1. Background
1. Background
1. Background
Processor hardware vulnerabilities refer to design flaws introduced by processor logic design that affect the correctness or security of processor functionality. Early academic research on hardware vulnerabilities focused on cryptographic side channels and malicious hardware. These two types of vulnerabilities are often difficult to exploit remotely via software. In 2018, the Google team first disclosed two sets of hardware vulnerabilities caused by transient execution mechanisms in processor microarchitecture, namely the well-known “Spectre” (CVE-2017-5753/CVE-2017-5715) and “Meltdown” (CVE-2017-5754). These two vulnerabilities were among the first processor microarchitecture hardware vulnerabilities recorded in CVE.
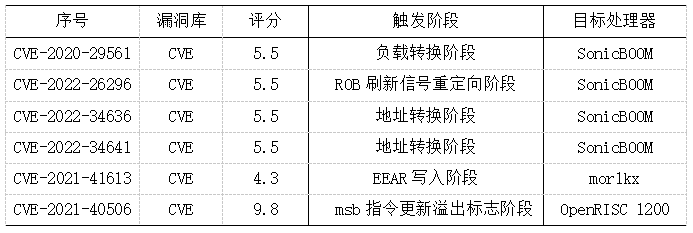
Currently, there are relatively few disclosed vulnerabilities related to RISC-V processors both domestically and internationally. The CVE includes vulnerabilities related to the BOOM processor such as CVE-2020-29561 (load conversion exception), CVE-2022-26296 (transient execution attack), CVE-2022-34636 (address translation PMA violation exception type error), CVE-2022-34641 (address translation PMP violation exception type error). In addition, CVE has also disclosed some other open-source processor vulnerabilities such as the controller logic error implementation for EEAR (Exception Effective Address Register) writing in OpenRISC processors, and the carry flag update vulnerability in ALU unit subtraction instructions.
Table 1: Current CVE Recorded Vulnerabilities Related to RISC-V Processors
2. Vulnerability Technical Analysis
2. Vulnerability Technical Analysis
2. Vulnerability Technical Analysis
1. Vulnerability Product Analysis
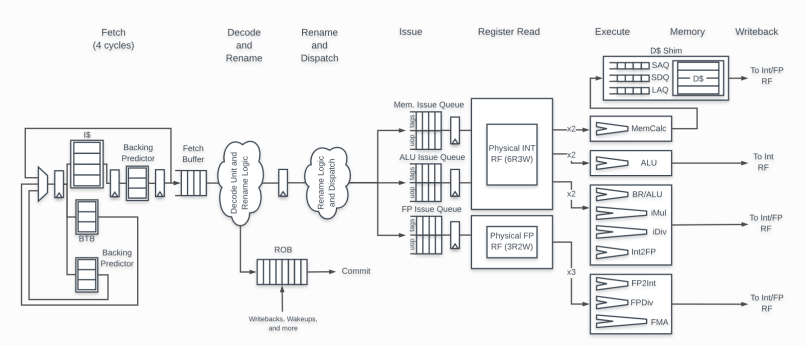
This vulnerability was found in the RISC-V SonicBOOM open-source code.SonicBOOM is a third-generation RISC-V superscalar out-of-order processor developed by the University of California, Berkeley, aimed at providing an advanced open-source platform for high-performance processor research and applications. The code link is as follows: https://github.com/riscv-BOOM/riscv-BOOM
The architecture of the SonicBOOM processor is as follows:
2. Vulnerability Cause Analysis
In the SonicBOOM processor, the ALU (including addition), multiplication, and division units use the same write port to access the register file. In the case of write port contention, there is fixed-priority arbitration, where the ALU has the highest priority and the division unit has the lowest priority. This means that due to port contention, division instructions may be delayed by younger multiplication or addition instructions, leading to differences in execution time for division instructions, thus creating a timing side channel.
3. Vulnerability Exploitation Pathways
The principle of exploiting this vulnerability is to perform division operations before transient execution, and then, within the transient time window, attempt to use branches related to confidential information. If the probe value exactly equals the confidential information, multiplication and addition operations are executed. Due to the lower priority of the division operation, there is contention with the younger multiplication and addition operations, which causes the overall code execution time to increase due to the prolonged execution time of the division instruction. An attacker can probe confidential information by measuring the time required to execute the code.
This vulnerability can be regarded as a new type of side-channel attack, combining the impact of transient attacks on the microarchitectural state, thus becoming a new type of transient attack.
4. Vulnerability Exploitation Effects
This vulnerability mainly affects confidentiality. By exploiting this vulnerability, an attacker can bypass processor boundary checks, memory access permission checks, and other security measures, directly inferring confidential information through timing differences caused by port contention, leaking data accessed during transient execution through side channels.
5. Comparison with Existing Microarchitectural Vulnerabilities
Current Spectre and Meltdown attacks, whether Spectre-v1 (exploiting processor mode history tables), Spectre-v2 (exploiting processor branch target buffers), Spectre-v3 (exploiting processor return stack buffers), Spectre-v4 (exploiting store-load), or Meltdown-type attacks, mostly use cache side-channel attacks to leak information during the information recovery phase after triggering transient execution. The port contention vulnerability discovered this time can replace cache side-channel attacks, serving as a new type of side-channel attack. The port contention vulnerability can combine with different transient execution mechanisms to form new types of processor security vulnerabilities.
3. Vulnerability Impact Analysis
3. Vulnerability Impact Analysis
3. Vulnerability Impact Analysis
In recent years, the RISC-V instruction set architecture has rapidly developed, attracting widespread attention due to its open-source, concise, modular, and easily extensible characteristics. Calista Redmond, CEO of RISC-V International, stated at the Embedded World Exhibition in July 2022 that RISC-V shipments have surpassed 10 billion. In particular, RISC-V is seen as an opportunity for China to achieve a leapfrog development in chip autonomy, leading to a surge in domestic RISC-V architecture processor cores and chip products.
RISC-V has two main application scenarios: one is independent RISC-V processor chips, and the other is as processor cores integrated into large system-on-chips, executing various computational and control tasks. By the end of 2022, there were about 50 different models of domestic RISC-V chips in mass production in China, focusing on embedded scenarios such as industrial control, power management, wireless connectivity, and storage control in the Internet of Things. With the continuous evolution of the ecosystem in recent years, RISC-V is also trending from embedded scenarios to higher computational requirement scenarios such as industrial control, autonomous driving, artificial intelligence, communication, and data centers.
SonicBOOM, as an open-source platform, is applied in both of the above scenarios and serves as the foundation for the development of many domestic commercial RISC-V processors. Although enterprises modify and optimize the original code during development, its instruction architecture still has similarities, therefore the security risks discovered in SonicBOOM remain a concern for domestic processor manufacturers and processor application parties.
ReprintPlease indicate the source: CNCERT National Engineering Research Center
