Comprehensive Analysis of Java SHA-256 Algorithm
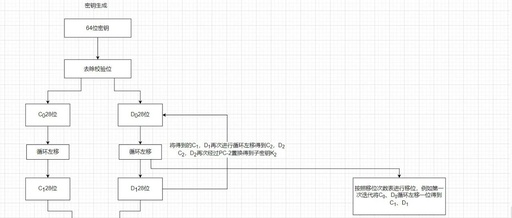
Comprehensive Analysis of Java SHA-256 Algorithm 1. Theoretical Background 1.1 Basics of Hash Functions The hash function is a core component of cryptography, with the following key properties: Determinism: The same input will always produce the same output Efficiency: Quickly computes the hash value for inputs of any length Pre-image Resistance: It is infeasible to … Read more