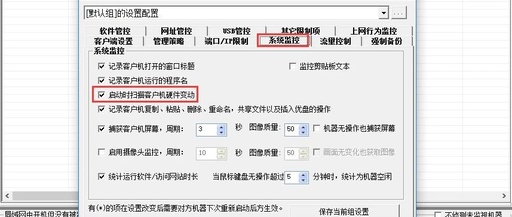
Managing Employee Computer Hardware Changes with WorkWin
In today’s digital office environment, managing a company’s computer systems is crucial, and managing employee computer hardware is a key part of this. The WorkWin computer monitoring software acts like a magical key, opening the door for companies to efficiently manage employee computer hardware changes, helping them navigate hardware management with ease. There are many … Read more