Peripheral Attention+Star PublicAccount to not miss exciting content
Source | Embedded Intelligence Bureau
When you are debugging a development board late at night, and your fingers habitually type <span>printenv</span> in the serial terminal, have you ever wondered: As the gatekeeper of the hardware world, why does U-Boot lack even basic password protection? This is not an oversight by developers, but a design choice made after careful consideration. Today, let’s discuss some of the considerations behind this.
1. Minimal Design Goals
The primary task of U-Boot is to initialize hardware, load the operating system kernel, and transfer control. Its design emphasizes lightweight, fast booting, and portability. Adding password functionality could increase code complexity, storage usage, and boot time, which is not entirely consistent with its core goals.
U-Boot does not allocate much space; every byte must be carefully calculated. Adding password functionality means: first, introducing encryption libraries, then needing a storage management module, and finally, authentication logic (which would significantly squeeze the space for critical drivers and initialization code.
Moreover, U-Boot should not slow down too much; many people already complain about slow Linux boot times, which can significantly impact systems requiring fast booting. Let Linux handle it; I serve Linux.

Additionally, there are many chip architectures to support, with variations in hardware random number generators and secure storage media (NOR/NAND/eMMC), all of which need to be considered, which complicates matters.
2. Deficiencies of Software Passwords at the Boot Layer
Even if password protection is forcibly implemented, it falls into a security paradox:
1. First, storage is not secure
The environment variable area CONFIG_ENV_ADDR is a gold mine for attackers:
# Attackers can easily extract Flash content via the serial port
=> md.b 0x1f800000100 # Read environment variable sector
1f800000: 626f6f74636d 643d 72756e 2070617373 bootcmd=run pass
1f800010: 776f72645f636865636b 3b 626f6f746d word_check;bootm
Moreover:
# Attackers can easily bypass the password via UART
=> iminfo 0x81000000 # Check image signature
=> erase 0x1f80000 0x1ffffff # Erase environment variables
=> setenv bootcmd 'run fastboot' # Tamper with boot commandWhere is the password stored? If placed in the environment variable area, it can be viewed directly via <span>printenv</span>; if placed in the code area, it can be extracted by decompiling the U-Boot image; if placed in the OTP area, it requires hardware support and increases customization costs.
2. Debugging interfaces are not secure
Debugging interfaces (such as ARM CoreSight) that exist during the chip testing phase can take over control flow with hardware privileges. Most SoC debugging interfaces are enabled at the factory, allowing attackers to read and write memory directly via JTAG, and they can also trigger boot exceptions via UART, then inject instructions to bypass password verification using electronic probes.
3. If an attacker modifies the U-Boot image to inject malicious code (such as removing password checks), any software protection will collapse. This is the original sin of boot layer password schemes, unless verified by a preceding bootloader. Currently, some newer secure chips from major manufacturers have such a process.

3. Alternative Solutions
1. Implement a secure boot trust chain
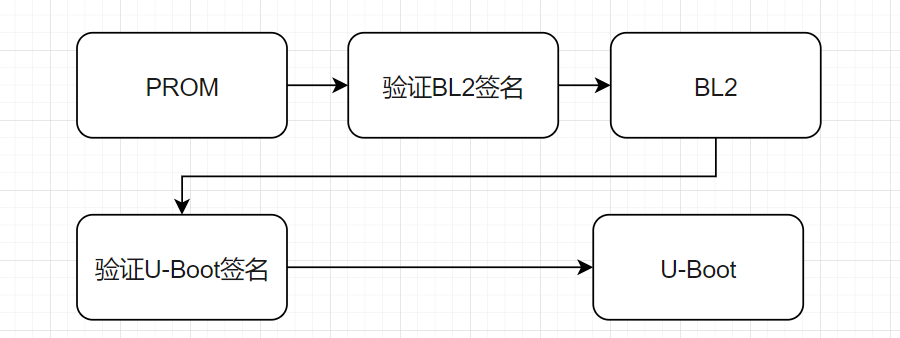 Establish an immutable trust path through RSA/ECC certificate chains
Establish an immutable trust path through RSA/ECC certificate chains
2. Eliminate debugging interfaces
After fuses are blown, physical debugging interfaces become permanently ineffective, for example:
// Example of critical fuse bits
#define FUSE_BANK0_WORD0 0x00020000 // JTAG_DISABLE
#define FUSE_BANK0_WORD5 0x00000020 // UART_DBG_DIS
void secure_disable_debug(void)
{
// Blow the debugging interface fuse
write_eFuse(FUSE_BANK0_WORD0, 0x1);
// Lock the eFuse area
write_eFuse(EFUSE_LOCK_REG, 0xDEADBEEF);
}3. If you want to strengthen your U-Boot security, consider the following solutions based on your needs:
| Protection Level | Recommended Solution | Implementation Example |
|---|---|---|
| Basic Protection | Pseudo password for environment variables | <span>if test "$sec" != "pass"; then reset; fi</span> |
| Production Protection | Disable debugging interfaces | Burn eFuse/OTP fuses |
| High Security Requirements | Secure Boot + Encrypted Boot | Enable SoC’s HAB/ATR features |
———— END ———— ● Column “Embedded Tools”● Column “Embedded Development”● Column “Keil Tutorials”● Selected Tutorials from the Embedded ColumnFollow the public accountReply “Join Group” to join the technical exchange group according to the rules, reply “1024” to see more content.Click “Read the Original” to see more shares.
● Column “Embedded Tools”● Column “Embedded Development”● Column “Keil Tutorials”● Selected Tutorials from the Embedded ColumnFollow the public accountReply “Join Group” to join the technical exchange group according to the rules, reply “1024” to see more content.Click “Read the Original” to see more shares.