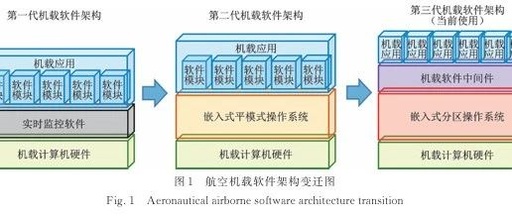
Research on Disaster Recovery System Model Based on Virtualization Technology
Research on Disaster Recovery System Model Based on Virtualization Technology Fundamentals of Virtualization Technology Virtualization technology is a technique that abstracts physical hardware resources into logical resources. By transforming hardware resources such as CPU, memory, disk, and I/O into a dynamically manageable “resource pool”, virtualization technology breaks physical boundaries, allowing a single physical server to … Read more