Idempotent means that multiple requests to the same URL should return the same result.
12. Protocol Corresponding to Each Layer in TCP/IP
Network Layer: IP protocol, ICMP protocol, ARP protocol, RARP protocol.
Transport Layer: UDP protocol, TCP protocol.
Application Layer: FTP (File Transfer Protocol), Telnet (Remote Login Protocol), DNS (Domain Name System), SMTP (Simple Mail Transfer Protocol), POP3 protocol (Post Office Protocol), HTTP protocol.
13. Protocols Corresponding to TCP and UDP
Protocols corresponding to TCP:
(1) FTP: Defines the File Transfer Protocol, using port 21. When someone says a computer has FTP service running, it means the file transfer service has been initiated. Downloading files and uploading homepages both require FTP service.
(2) Telnet: It is a port used for remote login, allowing users to connect to a computer remotely using their own identity. This port provides a communication service based on DOS mode. For example, older BBS systems were purely character interfaces, and servers supporting BBS opened port 23 to provide services.
(3) SMTP: Defines the Simple Mail Transfer Protocol, which is used by many mail servers for sending emails. For instance, common free email services use this mail service port, which is why you often see SMTP port settings in email configurations, with the server opening port 25.
(4) POP3: Corresponding to SMTP, POP3 is used for receiving emails. Generally, the POP3 protocol uses port 110. This means that if you have the appropriate program using the POP3 protocol (like Foxmail or Outlook), you can receive emails directly without logging into the web interface of your mailbox (for instance, with a 163 mailbox, there is no need to first enter the NetEase website and then access your mailbox to check for new messages).
(5) HTTP protocol: The protocol for transmitting hypertext from a web server to a local browser.
Protocols corresponding to UDP:
(1) DNS: Used for domain name resolution services, converting domain addresses to IP addresses. DNS uses port 53.
(2) SNMP: Simple Network Management Protocol, which uses port 161 and is used to manage network devices. Due to the large number of network devices, connectionless services show their advantages.
(3) TFTP (Trivial File Transfer Protocol), a simple file transfer protocol, which uses UDP service on the well-known port 69.
14. Special IP Addresses
(1) Network Address
An IP address consists of a network number (including subnet number) and a host number, with the host number of the network address being all 0, representing the entire network.
(2) Broadcast Address
The broadcast address is usually referred to as the direct broadcast address, to distinguish it from the limited broadcast address.
The host number of the broadcast address is all 1. When a message is sent to the broadcast address of a network, all hosts in that network can receive the broadcast message.
(3) Multicast Address
Class D addresses are multicast addresses.
Recall the A, B, C, and D class addresses.
Class A addresses start with 00, with the first byte as the network number, and the address range is: 0.0.0.0~127.255.255.255;
Class B addresses start with 10, with the first two bytes as the network number, and the address range is: 128.0.0.0~191.255.255.255;
Class C addresses start with 110, with the first three bytes as the network number, and the address range is: 192.0.0.0~223.255.255.255.
Class D addresses start with 1110, with the address range of 224.0.0.0~239.255.255.255, which are used as multicast addresses (one-to-many communication);
Class E addresses start with 1111, with the address range of 240.0.0.0~255.255.255.255, which are reserved addresses for future use.
Notice: Only classes A, B, and C differentiate between network and host numbers, while classes D and E do not have such a distinction.
(4) 255.255.255.255
This IP address refers to the limited broadcast address. The limited broadcast address differs from the general broadcast address (direct broadcast address) in that it can only be used within the local network, and routers will not forward packets addressed to the limited broadcast address. In contrast, general broadcast addresses can be broadcast locally and across segments. For example, packets sent to the direct broadcast address of host 192.168.1.1/30 can also be received by another segment 192.168.1.5/30; however, if limited broadcast packets are sent, they cannot be received.
Notice: General broadcast addresses (direct broadcast addresses) can be forwarded by some routers (though not all), while limited broadcast addresses cannot be forwarded by routers.
(5) 0.0.0.0
Commonly used to find one’s own IP address, such as in RARP, BOOTP, and DHCP protocols, where an unknown IP address machine wants to know its own IP address. It sends an IP request packet to the local range (specifically, the range blocked by various routers) using the destination address 255.255.255.255.
(6) Loopback Address
127.0.0.0/8 is used as a loopback address, representing the local machine’s address, commonly used for testing the local machine, with 127.0.0.1 being the most used.
(7) Class A, B, C Private Addresses
Private addresses (also called reserved addresses) are not used globally and have local significance.
Class A Private Address: 10.0.0.0/8, range: 10.0.0.0~10.255.255.255
Class B Private Address: 172.16.0.0/12, range: 172.16.0.0~172.31.255.255
Class C Private Address: 192.168.0.0/16, range: 192.168.0.0~192.168.255.255
15. The Role of NAT Protocol, DHCP Protocol, and DNS Protocol
NAT Protocol: Network Address Translation (NAT) is a technology for accessing Wide Area Networks (WAN). It is a conversion technology that translates private (reserved) addresses into legal IP addresses. It is widely used in various types of Internet access methods and networks. The reason is simple: NAT not only perfectly solves the problem of insufficient IP addresses but also effectively avoids attacks from outside the network, hiding and protecting internal computers.
DHCP Protocol: Dynamic Host Configuration Protocol (DHCP) is a network protocol used in local area networks, working with UDP protocol. It has two main purposes: to automatically assign IP addresses to internal networks or network service providers, and to serve as a central management tool for users or internal network administrators for all computers.
DNS Protocol: DNS stands for Domain Name System, a core service of the Internet. It is a distributed database that can map domain names to IP addresses, making it easier for people to access the Internet without having to remember numbers that can be directly read by machines.
Communication and sharing, thank you for your support!

<If you think this article is good and has helped your learning, please scan the QR code to support the operation of this public account> 