
1. Ping Command
The ping command is a frequently used utility primarily used to determine network connectivity. It is useful for determining whether the network is properly connected and the status of the network connection. Simply put, ping is a testing program. If ping runs successfully, it generally rules out faults in the network access layer, network interface card, modem input/output lines, cables, and routers, thereby narrowing down the problem.
The ping command can display the time taken for a request to be sent and a response to be received in milliseconds. If the response time is short, it indicates that the datagram does not have to pass through too many routers or networks, suggesting a faster connection. Ping can also display the TTL (Time To Live) value, which can be used to infer how many routers the data packet has passed through.
1. Command Format
ping hostname
ping domain
ping IP address
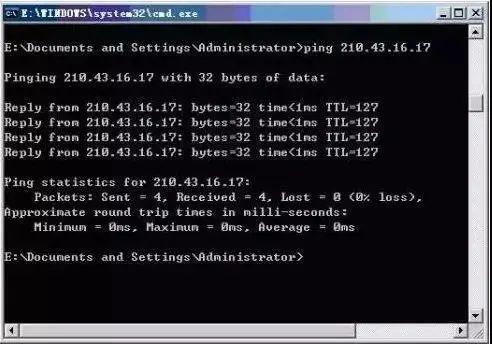
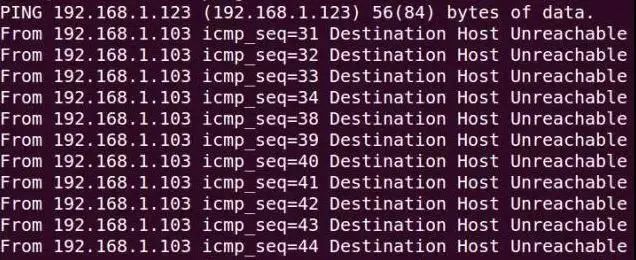
As shown in the figure, the ping command checks the connectivity to the computer with IP address 210.43.16.17, which is connected normally. Four test data packets were sent, and all four packets were successfully received.
2. Basic Applications of the Ping Command
Generally, users can use a series of ping commands to locate where the problem lies or to verify the status of network operation. Below is a typical detection sequence and corresponding possible faults:
① ping 127.0.0.1
If the test is successful, it indicates that the network interface card, TCP/IP protocol installation, IP address, and subnet mask settings are normal. If the test fails, it indicates that there is a problem with the installation or settings of TCP/IP.
② ping local IP address
If the test fails, it indicates that there is an issue with the local configuration or installation; testing and checking the network devices and communication medium should be performed.
③ ping other IPs in the local area network
If the test is successful, it indicates that the network interface card and carrier in the local network are functioning correctly. However, if no response is received, it indicates that the subnet mask is incorrect, the network interface card is misconfigured, or there is an issue with the cabling system.
④ ping gateway IP
If this command responds correctly, it indicates that the gateway router in the local area network is operational and can respond.
⑤ ping remote IP
If a correct response is received, it indicates that the default gateway has been successfully used. For dial-up Internet users, it indicates successful access to the Internet (but does not rule out issues with the ISP’s DNS).
⑥ ping localhost
Localhost is the reserved name for the system’s network; it is an alias for 127.0.0.1, and every computer should be able to resolve this name to the address. Otherwise, it indicates a problem with the hosts file (/Windows/hosts).
⑦ ping www.yahoo.com (a well-known website domain)
Executing the ping command on this domain requires the computer to first resolve the domain name to an IP address, usually via a DNS server. If there is a failure here, it indicates that the IP address configuration of the local DNS server is incorrect, or that the DNS server being accessed has failed.
If all the ping commands listed above run normally, then local and remote communication for the computer is generally fine. However, the success of these commands does not indicate that all network configurations are without issues; for example, some incorrectly configured subnet masks may not be detectable by these methods.
3. Common Parameters and Options for the Ping Command
ping IP -t: Continuously ping the IP address until interrupted by the user with Ctrl C.
ping IP -l 2000: Specify a particular data length in the ping command (here 2000 bytes) instead of the default 32 bytes.
ping IP -n 20: Execute the ping command a specified number of times (here 20).
2. Ipconfig Command
The ipconfig utility can be used to display the current TCP/IP configuration settings. This information is generally used to verify whether manually configured TCP/IP settings are correct.
Furthermore, if the computer and the local area network are using the Dynamic Host Configuration Protocol (DHCP), using the ipconfig command can help determine if your computer has successfully rented an IP address. If it has been rented, you can find out what address it currently has, including IP address, subnet mask, and default gateway network configuration information.
Below are the most commonly used options:
1. ipconfig
When using the ipconfig command without any parameters, it displays the IP address, subnet mask, and default gateway values for each configured interface.
2. ipconfig /all
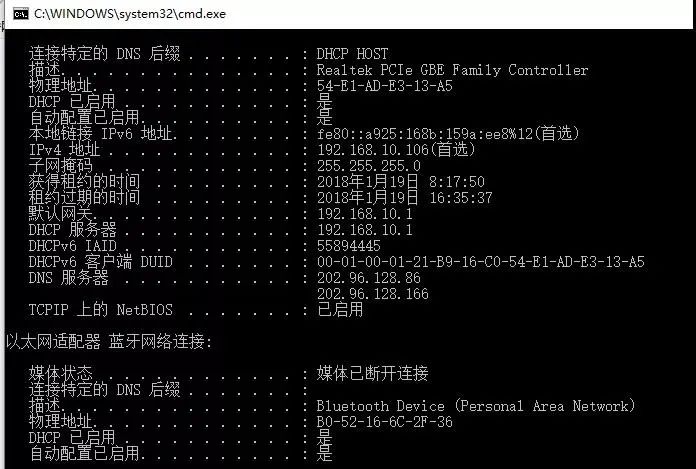
When using the /all option, ipconfig can display additional information for DNS and WINS servers that it has configured and all used information, as well as the physical address (MAC) built into the local network interface card. If the IP address is rented from a DHCP server, ipconfig will show the IP address assigned by the DHCP server and the expected expiration date of the rented address. The figure shows the result window of running the ipconfig /all command.
3. ipconfig /release and ipconfig /renew
These two additional options can only be used on computers that have rented IP addresses from a DHCP server. If you enter ipconfig /release, all rented IP addresses for all interfaces are returned to the DHCP server (the IP address is returned). If the user enters ipconfig /renew, the local computer attempts to contact the DHCP server and rent an IP address. In most cases, the network interface card will be reassigned the same IP address as before.
3. Arp Command (Address Resolution Protocol)
The ARP is an important protocol in the TCP/IP protocol suite used to determine the physical address of the network card corresponding to an IP address.
Using the arp command, you can view the current contents of the ARP cache on the local computer or another computer. Additionally, the arp command can be used to manually set static pairs of physical addresses/IP addresses, which can help reduce the amount of information on the network for commonly used hosts such as the default gateway and local servers.
By default, the entries in the ARP cache are dynamic; whenever data is sent to a specified location, and the current entry does not exist in the cache, ARP will automatically add that entry.
Common Command Options:
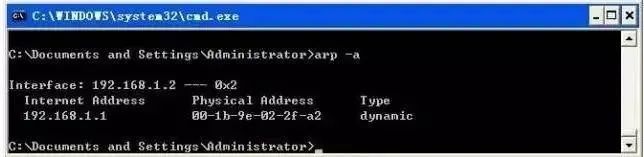
① arp -a: Used to view all entries in the cache.
② arp -a IP: If there are multiple network cards, using arp -a followed by the interface’s IP address will display only the ARP cache entries associated with that interface.
③ arp -s IP physical_address: Manually input a static entry into the ARP cache. This entry will remain valid during the computer’s boot process, or in case of an error, the manually configured physical address will automatically update that entry.
④ arp -d IP: This command can be used to manually delete a static entry.
4. Traceroute Command
Mastering the use of the traceroute command to measure routing is essential for displaying the path that packets take to reach the destination host. The basic usage of the traceroute command is to type “tracert host_name” or “tracert ip_address” at the command prompt, where tracert is the name of the traceroute command in Windows operating systems.
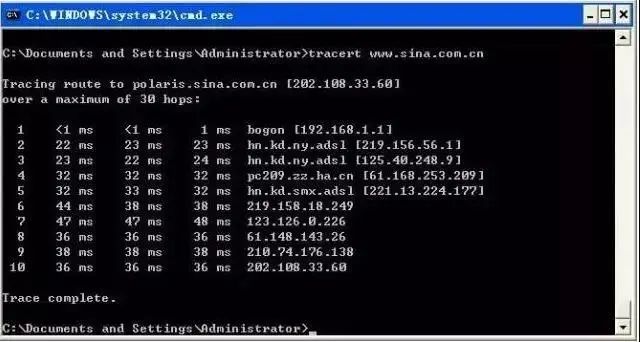
Output has 5 columns
The first column describes the nth hop along the path, which is the router sequence number;
The second column is the first round-trip time;
The third column is the second round-trip time;
The fourth column is the third round-trip time;
The fifth column is the name of the router and its input port’s IP address.
If the source receives fewer than 3 packets from any given router (due to packet loss in the network), traceroute will place an asterisk after that router number and report fewer than 3 round-trip times to that router.
Additionally, the tracert command can also be used to view the steps taken or the route taken to connect to a network site; if there is a network failure, this command can help locate where the problem occurred.
Considerations:
[Testing Routing for Large Networks]:
(1) Try the “ping www.sina.com.cn” operation several times and compare the IP addresses obtained for Sina. If the two pings yield different IP addresses, consider the reasons (such as load balancing). Then, for these different IP addresses, execute the “tracert ip_address” command and observe if there are differences in the output results.
(2) For a site in a large network, conduct a traceroute test and record the results. Observe whether the nth hop has a delay less than the n-1 hop. Try to analyze the reasons (hint: consider the role of each component of delay in total delay).
(3) At different times of the day, use the traceroute program multiple times to test the route from a fixed host to a remote fixed IP address. Analyze and compare the measurement data to observe if the route changes? If so, how frequent is that change?
5. Route Command
Most hosts are generally located on a subnet connected to only one router. Since there is only one router, there is no need to choose which router to send packets to the remote computer; the router’s IP address can serve as the default gateway for all computers on that subnet.
However, when there are two or more routers on the network, users may not want to rely solely on the default gateway. They may want certain remote IP addresses to be routed through a specific router, while other remote IPs are routed through another router. In this case, users need corresponding routing information, which is stored in the routing table. Each host and router has its own unique routing table. Most routers use specialized routing protocols to exchange and dynamically update routing tables between routers. However, in some cases, it is necessary to manually add entries to the routing tables on routers and hosts. The route command is used to display, manually add, and modify routing table entries. This command can be used with the following options:
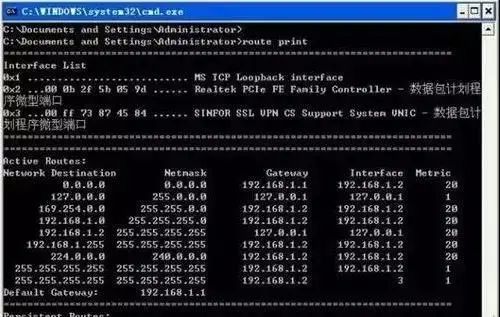
1. route print
This command is used to display the current entries in the routing table, as shown in the output for a single router subnet.
2. route add
Using this command, you can add routing entries to the routing table.
For example, if you want to set a route to the destination network 209.99.32.33, which must pass through 5 router subnets, first passing through a local router with an IP of 202.96.123.5 and a subnet mask of 255.255.255.224, then the user should enter the following command:
route add 209.99.32.33 mask 255.255.255.224 202.96.123.5 metric 5
3. route change
This command can be used to modify the data transmission route; however, users cannot use this command to change the destination of the data. The following example changes the previous route to use a path that includes 3 subnets:
route add 209.99.32.33 mask 255.255.255.224 202.96.123.250 metric 3
4. route delete
This command can be used to delete a route from the routing table. For example: route delete 209.99.32.33
6. Nslookup Command
The nslookup command is used to query the IP address of any machine and its corresponding domain name. It typically requires a domain name server to provide the domain name. If the user has configured a domain name server, they can use this command to view the IP addresses corresponding to different hosts.
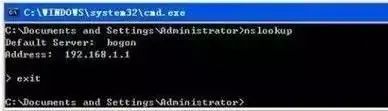
1. Use the nslookup command on the local machine to view the local IP and domain server address.
Simply type the command, and the system returns the server name (fully qualified domain name) and IP address of the local machine, entering an operation command line state with “>” as the prompt; typing “?” queries detailed command parameters; to exit, type exit.
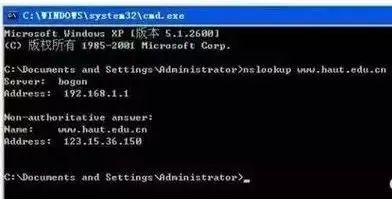
2. View the IP of www.haut.edu.cn
Type the IP address or domain name you want to query at the prompt and press enter.
7. Nbtstat Command
Using the nbtstat command, you can view some information about the network configuration on the computer. This command can also be used to find some private information on other computers. If you want to view the network information on your computer, you can run nbtstat -n to get your workgroup, computer name, and network interface address, etc.; to view the status of other computers on the network, run nbtstat -a *.*.*.*, replacing *.*.*.* with the IP address to return some information about that host.
8. Netstat Command
Learn to use the netstat command to understand the current state of the network.
The netstat command can display active TCP connections, listening ports on the computer, Ethernet statistics, IP routing tables, IPv4 statistics (for IP, ICMP, TCP, and UDP protocols), and IPv6 statistics (for IPv6, ICMPv6, TCP, and UDP protocols). When used without parameters, netstat displays active TCP connections.
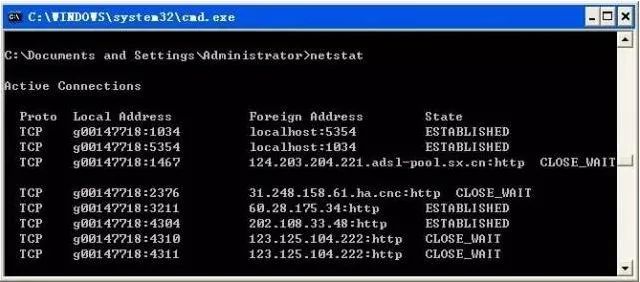
Below are some common options for netstat:
① netstat -a: The -a option displays a list of all valid connection information, including established connections (ESTABLISHED) as well as those connections that are listening for connection requests (LISTENING).
② netstat -n: Lists IP addresses in dotted decimal format instead of symbolic hostnames and network names.
③ netstat -e: The -e option displays statistics about Ethernet. It lists items including the total number of bytes sent, error count, dropped packets, number of packets, and broadcast count. This statistical data includes both the number of packets sent and received. This option can be used to gather some basic network traffic statistics.
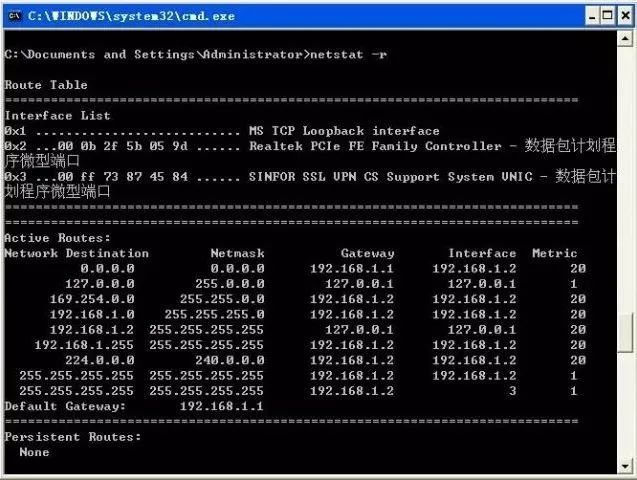
④ netstat -r: The -r option can display information about the routing table, similar to the information seen when using the route print command. In addition to displaying valid routes, it also shows currently valid connections.
The image above shows a routing table, where: Network Destination indicates the destination network, 0.0.0.0 indicates an unknown network, which is automatically generated by the system after setting the default gateway; 127.0.0.0 indicates the local network address used for testing; 224.0.0.0 indicates multicast addresses; 255.255.255.255 indicates limited broadcast addresses; Netmask indicates the network mask, Gateway indicates the gateway, Interface indicates the interface address, Metric indicates the number of routing hops.
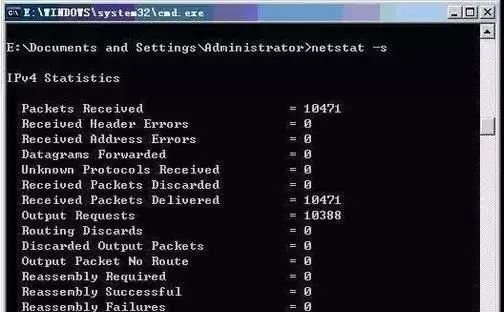
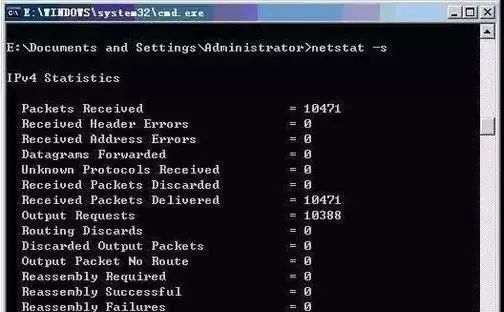
⑤ netstat -s: The -s option can display statistics by protocol. This way, you can see what connections exist on the current computer on the network, as well as detailed information on packet sending and receiving, etc. If applications (such as web browsers) are running slowly or unable to display web pages, this option can be used to check the displayed information. Carefully examine the statistics for errors to identify the problem.
9. Net Command
Understand the functions of the Net service and learn to use Net service commands to solve network-related issues.
Type net help command at the command line to get syntax help for the net command. For example, to get help information about the net accounts command, you can type “net help accounts”.
All net commands can use /y and /n command line options. For example, the net stop server command prompts the user to confirm stopping all dependent server services; net stop server /y confirms stopping and closing the server service.
The table below lists the basic NET commands and their functions:
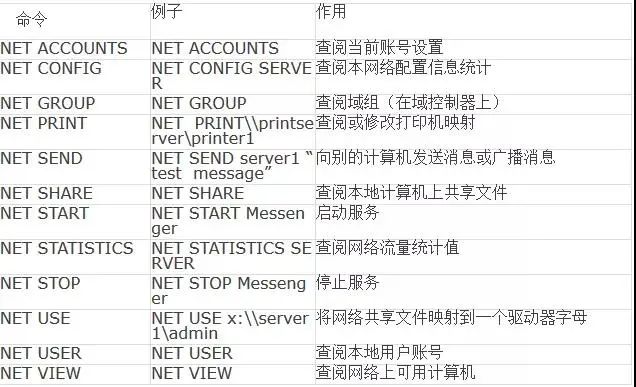
The execution results of the NET commands are similar to those obtained from other Windows Server 2003 management tools. However, the NET command can provide all information in one place and can redirect the results to a printer or a standard text file.
Many network commands used by services begin with net, and these net commands share some common properties. To see a list of all available net commands, you can type net /? in the command prompt window.
(Content Source: e安在线)

What Everyone is Watching
▶️[Association Activities] Experts Discuss | 2020 Changsha Cyber Security and Smart Manufacturing Conference Successfully Held
▶️[Association Activities] The 2020 Work Meeting of the Expert Consultation Committee of Our Association Successfully Concluded
▶️[Association Activities2020 Cyber Security “Golden Autumn Cup” Badminton Invitation Tournament Successfully Held
▶️[Association Activities]Our Association’s Forum on Cyber Data Security in Changde City Concluded Successfully
▶️[Association Activities]2020 Hunan Province Financial Industry Cyber Security Skills Competition Successfully Held
▶️[Association ActivitiesContent Rich, Multi-faceted – Summary of the Association’s “2020 National Cyber Security Awareness Week” Activities
▶️[Association Activities] Our Association’s Open Course “Practical Testing of Network Protection System Effectiveness” Creative Record
▶️[Security Circle]Is There an “Eye” in the Window: Can My 100x Zoom Phone Be Used for Theft and Peeping?
▶️[Security Circle]Experience Sharing from Practical Offense and Defense Drills in Small and Medium-sized Banks
▶️[Security Circle]Top 10 Chinese Hackers, Who Do You Think is the Most Successful?
▶️[Compliance]Essentials | Practical Compliance in the Medical Industry
▶️[Compliance]The Significance of Offense and Defense Drills for Level Protection
▶️[Compliance]Bank of Communications and China Merchants Bank Fined 1 Million Each: Failure to Safeguard Client Personal Information
▶️[Compliance]Level Protection 2.0 | Detailed Explanation of Security Devices Required for Level 2 and 3 Systems and Common Issues
▶️[Compliance]Key Points | Level Protection 2.0 “Must-Know Questions”
▶️[Compliance]Level Protection 2.0 System Classification Guidelines
▶️[Compliance]Summary of Issues of Concern for Enterprises in Level Protection 2.0
