As we all know, the TCP/IP model is the foundational model for most network communications today, and its basic function is to define the technical framework for interconnecting devices. Through it, networks around the world can interconnect, and information can be exchanged globally.

The protocol stack is also known as the communication stack. When we usually communicate using software, the computer divides a complete process into different functional parts, and these functions are arranged to be completed at different “layers”.

However, the work of these “layers” follows a specific order, and the order of these layers and the functions they are responsible for are standardized and universally applicable internationally.
Each layer at the sending end of the communication only interacts with the same layer at the receiving end, which is known as “virtual dialogue.” The functions or data carried by each layer are completely encapsulated within that layer, and higher layers can access lower layers only through the services provided by the lower layer’s Service Access Points (SAPs, which are a set of software-level interfaces). Therefore, any changes to the content (functions or data) of this layer will not affect other layers, which is also known as the “information hiding principle.”
The core of the protocol stack is the protocol. A protocol is a set of defined rules that determine the data format for communication between the same layer (at both ends of the communication).
For example, as shown in the figure below:
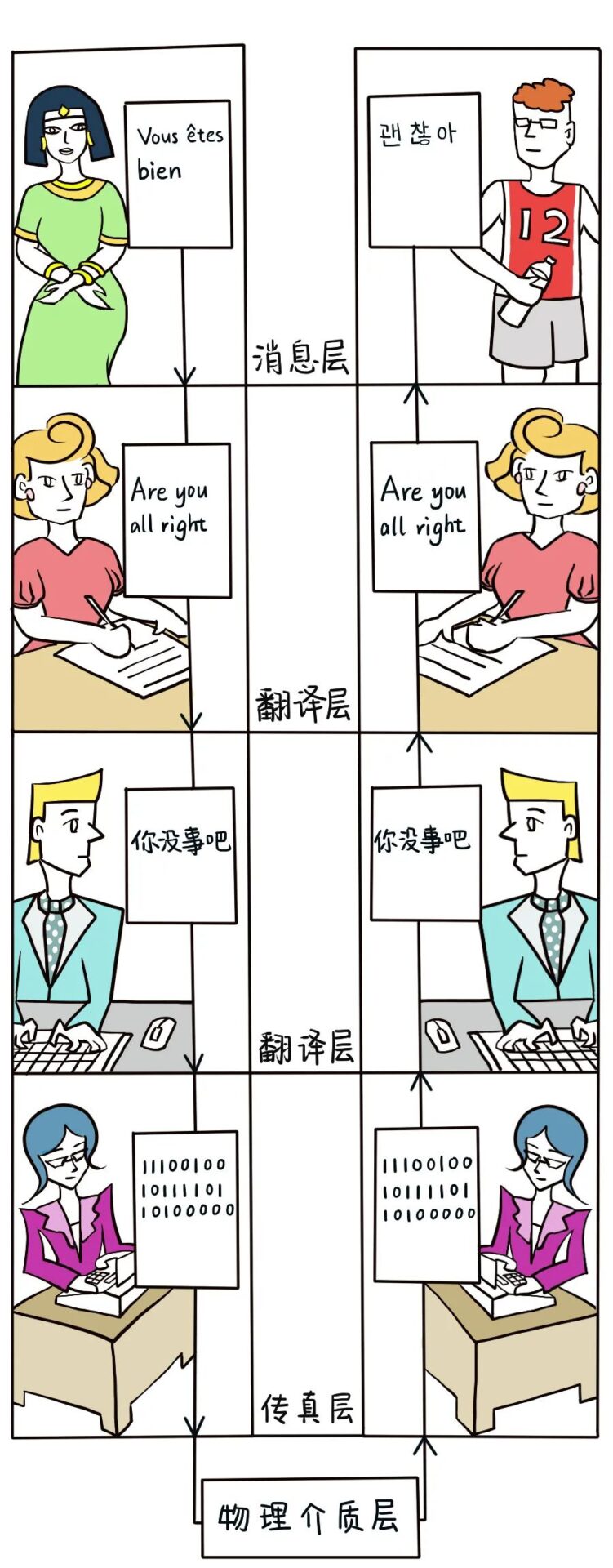
Two people speaking different languages, located far apart, want to communicate via fax within China. They first translate their local languages into a common language (Chinese) through several steps, then transform it into a language that the fax circuit can carry (digital) to communicate directly. In other words, except for the lowest “fax layer,” which can directly transmit information using the “digital circuit language,” all other layers (such as the second and third translation layers and the fourth message layer) are engaged in “virtual dialogue.” A person at location A communicates in French at the fourth layer with someone in Korean at location B; the translators at both locations only need to focus on the text’s language mapping at the second and third layers without altering the message content to be transmitted; the secretaries at the lowest layer at both locations only need to use the same encoding rules to convert the common language (Chinese) into circuit language to achieve message transmission. It can be seen that each layer only processes the content it is responsible for: the lowest layer’s secretary focuses only on the fax “digital circuit language,” the second layer only needs to focus on the conversion between Chinese and English, the third layer only needs to focus on the conversion between English and the local languages of A and B, and only the top layer focuses on the specific content of the communication.
Understanding the above example makes the principle of the protocol stack easy to grasp.
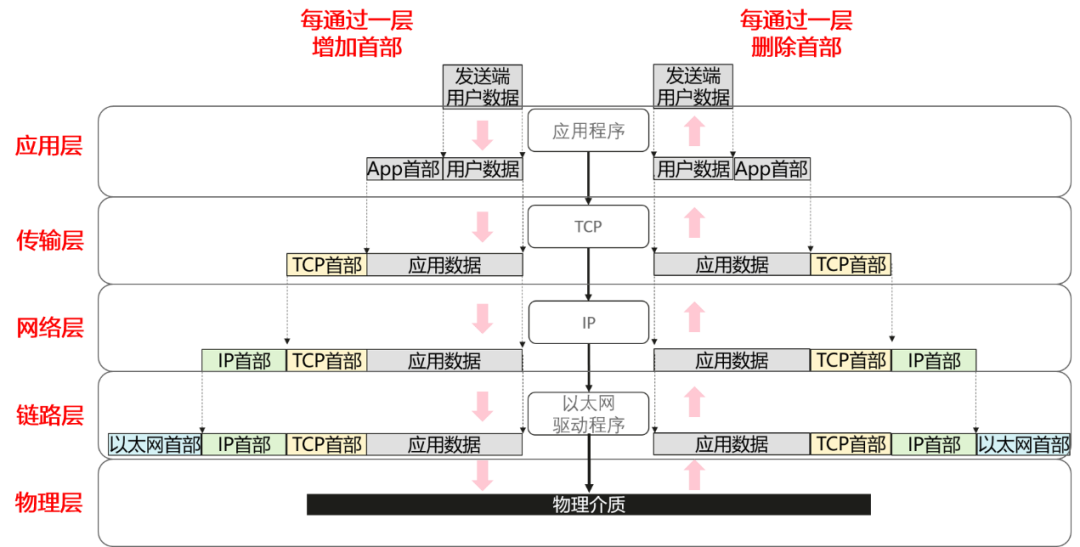
In a packet-switched network, the basic data packet is the content we need to transmit directly, but it needs to be encapsulated layer by layer, adding the corresponding layer’s data headers until it is encapsulated into a physical medium layer that can directly transmit digital language. The corresponding layers can be seen as engaging in “virtual dialogue.”
Next, let’s take a look at the main content and functions encapsulated at each layer of the TCP/IP protocol stack.
1
Physical Layer
The physical layer is used to establish the most basic physical connection between devices, and its main function is to convert binary bit streams into electrical signals, specifying the medium type, interface type, signaling type, standard levels, data rates, maximum transmission distances, and physical connectors, among other characteristics.
2
Data Link Layer
The main function of the data link layer is to specify how data is transmitted over physical lines, communicate with the physical layer, identify protocol types, and encapsulate data for transmission over the network.
The most significant content here is the MAC address that we are familiar with. The MAC address is a 48-bit string, where the first 24 bits are the vendor ID used to identify the device manufacturer, such as Huawei devices having a MAC address starting with 0x00e0fc. The last 24 bits are the serial number. The MAC address is primarily used to mark the location information of devices within the same network.
3
Network Layer
Next is the network layer, whose main function is to forward data packets from the source to the destination between different networks. The most important information it provides is the IP address. Unlike the MAC address, the IP address is mainly used to mark the location of devices within different networks and achieves data forwarding between devices through routing.
4
Transport Layer
The transport layer’s main function is to establish end-to-end connections, transmit data from one host to another, and ensure that data is transmitted in order, reliably, and correctly.
Here we must talk about the “three-way handshake” of TCP connection establishment.
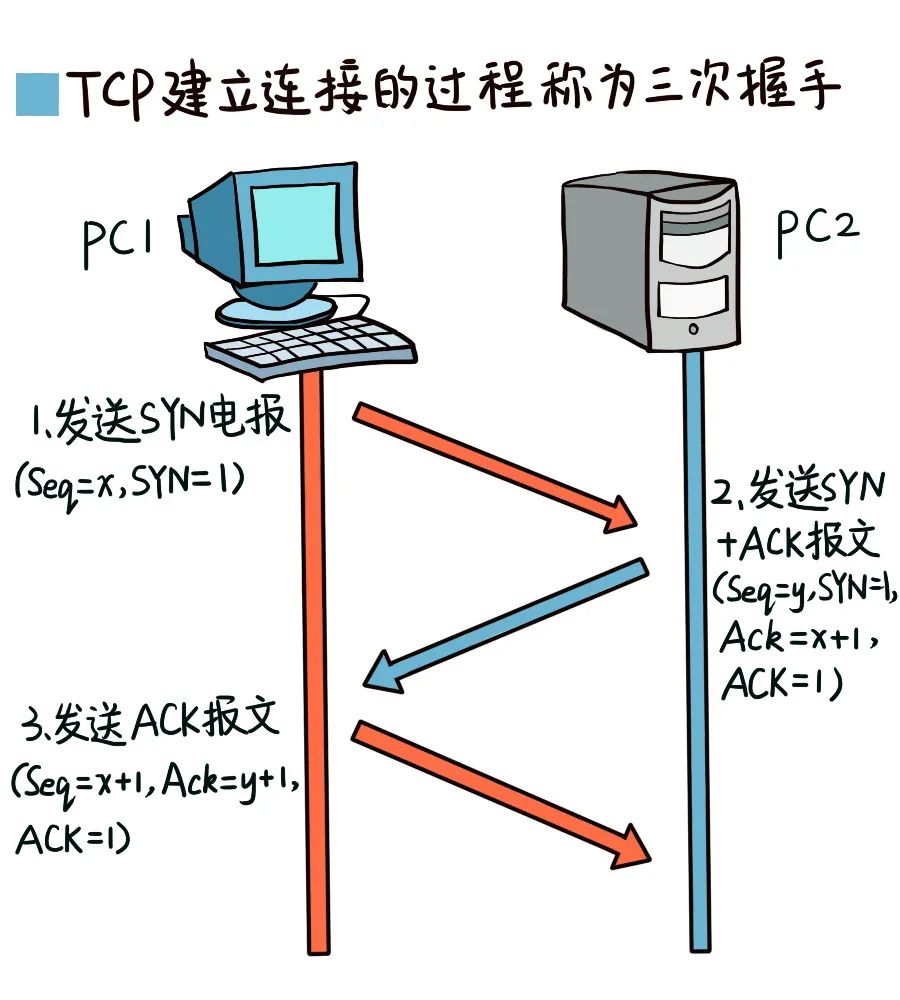
First: The client sends a SYN message, actively initiating a connection request, SYN=1, seq=x.
Second: The server receives the SYN message and replies with an ACK message, SYN=1, ACK=1, seq=y, ack=x+1.
Third: The client receives the server’s ACK and replies with an ACK message, SYN=1, ACK=1, seq=x+1, ack=y+1. The client and server enter the ESTABLISHED state.
Why is there a “three-way handshake” instead of a “two-way handshake”? The main reason is that the message segment sent by the client may remain in a network node for a long time due to network congestion, and when the server receives it, the connection request may have expired. To avoid the server mistakenly thinking this is a valid connection request, it sends a “confirmation” to the client, and a new connection is established. However, the server’s “confirmation” will not receive a response, leading to continuous resource consumption.
We can understand this through an example:
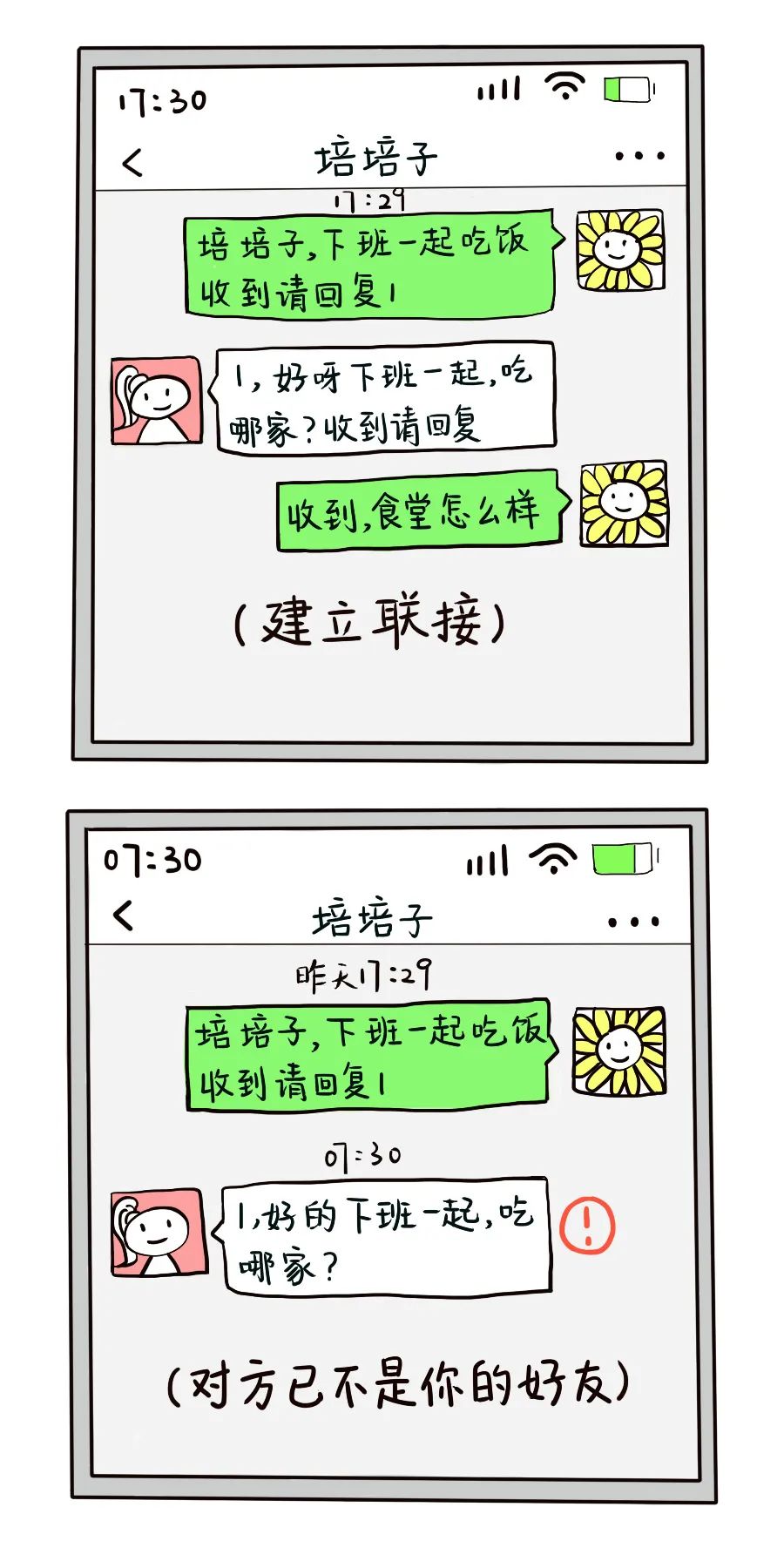
Thus, if the “three-way handshake” connection establishment method is used, the situation where the client does not respond to the server’s confirmation indicates that the client is currently unable to establish a connection.
5
Application Layer
The last layer is the application layer, which is also the layer closest to us. The various applications on our phones and computers belong to this layer. The application layer is primarily used to perform the initial processing of various information, converting various videos, images, text, and other information into binary data streams that devices can recognize. It provides user interfaces, processes specific applications, and handles data encryption, decryption, compression, and decompression.
The TCP/IP model divides the network into five layers, each functionally independent yet closely interconnected.
Today’s brief discussion on the data processing flow of the TCP/IP protocol stack ends here. If any communication professionals have questions, feel free to leave a comment for discussion!
——— More exciting content awaits at Huawei Training video channel ———
Please give a ‘like + favorite + share’ three-in-one! 👇