This article compares the performance of four commonly used encryption algorithms: DES, 3DES, Blowfish, and AES (Rijndael). By running several encryption settings to process data blocks of different sizes, the encryption/decryption speed of the algorithms is evaluated and compared. The simulation is performed using C#.
Keywords: encryption algorithms, performance, analysis, AES, DES, Blowfish, TripleDES, cryptography
Symmetric and Asymmetric Encryption
The data encryption process is mainly divided into two categories based on the type of secure key used for encryption/decryption of secure data. These two categories are: asymmetric and symmetric encryption technologies.
2.4.1 Symmetric Encryption
In this type of encryption, the sender and receiver agree on a (shared) key. They then use this key to encrypt and decrypt the messages they send. Figure 4 shows the process of symmetric encryption.
Nodes A and B first agree on the encryption technology used for the communication data’s encryption and decryption. Then, they agree on the keys that both parties will use in this regard. Once the encryption setup is complete, node A begins sending encrypted data using the shared key, while node B uses the same key to decrypt the encrypted messages.
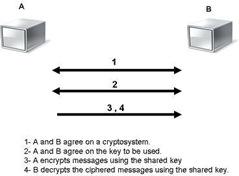
Figure 4: Symmetric Encryption
The main issue behind symmetric encryption is how to securely share the key between two nodes. If the key is known for any reason, the entire system collapses. Key management for this type of encryption is cumbersome, especially if each peer connection uses a unique key, then the total number of keys that n nodes need to store and manage will be n(n-1)/2.
2.4.2 Asymmetric Encryption
Asymmetric encryption is another type of encryption that uses two keys. To explain further, Key1 can only encrypt while Key2 can decrypt, and vice versa. It is also known as Public Key Cryptography (PKC), as users tend to use two keys: a public key and a private key known only to the user.
The following Figure 5 illustrates the use of two keys between Node A and Node B. After agreeing on the type of encryption used in the connection, Node B sends its public key to Node A. Node A uses the received public key to encrypt its message. Then, when the encrypted message arrives, Node B uses its private key to decrypt it.
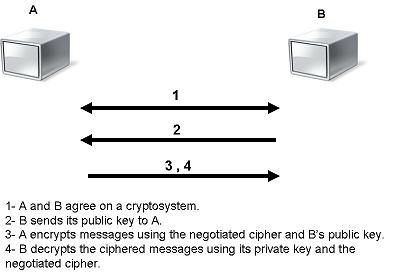
Figure 5: Asymmetric Encryption
This feature overcomes the key management problem of symmetric encryption. However, on the other hand, this unique feature of public key encryption makes it mathematically more susceptible to attacks. Additionally, asymmetric encryption techniques are nearly 1000 times slower than symmetric techniques because they require more computational processing power.
To benefit from both methods, hybrid techniques are often used. In this technique, asymmetric encryption is used to exchange keys, and then symmetric encryption is used to transfer data between the sender and receiver.
2.5 Comparison of Algorithms
This section aims to provide readers with the necessary background to understand the key differences between the comparison algorithms.
DES: (Data Encryption Standard) is the first encryption standard recommended by NIST (National Institute of Standards and Technology). It is based on an algorithm called Lucifer proposed by IBM. DES became a standard in 1974. Since then, many attacks and methods have exploited the weaknesses of DES, making it an insecure block cipher.
3DES: As an enhancement of DES, the 3DES (Triple DES) encryption standard was proposed. In this standard, the encryption method is similar to that in the original DES, but applied three times to increase the encryption level. However, it is known that 3DES is slower than other block cipher methods.
AES: (Advanced Encryption Standard) is the new encryption standard recommended by NIST as an alternative to DES. The Rijndael algorithm (pronounced as Rain Doll) was selected after a competition to choose the best encryption standard in 1997. The only known effective attack is a brute-force attack, where the attacker tries all character combinations to unlock the encryption. Both AES and DES are block ciphers.
Blowfish: It is one of the most common public domain encryption algorithms provided by one of the world’s leading cryptographers, Bruce Schneier, who is also the president of the consulting company Counterpane Systems, specializing in cryptography and computer security.
Blowfish is a variable-length key, 64-bit block cipher. The Blowfish algorithm was introduced in 1993. While primarily used for software applications, it can be optimized for hardware applications. Although it suffers from weak key issues, it is known that no successful attacks have occurred.
This section briefly introduces the comparative encryption algorithms. The introduction of each algorithm in this article is intended to provide minimal information to distinguish the key differences between them.
To better forecast the performance of comparison algorithms, this section discusses results obtained from other resources.
One known encryption library is Crypto++. The Crypto++ Library is a free C++ encryption scheme class library. Currently, this library contains the following, some of which are other people’s code repackaged into classes.
Table 1 contains speed benchmarks for some of the most commonly used encryption algorithms. All of these were written in C++ and compiled using Microsoft Visual C++ .NET 2003 (whole program optimized for speed, P4 code generation) and run on a Pentium 4 2.1 GHz processor under Windows XP SP 1. Multi-precision addition and subtraction operations were performed using 386 assembly code. Multi-precision multiplication was performed using SSE2 intrinsic functions.
From the table, it can be seen that not all modes were tried for all algorithms. Nevertheless, these results indicate what the presented comparative results should look like.
Furthermore, it shows that Blowfish and AES exhibit the best performance. It is well known that both have better encryption (i.e., stronger resistance to data attacks) than the other two.
|
Algorithm |
Megabytes (2 ^ 20 bytes) Processed |
Time Used |
MB / Second |
|
Blowfish |
256 |
3.976 |
64.386 |
|
Rijndael (128-bit key) |
256 |
4.196 |
61.010 |
|
Rijndael (192-bit key) |
256 |
4.817 |
53.145 |
|
Rijndael (256-bit key) |
256 |
5.308 |
48.229 |
|
Rijndael (128) CTR |
256 |
4.436 |
57.710 |
|
Rijndael (128) OFB |
256 |
4.837 |
52.925 |
|
Rijndael (128) CFB |
256 |
5.378 |
47.601 |
|
Rijndael (128) CBC |
256 |
4.617 |
55.447 |
|
DES |
128 |
5.998 |
21.340 |
|
(3DES) DES-XEX3 |
128 |
6.159 |
20.783 |
|
(3DES) DES-EDE3 |
64 |
6.499 |
9.848 |
Table 1: Comparison results using Crypto++
In this article, popular key algorithms including DES, 3DES, AES (Rijndael), and Blowfish are implemented and their performance compared by encrypting input files of different contents and sizes. The algorithms are implemented using a unified language (Java), following its standard specifications, and tested on two different hardware platforms to compare their performance.
Tables 2 and 3 show their experimental results where experiments were conducted on two different machines: P-II 266 MHz and P-4 2.4 GHz.
|
Table 2: Comparison execution times of encryption algorithms in ECB mode on P-II 266 MHz machine (in seconds)
|
Table 3: Comparison execution times of encryption algorithms in ECB mode on P-4 2.4 GHz machine (in seconds)
From the results, it is easy to see that Blowfish outperforms other algorithms in throughput. Aamer Nadeem et al. also compared the algorithms in CBC stream mode, but since this article focuses more on block ciphers, the results are omitted.
The results indicate that Blowfish has very good performance compared to other algorithms. Additionally, it shows that AES performs better than 3DES and DES. Surprisingly, it also indicates that 3DES has nearly 1/3 the throughput of DES, meaning it takes 3 times longer than DES to process the same amount of data.
Priya Dhawan also conducted experiments to compare the performance of different encryption algorithms implemented within the .NET framework. Their results are close to those previously shown (Figure 6).
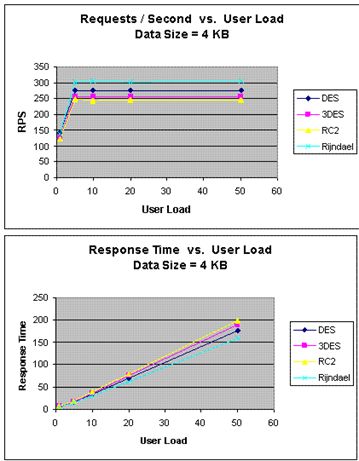
Figure 6: Comparison results using .NET implementation
The comparison was conducted on the following algorithms: DES, 3DES, RC2, and AES (Rijndael). The results show that AES outperforms other algorithms in terms of the number of requests per second and response time under different user loads.
This section summarizes the comparative results from others in the field.


Performance Analysis of Data Encryption Algorithms – 1
How Papers are Made
How to Install NTL Library on Ubuntu
Compiling NTL_11_3_2 Version on Windows
How to Detect Hidden Surveillance Cameras with Your Phone – 2
How to Detect Hidden Surveillance Cameras with Your Phone – 1
How to Steal Ethereum Wallet Keys – 3
How to Steal Ethereum Wallet Keys – 2
How to Steal Ethereum Wallet Keys – 1
NIST Lightweight Encryption Algorithm Standardization Round 1 Candidate Schemes
A Data-Driven Cryptocurrency Prediction Method – 3
A Data-Driven Cryptocurrency Prediction Method – 2
Welcome to Listen to the “Blockchain Talk” Program, the Most Quality Blockchain Knowledge Sharing Program in China.


Geomancy Chain
Focusing on Cryptographic Technology on Blockchain
Long press the QR code to follow