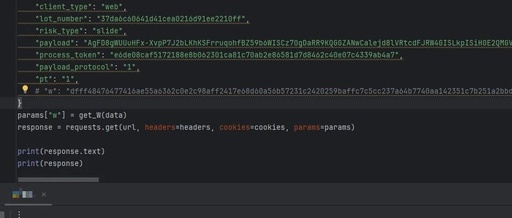
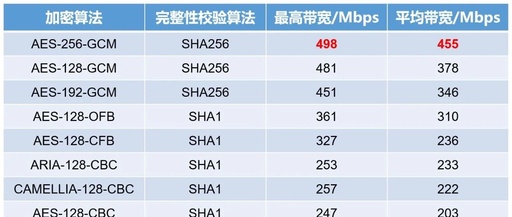
Latest Slider Encryption Parameters of Verification 4th Generation with Pure Algorithm Restoration
Special Statement All content in this article is for learning and communication purposes only and cannot be used for any commercial or illegal purposes. Otherwise, the consequences are at your own risk. If there is any infringement, please contact the author for immediate deletion! Due to my limited ability, if there are any inaccuracies in … Read more